3a) What is a Cryptocurrency?
b) What is Cryptography and how does it make cryptocurrencies secure?
c) Explore the Steem Genesis Block and Sign in as proof of completion.
a) What is a Cryptocurrency?
Cryptocurrency is purely a digital currency (not physical) that will be used in transactions related to the exchange of products and services.
It works on a decentralized block chain technology that gives each owner total management of their tokens without interfering with the government.
This can be different from the significant currencies that field units hold on a centralized system (banks) and controlled by the government.
The word cryptocurrency is roughly a combination of 2 Greek words cryptus meaning "hidden" and kare meaning flow.
Its origins date back to the eighties, when a decoder named "David Cham" introduced a centrally trendy web-based encoding called the Binding Algorithm Rule.
This algorithmic rule allows a safe and secure exchange between 2 parties. It currently holds the store for digital currency transfers.
b) What is Cryptography and how does it make cryptocurrencies secure?
Cryptography:
A technique or tactic is to convey or transmit a hidden, hidden, or secret message, idea, or information to a person or several persons who decrypt it in order to inspire or organize an important message. Wat can be done.
Without this idea (cryptography) I don't think crypto-currency will achieve success, as we look at the field unit, we have the trend of specialization recently.
Furthermore, cryptography is the main tool for keeping crypto-currency secret and secure;
- Intrusion Protective Cryptocurrency
With the involvement of any third parties or intermediaries the central authority is attempting to enable human activity or decision-making or double payment in a single cryptocurrency peer-to-peer, and at the same time protect the central authority from theft. can be saved and is protected from interference
- use keys to work
The cryptography used in crypto-currency also involves a pair of keys, which are exactly "private and public keys".
Public secret's pocketbook address which belongs to someone whereas private secret is like someone's signature which is good for the owner only. Human activity cannot be valid while this private key is not.
The result is a signature for any human activity language, such as the language-specific tradeoff on checks at intervals.
Once the crypto-currency is delivered to a person's pocketbook, the personal secret is employed in decrypting operations, reducing the chances of someone else stealing your coins. You don't have any private key. Proof and signature of the owner.
- Hashing
The use of "hashing" is to convert knowledge into text strings that do not square measure to verify the authenticity of the knowledge, thereby keeping the cryptocurrency safe, secure and free of danger, not like ancient currency.
c) Explore the Steem Genesis Block and Sign in as proof of completion.
Step1- to sign in first tap on the link that is given below ⬇️
https://steemworld.org/
Step2- then click on explorer icon
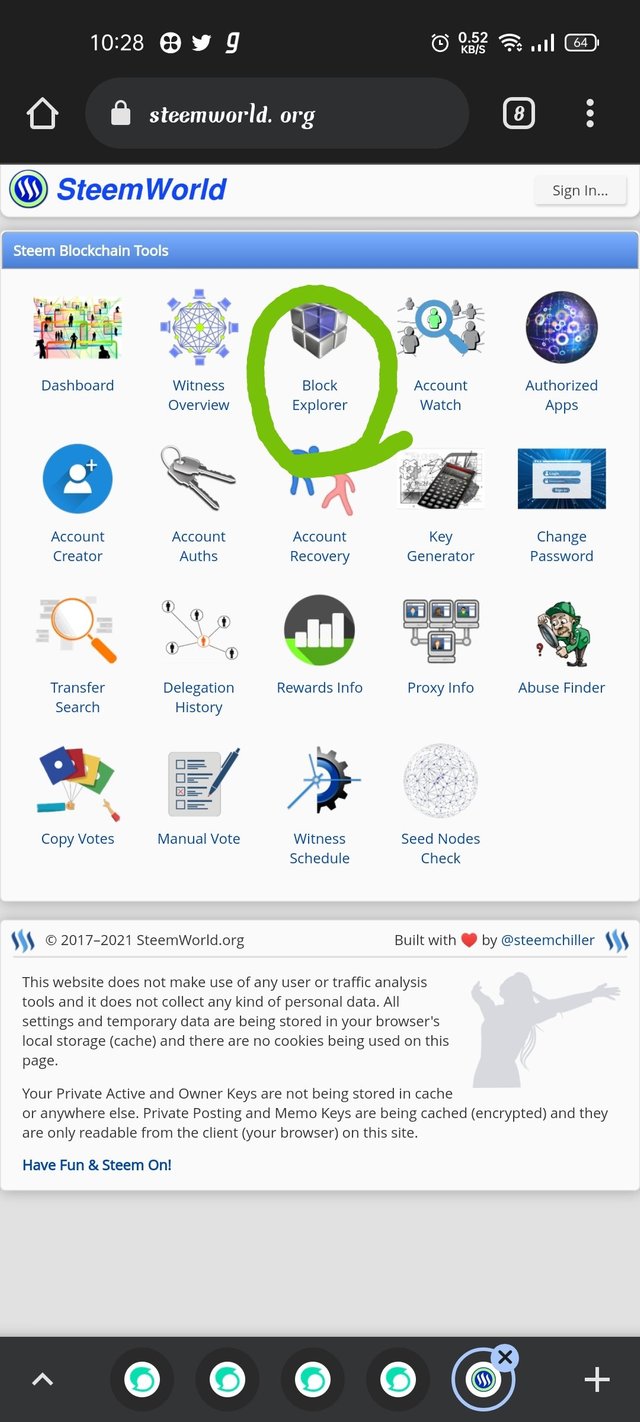 source
source
Step3- afterthat new page is pop pup then tap on ok
Step4 - afterthat new tab is open
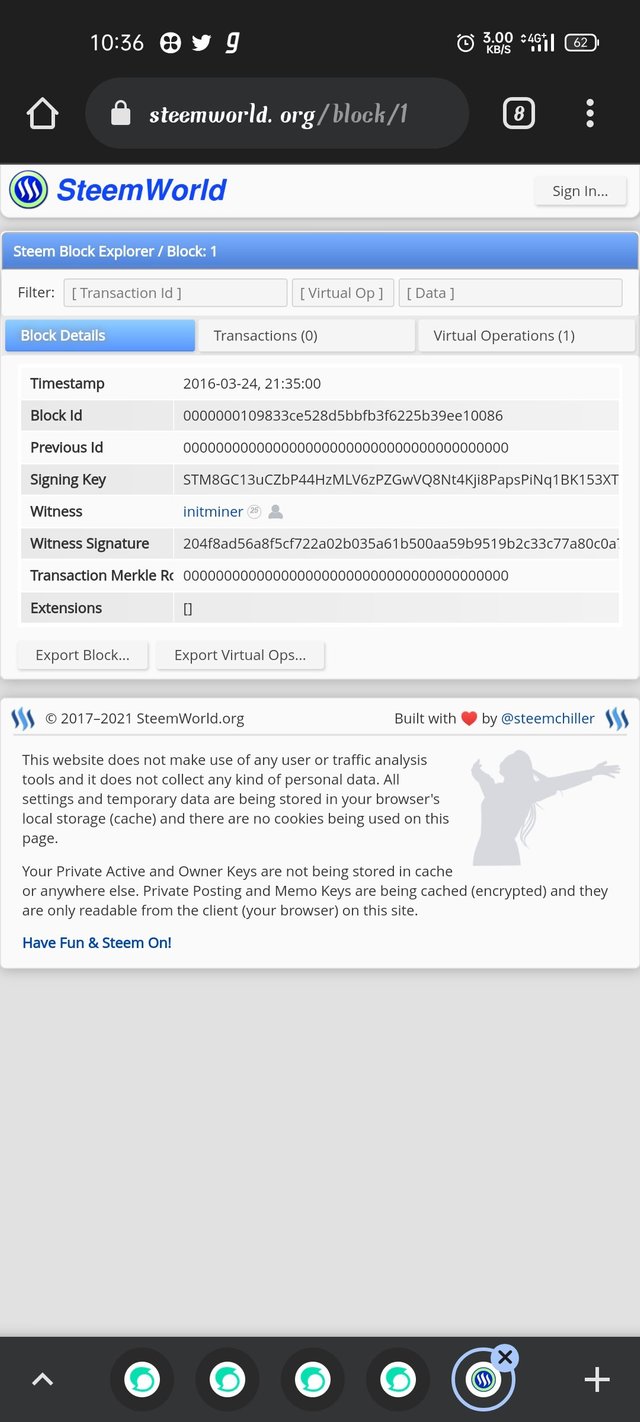
Information above is given below ⬇️
Timestamp- 2016-03-24, 21:35:00
Block Id - 0000000109833ce528d5bbfb3f6225b39ee10086
Previous id - 0000000000000000000000000000000000000000
Witness- initminer
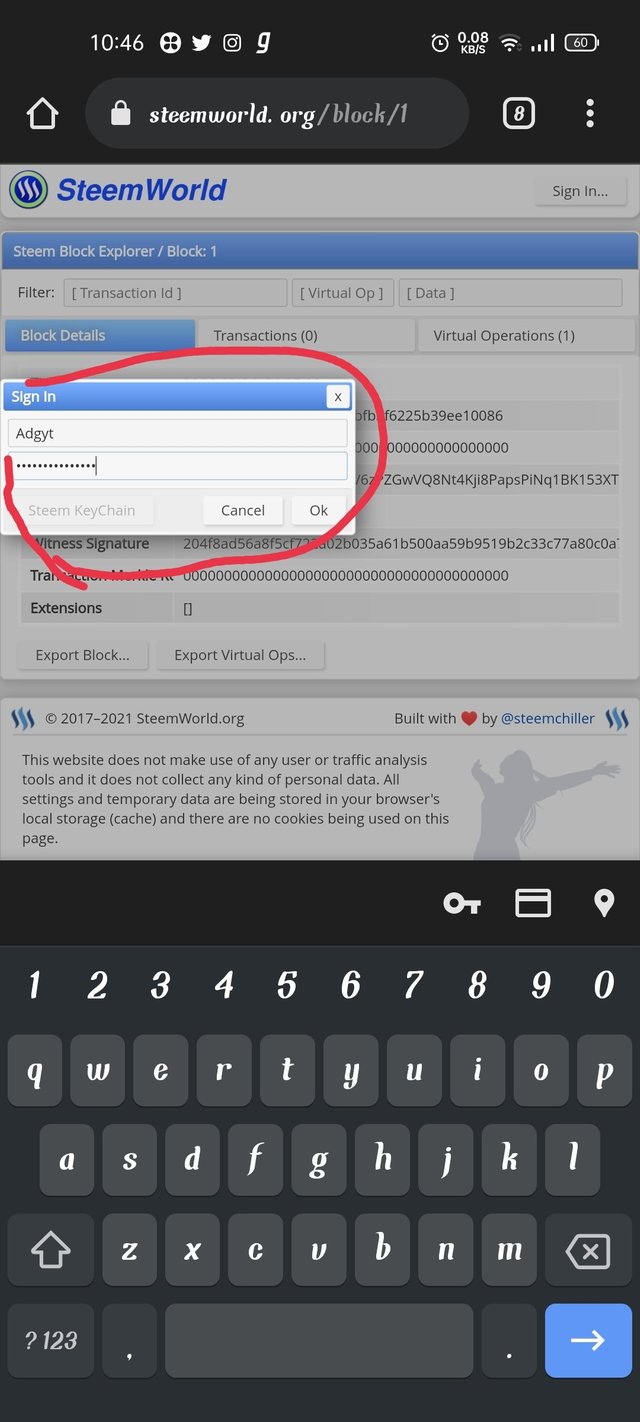
Step5- after that click on sign in
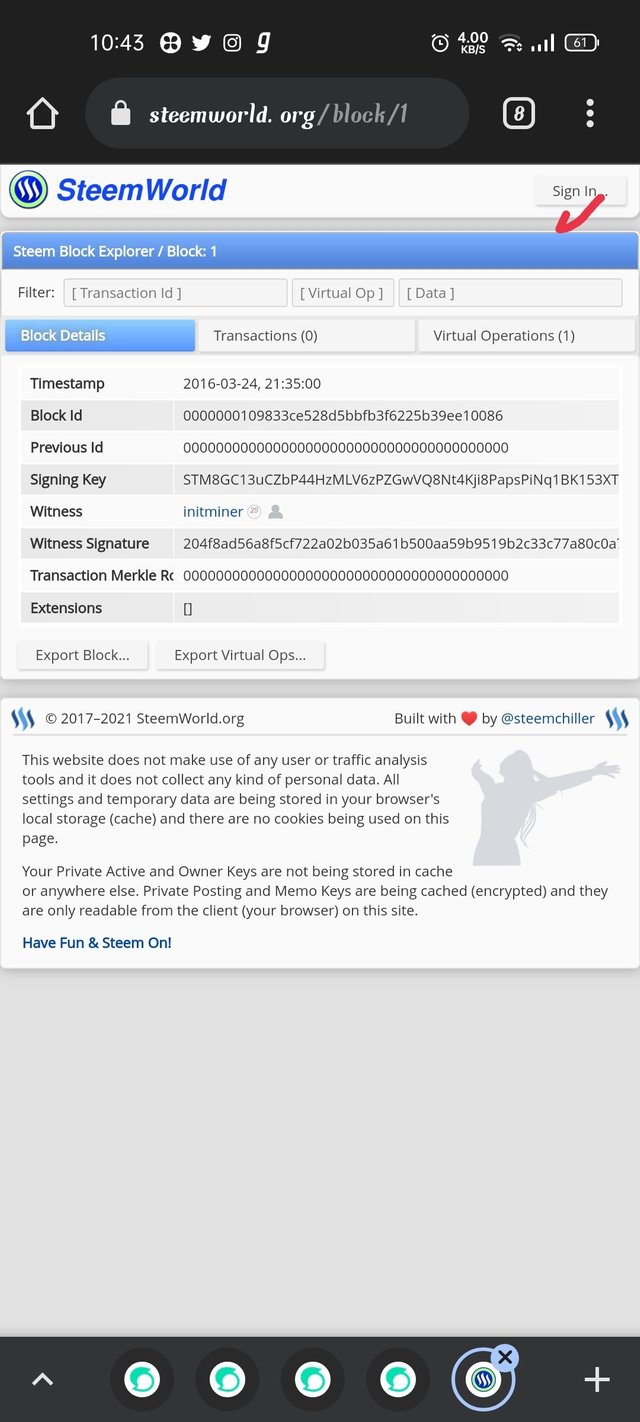 [source](Timestamp- 2016-03-24, 21:35:00source
[source](Timestamp- 2016-03-24, 21:35:00source
Step6 - now write your I'd and password
After that all you are in.
Conclusion:-
Cryptocurrency, anonymity and hiding are the opposite of the day. And each one of these many scientific discipline techniques tries and certifies that these goals have been achieved, and to ensure that users and their activities remain hidden on the network to the extent necessary.
.jpeg)
.jpeg)
.jpeg)