USB or Universal Serial Bus was not designed with security in mind. Windows, Linux and OS X basically trust anything plugged in USB port. If a hacker has a very short, but private time with your laptop, this attack vector becomes very feasible. Before actual security threats, let's analyze how USB works in general.
Every USB device has a controller chip and memory storage for firmware, both invisible to the user. Only mass storage is visible to the user. Following picture shows it on a flash drive.
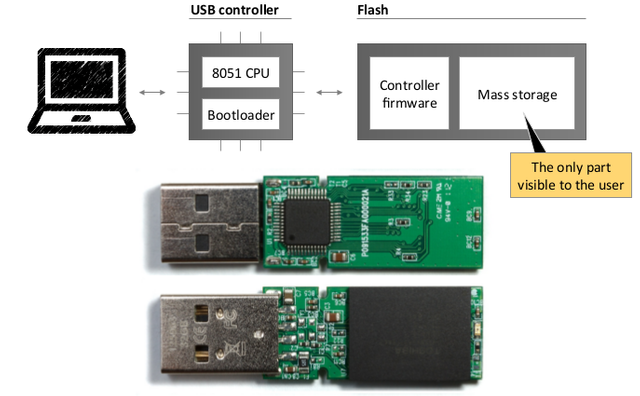
When USB device is plugged into the computer, the chip executes firmware code. On a legit flash drive, firmware is programmed to first register itself as some device (simply by sending a number, no questions asked) and load a driver to be installed. However, the firmware can be programmed to do a vast majority of stuff which makes a big range of possible USB attacks. Most devices are trusted by default – all user interaction needed for a keyboard is plugging it in. Also, it's worth noting that USB device can legitimately register as more than 1 type of device. It can also stop being 1 type and become another by deregistering.
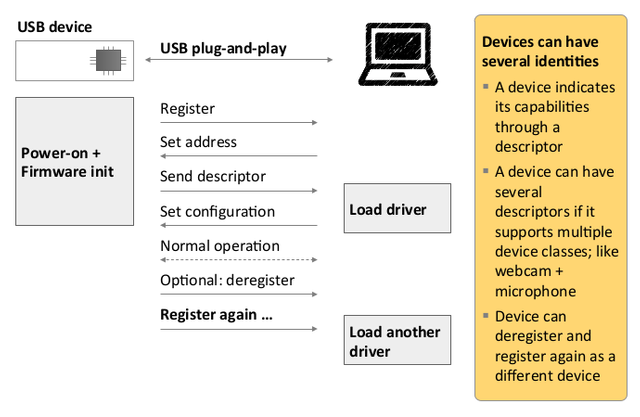
Also, each operating system can be identified because of configuration information that is sent back to the chip. This makes the USB globally a widespread security threat targeting all major operating systems.Here’s a partial list of realistic dangers, starting with the most popular and ending with the most badass.
Human Interface Device (HID)
We’re talking about keyboards, mice and other devices that are controlled by the user. Keyboards work as soon as you plug them in, which is very attractive to hackers. You might’ve heard of RubberDucky or BashBunny, devices that look like regular USB sticks, but they actually emulate pre-programmed keystrokes when plugged in, no questions asked. Such devices can download and execute a backdoor in 20 seconds. If you don’t like Ducky’s or Bunny’s price, I suggest using your Android phone or Arduino Digispark (less than $1.5). These are also awesome for pranking people in PC labs (or office or whatever), e.g. it can make the screen rotate around endlessly while playing 'never gonna give you up...' on youtube :D.
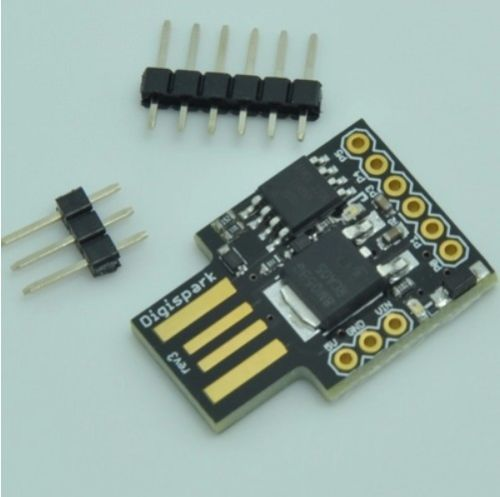
If you lock your computer, those attacks are prevented, but following attack can do significant damage on a locked computer.
Ethernet device
I love this attack! My hero‘s PoisonTap is RasperryPi Zero device ($5) which emulates an Ethernet device over USB. PoisonTap produces a cascading effect by exploiting the existing trust in various mechanisms of a machine and network, including USB/Thunderbolt, DHCP, DNS, and HTTP, to produce a snowball effect of information exfiltration, network access and installation of semi-permanent backdoors. This type of attack works because computers automatically perform a DHCP request upon recognizing a new network card. Such a malicious device assigns an IP address to the computer and tells it that every single IP address in existence is inside of its local area network (you need to send a packet? I got you bro :D). From now on, when an infected computer sends a packet to any IP address, it will go through malicious USB-Ethernet device because LAN over WAN routing priority. From that point on, it is possible to poison a victim’s cache, DNS table, steal cookies and do more.

Android phones seem to be the simplest tools to perform this attack by taking advantage of a USB-Ethernet service, possibly by “charging” your phone on someone’s computer. Check out the demo by Samy.
Killer
Looks like a USB stick, but packs a few capacitors that charge through the USB port and then release the charge at 200+V with the goal of frying the motherboard. Some new computers, e.g. Apple Macbooks, have hardware mitigation for this type of attack, but most computers’ motherboards can be destroyed with a USB Killer. Not for pranking though.
Infecting the World
This is a very time-consuming task, but reverse engineering the firmware is very powerful. Not only can we make our own rubber ducky out of regular flash drive (github), we can also change the drivers that get installed on the connected computer. An unpleasant scenario goes like this – someone patches the firmware to install malicious drivers which turn the computer in a spreading point. Each (compatible) USB plugged into the infected computer gets “firmware update” and becomes a spreading stick, resembling STDs perfectly. Combining this idea with identifying the OS and choosing the right payload, every major operating system is at danger. I will write much more about this in a separate article. Luckily for us, wikileaks revealed how CIA put this idea to life with Brutal Kangaroo (not this kangaroo) and Drifting Deadline. Also, some folks at Blackhat conference also shared their ideas so stay tuned for that.
How to secure yourself?
Most researchers talk about code signing and integrity protection for firmware updates but it’s not coming very soon. I recommend using software that disables your USB ports when you lock the screen so you can take your break without worries. As far as malicious firmware and drivers are concerned, there’s no feasible and easy patch so be careful what you insert into your port (reminds me of mother-daughter advice LOL).
A bit more formal version was also posted on https://www.deepdotweb.com/2017/06/23/fundamental-security-flaws-in-usb/
Hi! I am a robot. I just upvoted you! I found similar content that readers might be interested in:
https://www.deepdotweb.com/2017/06/23/fundamental-security-flaws-in-usb/
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit