Hello fellows. How are you all?
.jpg)

What is the Hash Rate?
The number of hashes created per second is referred to as hashrate. It is the definition or literal meaning of hashrate. If we examine it further, we can conclude that it is a measure of the number of calculations performed in a second, as hash is derived after solving cryptographic puzzles. Another way to look at it is in terms of the computational power of the mining hardware.
The hash rate was invented when Bitcoin was born, Today, all of the world's cryptocurrencies are mined using the hash rate process. This whole process is called proof of work consensus. The more technology a miner has, the more hash rate power he has, The miner has more chances to complete the block and keeping the long-awaited reward.
A miner can measure in the network what is hash rate, There are many lucrative mining calculators available on the internet from which we can easily estimate the hash rate. Blockchain networks with higher hash rates have higher security. In other words, we can say that the data contained in them is secure.
If we talk about numbers, we can estimate how complex the mining of cryptocurrency is. Similarly, if we look at Bitcoin, it takes ten minutes to mine one block, due to the complicated operations and high energy required for its mining. The blockchain is very secure. Because of hash rate, the minors try to find the correct hash. A fall in hashrate make a blockchain more susceptible to the attacks

The Merkle Tree
Now I am going to make a Merkel tree in front of you according to the method given by the teacher.Transaction (tree leaves): Steem1; Steem2; Steem3; Steem4; Steem5; Steem6; Steem7; Steem8.
Tree leaves
.jpg)
Steem1
B97D34F73C7742D805111D1243BD5BF396BDB43122C3755081A3325D613B9803
.jpg)
steem2
B5F6EE9E3D63B48E00096DE32C8E1FF8EBB94D50337624A073534B995B2F6226
.jpg)
steem3
419F6C383AC9F89E5653BA37FA88F2588E969A2886A0B84E51981159B59D82A0
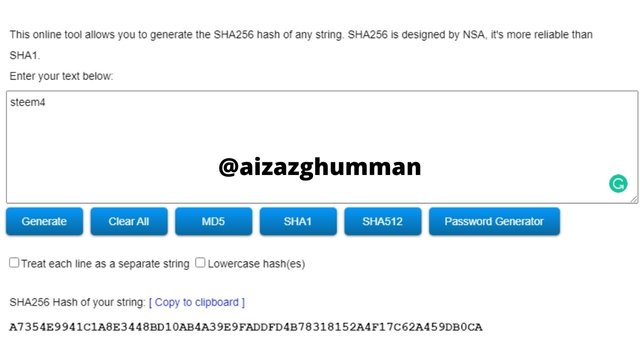
steem4
A7354E9941C1A8E3448BD10AB4A39E9FADDFD4B78318152A4F17C62A459DB0CA
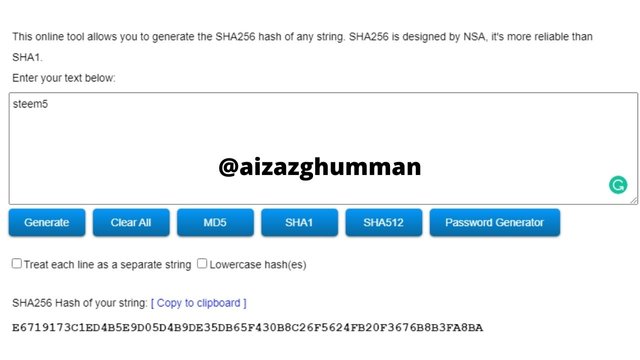
steem5
E6719173C1ED4B5E9D05D4B9DE35DB65F430B8C26F5624FB20F3676B8B3FA8BA
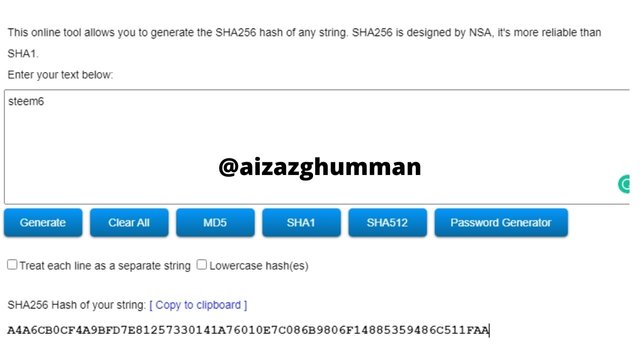
steem6
A4A6CB0CF4A9BFD7E81257330141A76010E7C086B9806F14885359486C511FAA
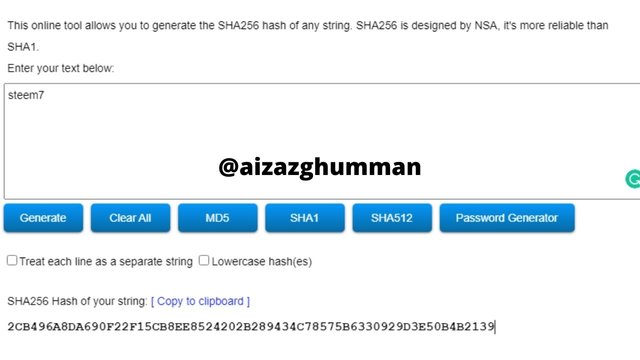
steem7
2CB496A8DA690F22F15CB8EE8524202B289434C78575B6330929D3E50B4B2139
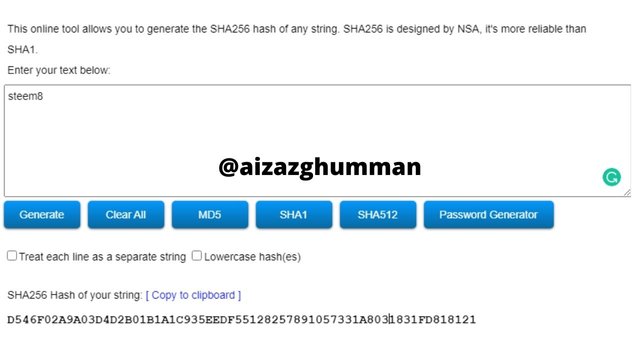
steem8
D546F02A9A03D4D2B01B1A1C935EEDF55128257891057331A8031831FD818121
First level branches
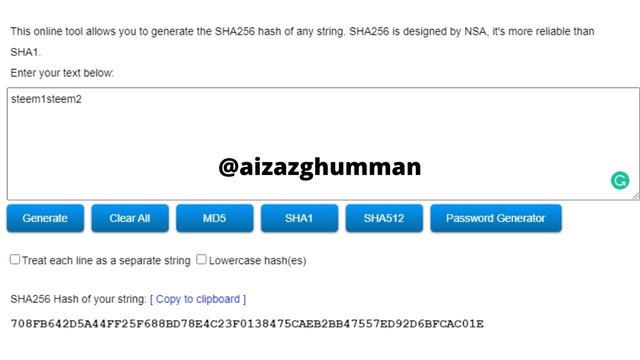
steem1steem2
708FB642D5A44FF25F688BD78E4C23F0138475CAEB2BB47557ED92D6BFCAC01E
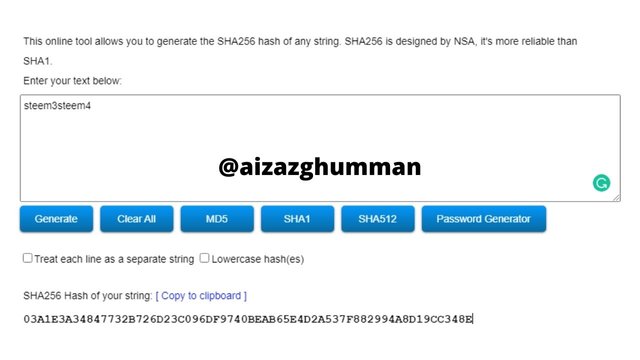
steem3steem4
03A1E3A34847732B726D23C096DF9740BEAB65E4D2A537F882994A8D19CC348E
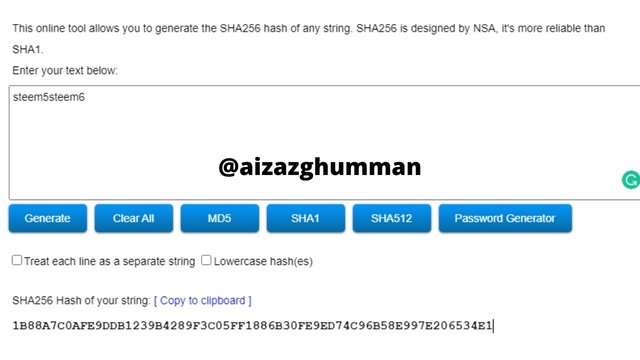
steem5steem6
1B88A7C0AFE9DDB1239B4289F3C05FF1886B30FE9ED74C96B58E997E206534E1
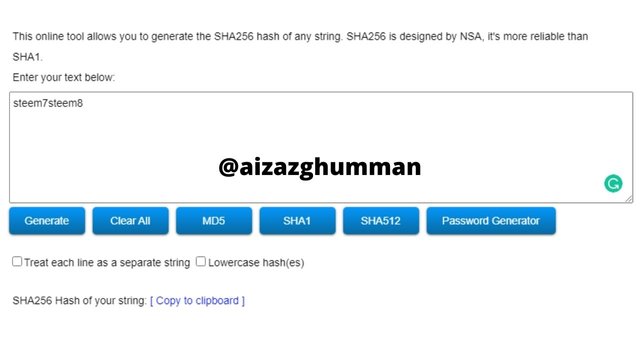
steem7steem8
C856FD0E48434FD57974AF89FFA957B0F51D2D2BFF2141C950DB1091A5C52AE3
Second level branches
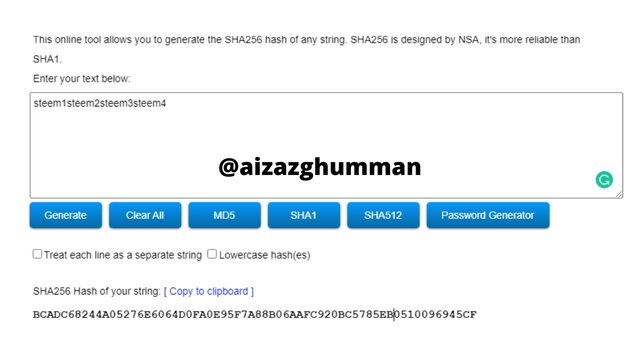
steem1steem2steem3steem4
BCADC68244A05276E6064D0FA0E95F7A88B06AAFC920BC5785EB0510096945CF
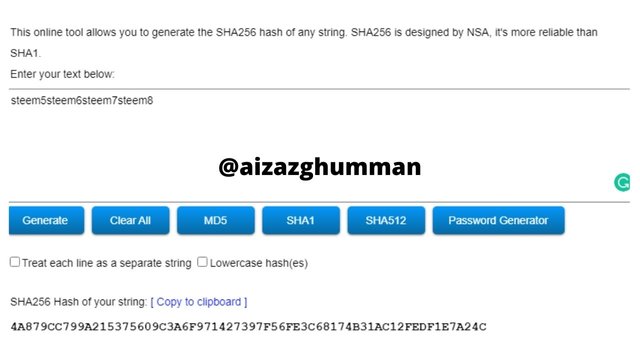
steem5steem6steem7steem8
4A879CC799A215375609C3A6F971427397F56FE3C68174B31AC12FEDF1E7A24C
Tree root
we already generate the tree leaf and the first and second levels of branches. So here we are going to generate the root of the Merkle tree.
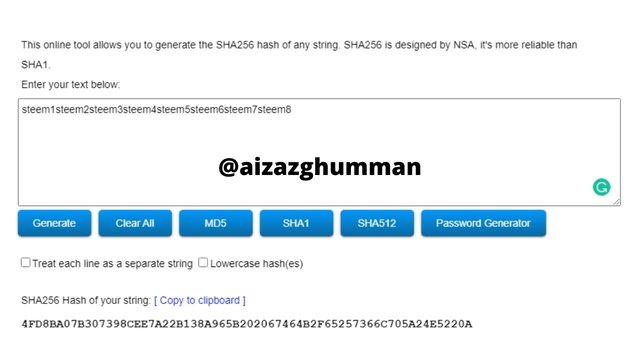
steem1steem2steem3steem4steem5steem6steem7steem8
4FD8BA07B307398CEE7A22B138A965B202067464B2F65257366C705A24E5220A
With the help of my editing program, I create my Merkle tree, copying each Hash corresponding to its message. And this is the result:
.jpg)

How to check if Steem6 is included in the Merkle Tree.
To check if Steem6 is included in the Merkle Tree (Root hash), a user needs to having access to the following...
- Hash of Steem5
- Hash of Steem7Steem8
- Hash of Steem1Steem2Steem3Steem4
.jpg)
Now, to start verifying Steem6, we should know the node connected to Steem6 or we can say the brother hash which is Steem5
Calculate the hash of Steem5 and Steem6 and it will give us the hash Steem5Steem6, Since the Hash of Steem7Steem8 is known so calculate the hash of Steem5Steem6 and Steem7Steem8 which will give the hash Steem5Steem6Steem7Steem8
Now, As we have already known about the Steem1Steem2Steem3Steem4 hash so calculate the hash of Steem1Steem2Steem3Steem4 and Steem5Steem6Steem7Steem8 and it will give us the Root Hash of Merkle Tree which is Steem1Steem2Steem3Steem4Steem5Steem6Steem7Steem8

Creating our own Markle Tree from its leaves.
Tree leaves
.png)
SCA1
13E0A04BB0E669E1C638DBE3A704743F99F162B25245E4D8C064D35BA38FA8C8
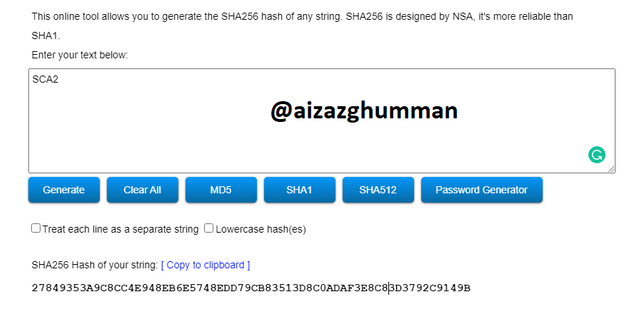
SCA2
27849353A9C8CC4E948EB6E5748EDD79CB83513D8C0ADAF3E8C83D3792C9149B
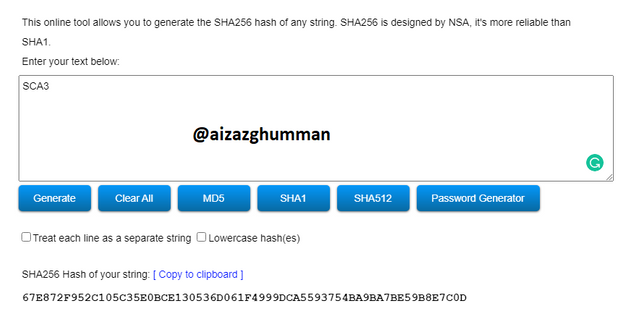
SCA3
67E872F952C105C35E0BCE130536D061F4999DCA5593754BA9BA7BE59B8E7C0D
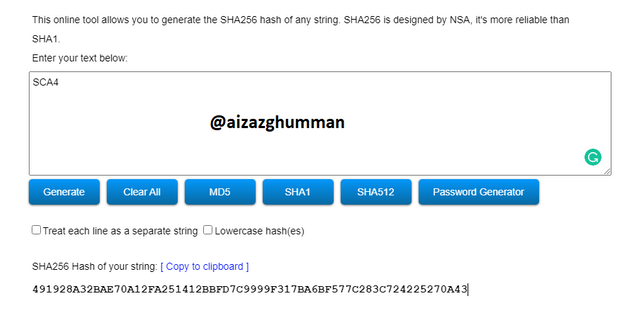
SCA4
491928A32BAE70A12FA251412BBFD7C9999F317BA6BF577C283C724225270A43
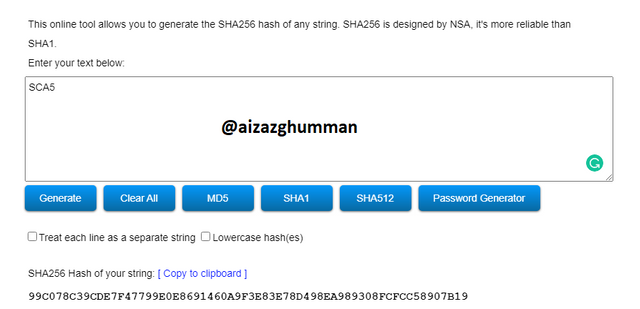
SCA5
99C078C39CDE7F47799E0E8691460A9F3E83E78D498EA989308FCFCC58907B19
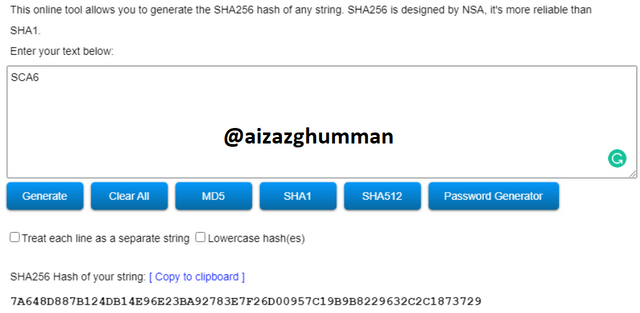
SCA6
7A648D887B124DB14E96E23BA92783E7F26D00957C19B9B8229632C2C1873729
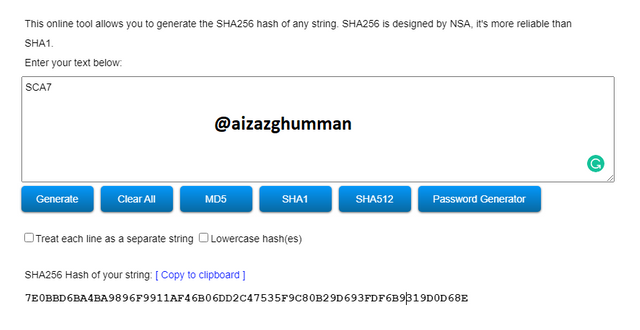
SCA7
7E0BBD6BA4BA9896F9911AF46B06DD2C47535F9C80B29D693FDF6B9319D0D68E
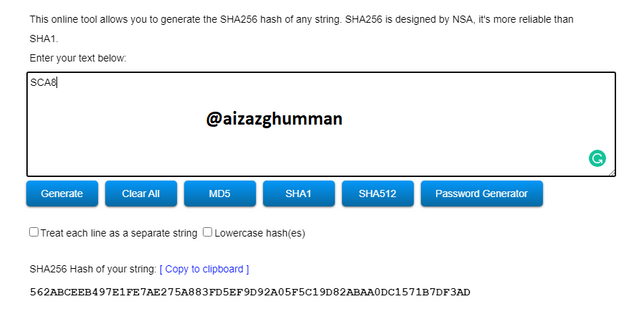
SCA8
562ABCEEB497E1FE7AE275A883FD5EF9D92A05F5C19D82ABAA0DC1571B7DF3AD
First level branches

SCA1SCA2
91B09BBA815748166FB36413342C7E4E7E809F4BAC538C0418841A4476B527EF
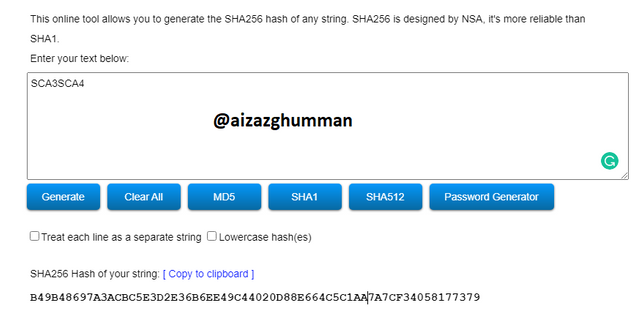
SCA3SCA4
B49B48697A3ACBC5E3D2E36B6EE49C44020D88E664C5C1AA7A7CF34058177379
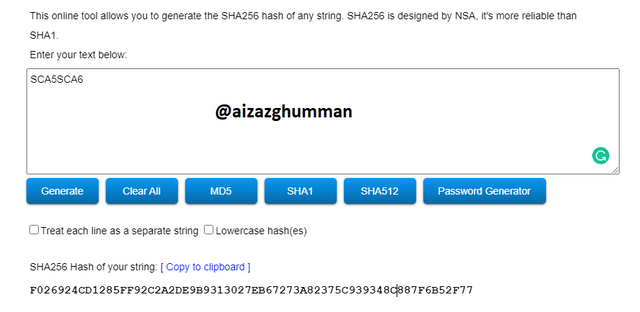
SCA5SCA6
F026924CD1285FF92C2A2DE9B9313027EB67273A82375C939348C887F6B52F77
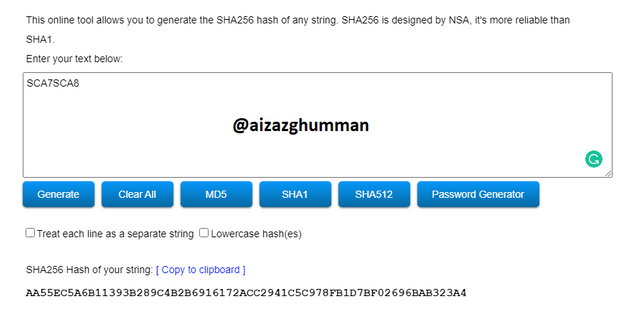
SCA7SCA8
AA55EC5A6B11393B289C4B2B6916172ACC2941C5C978FB1D7BF02696BAB323A4
Second level branches
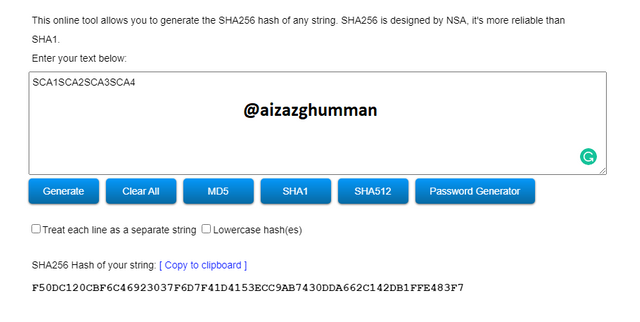
SCA1SCA2SCA3SCA4
F50DC120CBF6C46923037F6D7F41D4153ECC9AB7430DDA662C142DB1FFE483F7
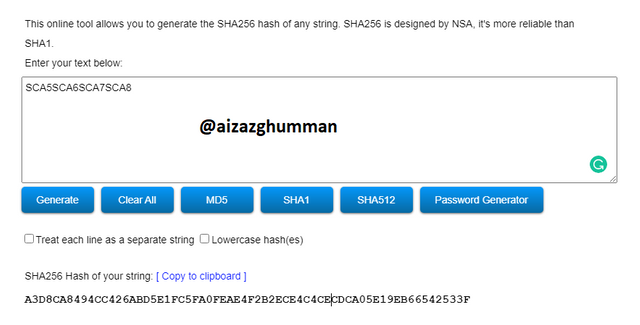
SCA5SCA6SCA7SCA8
A3D8CA8494CC426ABD5E1FC5FA0FEAE4F2B2ECE4C4CECDCA05E19EB66542533F
Tree root
we already generate the tree leaf and the first and second levels of branches. So here we are going to generate the root of the Merkle tree.
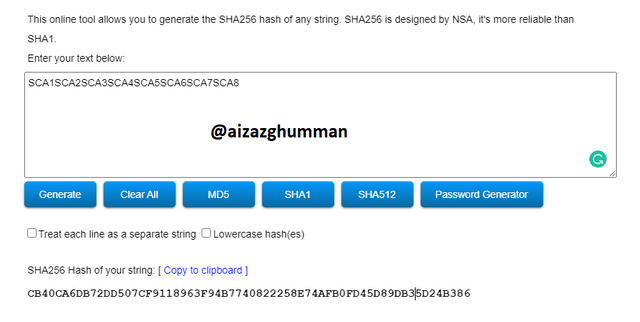
SCA1SCA2SCA3SCA4SCA5SCA6SCA7SCA8
CB40CA6DB72DD507CF9118963F94B7740822258E74AFB0FD45D89DB35D24B386
With the help of my editing program, I create my Merkle tree
.png)
##
we have seen in the above questions that the Merkle tree was formed only with an even number of leaves at every level. Even at the first-level branches, second-level branches, or leaves, all should be even. But if we have an Odd number of leaves, then? then the brother leaves will form a new leave with its own name.
Like, If we have an odd number of leaves like SCA1,SCA2,SCA3,SCA4,SCA5,SCA6,SCA7 then the last leave here is SCA7, and to make it an even number of leaves, there will be a new leave name SCA7 to make it even.
As we can see in the following image, when the hash of one of the base leaves is missing, it is impossible to continue with the shaping of the tree and reach the Root Hash.
.png)
So we proceed to duplicate"SCA7" as its partner and can continue with the process.
.png)
Similarly, we have created a duplicate hash with the help of SCA7 and now we repeat the forward hash with the help of SH256
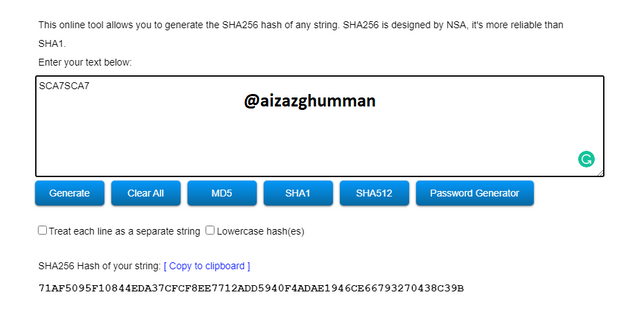
SCA7SCA7
71AF5095F10844EDA37CFCF8EE7712ADD5940F4ADAE1946CE66793270438C39B
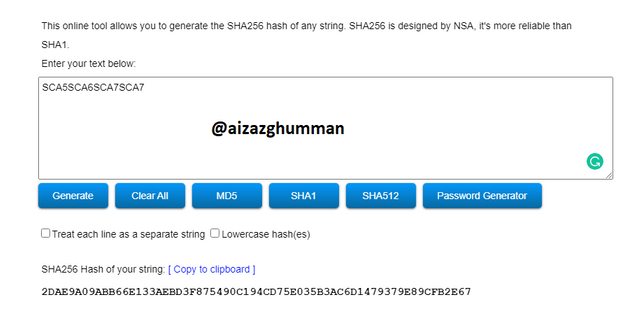
SCA5SCA6SCA7SCA7
2DAE9A09ABB66E133AEBD3F875490C194CD75E035B3AC6D1479379E89CFB2E67
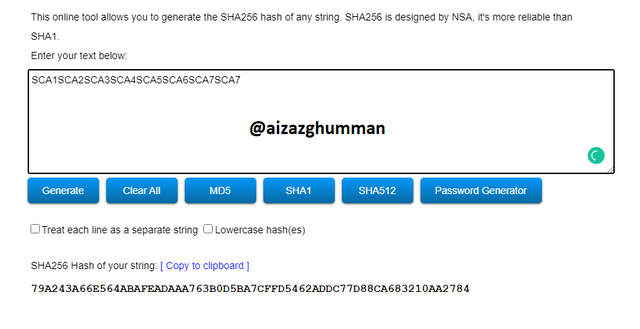
SCA1SCA2SCA3SCA4SCA5SCA6SCA7SCA7
79A243A66E564ABAFEADAAA763B0D5BA7CFFD5462ADDC77D88CA683210AA2784
.png)
so the Merkle tree become like this SCA1SCA2SCA3SCA4SCA5SCA6SCA7SCA7

Conclusion
It has been great learning from professor @pelon53, his lectures are always taught us something different every week. In this week's Homework task, we learned about Hash Rate, Merkle Tree, and how Merkle Tree can be created even if there are an odd number of leaves.
I hope to continue learning more from Professor in the coming weeks.
.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit