My grandfather is 77 and has lived a very full life. He has a law degree, a master’s in theology and this summer he repaired an old car installing a new engine. My grandfather is intelligent and well educated, but despite this he struggles with basic tech and digital skills. Basic things like updating his computer, going on Facebook and using the apple TV remote. I, as his eldest grandson, of course help him, but I am confounded with his difficulty in adapting to new tech.
My grandfather has remarked to me how the rapid development of technology has made everyday activities like interacting with a foreign culture.

Statistically, the Baby Boomer generation (51-69) and the Silent generation (70-87) find it difficult to adapt to new technologies and most members of government are in these age groups, given that the average age in the House is 57 and that in the Senate it is 61. It might not seem like it, but Capitol Hill is like any other workplace and is effected by new trends in technology. Our Senators and Representatives, similar to other Senior Citizens who work to or past retirement, are no doubt baffled by the latest smart iPhone or the latest version of Windows. They too have common everyday struggles. However, their struggle to develop even basic skills and knowledge has cost many of them politically and compromised government institutions.

Let’s examine the publication of former White House Chief of Staff John Podesta’s email by Wikileaks. Mr. Podesta is an intelligent and well-educated man, and very powerful. He is also 68 years old and the email 2things demonstrates isn’t computer savvy.
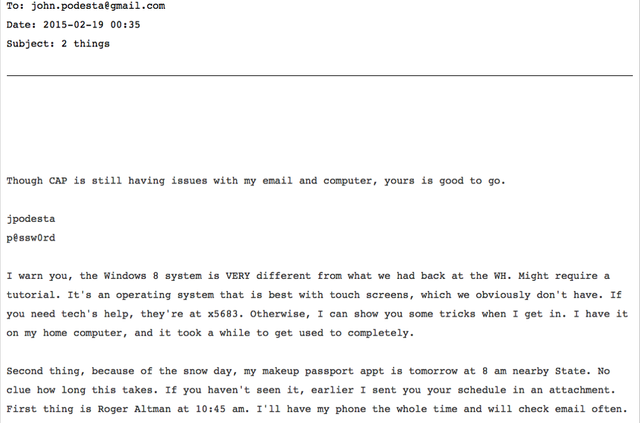
In this leaked email, an assistant in the Hillary Clinton Presidential campaign explains that a new computer he received runs on Windows 8 which is different from what he is used to. It is unlikely that Mr. Podesta is an Apple or Linux user and given his seniority in the campaign it is likely he would have requested his preferred OS.
How Mr. Podesta’s emails were stolen isn’t clear, but there are two prevailing theories. Either it was due to poor password protection or he fell victim in a phishing scam. The email 2 things shows that his password was p@ssw0rd and the Chief Editor of Wikileaks Julian Assange confirms this. Having a sufficient password is the first line of defense for any computer system or device and using the word password as a password is relatively common. Julian Assange commented,
”So, this is something ... a 14-year-old kid could have hacked Podesta that way”
In the email S0me0ne has your passw0rdw have evidence of Mr. Podesta falling victim to a phishing scam.
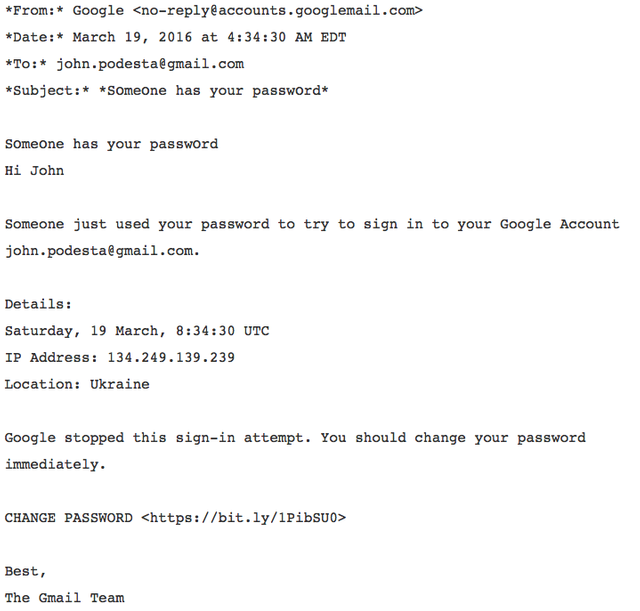
To anyone with basic computer knowledge, or strong intuition, receiving an email with the subject line ’S0me0ne has your passw0rd’ should raise suspicion. If Mr. Podesta had quickly reviewed Google’s Help page he would have learned that Google uses the subject line ‘suspicious sign in prevented’, to raise awareness of malicious sign in attempts. The subject line the phisher used was clearly designed to create panic and if Mr. Podesta had been clear headed he’d have noticed that in the subject line zeroes were used instead of o’s.
Mr. Podesta was suspicious of the email and asked an assistant if it was legitimate. The assistant, not being sure herself, requested help from the IT department, who said it was authentic. After Wikileaks publication of his emails, the IT associate later claimed he hadn’t said it was legitimate, but made a typo in the reply email; I think he was bad at his job. Mr. Podesta’s true sin is not his lack of computer skills, it is that his lack of computer skills caused him to delegate the responsibility of his personal cyber security to individuals who were incompetent.
Mr. Podesta created an ensuing controversy for Hillary Clinton’s presidential campaign and may have cost her the presidency, of which Mr. Podesta may have been the Secretary of State.
This sickening lack of adaption to technology and inability to ensure the proper security is evident in another incident in the House of Representatives. The capitol police are currently investigating three brothers Abid, Imran, and Jamal Awan who were the personal IT for ,' some on the foreign affairs and intelligence committee. In the House of Rep, the HIR (House Information Resources) monitors administration access to the House network. Special written permission is required to access certain IT resources. However, after complaining to their congressional employers the Awan Brothers were given Top Secret Compartmented Information Security (TS/SCI) Clearance, which prevented the HIR from keeping log of their access. While they may not have seen classified information they certainly could have found material to black mail the representatives with.
The three brothers are now at the center of an investigation which has revealed that they took a $100,000 loan from an Iraqi fugitive with connections to Hezbollah. The Awan brothers have not had their passports taken or have been arrested. While Congress and the Capital Police are keeping the investigation quiet, however a HIR staffer is quoted,
“Unfortunately, as the recent election has shown, security of computer systems on the Hill is not really taken seriously.”
Yet it is these very same people who oversee the institutions that safeguard our national security. If our elected officials cannot use the latest word processor how can they defend our nation against cyber threats? More importantly, how can they prevent our institutions from abusing the liberties of citizens?
A hallmark failure of the Bush and Obama administrations was the inability to properly institute protocols for our government institutions to safeguard against the rise of cyber attacks. President Trump seems to seek to remedy this.President Trump is a prolific user of social media, his tweets have the voice of a pubescent teenager, which is impressive for a man of 70.

Perhaps we can assume that because of this his adaption to technology is better than his peers and at the very least he recognizes the problem. President Trump has issued an Executive Order mandating a review of America’s cybersecurity and holding more accountability to agencies who fail to meet standards. As far as first steps go this is acceptable. However, the issue of cyber security is a multifaceted, and the age gap adds to its complications.
Mr. Trump’s selection for intelligence positions reflects a deep mistrust of those agencies. Who could blame him? The White House is spouting leaks. Mr. Trump seems to prefer ex-military and retired elected officials, however they too fall into the age of low technological adaption. His selection for DNI is Dan Coats, a former Senator on the intelligence committee, age 73. Mike Pompeo is CIA director, a former rep. on the Intel Committee who in the army patrolled the ‘Iron Curtain’ in Europe, age 53. As his Cyber Czar Mr. Trump has selected the elderly Rudy Giuliani, former Mayor of New York and age 72. With the exception of Mr. Pompeo, these appointments are well past the digital divide.
The selection of Rudy Giuliani is the most interesting. Certainly Mr. Giuliani is a capable attorney and well versed in counter-terrorism, the primary issue he ran on during his 2008 bid for President, but cyber-security? Though it appears an old dog can learn new tricks. During the V4 Cybersecurity Conference in Washington Washington, Mr. Giuliani opened his presentation by confessing the issue with cybersecurity is,
“We spent too little time talking about it in the past.”
In his presentation, Mr. Giuliani explained that a five point system was necessary to prevent intrusions. During his presentation Mr. Giuliani demonstrated a strong understanding of cyber security theory. While this is reassuring, the issue of the digital divide, age and security still persists.
The rapid development of technology, digital infrastructure and cybersecurity is a skill primarily localized in the Millennial
generation. Mark Zuckerberg has said,
“young people are just smarter .”
The average age for an employee at Facebook, Google and Apple is late twenties to early thirties. While companies like Dell, IBM and HP is late thirties to early forties. The best tech companies try to hirer as young as possible. As for governments, the Israeli’s have begun teaching 10th graders how to stop malicious cyber attacks.
As Mr. Giuliani said past generations were slow to realize the threat of the machines. Like in The Matrix, they (pre Millennial generations) are the last of the ‘freeborn humans’ having lived in mankind ‘Golden Age,' before the birth of A.I. However, Millennials, like the savior Neo, are artificial humans and were born in pods. The recruits into our intelligence agencies are younger than they have ever been before, and the grandfathers and grandmothers on top, however wise they maybe, cannot understand these youngsters. This vast generational gap of experience is akin to the differences between the German and the French, and it too has led to conflict.
We have evidence that this is so, former Director of the CIA Michael Hayden, age 71, when discussing the CIA leaks, published by Wikileaks as Vault 7, laments,
“In order to do this kind of stuff, we have to recruit from a certain demographic. I don’t mean to judge them at all, but this group of millennials and related groups simply have different understandings of the words loyalty, secrecy and transparency than certainly my generation did. Culturally, they have different instincts than people who made the decision to hire them,”
Mr. Hayden confirms that there is an age gap in intelligence agencies, but also demonstrates a distain towards them. Why does he voice such a distain? Surely being an intelligent and well educated man he realizes that for the CIA to stay relevant they must hirer the best. If the best are Millennials then by golly so be it! I believe this distain comes from a difference in foreign affairs philosophy.
The old guard, the senior intelligence and military officials, who spent their younger days fighting Communism, developed their own philosophy of Neoconservatism to combat the Soviets. Today, Millennials say the word neocon like a curse. To illustrate, Edward Snowden was 28 when he leaked the stolen documents from the NSA. When asked why he did it, Mr. Snowden said,
”The government has granted itself power it is not entitled to. There is no public oversight. The result is people like myself have the latitude to go further than they are allowed to,"
The statement is sacrilege to the foreign policy of the last thirty years.
In a separate interview Mr. Hayden remarked how since 2001 their have been very little changes in the upper echelon of the CIA. If this is so then his sentiment towards millennials is most likely shared by them. Yet, such an attitude is strange. Does the old guard really expect to abuse their subordinates who, as Chuck Schumer said, ‘have six ways from Sunday at getting back at you’ and not suffer for it? They mistake these pupsf or the canine variety not realizing that they are sharks, and there is blood in the water.
My father used to tease me that, ’father and son are in a constant battle and eventually one must destroy the other’ and my grandfather would joke ‘when I get too old take me out into the woods and hit me in the back of the head with a shovel,' an act I would never do, but a common theme in history is the challenging of authority by youthful revolutions.
In a blog entry entitled, ‘Does a Rogue Deep State have Trump’s Back?’, Charles Hugh Smith proposes such a scenario. Mr. Smith theorizes that a ‘progressive’ element in national security is quietly challenging the neocon establishment. It could be that this new ‘Deep State’ is leaking intelligence documents to force their superiors into early retirement. However, concrete evidence is diffuclt to produce, and as Mr. Smith says,
“…the one thing everyone agrees on is the Deep State’s dirty laundry must be kept private.”
Mr. Hayden’s statements, are similar to those expressed by other ‘old men’ in William A. Allcott’s book A Young Man’s Guide published in 1835.
While a lad, I was at play, one day, with my mates, when two gentlemen observing us, one of them said to the other;
'Do you think you ever acted as foolishly as those boys do?'
'Why yes; I suppose I did;' was the reply.
'Well,' said the other, 'I never did; I know I never did.'
Both of these persons has the name of parent, but he who could not believe he had ever acted like a child himself, is greatly destitute of the proper parental spirit.
It seems that our wizen leaders have forgotten their youth, resent those beneath them and seek to hold onto power, but their poor technological adaption is causing them to be incompetent. While, the Millennials, filling the basements of intelligence services and the military, concoct plans in secret and release potentially harmful documents.
The digital divide has not just effected main street, but the capitol as well. The lack of technological adaptiveness in our leaders is affecting their performance and our national security. I see no clear solutions to this problem. Nonetheless, it is a fascinating time to be a Millennial, and I’m happy to be one. The hypnotic optimism and rampaging negativism over our countries future is like hot and cold hair crashing together to make a storm. I like storms, and I wonder what the America landscape will look like once the clouds have rescinded.
Impressive post. Keep it up. Upvoted and Followed.

Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Some more thoughts...
I think we can all feel safer now as Mr. Podesta saw the error in his ways and changed his password from "password" to "podesta".
Hillary Clinton's emails is another thing. Talk of computer naïveté! She is handling power on the highest levels imaginable. Human lives and death are a constant issue. Wars and the deaths of millions could rest on a single keystroke. But she sets up shop on some computer she bought at a fire sale from Radio Shack. Any 12 year old could have hacked it with a smartphone and some hackware he bought on the dark web. Sheeeesh!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
I tried to add a part from the FBI document releases about how she was buying a new blackberry fairly often, but would get rid of it and go back to her old one because she had trouble adjusting to it.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Congratulations @squidly27! You have received a personal award!
Click on the badge to view your own Board of Honor on SteemitBoard.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit