
Question 1
Explain the Blockchain CryptoGraphy and mention few names which are the Blockchain Platforms?
Blockchain Cryptography
The security infrastructure of blockchain technology is built with cryptographic algorithms that use asymmetric cryptography in form of Access keys (private and public), Hash functions, and Digital signatures to maintain robust security within the blockchain network.
Private and Public Keys
The cryptographic public key can be shared between connected nodes within a network, but the Private key is meant to be kept private, such that only the owner has access to the keys. During a transaction, the receiver share the public key to the sender, which enables the senders encrypt the transaction information and broadcast it to the blockchain network, the ensures that only authorized node (the receiver) with the required key can decrypt the transaction and claim the funds sent.
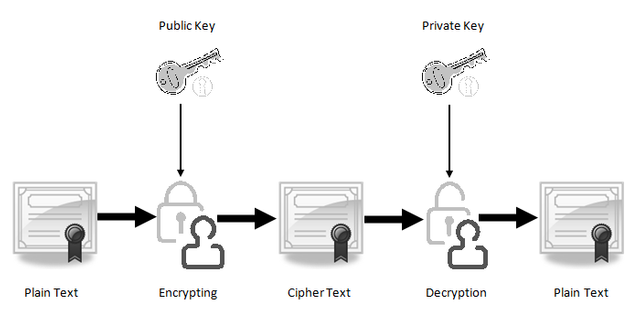
The use of cryptography within a Blockchain ensures that the identity of the nodes (sender and receiver) involved are authentic, and the transmitted information is from the original source, through the use of digital signatures and unique private keys. This compliments the Authenticity and Integrity features of cryptography.
public keys are combined with hash functions to create a unique public identifier in the form of public wallet addresses that nodes use for Sending and Receiving operations within the Blockchain.
How Blockchain cryptography works
To demonstrate how Blockchain Cryptography works, let's assume that node A is required to transfer 0.001 BTC to node B, the receiver which is node B will forward the public address to node A.
With the received public key, node A will encrypt the transaction using the node B's public key and node A's private key. During the encryption, node A's digital signature is added to the transaction to validate the identity of the sender (node A), then the transaction is broadcasted to the Blockchain.
The transaction is forwarded to the node with the public address, with a pending condition that requires that the node prove ownership of the public. With node B's public and private keys the transaction will be decrypted and node B can claim the reward 0.001 BTC.
Blockchain Platforms
Some of the popular blockchain platforms include:
1- Bitcoin blockchain.
2- Ethereum blockchain.
3- EOS blockchain.
4- Tron blockchain.
5- Binance smart chain etc.

Question 2
Explain the Public Key CryptoGraphy
Public Key Cryptography
A Public key is a combination of unique alphanumeric values that can be shared publicly within a blockchain network. Public keys are used for encryption of transactions through the generation of unique alphanumeric codes that replace the input value (plain text). The replaced input value is converted to a cipher text which is a machine only readable language before the encrypted information is broadcasted within the network.
The public key is designed in a way that allows it to be shared without comprising the private key paired with it, this is achieved with the use of hashing algorithms. The public key encryption ensures that only the authorized node with the corresponding private key can decrypt the information.
Public keys are also combined with hash functions to generate public addresses (wallet addresses) that connected nodes can use for sending and receiving funds within a network. This method of address generation works because hashing algorithm is a one-way cryptography, this means that the hash of an input can not be computed to give the actual input value.
Public keys are placed and stored in digital certificates that can be used in multiple places within a blockchain network.

Question 3
Explain the Private Key CryptoGraphy
Private key cryptography
Private keys are cryptographic keys that are meant to be kept confidential, such that only the owner (authorized node) should have access to it. Private keys are used in the decryption of transactions in a Blockchain, this is because the used public key corresponds with the private key used.
Private keys are paired with digital signatures to verify the originality through verification of sender's identity (digital signature computation) and correctness of the transaction (ensuring that the contained information was not altered) a given transaction.
Private keys are stored within program software like in exchange wallets, that automatically generate, sign and verify transactions using private key attached to the wallet. Or offline drives like USB drives, Hard copies, etc. are used in decentralized wallets to verify and sign transactions.

Question 4
Explain the Digital Signatures CryptoGraphy and what is Singing Of Transaction/Message?
Digital signature
Digital signatures are confirmation techniques that involve mathematical computation to verify the originality and correctness of a piece of information. Digital signatures are combined with private and public keys to sign and verify the details of a transaction within a Blockchain, such that only the verified receiver can access the information.
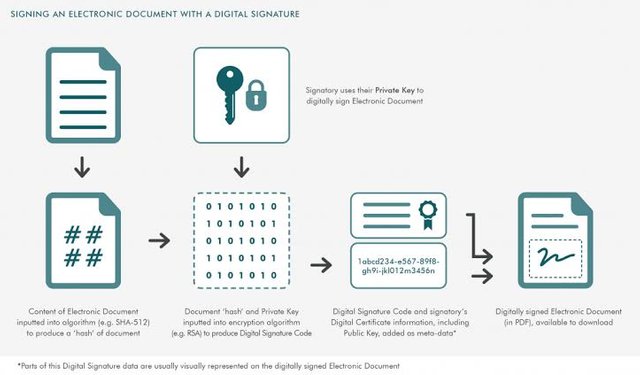
Digital signature performs two basic tasks, and they include:
1- Sign Function
New digital signatures are generated with the encryption hash and private keys for every new information encrypted. This digital ensures that the sender's identity is authentic.
i.e Encrypted Transaction + Private key + Digital signature = Signed Authentic transaction.
2- Verification function
Correctness of a transaction is verified using the public keys and the signed digital signatures attached to the transaction. The computation checks if the signature is from the original source.
i.e Encrypted Transaction + Public key + Digital signature = Verified Identity and valid information.
Signing a transaction
Signing a transaction is simply a process of adding digital signatures to a transaction, using required private keys to prove the source, originality, and correctness of the transaction to the blockchain network and the receiver of the transaction.
This signing process can be done manually, like in the case of multi-sign wallets that require more than one digital signatures to initiate a transaction depending on the wallet configuration. Or automatically, like in the case of exchange wallets that automatically generate and sign the digital signatures using the generated privates keys.

Question 5
Explain what is Symmetric and Asymmetric cryptography?
Symmetric Cryptography
The Symmetric cryptography is a type of cryptography that requires a single key that is kept confidential, shared between connected nodes (sender and receiver) for encryption and decryption of information in a network. For symmetric cryptography to work, the sender and the receiver must have access to the same key.
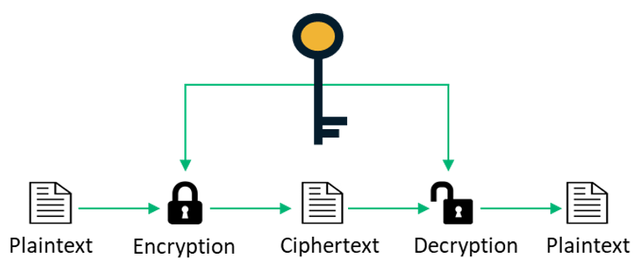
In symmetric cryptography encryption, the single key known by the sender and receiver is used to encrypt the information to a cipher text (machine-readable language) and broadcast the information to a network. When the receiving node is identified, the same key is used in decrypting the information, thus changing the ciphertext to the human-readable format.
Types of Symmetric cryptography
There are two types of symmetric cryptography algorithms, they include:
Block symmetric cryptography
This type of symmetric cryptography that encrypts a fixed length of information. The encrypted information is stored in blocks till the final piece of information is encrypted before broadcasting it to the network.
Stream symmetric cryptography
This type of symmetric cryptography encrypts and broadcast the information in a continuous sequence without storing the encrypted information.
Examples of Symmetric Cryptography
1- Data Encryption standard (DES)
2- Advanced Encryption standard (AES)
3- International Data encryption algo (IDEA)
4- Rivest cipher 4, 5,6. Etc.
Asymmetric cryptography
Asymmetric cryptography is a type of cryptography that requires two separate keys that correspond to each other, known as public and private keys for encryption and decryption of information in a network. The public key can be shared to connecting nodes within the network and is used for encryption of information. But the private key is meant to be kept secret, and it is used for decryption of received information.
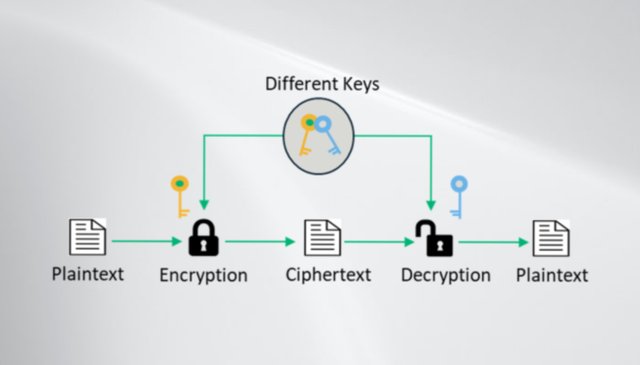
This is the type of cryptographic keys used within the cryptocurrency and Blockchain ecosystems. In asymmetric cryptography, the connecting nodes exchange public key that enables the sender encrypt the information, attach a digital signature, and broadcast the information to the network. When the receiver gets the information, the private key is used to decrypt the information.
Private and public keys serve other functions when paired with hash algorithms to create an even more secured operation, like in the case of blockchains, the creation of public addresses is done with the use of public keys and hash functions.
Examples of Asymmetric cryptography
1- Rivest Shamir Adleman (RSA)
2- the Digital Signature Standard (DSS)
3- Elliptical Curve Cryptography (ECC)
4- the Diffie-Hellman exchange method
5- TLS/SSL protocol

Question 6
How Blockchain Wallets CryptoGraphy works and explains the available types of Crypto Wallets
Wallet Cryptography
A crypto wallet is a secured digital space hosted on digital devices (servers, offline drives, ledger drives) that stores the private keys and holds crypto assets. Wallets are differentiated in the cryptocurrency ecosystem by a means of unique Identifier code called wallet addresses (no two generated wallet addresses are the same).
A wallet has two corresponding keys, a private key which is kept secret, and a public key which is shared publicly.
Example of a Private Key
65353832712598188397057776692221459589316196485155527199304545234423083149336
Example of a Public Key
048fd4f5e527e933bef2bec6f41960570c6611995ca14f67b3150741a2e75417b0936a5098054eb33d88d25f82d7b291b79d04ad107435f3e74cd12e2035d4d387
Wallet addresses are generated using hash algorithms and public keys, this makes the wallet address secure. While digital signatures and identity verification are done using the private keys and hash algorithms.
Wallet addresses can be shared publicly and used to send or receive crypto assets from connecting nodes within a network. The hashing of crypto wallets ensures that wallet addresses can be used publicly without compromising the private keys and digital asset values stored in them.
With the layered cryptographic functions of wallet keys (private and public) wallets are also secured with user-created passwords. This password is usually required before accessing the wallet. This adds a security feature to the keys of a wallet.
Categories of Crypto wallet
There are two main categories of cryptocurrency wallets, they include:
Cold wallet
Cold wallets are offline storage drives that can hold the value of a crypto asset. The cold wallet is considered more secured because it is physically held by the owner and does not require online services to access store crypto assets.
Hot Wallet
Hot wallets are online storage drives that store crypto asset values. It is considered less secure because it relies on online services hosted on different servers to access the stored crypto assets.
Types of cryptocurrency wallet
Based on the above categories, there are about three main types of cryptocurrency wallets, they include:
1- Software wallets
Software wallets are wallets stores access keys and crypto-assets digitally using software programs that operate on digital devices. This implies that an online connection is required to access the content of these types of wallets.
Examples of software wallets include; Web wallets, desktop wallets, mobile wallets, etc.
2- Hardware wallets
Hardware wallets are wallets that physically store access keys and crypto-assets. No online connection is required to access the stored values. It is simply connected to computers through USB drives.
An example of a hardware wallet is the Ledger wallet.
3- Paper wallet
Paper wallets are physical wallets that store values through means of paper documentation, like a written document. This can be conveniently less secured and tedious to use because losing the paper implies the loss of the asset and keys stored.

Question 7
What is the Merkle trees and What its importance in blockchain?
Merkle Tree
Merkle tree refers to the arrangement of transaction data (hashes) in a blockchain, such that each hash of a transaction in a block is represented in the root hash (block hash). This allows miners to verify transactions without validating every transaction contained in the block, as every transaction hash is represented in the block hash.
Merkle trees are generated by combining the hashes of the transactions represented as leaves on the Merkle tree. This process is continued till the root hash is generated. The root hash is the hash that contains all the hashes of transactions contained in the block.
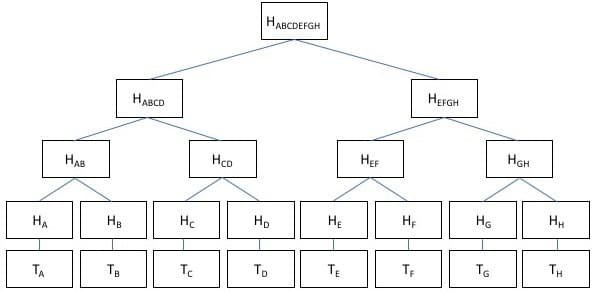
In the Merkle tree image above, transaction TA,B,C,D,E,F,G,H where hashed using hash function algorithm to get the transaction Hash HA,B,C,D,E,F,G,H which are the leaves of the Merkle tree.
Hash of transaction A and B were combined to get HAB, the hash of transaction C and D were combined to get HCD, hash of transaction E and F were combined to get HEF, and the hash of transaction Hand H were combined to get HGH.
The root Hash was derived from combining the Hash AB and Hash CD to get HABCD, and combining Hash EF and Hash GH to get HEFGH.
Combining the Hash ABDC and Hash EFGH will give the Root Hash HABCDEFGH, as stated the root hash contains all the hashes of the transactions within the block.
Importance of Merkle Tree in Blockchain
Some of the importance of the Merkle tree system in Blockchain are:
1- Reduce process Time
Validation of transactions in a blockchain is done in batches called blocks, the use of Merkle tree within the block allows miners to validate the block nonce and validate the block without going through all the transactions stored in the block. This greatly reduces block validation process time.
2- Data integrity
The use of Merkel tree ensures that hashes of transactions are represented in the root hash, thus any change within the block will invalidate the root hash, and the whole block will require to be re-mined.
3- Reduction of CPU & Memory Resources
The use of Merkle trees doesn't only reduce process time, it also reduces the CPU, memory, and network bandwidth used. This is because focusing on mining the blocks reduces the load compared to mining each transaction within the Blockchain.

Question 8
Practical + Theory, do some practical research explain the functionality of Key, Signature, Transaction, Blockchain with proper screenshots of yours practical.
Keys
The cryptographic keys (private and public) are explained to be linked together and bound to a unique public wallet address. This ensures the sender and receiver identities are authentic and the transaction is deemed correct. To illustrate this, the Blockchain Demo Link can be used.
Cryptographic Key linking
Crypto wallet has a unique address, public and private key that corresponds to each other bound to it.
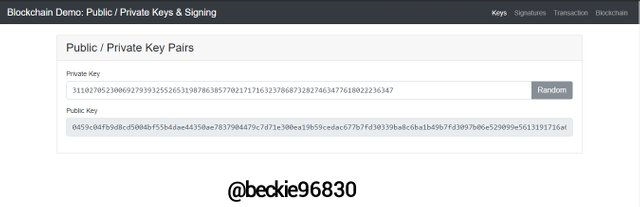
The image above shows a private key with a corresponding public key.
Private key:
31102705230069279393255265319878638577021717163237868732827463477618022236347
Corresponding public key:
0459c04fb9d8cd5004bf55b4dae44350ae7837904479c7d71e300ea19b59cedac677b7fd30339ba8c6ba1b49b7fd3097b06e529099e5613191716a6b325491b1ed
Changing the private key will generate a corresponding public key. To illustrate this:
The private key was change to 2021:
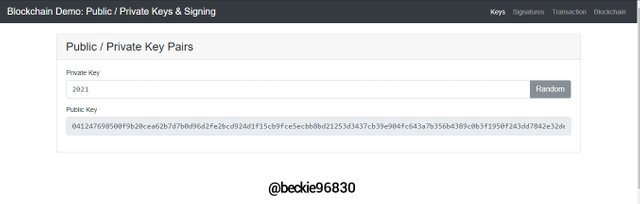
Private key:
2021
Corresponding public key:
041247698500f9b20cea62b7d7b0d96d2fe2bcd924d1f15cb9fce5ecbb8bd21253d3437cb39e904fc643a7b356b4389c0b3f1950f243dd7842e32de16d2b522004
This proves that all private and public keys are unique and that private keys are linked to corresponding public keys. Note that public keys are shared publicly and private keys are kept secret.
This is why a sender can use the receiver's public key to encrypt a transaction.
Digital Signatures
Digital signatures are attached to a transaction to prove the authenticity and correctness of a transaction, through the sign and verify function. A digital signature is generated with the hash of a given transaction and the private key.
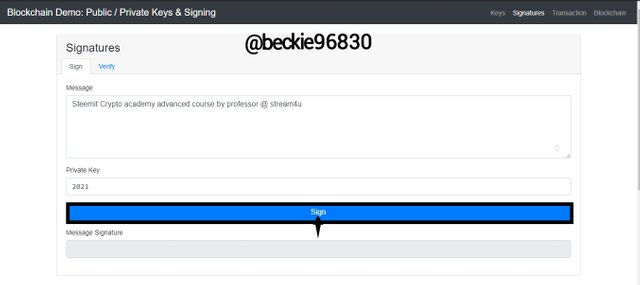
Sign Function
Clicking sign will sign the transaction/message by generating a unique digital signature
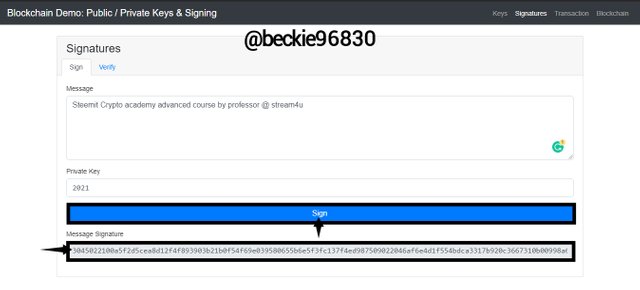
The digital signature is:
3045022100a5f2d5cea8d12f4f893903b21b0f54f69e039580655b6e5f3fc137f4ed987509022046af6e4d1f554bdca3317b920c3667310b00998a6db4a4d0ddad4a16b5e95f34
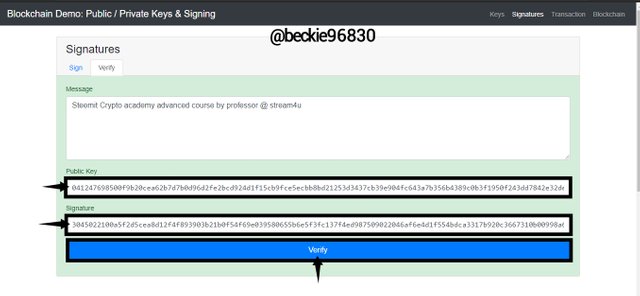
Verify Function
Digital signatures and public keys are used in verifying the identity of the sender and the validity of the transaction.
In this case, the sender's digital signature corresponds to the public and private address. Thus sender's identity is confirmed since private keys are only known by the owners but the public corresponds to the private key.
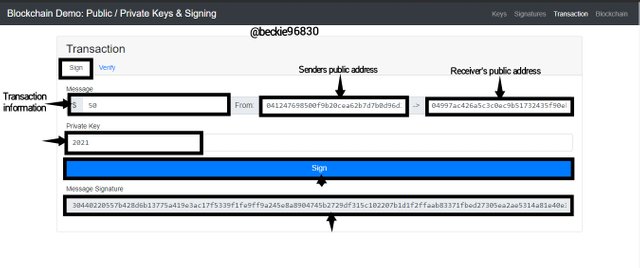
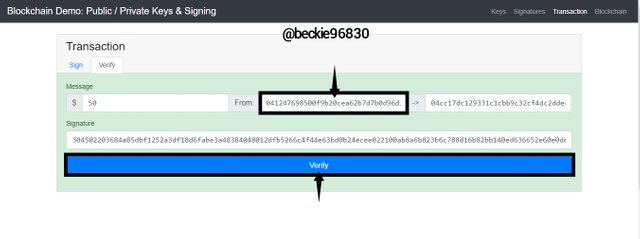
Transaction
This illustrates how a Blockchain transaction is encrypted by the sender. The sender and receiver's public keys are used to encrypt the transaction before broadcasting to a Blockchain network.
Since the receiver's public key is linked to the corresponding private key, the receiver can decrypt and claim the transaction information
The sender adds a digital signature to authenticate the transaction. This is done by clicking Sign on the blockchain Demo.
When the transaction reaches the receiving node, the validity of the transaction is checked. If the sender's digital signature corresponds to the public address attached, the transaction is checked as valid, if not the transaction is invalid.
Blockchain
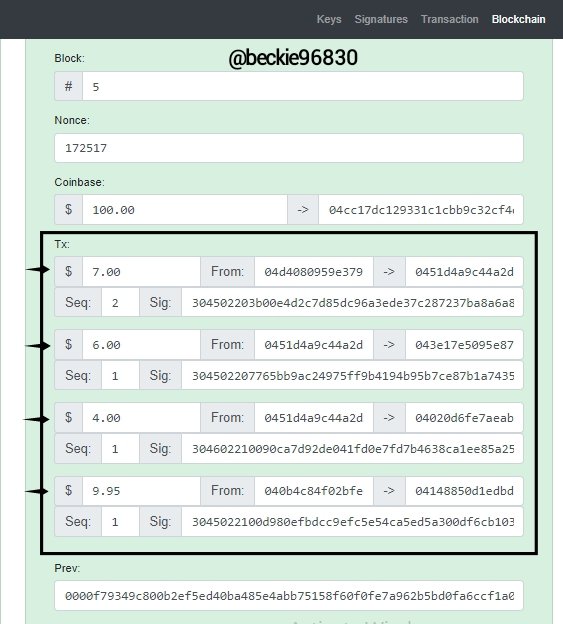
The Blockchain section illustrates how transactions are stored in a block of a Blockchain. Application of Cryptographic algorithms on transactions ensures that the transaction remains original and correct. Any attempt of modification made will invalidate the transaction and the blocktransaction
The image below shows a block with number 5, the block nonce is 172517, and it contains 4 signed and verified transactions. Linked to the previous block 4.
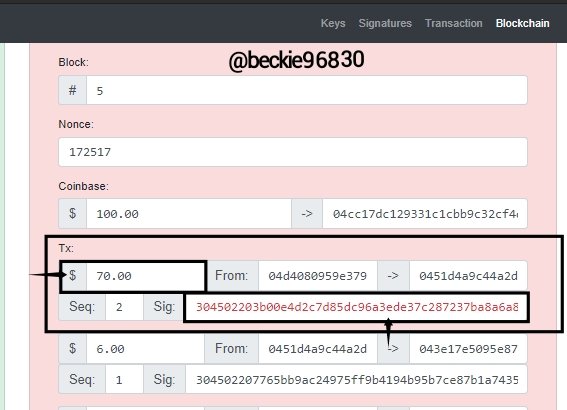
Attempting to change any detail of any transaction will invalidate the transaction and the block.
I changed the amount of the first transaction form $7 to $70
Automatically the transaction and block were invalidated, and also the digital signature became invalid, because the transaction information in no longer authentic from the source (sender).
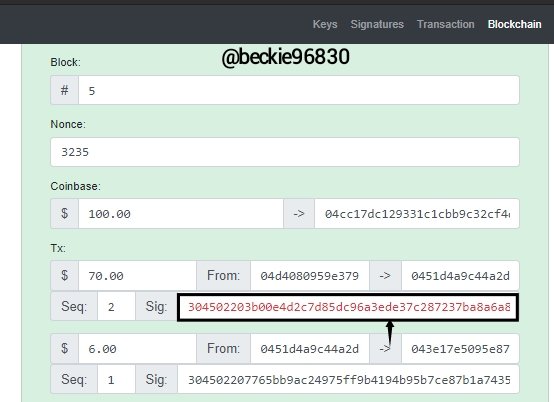
Re-mining the block will compute the new nonce value, but the transactions digital signature will remain invalid. This will indicate that the transaction is not from the intended sender since the attached digital signature is invalid.

Conclusion
Blockchain technology uses asymmetric cryptography to ensure the security of the network, which uses private and public keys to ensure transaction security. The private keys are linked to the public keys but are kept secret, while the public keys are shared between connecting nodes in the Blockchain.
Nodes use wallet addresses to send or receive funds within the network. The wallet address is a unique identifier that is generated from the combination of the public key and a hash algorithm.
During a transaction, the receiver sends their public key to the sender, and the sender encrypts the transaction using their public keys and the sender's private key. A digital signature is attached to the transaction to prove publicly the identity of the sender through the correspondence of the public address and the digital signature.
The Merkle tree is adopted within the Blockchain to reduce the processing time and usage of resources in processing transactions. The hash of every transaction in a block is represented in the root hash of the Merkle tree, this allows miners to main the entire block once without focusing on mining every transaction contained in the block.
Thank you professor @stream4u for this informative and insightful lesson.
Please complete the Homework Task title.
Crypto Academy / Season 3 / Week 8 - Homework Post for professor @stream4u - Let's Open The CryptoGraphy.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit