Broken Authentication and Session Management - Common Vulnerability to Hack Website

Today i will told you about one of the most common Vulnerability to Hack websites .But first let me told you
THIS IS JUST FOR EDUCATION PURPOSE!
In Broken Authentication and Session Management Vulnerability i will told you about two ways to break the authentication of website.
Login (Username or Password) Guessing (Brute Force)
Another type of network attack is Password Guessing attack. ... Password guessing attacks can be classified into two. Brute Force Attack: A Brute Force attack is a type of password guessing attack and it consists of trying every possible code, combination, or password until you find the correct one.
For example:
An website admin panel login is:
Username: admin
Password: admin
So the attacker will guess the user and password and trying to login if he were lucky.
You can try google to get websites login and then practice if you want but don't harm the websites
i will also tell in future posts how did we can get websites from google :)
you can try this website:
http://unitytradebdcapital.com/admin/
But please Don't harm the websites this is just for example and if practice if you want.
Insecure login form
Insecure login is a that type of form in which attacker can enter some payloads (Payloads means attacks) and the developer didn't sanitize the form inputs
This type of broken auth is in mostly websites those have SQL Injection vuln(vulnerability).
For example this form:
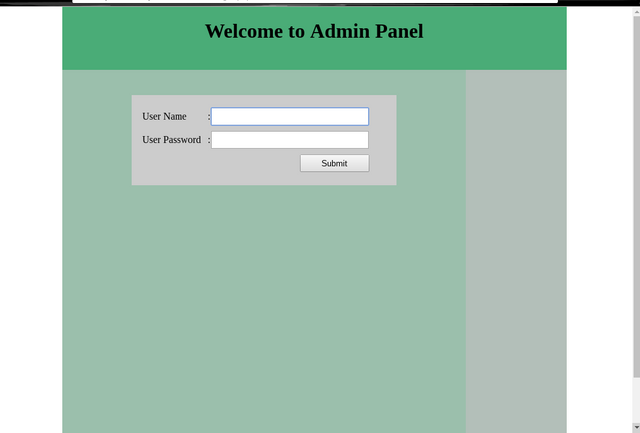
Now let's try the popular payload of SQLI, Enter the following payload in username or password field (maybe it's better to enter payload in both inputs).
Payload:
if that payload doesn't work then try this one:
admin' -- -+
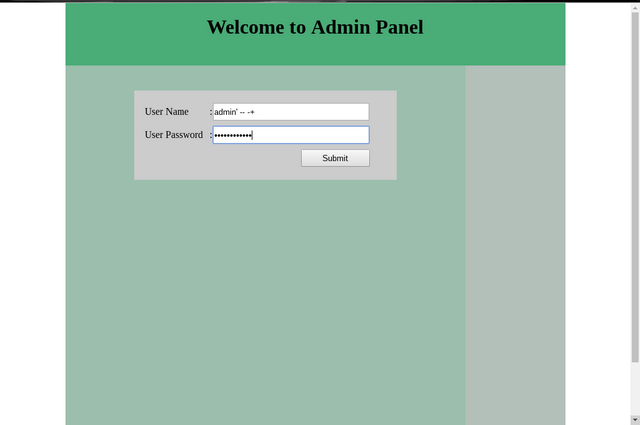
The vulnerable input can be username input field or password, so it's better to test all inputs fields of form.
i've enter the payload in both input fields :p
And now login, then you can see admin panel is bypassed!
i used the same website :p to show you example of this one
Session Management
Session management is a bug (vuln) due to mistake of web dev... for example developer is forget to verify the user is logined or not in chat room or control panel of website so, the attacker is easily gained the access of some private data of website.
i'm sorry for bad english :p and follow to get more information :)