
Note: The information within this article is for educational purposes only. It is only meant to help instruct people to secure their accounts on the listed providers that will be named within.
It is no secret that any kind of service has its vulnerabilities, especially cell phones. What many may not realize is just how vulnerable some of the devices and services we use every single day really are. This is especially true when we are talking about voicemail systems. Every single day we all receive calls on our cell phones. Many of them go unanswered if you are like me. When the call goes unanswered or we hit ignore the voicemail picks up, the person leaves a message that we check later.
One thing I am sure a lot of people don’t think about is where those voicemails actually reside. I bet the average user probably thinks the initial voicemail is stored on his or her cell phone directly. Obviously this is not the case. The voicemail system needs something to verify each person, so they simply use the cell phone number to identify/verify each person and their corresponding voicemail inbox. This brings me to the point where I found this particular vulnerability. When we check our voicemails we usually just hit a speed dial number to call and access our voicemail. Then immediately as soon as you’re connected it proceeds to tell you how many new messages you have. People tend to believe as long as their cell phone is in their possession their voicemails are safe. What if I were to tell you that all I would need to hack your voicemail is your cell phone number? I would not need any other information.
A simple question led me to figuring out this particular vulnerability around 10 years ago. I asked myself if the voicemail system only uses the cellphone number to identify each mailbox and drop the caller directly into their voicemail inbox… What would stop someone from spoofing their number to a target’s number then calling their target number and ending up in the targets voicemail inbox?
Could it really be that simple? I gave it a try, I targeted another cellphone line (owned by me of course). I changed my current number to my other line via software, I called my other line and bingo… I hear “You have 4 messages” I skipped passed the messages to realize I still had access to the administrative end of the voicemail. I could change my greeting, I could delete or change anything I could as if I were calling directly from that cellphone. I then attempted (with permission from the people) on lines from all other carriers. The carriers that are vulnerable to this simple exploit are: AT&T, Sprint, and various 3rd party carriers.
I figured this out ten years ago in just a few minutes of boredom. These kinds of simple hacks have been around since landline voicemails, so understand a good amount of people know about this problem and it has not been fixed in all this time. Scary thought. All that is required for this to work is:
1.)You have your targets cellphone number
2.)Your targets cellphone is provided by one of the aforementioned carriers
3.)Software to fake your number, app, or website.
4.)The call to your target cellphone is not answered. If the call is answered it will go through and your call will be connected as normal. Either it has to ring until it hits the voicemail, or the ignore button is hit.. as long as its not answered.
Once you have the software/app/website ready you will see an area to place the number you want to appear as. In that space type in the target cellphone number. You will see a space to enter the number to call, once again enter your targets number.
Here are the steps in order to carry it out in case it’s not obvious:
1.) Make sure the target cell phone number is provided by either Sprint, AT&T, and some 3rd party providers. If you are not sure who the target cell phone number is provided by simply perform a reverse number lookup. It will list the provider:

2.) Make sure your call will not be answered on the target phone. In order for this to work your call cant be answered. Your call must be redirected to voicemail in order to fool the voicemail system into thinking you are the owner of the inbox. Ways someone might do this is call when the target’s cell phone will be off, late at night for example. If the target sees the phone while its ringing they will become immediately suspicious, after all it’s not every day someone receives a call from their-selves…
3.) Spoof your cell phone number as the targets cell phone number using either software, an app, or a website:
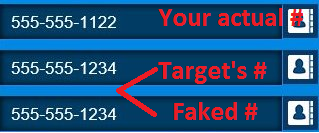
The example above is assuming you are using one of the many websites to fake your number. On these websites they need to know your actual number to route the call because once you enter your info they will give you a toll free number to place the call. Even considering the extra steps necessitated by using such a site this method to access the voicemails will still work. I cant vouch for certain sites because I used software to achieve the same results. I did make an attempt with the most popular website for faking caller id to make sure it would achieve the same results I have when using software and it did in fact work. I’d imagine it all depends on how they handle the call.
Conclusion: Simply applying a lock screen password, fingerprint, or facial recognition security to your cell phone is not enough. You may do such and feel as though everything involving your cell phone is protected which isn’t true at all as you can see from this one example. This method doesn’t just give you access to the voicemail messages, the attacker will also be able to change your greeting to his or her choosing… I mean it could be mighty inconvenient for a well known drug dealer to have their greeting be changed to a police dept. detective greeting. They can wipe out your voicemail contents as well.
To protect yourself: Depending on the provider while you are in your own voicemail inbox you can access the settings to add an additional pin number. If you have that option set a pin number immediately, it will stop this specific method. Just know if you use the affected providers that option is not on by default, you have to manually do it in the voicemail settings.
Find me on:
https://twitter.com/Retroact1ve
http://www.medium.com/@Retroact1ve
https://www.minds.com/Retroact1ve
Hi! I am a robot. I just upvoted you! I found similar content that readers might be interested in:
https://medium.com/@Retroact1ve/note-the-information-within-this-article-is-for-educational-purposes-only-a4b4678f2f35
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
This is a great read. I never thought about where my voicemail resides... I have to honest, I thought they kept them on my phone.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thanks for the kind words. Yes when someone leaves a voicemail initially it resides on the providers systems and not the phone. However people have visual voicemail apps, and other voicemail apps that may copy over the voicemails to the phone. However, the original is on the provider's side. I suggest even if you have a carrier I do not mention to try it on their own phones either with a landline & website, or another cell phone line to make sure they are not vulnerable.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Please only use the #introduceyourself tag for actual introductions - not doing so might result in you getting flagged - I have seen it happen. Will check you out on Twitter!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Oh ok I didn't realize I couldn't use whatever tags I wanted. I'll pay attention to that next time thanks. See you on twitter, and thanks for heads up.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
No problem. All the best!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Im familiar with the spoofing sites and apps, but what software do you use to do it?
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit