Katyusha Scanner — Telegram-based Fully Automated SQL Injection Tool
A new powerful hacking tool recently introduced in an underground forum is making rounds these days, allowing anyone to rapidly conduct website scans for SQL injection flaws on a massive scale — all controlled from a smartphone using the Telegram messaging application.
Dubbed Katyusha Scanner, the fully automated powerful SQLi vulnerability scanner was first surfaced in April this year when a Russian-speaking individual published it on a popular hacking forum.
Researchers at Recorded Future's Insikt Group threat intelligence division found this tool for sale on an underground hacking forum for just $500. Users can even rent the Katyusha Scanner tool for $200.
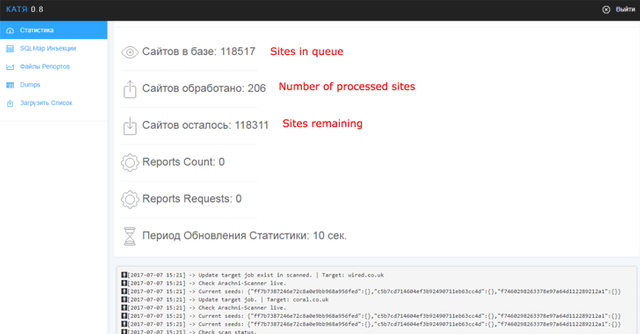
According to the researchers, Katyusha Scanner is a web-based tool that's a combination of **Arachni Scanner **and a basic SQL Injection exploitation tool that allows users to automatically identify SQLi vulnerable sites and then exploits it to take over its databases.
Arachni is an open source vulnerability scanning tool aimed towards helping users evaluate the security of their web applications.
What makes this tool stand out of line is its 'Infrastructure-as-a-Service' model.
Remotely Control Hacking Tool Via Telegram
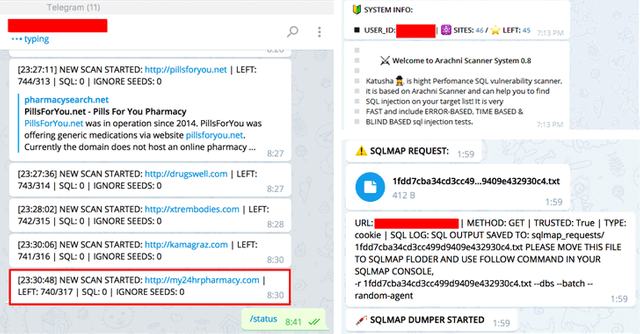
Katyusha Scanner is abusing the Telegram messaging application to control its operations, such as sending and receiving commands.
The Katyusha Scanner tool is quite easy to setup and use, allowing anyone to conduct large-scale penetration attacks against a large number of targeted websites simultaneously with the mere use of their smartphones.
The Pro version of the tool not just identifies vulnerable websites, but also allows hackers to establish a "strong foothold within vulnerable web servers" and automatically extract "privileged information such as login credentials."
Once the scan is complete, Katyusha Scanner sends a text message to the criminals with the vulnerable site name, its Alexa web ratings, helping criminals identify popular websites that would likely be more profitable for them to attack, and the number of databases.
The criminals, even with no technical knowledge, can download any exfiltrated data available by just clicking on their smartphones to issue commands.
Katyusha Scanner also allows for the automatic dumping of databases and can be used on both Linux as well as Windows machines.
"The availability of a highly robust and inexpensive tool...Katyusha Scanner to online criminals with limited technical skills will only intensify the compromised data problem experienced by various businesses, highlighting the importance of regular infrastructure security audits," researchers at Recorded Future wrote.
Many buyers praised the quality of the tool on the black market site, one of the satisfied customers who got immediate success in obtaining access to eight web servers wrote:
"Excellent support! The seller has configured the software for my server, which was failing before, however, right now it flies divinely! I highly recommend the software, and it has found eight SQL vulnerabilities in half a day, great automation of the routine. Very grateful to the seller."
Another wrote: "The author has helped with the product setup after the purchase, and (Katyusha) has immediately found SQL vulnerability. Thank you for the great product."
Initially, Katyusha Scanner was sold for $500, but due to unexpectedly high demand, a light version of the tool with slightly limited functionality was released on May 10, 2017, at just $250.
With the release of the most recent Katyusha 0.8 Pro update at the end of June, the author also made the scanner available for rent at $200 per month for the first time.