
Welcome once again to another wonderful episode in the crypto Academy community. Before I present my homework post, I would like to acknowledge the professors and the crypto Academy community for making such an educative lecture possible. Today the topic is all about your favorite concept with blockchain

About Blockchain Cryptography

CryptoGraphy refers to the new modified system which allows people to send and receive messages without any interruption. With cryptography, people can send private messages without any leak from hackers. The system was introduced to enhance privacy when messaging and also to maintain confidentiality. The cryptographic system secures any information or data from the author before it reaches the receiver.
With CryptoGraphy, when two people want to make any transaction, let's assume avagah wants to send private data to Kouba. avagah needs Kouba’s public keys together with his private key to encrypt the data since it could be leaked. Now Kouba would need his private key to decrypt the encrypted data from avagah. Now the message can be disclosed to Kouba since he has decrypted the message.
How the process looks
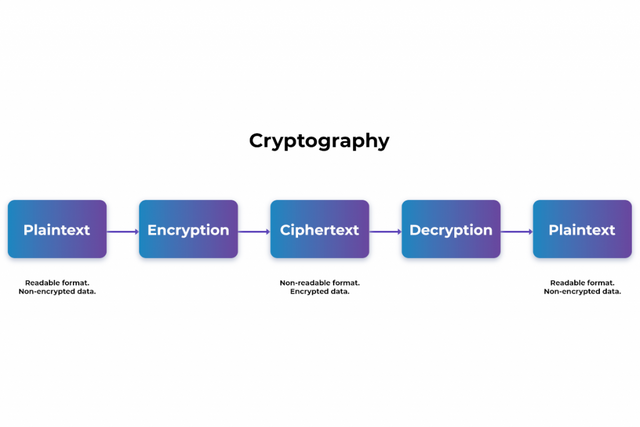
There are different types of blockchain cryptography
Public Cryptography
Private Cryptography
Symmetric Cryptography
Asymmetric Cryptography
Public Cryptography
This type of cryptography involves different keys from both the receiver and the sender. With this type of cryptography, the sender needs the public key to encrypt the message he or she wants to send. But the receiver on the other hand needs the private key to decrypt the encrypted message from the receiver to be able to understand the message. Hence with the public key cryptography, two different keys are needed for the process to be successful.
Let's take a typical example. When avagah wants to send an anonymous message to Kouba, avagah needs Kouba’s public key to encrypt the message before he sends it. However, Kouba will also require his private key to be able to decrypt the message avagah sent. This is basically how the Public CryptoGraphy works.
How the process looks
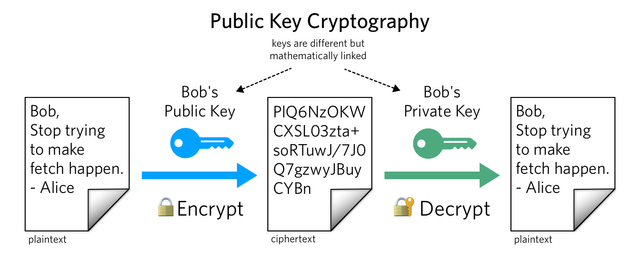
Purpose of Public CryptoGraphy
- Public cryptography ensures anonymity: since the system requires the public and private keys to encrypt the message from the sender and to decrypt the message by the receiver respectively, the message is kept anonymous to the public. No one without any of the keys can see the message.
Private Cryptography
Unlike public key cryptography which requires two different keys to complete the transition, private key cryptography requires just one secret key which is used by the sender to encrypt the message and the receiver to decrypt the message.
Let's assume avagah wants to send a private message to Kouba, avagah and Kouba must generate a secret key which would be used by avagah to encrypt the message before Kouba uses the same secret key to decrypt the message from avagah. This is basically how the Private cryptography works.
Structure of the Private CryptoGraphy
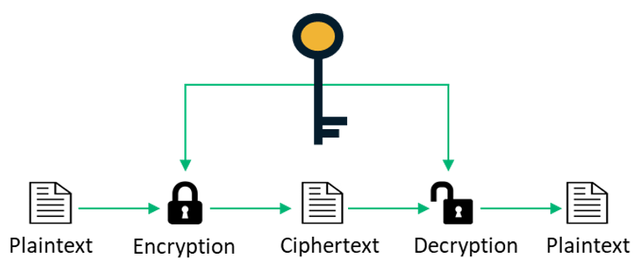
Purpose of private key cryptography
- Enhance Anonymity: with this type of cryptography, only one secret key is required to complete the transaction. Hence, anyone without the key can't decrypt the message in any way.

Important of Blockchain Cryptography

Enhance Anonymity: with this feature in blockchain technology, users are guaranteed their privacy. Everyone would like to have private and secure conversations and transactions. That’s why I think blockchain cryptography is one of the most important things that happened to blockchain technology. With this feature, two users can make private transactions and conversations without being tracked.
Ensures Security: With blockchain cryptography, users are also guaranteed secured transactions. The keys are generated with cryptographic alphanumeric hash functions which would be very different for scammers are fraudsters to compromise. Moreover, looking at the process of the cryptographic hash function, there’s no probability that any key could be generated twice.
Confidentiality: From the above-listed points, there’s no doubt that blockchain cryptography ensures confidentiality.

Do you think that the existence of the blockchain would be possible without this concept? Is there an alternative or similar term?

From my knowledge, I don’t think blockchain could exist without cryptography. The reason why I’m saying this is because blockchain is characterized by its decentralized nature and high security. However, without cryptography, numerous passwords could be easily compromised.
Moreover, without cryptography, wallet addresses and private keys wouldn’t also exist as well and blockchain would be very difficult to exist. I don’t know how blockchain could manage without the existence of cryptography. Blockchain cannot exist without cryptography.
Probably, blockchain could exist without cryptography. But this current blockchain we are all using now would never exist without cryptography. Probably, it would be something entirely different from the current blockchain.

Do you think it is possible to improve this term in some way? Explain us how

To my knowledge, blockchain cryptography is a very advanced technology that could be maintained for a very long time without any significant amendments. Currently, I see everything working perfectly with blockchain cryptography.
However, for further improvements, I still think blockchain cryptography could use some features about the users to generate these keys. A feature like fingerprints and face recognition could be used to generate these keys.
For instance, steem keys are generated by the cryptographic hash function technology. However, when the keys generation is backed by a fingerprint or face recognition, no account could be compromised since it would require these features. Introducing this feature could be a very massive change.
In any case, blockchain cryptography is my favorite feature of blockchain technology.
Very detailed explanation on blockchain...I’ve learnt a lot from this article
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thanks brother
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
I agree with your statement about securities on blockchain.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit