Hello Steemians !!
Today I'm going to make my Steemit Crypto Academy Homework task by professor @pelon53 Lesson that talking about Hash and Cryptography. A new and good lesson for me. I will try to discuss it, i hope my knowledge is more developed about Hash and Cryptography.
Explain what does the resistance to collision mean? And what does resistance to preimage mean?
Hash is a tool in the blockchain system that is used to process and manipulate input data into output by providing algorithms that are difficult to guess. The hash function plays an important role in maintaining the security of transaction data in the blockchain system in order to make users have high privacy. Hashes have special characteristics that support their work and operations such as immutable, non-repeatable, fixed length, safe and efficient. This is all intended so that everything that is expected is achieved and runs smoothly.
Resistance to Collision
One of the hash functions is resistance to collision which means it is small chance to equal output from different inputs. This has been well anticipated by the hash by processing each different input and producing a different output by relying on a fixed-length algorithm even though the input length is different. Hashes are created and trusted to overcome any system errors or hack.
Based on the results and testing the possibility of a collision is small and still efective. But it is not impossible to happen in a very long time. Because the output is finite while the input is infinite. But in general the hash function works well and is suitable as a tool to maintain data security in the blockchain system because of its resistance to collision.
Resistance to Preimage
Another hash function is resistance to preimage which means it is small chance to know or find the input based on or by understanding the output. This has been well anticipated by hashes by processing each input by providing and manipulating data into output by relying on algorithms that cannot be guessed or learned. Hashes are created and trusted to deal with hacks that might be done by criminals.
Based on the results and testing the resistance to preimage is still effective. Determination of input from output is almost impossible to complete. With all its uniqueness and main functions, hashes have provided a high level of difficulty for criminal behavior that can harm anyone. The hash function works well and is suitable as a tool to maintain data security in blockchain systems due to resistance to preimage.
Resistance to second preimage
One of the other and continuous hash functions is the resistance to second preimage which means it is small chance to know or find the input based on or by understanding the output due to the similarity of the output. This occurs when a collision occurs resulting in the same output from different inputs.
Based on the results and testing the resistance to the second preimage is still effective. This is because the hash function is also collision resistant. If anything happens, the hash can anticipate and eliminate criminal actions that may occur due to system errors. In this case data security is the key that is most concerned and guarded.
Use tronscan and etherscan to verify the hash of the last block and the hash of that transaction. Screenshot is required for checking
To verify the hash of the last block and the hash of the last transaction using Tronscan. First visit the web https://tronscan.org/#/. On the home page there is a list of blocks and transactions. In the image I marked, select the last block to see more information.
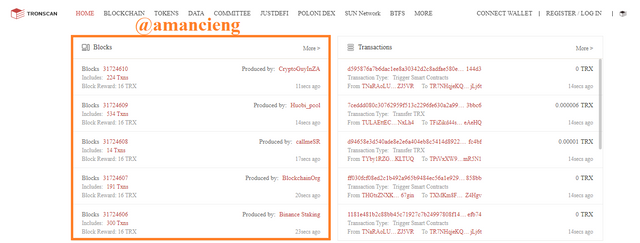
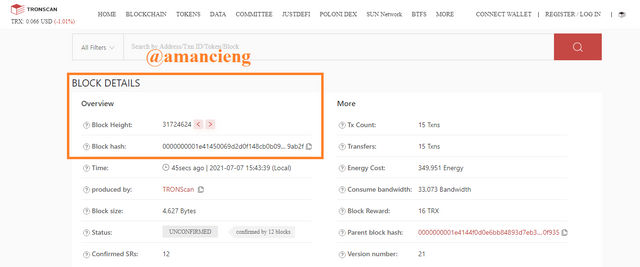
In the image I marked, there is Block Height: 31724624 and Block Hash: 0000000001e41451ff14e10ddfd0f12b09...9ab2f and there is other useful information.
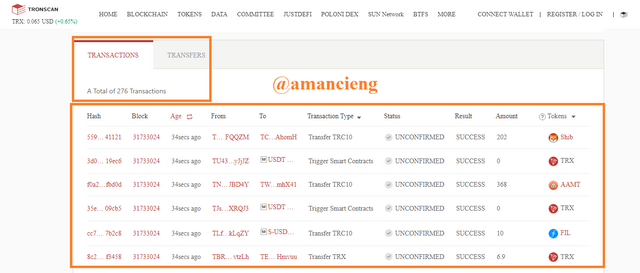
On the page below. In the image I marked, there is total of 276 transctions and details.
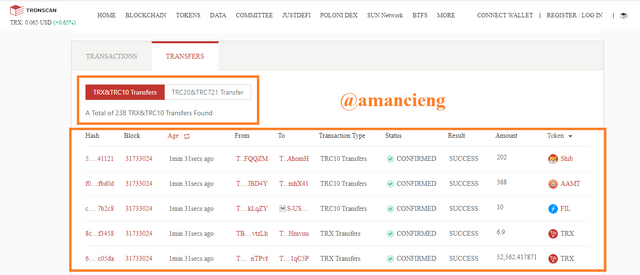
In the image I marked, there is total of 238 TRX & TRC10 transfers and details.
In the image I marked, there is total of 28 TRC20 & TRC721 transfers and details.
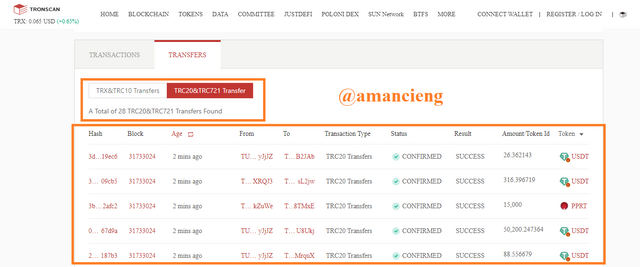
Return to home page. In the image I marked, select the last transaction to see more information.
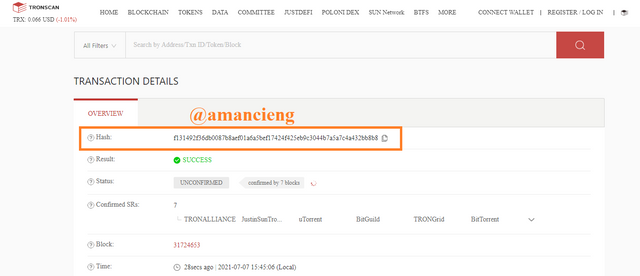
In the image I marked, there is Hash: f1314a1bcb6ab8789a74c6f84e9dafc5110fb513655f43aa9d7576fcaf6bb8b8 and there is other useful information.
To verify the hash of the last block and the hash of the last transaction using Etherscan. Second visit the web https://etherscan.io/. On the home page there is a list of blocks and transactions. In the image i marked, select the last block to see more information.
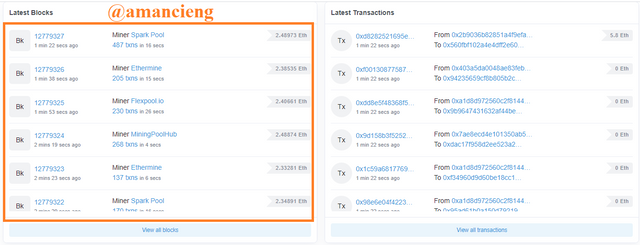
In the image I marked, there is Block Height: 12779380 and and there is other useful information.
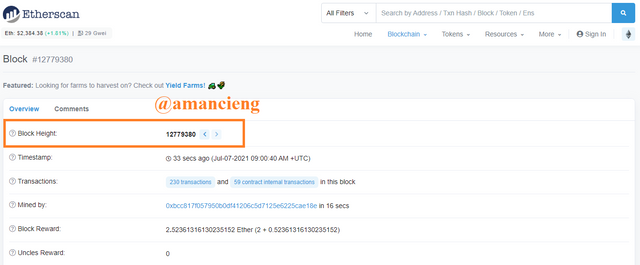
Then scroll the page down. There is Hash: 0xaed7af4aaa9c7ab4fdb8e5fd85b3c3a3fbee6f1422fea45d55dc1bb1faffd8409 and and there is other useful information.
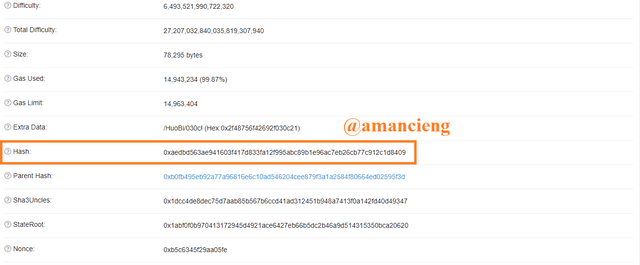
Return to home page. In the image I marked, select the last transaction to see more information.
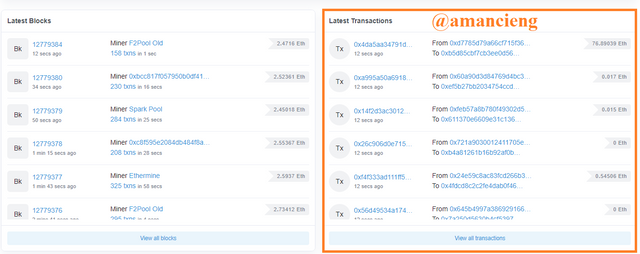
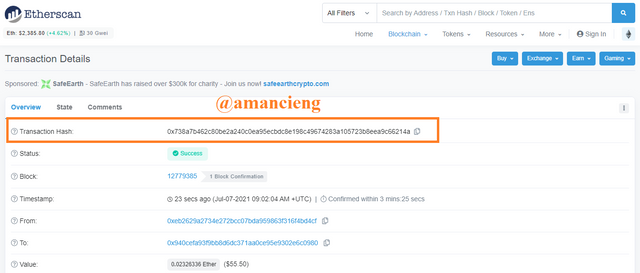
In the image I marked, there is Hash: 0x378c2a22ee84b9bff9a3890e05c845247955d034b453f15fd6275ad37066214a and there is other useful information.
Generate the hash using SHA-256, from the word CryptoAcademy and from cryptoacademy. Screenshot required. Do you see any difference between the two words? Explain
To generate the hash using SHA-256. Visit the web https://passwordsgenerator.net/sha256-hash-generator/.
Do the first example by typing CryptoAcademy. Hash : D03CA34B258E6E0FD06B2070DDE61B50BD4EEF6161A8EDAA4A420C9AE1BEB7F9.
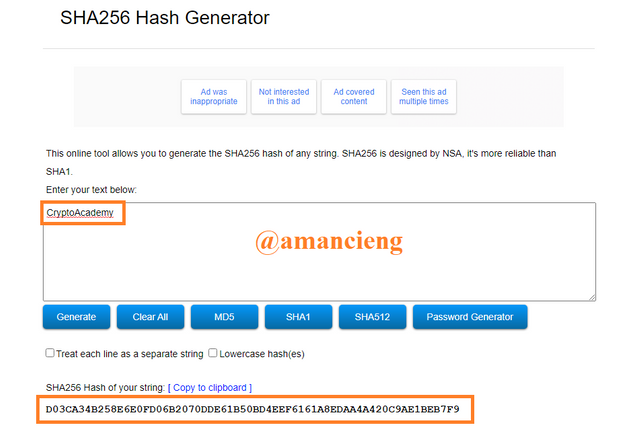
Do the second example by typing cryptoacademy. Hash: 0592F5DD27DC72E675B2AB9C77487A69FAAF84196597FA052EC099C18EE7C4C5.
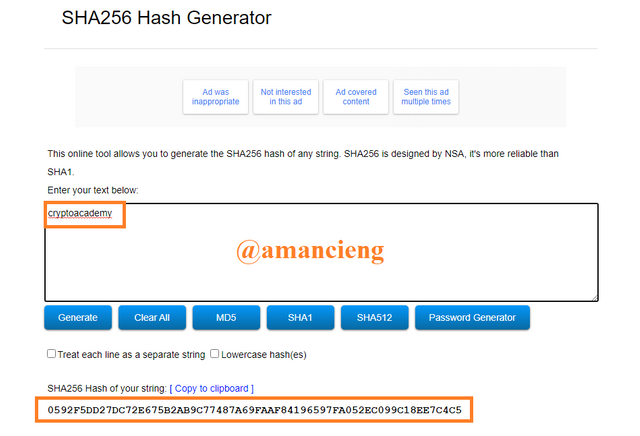
Filling in the two input examples above where there are very simple differences in capital and non-capital letters in the same word proves that the hash processes an algorithm that is immutable, non-repeatable, fixed length, safe and efficient. The implementation of the same word (cryptoacademy) and given the difference in the letters "C" and "A" has proven that any input that differs a little or a lot will still produce different outputs. Hash is highly tested in terms of security and deserves to be used and continues to be developed.
Explain the difference between hash and cryptography
Hash
Hash is an immutable, non-repeatable, fixed length, secure and efficient algorithm. These algorithms are also unpredictable and unlearnable. The purpose and function of a hash is to create and manipulate data so that it is unreadable and hidden so that it can trick anyone who wants to hack. This is intended to make the level of security of the input process until the output reaches the maximum level. It is a very precise and feasible tool to run on the blockchain system to keep all data and transactions secure. The hash on the blockchain for output has a fixed length even if the input length is different.
Cryptography
Cryptography is a science and method that is run and implemented on a blockchain system to provide and maintain a high level of security especially those involved with data and privacy. The purpose and function of cryptography is to reduce errors or damage as much as possible and prevent the involvement of criminals from doing what they want. All processes and things that go in and out of the blockchain system will be monitored and maintained. All things that are confidential and possible to be found and hacked by criminals will be prevented and eliminated as much as possible. Important things such as data, information, passwords, and history will be well hidden so that users are comfortable in accessing anything in the blockchain system.
| Hash | Cryptography |
|---|---|
| Complicating and manipulating data with algorithms | Keeping the entire blockchain system secure |
| Process input into output with algorithms | Manage and hide information |
| Unpredictable and unhackable | Prevent harmful criminal acts |
| Data fixed length | Data length varies |
| Does not require password | Requires password |
| Cannot be changed and repeated | Possible to log in with the same password |
Conclusion
Hash and cryptography are two things that are related and have involvement in terms of maintaining the security of blockchain systems. With the same purpose and different functions, hash and cryptography are expected to be able to make users feel safe and confident to carry out all activities in the cryptocurrency world. These are all meant to protect and keep your data, privacy, passwords, anonymity, history and other important things from being hacked.


El hash de la transacción no coincide con el bloque 31724624 que es el último bloque, en tronscan. En el caso de etherscan tampoco coincide. La pregunta era encontrar el hash del último bloque y el hash de la transacción de ese mismo bloque.
Buen trabajo, sigue adelante.
Recomendaciones:
Leer con detenimiento cada pregunta para dar la respuesta correcta.Calificación: 8.3
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Sorry about that professor, Thank you!!!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit