
Imagine a tool designed specifically for cyber-espionage tasks, which is able to access our computer using the router as a port of entry. And once inside, get system privileges to have control of everything that happens inside our device. It might sound like a spy movie script, but it's real, it exists and it's just been discovered.
It is called 'Operation Slingshot' and it is one of the most advanced attacks of recent years, which seems to be aimed at very specific objectives, people and institutions, in the Middle East and Africa. An attack that is believed to have been operating since at least 2012 and that has affected close to 100 victims.
A custom-made malware that does not know who is behind
Slingshot was discovered after a group of Kaspersky Lab researchers found a keylogger inside the computer of an African government institution. Given this, a monitoring of the behavior of this program was created to see if it appeared elsewhere, which led to find a suspicious file inside the system folder called 'scesrv.dll'.
After analyzing this file, it was found that it has malicious code inside it capable of obtaining system privileges through 'services.exe', so it is an incredibly advanced malware that runs on the kernel, thus reaching the core of the computer taking control of it without the user even being aware of its existence.
Slingshot has a form of attack that has never been seen before, since it is something new that is not based on any other malware that has arisen previously. Therefore, it is believed that it is a tool created to measure by professionals, who are possibly financed by some country, since initially it was believed that it was hacktivism. But seeing the sophistication of the attack, this theory was discarded.
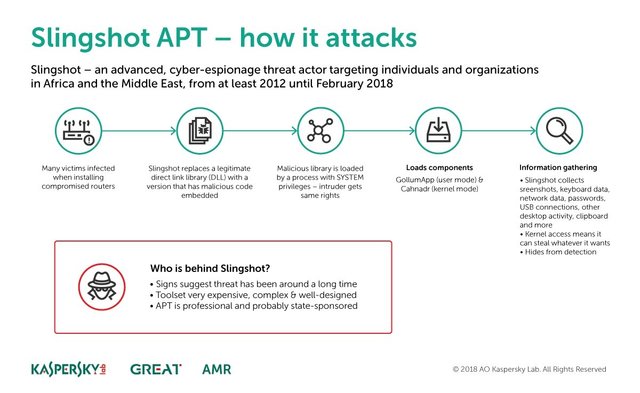
Among what has been discovered about Slingshot is the fact that the infection comes from hacked routers, which are loaded with malicious dynamic links, which in fact is a download program for other files. When the administrator logs in to configure the router, it downloads and runs this code on the administrator's computer, infecting the entire network in just a few minutes.
The method that attackers have used to hack (crack) the routers is still unknown. Once the computer is infected, two powerful tools like Cahnadr and GollumApp do the dirty work. Both modules are connected to each other and are able to collect all the information from the device and then send it to the attackers.
Slingshot screenshots from time to time, obtains data of what the keyboard receives, network data and connections, passwords, devices connected via USB, desktop activity, files saved in clipboards and much more. And you have to remember that this malware has access to the Kernel, so you have access to everything.
Powerful and discreet
But that's not all, since Slingshot also knows how to hide. It includes encryption in all its modules and chains, it connects directly to the services of the system to avoid antivirus and other security programs. It uses anti-debugging techniques and selects the processes in which it will be activated depending on the levels of security installed in the computer, in order to pass completely unnoticed.
But most impressive of all, Slingshot takes advantage of the data it gets via Kernel to hide its communication and links as if it were a legitimate protocol, so it never raises suspicions. This is done by intercepting real connections to later pass through them, all without leaving traces when controlling and hiding IP addresses.
The investigation also showed that it is version 6.x, which suggests that Slingshot has been around for several years. This could explain its complexity, which undoubtedly required a lot of time for its development and especially money, since it is a work of art.
Therefore, it is believed that there is someone with a lot of power behind their development, someone organized and professional. The clues show English-speaking code, although the exact attribution is complicated or almost impossible to determine.
Who are those affected and how to block this threat
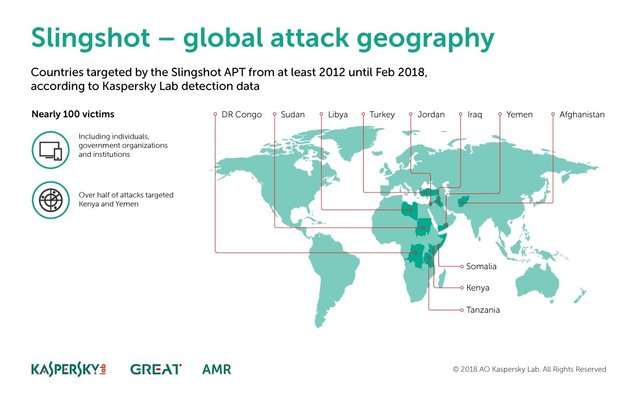
The investigators assure that they exist until February of 2018 near 100 affected by Slingshot, which are located in Yemen, Kenya, Afghanistan, Libya, Congo, Jordan, Turkey, Iraq, Sudan, Somalia and Tanzania. These affected are mainly specific people related to the government and only some organizations, so it is believed that it is very well studied to spy on certain members.
The routers of the Mikrotik brand are the ones affected and to avoid a possible attack, the firmware must be updated to the latest version as soon as possible. This is the only way to guarantee its elimination and protection against possible derivatives based on Slingshot that may arise.