
Hi! Welcome to my blog once again, still in the SteemCryptoAcademy class, I want to present to you my understanding of the lecture of professor @pelon53. It was really a wonderful class, and I want to say that I've learned something which I will display in this article.
Understanding Hashes and Cryptography

In the lecture, we have learned that hashes are cryptographic functions that encode pieces of information on the blockchain. In other words, they are functions in form of an algorithm taking in some information and then produces that information in alphanumeric characters that are usually called hash values.
Hashes are very unique characters and can not be repeated, They are not like encrypted keys that can be decrypted with the proper key, in the case of hashes, they are a one-way function that makes them difficult to reverse thereby stopping cyber attackers from penetrating any file.
Hashes are very important in the blockchain industry because it has the ability to store information, encoding them in a simple combination of alphabets & numbers. Examples of transactions that can be stored in blockchain technology are; sending & receiving addresses, the amount of assets transacted, the time of the transaction, the number of blocks in which the transaction was recorded, and so on. Let's see the image below.
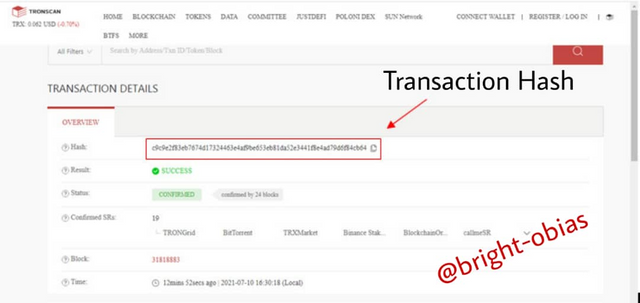
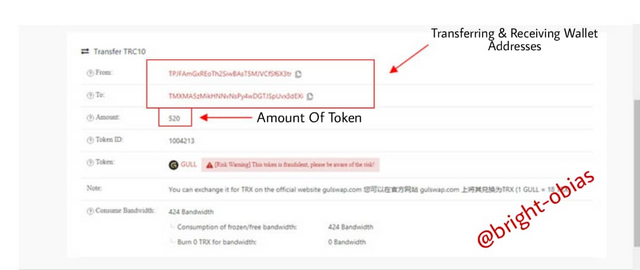
The above image is a typical example of what I have explained above, talking about what a hash can do on blockchain technology. Based on the image, it has information like the time of the transaction, the wallet address involved in the transaction, the amount involved and lot's more with just a combination of alphabet & numbers.
On the other hand, cryptography is a method that integrates different techniques and protocols in other prevent a third party from secret information. It has its greek name from the word Kryptos which means secret and Graphein talking about to write.
Key points to know in cryptography are encryption, key, decryption, and cipher. Blockchain technology adopted this protocol because it has the ability to secure information as such helping users to securely store information. Blockchains make use of two types of cryptography which are Hash functions & Asymmetric-key algorithms which the professor discussed in the lecture post. Let me now proceed to the task.
Explain what does the resistance to collision mean? And what does resistance to preimage mean?

Resistance to the collision:
To the best of my knowledge is a cryptographic hash function that its hash input appears the same in the output, that is two different input that are producing the same hashes. In some cases, there some little change in attributed information, the outcome we get will be completely unique hash.
They are very important in the cryptographic hash function as they tend to keep the record of every inputs and output of transactions, and history has it that the earliest has function gives hashes that are similar which can be misleading. Let's consider the importance of this context.
- With consider resistance to collision, it will be easier for some systems to compare cryptographic hashes in others to be sure that they are having the same version, some times an attacker could just trick users of producing one file but would be deceiving users that they had created two files whereas it was only one.
On the part of blockchain technology, they are hash functions that enable the transactions of a blockchain to be difficult in appearing twice. If the hash function becomes resistant to collision then it will be very difficult to find outputs that are similar which can also stop confusion.
Resistance to Preimage:
This is another component of cryptography, that has the ability of a hash function that can turn an input upside down thereby making it difficult for cyber attackers to have access to the result of the output. This kind of hash serves as a high-security hash that stops attackers that may want to play around by exchanging the outputs.
There are two kinds of Resistance to preimage, and: Preimage resistance and Second preimage resistance, both of them are also seen as weak collision resistance because they share the same similarities.
Note: Resistance to preimage causes the output to repeat itself as such, choosing the hash function will then make it unchangeable. A cyber attacker may be asked to choose the hash function work, in some cases, the attacker may choose correctly if he/she finds the value then he wins.
Use tronscan and etherscan to verify the hash of the last block and the hash of that transaction. The screenshot is required for checking.

In responding to this question, I will be talking about Tronscan and Etherscan. Read on as I will explain in few lines what tronscan & etherscan depicts.
Tronscan:
Tronscan is Tron is a block explorer where all information about the transactions of crypto coins are stored, it has a public ledger where it draws information and displays them on its site for viewers. Relative to the question given, let's explore tronscan now.
First, you will have to visit the tronscan site with this https://tronscan.org After clicking on the link you will be taken to the below image.
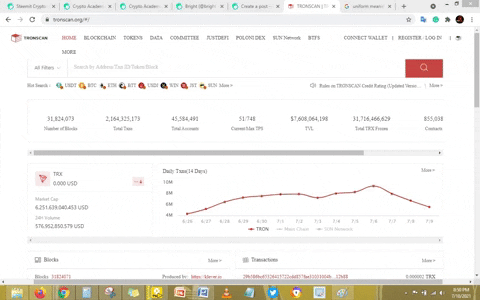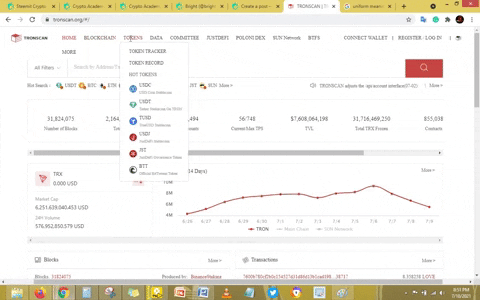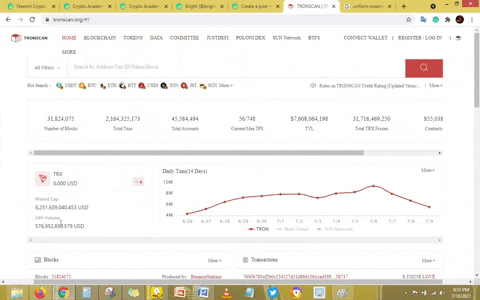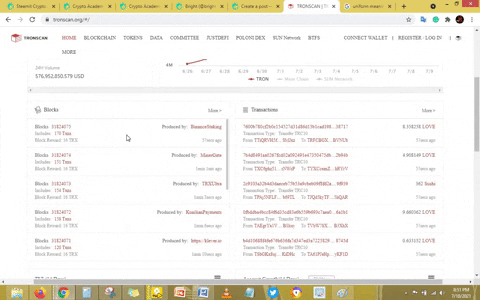
The above GIF image shows the home interface of the tronscan site. Now, in other to view the latest blocks and transactions, I screw down.
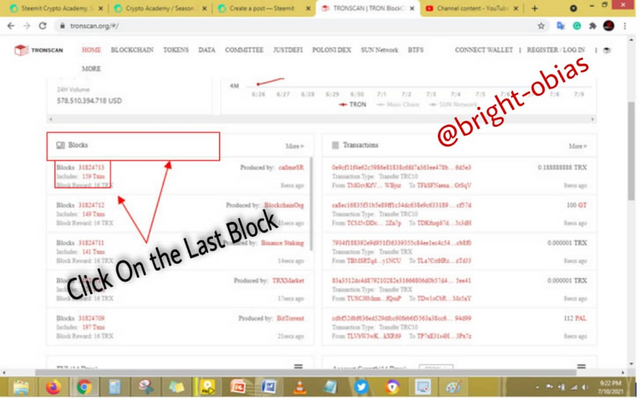
On the above image, you can see how I selected the first block which is 31825633, Immediately I clicked on it, I was taken to the next step where I saw the below image.
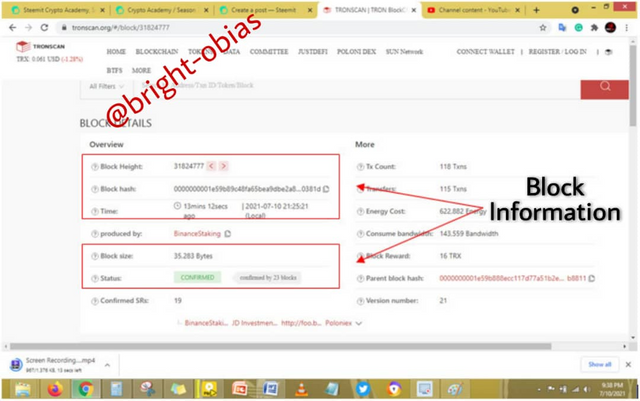
The above screenshot from tronscan.org depicts the block details of block 31825633, which I selected on the previous page. It has information like the Block hash which is 0000000001e59ee12c6ac3d7 3e0b0a0fb5193f11e4373042bf71d9290081983e, time of the transaction, block size which is 31,843 Bytes, status, transaction count and lots more. Now, I want to explore the latest transaction on the chain, I had to screw down in others to view this section. See the image below.
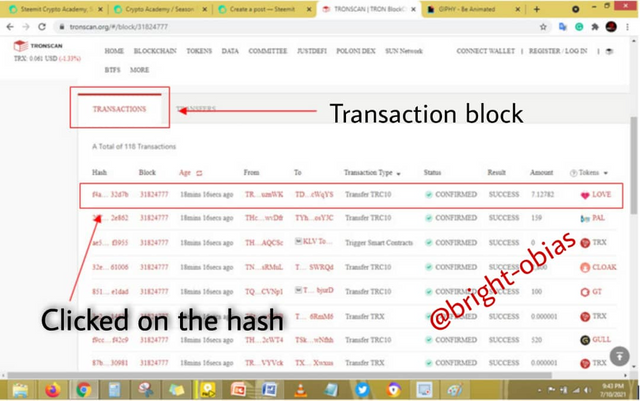
On the above image, you can see how I indicated my actions, for me to view the transaction I clicked on the transaction section and saw the latest transaction. To view more I then clicked on the hash, where it then took me to the image below.
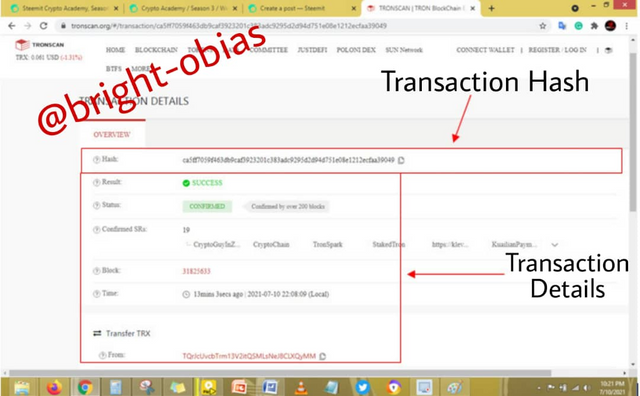
On the above image, you see details like Hash which is ca5ff7059f463db9caf3923201c333adc9295d2d94d751e08e1212ecfaa39049, the result of the transaction whether successful or failed, the status whether rejected or confirmed, the block number, the time, and so on... now let's explore the etherscan.
Etherscan
Similar to tronscan, it is a platform built with blockchain technology to help you view data regarding all ethereum blockchain transactions. it has all information regarding the ethereum network, and it is open to everyone. Let's visit Etherscan by clicking https://etherscan.io/
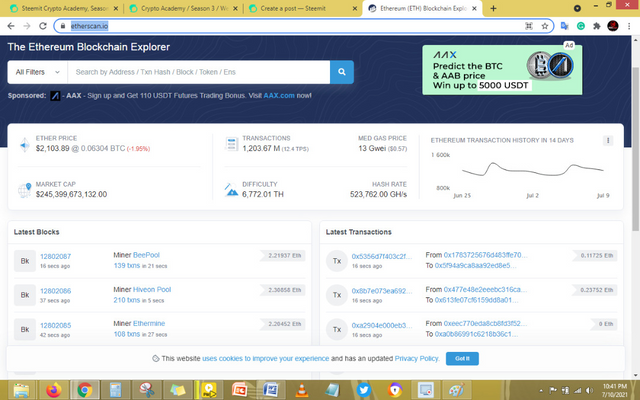
The above image is a preview of the etherscan site. You can see the latest block and latest transactions on the homepage of it, now let's take a look at the first block by clicking the block below.
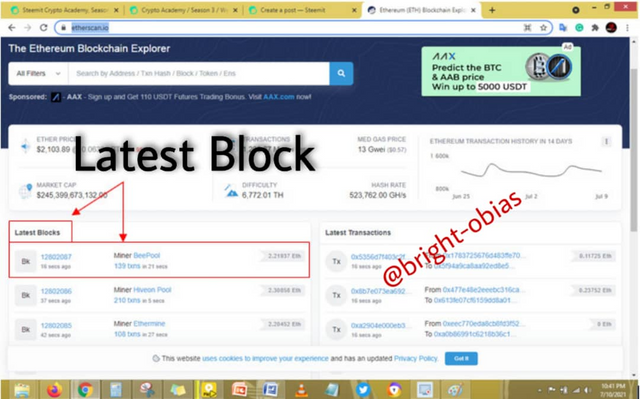
On the image above you can see how indicated, I clicked on the latest block which is 12802087, after clicking on the block, it then drove me to another page with lots of information, see image below.
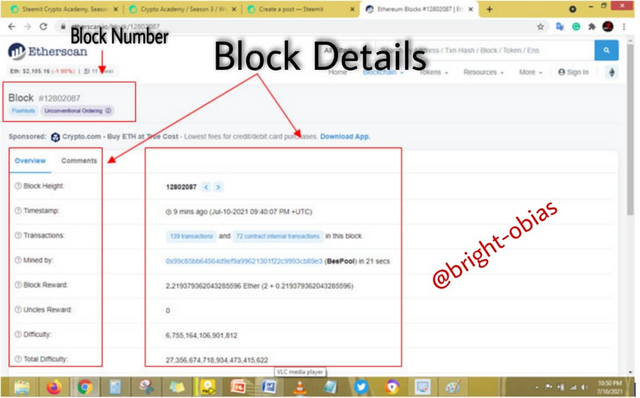
On this image, you will see the block details, such as block height, timestamp, transaction, block size, and lots more. Looking at the page, you will notice that the hash is not there, so to get the hash of this transaction, you will have to scroll down. See the image below.
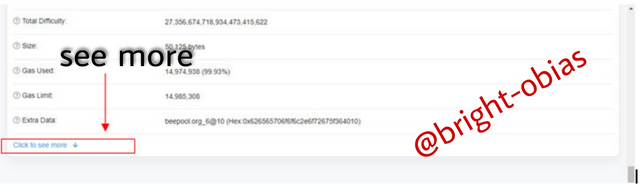
On the above image, I screw down where I then saw the button for see more, In Other to find the hash of the transaction, I clicked on to see more. See the image below.
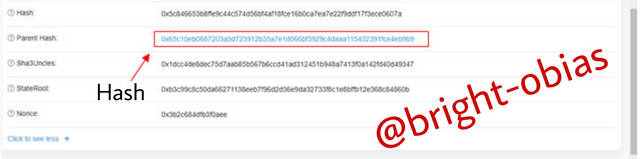
Now, you can see that I have found the hash of the transaction, you can check the image to see how I indicated the hash which is 0x5c846653b8ffe9c44c574d56bf4af18fce16b0ca7ea7e22f9ddf17f3ece0607a.
Generate the hash using SHA-256, from the word CryptoAcademy and from cryptoacademy.

In this section, I will be generating a hash using SHA-256 from the word CryptoAcademy and cryptocademy. First, you visit the link by clicking on https://passwordsgenerator.net/sha256-hash-generator/, it will reload, and you will be having the below image on your screen.
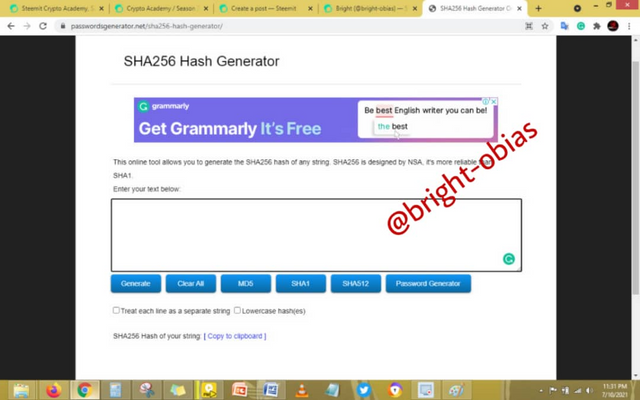
Now, to convert the input 'CryptoAcademy', I typed it on the input space where it then results in what is given in the image below.
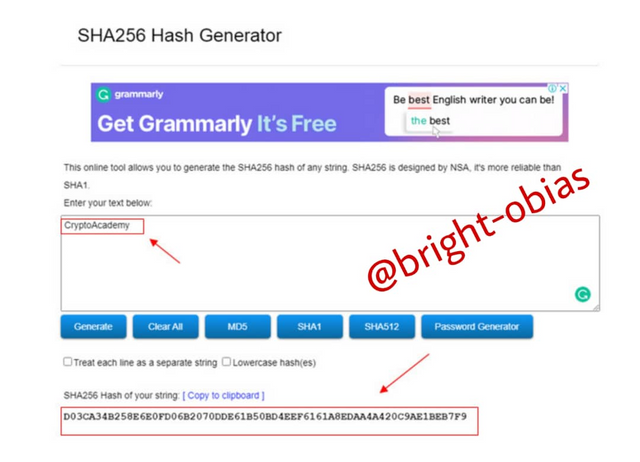
As you can see in the above image, after inputting the given word, the output was given below:
D03CA34B258E6E0FD06B2070DDE61B50BD4EEF6161A8EDAA4A420C9AE1BEB7F9
On the other hand, I also inputted the second which also resulted in another different output. see the image below.
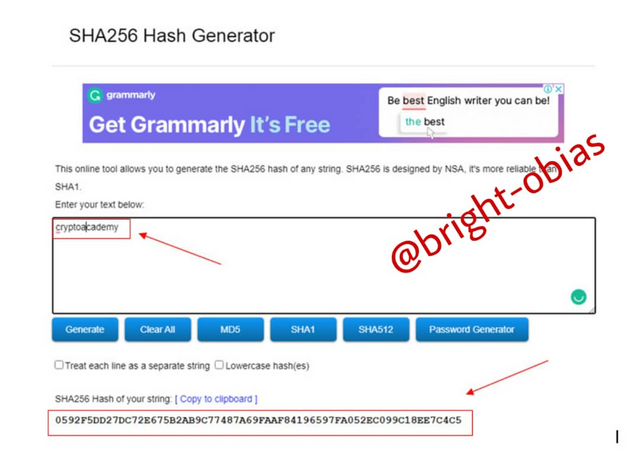
A different hash was given on the second word that consists of only lowercase letters. For the word 'cryptoacademy' see the output below:
0592F5DD27DC72E675B2AB9C77487A69FAAF84196597FA052EC099C18EE7C4C5
Observations
While inputting those words, I noticed a change in the hash which is the output, is because the given letters (CryptoAcademy & cryptoacademy) was different. The first letter was having two capital letters while the second was without a capital letter, as such making the hash result differently. Also, I have come to understand that despite that both terms are the same in meaning, the computer(SHA-256 hash) doesn't read it, what it understands is the changes made in the arrangement of the words.
In your own words explain the difference between hash and cryptography.

In the cause of study, I have come to understand these two terms, and on the context below, I will be elaborating the differences in these two terms,
Hashes are irreversible while cryptography can be reversed. In terms of security, they are more secured than cryptography this why the one-way function is important, they cannot be used to input value because of their nature(one-way function)
Cryptography is more of encryption, it encrypts data and generates a key for it, which is not secure because the data that was encrypted can be decrypted using the encrypted key.
Conclusion
In conclusion, I want to thank the prof for bringing up such a wonderful topic, it was really interesting to become a student of this class. Based on the context, it is very clear that both terms are good in security, however, noting that hash function is a one-way function that securely stores data that can not be repeated, thereby making it strong and secure. I have also come to the knowledge that cryptography is also a secure means of communicating, but not in a hidden way like the hash function. It was really a wonderful class, Thanks, prof. I enjoined the lesson.