Insecure Direct Object References:
According to owasp:
Insecure Direct Object References occur when an application provides direct access to objects based on user-supplied input. As a result of this vulnerability attackers can bypass authorization and access resources in the system directly, for example database records or files.
Insecure Direct Object References allow attackers to bypass authorization and access resources directly by modifying the value of a parameter used to directly point to an object. Such resources can be database entries belonging to other users, files in the system, and more. This is caused by the fact that the application takes user supplied input and uses it to retrieve an object without performing sufficient authorization checks.
For example: two users each having access to different objects (such as purchase information, private messages, etc.), and (if relevant) users with different privileges (for example administrator users) to see whether there are direct references to application functionality. By having multiple users the tester saves valuable testing time in guessing different object names as he can attempt to access objects that belong to the other user.
Let's suppose an website is using get ($_GET) method means using some parameters (like user id in database)
and that website have multiple users let's suppose they have two users one is admin and another is normal user.
let take this url as example:
http://vulnweb.com/account.php?id={$id}
{$id} is id's of user in database, Now let admin id is 1 and normal user id is 2.
http://vulnweb.com/account.php?id=1
Let's suppose the admin have different features like control panel of website etc.
and now attacker will change the user 2 id to 1 and he gain the access to admin panel easily.
i'm just trying to makes you understand the concept of it. there are too many examples like we can access the different files on server etc.
this image is good example also:
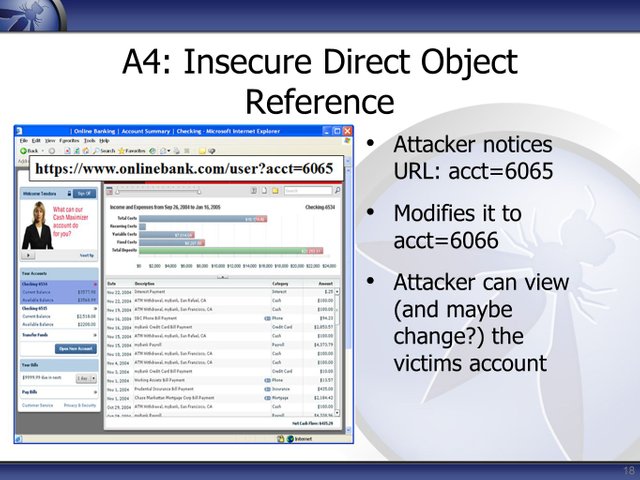
Thanks Don't forget to follow @ammadkhalid
Hi! I am a robot. I just upvoted you! I found similar content that readers might be interested in:
https://www.owasp.org/index.php/Testing_for_Insecure_Direct_Object_References_(OTG-AUTHZ-004)
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit