
The WikiLeaks site was exposed on Thursday to an embarrassing electronic attack when the Saudi-based piracy group, OurMine, seized its Web address.
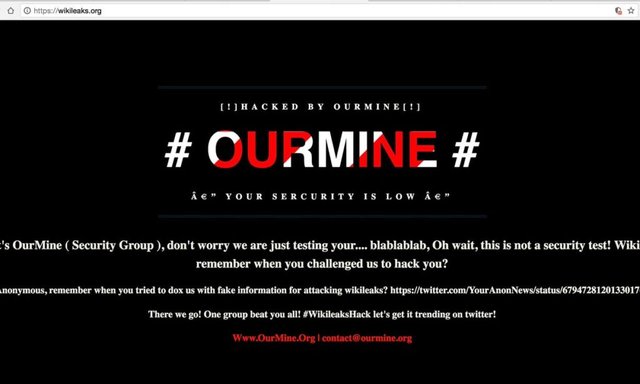
After the cyber attack, users visiting the site were taken to a page created by the Ormain group, which claimed that the attack was in response to a challenge from the organization to penetrate it.
But while hacking may be offensive to Wikileaks, which boasts its technical competence, experts believe the actual "breakthrough" was a low-tech affair, similar to a group of thieves writing phrases on the walls of a bank, Security protection.
The group apparently carried out an attack known as "DNS poisoning" for a short time on Thursday morning. Instead of directly attacking Wikileaks servers, they persuaded one or more DNS servers, which are responsible for converting the human readable wikileaks.org web address into a series of machine-readable numbers that tell the computer to change their records. For a brief time, these DNS servers were told that wikileaks.org was actually located on a server controlled by the Ormain group.
So Wikileaks servers are unlikely to have been hacked. The DNS Protocol is a weak link because of the ease with which individual hackers or those supported by States can be endangered.
In the letter posted on the Wikileaks website, Ormain joked that what happened was just a test of the site's security, before cutting it off and recalling the organization as a challenge to its ability to penetrate the site.
It is the third time that WikiLeaks hackers have been attacked in the past two days by a DDoS denial attack in December 2015 and July 2016.
Last October, the Ormain group broke into the famous BuzzFeed website, apparently reprisal for publishing a report revealing the identity of a member of the secret group.
The group is known for its ability to penetrate the accounts of many technology celebrities such as founder and CEO of Twitter Jack Dorsey, Google CEO Sondar Pichai, Facebook founder and CEO Mark Zuckerberg and Wikipedia founder Jimmy Wales. Of hacking Pokemon Jo's enhanced reality game servers in July 2016.
Last year, two members of the group revealed to The Guardian that the primary purpose of their work was to become known as "moral" advisers in information security, and indeed earn between $ 20,000 and $ 40,000 a month from security consultations.
A member of the group, Aboudi, told the Guardian that he had worked for Microsoft and that he was proud to have penetrated the Sundai Pichai account, which aims to make people more secure and to make Ormain the world's largest security group.
Aboudi told the newspaper that he learned piracy when he was 10 years old and that he was working from his friend, and they were now working together at Ourmine.