It gives me great pleasure participating in the Week 5 lecture delivered by professor @stream4u on the basic concept and functionality of blockchain distributed ledger technology. Having learnt so much about how blocks function, the identification of such blocks and the generation of hashes through hash functions, I feel glad, then, to make a submission for the homework task.
What is Blockchain and What are the types of Blockchains / Explain in detail the types of Blockchain?

copyright free image from pixabay
Blockchain is a term that is generally used to describe a system of distributed, decentralized and most times public ledger which is made up of a record of blocks that are useful for the recording and transmission of timely transactions that take place across networks of computers. In this setup the blocks are ever-growing and the details of each block cannot be changed without the change having to affect the succeeding blocks. This means that any change that occurs in a block would invariably affect the subsequent blocks. The structure of the blockchain is such that different participants have the ability to audit and verify transactions on their own.
The database stored in a blockchain is said to be peer-to-peer and distributed in the sense that exactly the same forms of the data stored in the ledger are owned by different networks of computers at the same time even from different locations. The first proposed model or protocol which looked like the concept of blockchain was propagated by David Chain, a cryptographer who published a dissertation in 1982, "Computer Systems Established, Maintained, and Trusted by Mutually Suspicious Groups. Finally, the blockchain was conceptualized by a person or a group of persons called Satoshi Nakamoto in 2008 with the introduction of the Bitcoin blockchain.
Arguably, a blockchain can be said to comprise of different layers, namely:
- The hardware or the infrastructure itself
- The dissemination and verification of information by the discovery of nodes known as networking
- The mechanism for consensus
- Data stored in the form of blocks and transactions
- Applications hosted on the blockchain, like decentralized applications and smart contracts (in applicable cases)
Features Of The Blockchain
There are some important features associated with the blockchain which invariably add to its structure. They include:
- The blockchain consists of blocks which are made to contain valid and verified transactions which are encoded and hashed into a system or structure known as the Merkle tree. The blocks are interlinked and, hence, the name, blockchain. However, they can be created concurrently producing what is known as a temporary fork.
- The block time which refers to the average time the network requires for the generation of an additional block to be added to the chain of blocks.
- Blockchains can equally be hard forks which means that rules guiding the production of new blocks could be changed in such a way that the old blocks validating transactions based on old rules may be made to exist independently in such a way that a set of new blocks validating based on new rules would be considered invalid in the operational model of the old blocks. This is such that a dichotomy could be created where some blocks validating transactions based on new softwares and another set of blocks validating based on the old rules would result in a permanent split.
- Blockchain is decentralized which means that data is stored across a network of peer-to-peer connection which removes the need for a central node for connection.
- Blockchain exhibits openness in that records of transactions are stored in such a way that they can be viewed at any time and cannot be changed.
- Some blockchain are said to be permissionless meaning that approval is not needed from anyone before someone can join or host an application on the platform.
- There are some private blockchains which can be permissioned in that access is only granted to some individuals through a sort of layer for access control.

TYPES OF BLOCKCHAIN
copyright free image from pixabay
At the moment there are up to, at least, four known different types of the blockchain technology. They include private blockchains, public blockchains, hybrid blockchains and consortium blockchains. I am going to examine the four of them in depth.
Public Blockchain
This type of blockchain happens to be the very first time. In this blockchain there are restrictions on its accessibility by anyone. If you can boast of an internet connection, then it is possible for you to carry out transactions over the blockchain and even carry out the operations of validation of transactions by participating in the consensus protocol. In this type of network incentives are usually given to the people that perform some work in order to keep the system secure. Normally, they make use of proof-of-work or proof-of-stake algorithms.
It makes use of distributed ledger technology(DLT) and eliminates the problems and challenges that are caused by centralisation, thereby giving added security as well as transparency to the blockchain technology. Anybody can access the records of the blockchain - both previous and current. Normally, the records that are validated cannot be altered. Furthermore, anybody can propose new methods or changes to the functionality of the public blockchain. Although it is decentralized there are some laid down methods that have to be reached in verifying data that is to be added to the blocks. However, anybody can become a member of the participatory group that uses a consensus mechanism to arrive at these agreements. Examples include Ethereum, Bitcoin and NEO networks.
Private Blockchain
A private blockchain is one in which permission is required before it can be used or accessed. Normally, you would have to be invited by the administrators of a private blockchain before you can join. It functions like a closed network with restrictions and is usually controlled by a single body. Actually, it does possess some features like the public blockchain such as peer-to-peer distributed ledger network.
However, it is not as large as the public blockchain. Anyone can not just join in providing consensus and as a computing network. The network which runs the blockchain is usually organised within a particular office or location. It can also be known as an enterprise blockchain. On a private blockchain access to information relating to the blocks and transactions added could be made public or limited to some users or participants. Examples include Corda, Hyperledger Fabric and Multichain.
Hybrid Blockchain
A hybrid blockchain is one that contains the features of both centralised and decentralized blockchains. However, the level to which centralisation or decentralization is applied can vary based on particular cases and application. This would eventually affect the working mechanism of the particular hybrid blockchain in question. Normally, it would combine the features of both private and public blockchains to achieve the custom designs of an organisation.
Examples of hybrid blockchains include XinFin's hybrid blockchain and Dragonchain.
Consortium Blockchain
In a consortium blockchain the company usually employs different approaches towards solving its unique needs. It can also be called a federated blockchain and may combine the features of both private and public blockchains. Usually, in a consortium blockchain, procedures for the achievement of consensus are usually determined by nodes that are pre-selected for the purpose.
Although it may not be open to the general public, it is often seen to retain the feature of decentralization. This is usually due to the fact that they are managed mostly by more than one company or organization. A narration in this type of plugs and would offer efficiency, privacy, transparency and even trustlessness without full power and authority being vested on any element. Examples include IBM Food and Energy Web Foundation.
| Type Of Blockchain | Advantages | Disadvantages | Use Cases |
|---|---|---|---|
| Public Blockchain | (1). Public blockchains are not controlled by any organisations that may jeopardize its continued existence at the closure of such organisations.(2). Public blockchains are known to be very transparent as the procedures required for the addition of transactions are already laid down.(3). Generally public blockchains are quite secure.(4). In public blockchains, access is quite easy as you may not require going through third-party intermediaries before participating | (1). Public blockchains can become slow and just about anyone even with a dubious mission can join. (2). With the addition of more nodes to public blockchains, scalability gets hampered.(3). There is the possibility of 51% attack where miners can cooperate to put the entire system at risk | (1). They can be used for the purposes of exchanging different crypto coins.(2). They can be used for mining of cryptocurrencies.(3). They can be used to produce records that are fixed but which can be audited (such records can include public records, affidavits and owned properties) |
| Private Blockchain | (1). It is easy to alter the rules that are governing a private blockchain to suit changes in an organisation.(2). It is possible to modify records of transactions and registrations that may become necessary - an example is in the case of land registries.(3). The risk of 51% attack is eliminated due to the fact that the miners in the network are not secret or unknown.(4). Transactions on the private blockchain can be much cheaper since they would have to be verified by a few nodes and not up to 10,000 nodes.(5). In the cases where access to information relating to blocks and transactions added are made private, user privacy or organisational privacy is provided in a greater measure. | (1). Private blockchains have been argued to not really represent the core concept of blockchain which is decentralisation and hence should not be considered as one.(2). The fact that there are fewer nodes validating the system may become a security threat.(3). The issue of trust becomes a crucial factor since there are centralised number of nodes providing validation.(4). A fewer number of corrupt nodes could mean a devastating systemic downfall of the entire network.(5). Private blockchains do not give room for anonymity | (1). They can be used for the management of supply chains.(2). They can be used for the validation of owned assets.(3). They can be used for the secretive auditing and management of trade results by an organisation(4). Private blockchain provide more speed.(5). Present blockchains can be used to cryptographically encrypt information that does not need to be made public. |
| Hybrid Blockchain | (1). It can give privacy to an organisation as it works within a closed system that may not be publicized.(2). It is possible for the company to change or alter the rules based on changes to the organization's goals and desires.(3). It is also difficult to carry out a 51% attack since the validators are recognisable.(4). It can explore the features of public blockchains while equally retaining the feature of privacy as required.(5). It is more scalable than the public blockchain despite the fact that it may still enjoy some features of public blockchain. | (1). It may not be absolutely transparent in its operation as there may still be a few elements of publicization.(2). It may be difficult and challenging to upgrade to the standard of a hybrid blockchain.(3). Participating in the validation of blocks may not always be incentivised. | (1). They can be applied to the management of the real estates where assets can be open to the public while the mode of operation remains private. (2). It can also be used in the place of retail activities where available wares can be made public but organisational structure remains private.(3). Hybrid networks can also be very good for markets like financial markets which are usually regulated but must be made known to the public |
| Consortium Blockchain | (1). It comes with the opportunity to customise and control ownership of resources by up to two different organisations.(2). They are quite scalable(3). They offer a lot of security(4). The governance of this type of blockchain is usually properly defined(5). It is possible to control who gains access to the blockchain(6). It has been tested to be more efficient than the public blockchain. | (1). It relies on the integrity and ingenuity of members to remain fully operational(2). Usually, it may become less transparent in nature.(3). It can be regulated and censored by the organisations involved and this may hamper its functionality.(4). Anonymity may not be fully achieved when compared to some other types of blockchain. | (1). This type of structure can be used to share results gotten from research and data analysis in a secure way.(2). This type of blockchain can be utilised in the banking sector where financial institutions can co-operate and choose which node validates transactions.(3). It can be used for the tracking of food supplies and supply chain |

What are the benefits of blockchain?
copyright free image from pixabay
There are quite some enormous benefits and uses associated with the blockchain. Some of them include:
They are useful as distributed ledger for cryptocurrencies
In most cases, cryptocurrencies which have become the order of the day, utilise blockchain networks to keep records of their transactions. The two major cryptocurrencies that have become an integral part of human existence namely Bitcoin and Ethereum both rely on blockchains for their feasibility. Currently, top organisations and even governments are beginning to adopt the use of cryptocurrencies in one way or the other and this means that, in extension, blockchain technology would have to be deployed for the fulfillment of such dreams.
For smart contracts
Blockchain has been deployed in the area of creating applications and programs that do not require human interaction for its execution. They do not require the trust of anyone and beneficial transactions can be carried out with an automated escrow.
For financial services
Some banks and big financial organisations have expressed interest in the deployment of blockchain technology for the fulfillment of financial settlement services. Interestingly this favours the use of distributed ledger's in the banking sector. Also, financial stocks are now being tokenized even in some exchanges.
For video games
Blockchain has been deployed for leisure in the creation of video games like crypto kitties. One of these virtual pets had sold for over $100,000 in December 2017. In the same year about 30% of all transactions on the Ethereum network was attributed to crypto kitties.
For energy trading
Blockchain technology has been used in the aspect of energy trading on a peer-to-peer basis. In this scenario, virtual net metering is used in such a way that sellers are able to generate energy and share it with other people.
Some other benefits include:
- It can be applied in the management of supply chains
- It can be used to fight against counterfeiting by assigning unique values to products
- It can be used and healthcare for processes involving insurance payments and patients monitoring
- Also, efforts are being made for blockchain to be used for registration of domain names

Explain Blockchain Distributed ledger.

copyright free image from pixabay
Distributed ledger technology is a term used to describe a situation whereby exactly the same form of data is replicated, digitally synchronised, shared across a wide geographical spread, among multiple institutions, different countries and different sites at the same time without the need for a central administrator as can be seen in the case of centralised database. In some cases it can be referred to as Replicated Journal Technology (RJT) as the same type of information is sent across different nodes.
In the establishment of this type of network, there is the need for a general consensus algorithm for reaching agreement and a peer-to-peer network established for the purpose of the underlying technology. This type of technology is utilised by the Bitcoin network and some other cryptocurrency blockchains. Notably, this kind of technology makes it possible for public nodes to have access to transactions that occur over it at the same time. Identical copies of the data structure are owned by the different nodes. Any time changes occur in the network, it reflects across all the different copies.
There are a few benefits associated with distributed ledger technology in blockchain, namely:
- There is no single reference of failure in this technology and transactions will be carried out exactly as programmed
- There is high level of reliability in the technology since it is immutable and irrevocable
- DLT in blockchain ensures that two parties can interact without the need for an intermediary thereby reducing risk
- DLT in blockchain ensures that transactions are time stamped, recorded and can be audited or traced
- DLT in blockchain ensures that transactions can be recorded in one public ledger thereby eliminating the cost of multiple ledgers
- DLT in blockchain reduces cost of operation by removing third parties and automating a lot of processes
- This network ensures that the end participants control their operations and transactions themselves
In spite of its benefits there are still a few demerits of DLT in blockchain. Some of these demerits include:
- It is relatively new and issues like limits on data, processes involved in verification and speed of transaction need to be handled
- The stand of the government on its regulation is still unsettled as such this may delay its adoption by some interested corporations
- Linking physical products with DLT in blockchain, as has been seen with digital products, may have to come with additional technological cost like implementation of RFID chips and IoT
- DLT and blockchain consumes a lot of energy for its operation and over 450,000 trillion solutions are being attempted per second by Bitcoin miners
- With regulations like the European regulation on data privacy (GDPR), DLT in blockchain must seek ways to implement the right for private data to be forgotten as required by the law
- Adoption of the DLT used in blockchain may be delayed as it often requires the replacement of already existing systems and technology by corporations

What Is Blockchain Double Spending and how Bitcoin handles this problem?
Double spending can be defined simply as the act of using exactly the same fund, bill or currency to make two separate payments. This may not be possible with physical transactions. However, it is a reality in blockchain technology. In the blockchain technology this kind of hack or attack can occur in the situation whereby transactions are accepted by payees before their actual confirmation on the network. This can make the attacker to spend the same currency on another transaction which may invalidate the funds earlier sent to the first payee if the second transaction is rather validated upon confirmation by the network.
In the Bitcoin network double-spending is a possibility due to the fact that transactions may be delayed before confirmations take place. This makes it possible for an attacker to send the same payments to two different persons before actual confirmation. However, the Bitcoin network has put in place some measures to tackle this form of attack. I will explain two of these measures.
Mining

copyright free image from pixabay
Let us look at the case scenario where one attempts to send the same amount of Bitcoin to two different bitcoin wallets at the same time. The two transactions would both enter into the transaction pools and would be recognised as being unconfirmed. Through the mechanism for verification which is the proof-of-work, the first transaction would be confirmed after miners would have solved the cryptographic puzzle to that effect. This would then verify the first transaction and invalidate the second one. This means that when the two transactions are put into the pool for confirmation, the one that gets the highest number of confirmations would be added to the next block and the other would be jettisoned.
The processes taken for the confirmation of transactions and their subsequent addition to blocks is always referred to as the mining of new blocks. However, the problem or disadvantage with this particular method is that in a situation whereby the second transaction that was meant for the second payee is the one that eventually receives more confirmations, the first payee would then not receive his expected bitcoin payment. Nevertheless, this ensures that the two payees do not both receive payments at the same time thereby giving room to double spending.
Proof-Of-Work Mechanism
In a different scenario, if the attacker is able to gain a 51% mining power then double spending can be comfortable. However, the proof-of-work mechanism of the Bitcoin network makes this practically unimaginable. In this mechanism hashes are used for the detection of double-spending attempts. These hashes are a very long string of numbers or integers. A particular input will generate a definite string of hash. The slightest alteration to this input will generate a totally different hash. This means that altering the input can never generate the former hash again. Usually, generating a hash for a particular transaction can be easy with modern computers.
So, the network sets a particular difficulty level by pre-determining a target hash to be generated for every transaction. This generally means that once a transaction has been entered and the amount to be spent inputted, the target hash is set. The slightest change to this entry would create a divergent hash which is immediately rejected by the network. This ensures that any effort by a single individual to double spend is foiled. This can only be possible if he is able to gain control of more than half of the mining power of the Bitcoin network. The resources required for this are unimaginable and practically impossible.

PRACTICAL AND THEORY SECTION
This practical section was carried out on a Blockchain Demo website, https://andersbrownworth.com/blockchain/
In this section I am going to be explaining how blockchain hashes function and practically demonstrate a few important features of it.
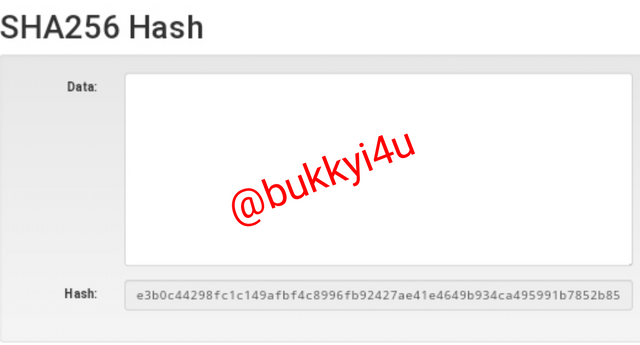
The image below shows what the SHA-256 hash looks like without any data input.
screen from source
Throughout this practical to demonstrate how blockchain hashes work, I would be using the phrase Steemit Crypto Academy with a variation on the use of uppercase or otherwise with the phrase.
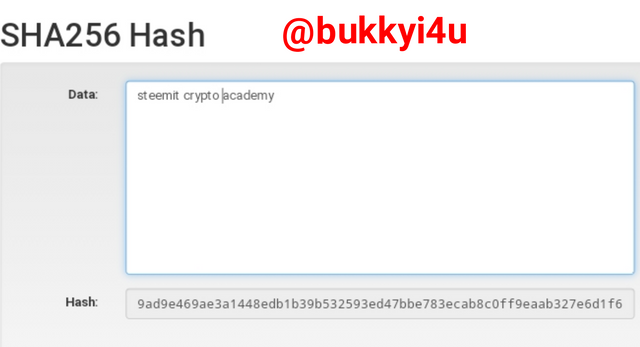
So, I decide to input the data steemit crypto academy all written in lowercase.
screen from source
As indicated above, it produces this hash: 9ad9e469ae3a1448edb1b39b532593ed47bbe783ecab8c0ff9eaab327e6d1f65
Then, I input Steemit Crypto Academy which is still the same phrase but putting the first letter of each word in uppercase.
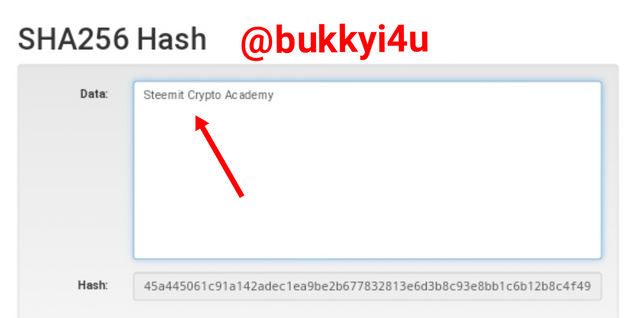
screen from source
This produces a totally different hash - 45a445061c91a142adec1ea9be2b677832813e6d3b8c93e8bb1c6b12b8c4f492 - which amplifies the fact that any slightest change to the data input would produce a totally different hash irrespective of the fact that it is still the same phrase.
Then, I decided to input the phrase STEEMIT CRYPTO ACADEMY all in uppercase.
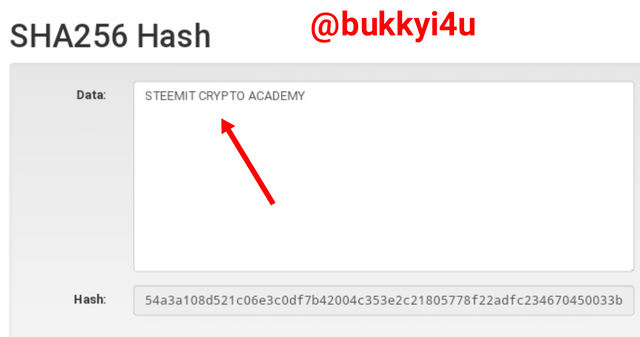
screen from source
As shown above it produces entirely different hash. Equally, this shows that you cannot get different messages that produce exactly the same hash.
To verify whether the output can be used to get back the input, I decided to input the hash for STEEMIT CRYPTO ACADEMY as shown below:
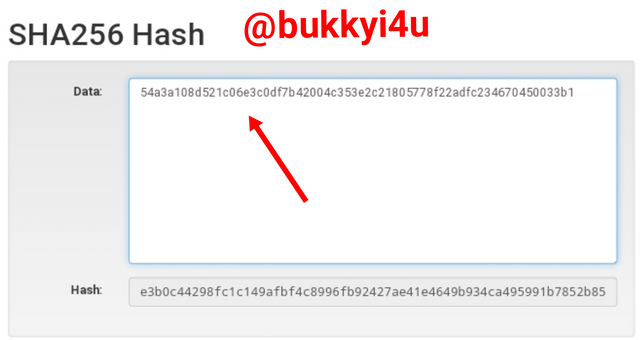
screen from source
This does not produce back the phrase but gives another hash that is entirely different as shown above.
This means that it is a one-way function. Also, it can be noted that the hashes produced do not in any way look like the input given.
Again, I decided to include a very long input (my entire homework post)
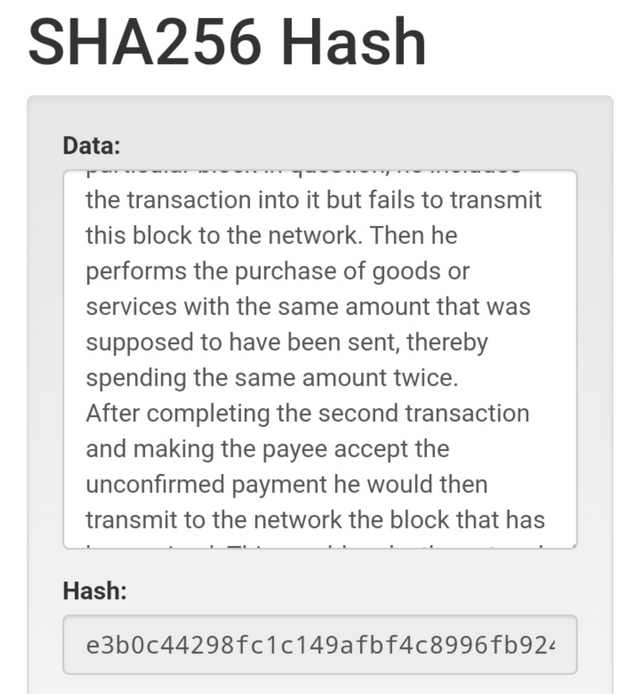
screen from source
It produced the hash below:
e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855
This hash is still of the same length or number of characters - 64 characters - as the others, irrespective of how large the text input is
Finally, I input the phrase steemit crypto academy again. It gives me the same hash below:
9ad9e469ae3a1448edb1b39b532593ed47bbe783ecab8c0ff9eaab327e6d1f65
This verifies that the same input would still produce exactly the same hash every time.
Also, hashes are used in the case of adding blocks to the blockchain. When data input in a block which includes a Nonce produces a hash that starts with four zeros, it signifies that, that particular block is signed.
This is shown below:
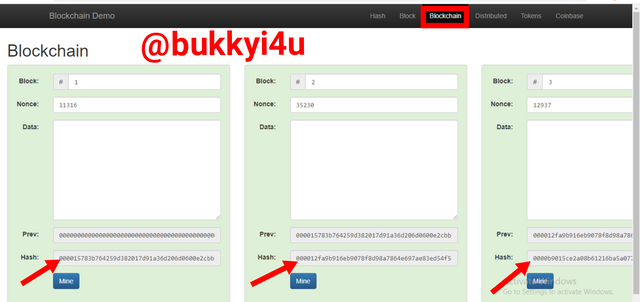
screen from source
Changing any of the input would change the hash in the block automatically. This is seen in the case below where I have included an information in the data section which reads, How are you?.
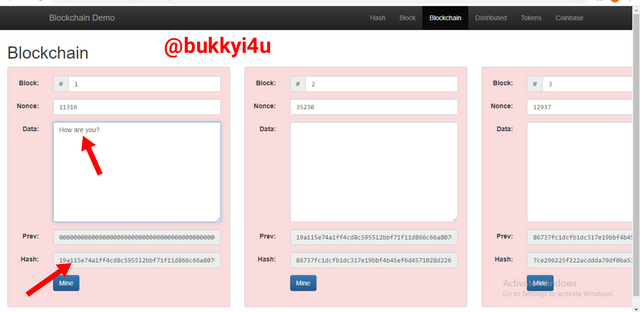
screen from source
It changes the hash to a value that does not start with zeros - meaning it is not validly signed.
The Nonce comes in here. In order to get a particular value of the Nonce which produces a validly signed hash we can decide to tweak this Nonce to achieve that. This explains the process of mining.
Note: The "Nonce" which stands for "Number Only used Once", refers to a number that needs to be solved in order to meet the difficulty requirement for that particular block
I tried to achieve the needed Nonce by myself by experimenting with two different values for the Nonce.
I input the first experimental value but it does not produce a validly signed hash:
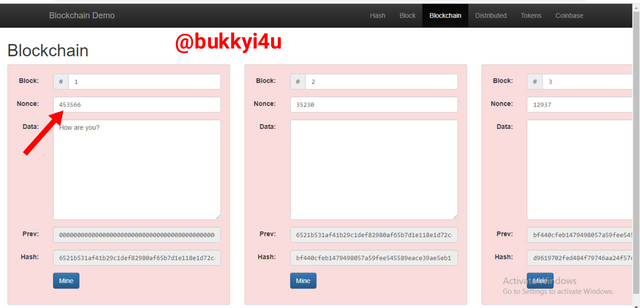
screen from source
Then, I input the second experimental value. Still, it doesn't produce a validly signed hash:
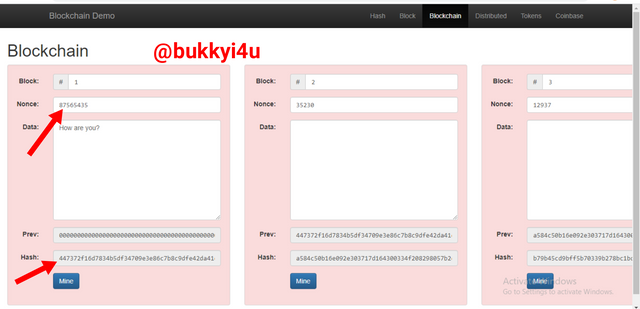
screen from source
To achieve the suitable Nonce value, I click on mine
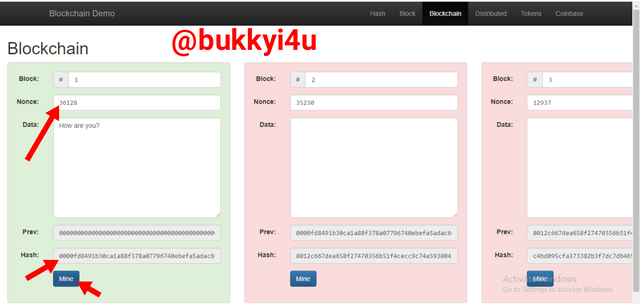
screen from source
This tweaks the Nonce to suit the data I have inputted in order to produce a validly signed hash in the process known as mining. This suitable Nonce is displayed in the image shown above.
This idea can be applied in the production of subsequent blocks. As a way of pointing back to its proceeding block, each succeeding block would carry a previous value which is the hash of the previously signed block.
The image below displays Blocks 1, 2 and 3 as all being validly signed.
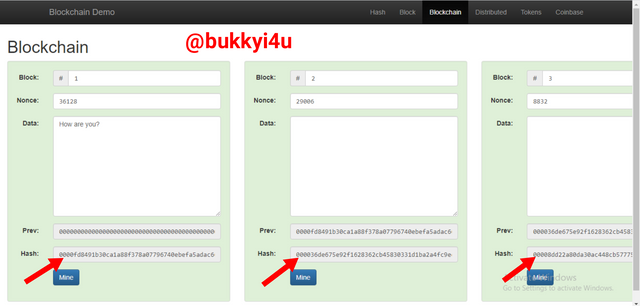
screen from source
Interestingly, changing any input value for any of the blocks, say Block 2, would invalidate that particular block as well as all the other succeeding blocks as shown below:
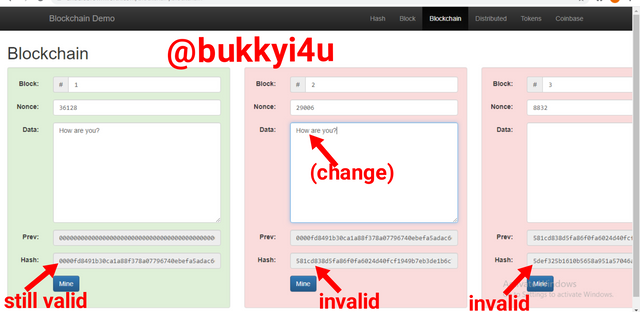
screen from source
Consequently, both Block 2 and the succeeding blocks would have to be re-mined. However, note that this change does not affect the block preceding Block 2.

FINNEY ATTACK IN BLOCKCHAIN
The Finney attack in blockchain is a type of blockchain security issue that actually affects Bitcoin or any other crypto that originates from it. Usually, it occurs as a double-spending security lapse which takes place in a situation whereby someone accepts a transaction that is not yet confirmed on the network.
How It Happens
Carrying out a Finney double-spending hack or attack is quite difficult. This is because it means that the attacker must have the ability to extract the particular block that would validate his transaction. Furthermore, it requires that the payee would accept a transaction that has no confirmations on the network. In theory, it is possible even without having 51% hash power and may occur in three steps, viz a viz:
- An attacker who is also a miner carries out a transaction and transfers his coins to a wallet address he manages. Having transferred the coins the attacker starts mining in order to mine the particular block which contains that transaction.
- In the case that he is able to get the particular block in question, he includes the transaction into it but fails to transmit this block to the network. Then he performs the purchase of goods or services with the same amount that was supposed to have been sent, thereby spending the same amount twice.
- After completing the second transaction and making the payee accept the unconfirmed payment he would then transmit to the network the block that has been mined. This would make the network invalidate the payment that was carried out to the payee while validating the block that had been earlier mined.
Who Can Fall Under Finney Attack
Anyone or payee that accepts a transaction that is yet to be confirmed is susceptible to this attack. A good example can be an online retail store which upon the acceptance of cryptocurrency as payment immediately allows access to their services. In this case the services could be accessed without network confirmation of payments leading to possible Finney attack.
Another case scenario can be a situation whereby large order flows are to be handled within a short period of time and the payment is to be made in cryptos. In such a situation if the network is congested the payee may be forced to accept transactions or payments that may not yet been confirmed thereby putting him at risk of Finney attack or Finney hack.
Protecting Oneself From This Attack
One of the very first steps involved in protecting yourself from the Finney attack is to patiently wait for a minimum of six(6) transaction confirmations on the network. At least this is required to consider the transaction as irreversible and safe.
However, the decentralized nature of blockchains may usually mean that about two confirmation may be enough. A $50 bill that has received one confirmation may even be considered safe, after all. This is due to the fact that the cost involved in carrying out a Finney Attack would be way more than that.

Limitations/disadvantages of Blockchain.

copyright free image from pixabay
There are a few limitations or disadvantages associated with blockchain technology. They include:
(1). The computing power of blockchain is such that there is heavy dependence on the participation of nodes for its success
(2). Blockchains are not very scalable like their centralized counterparts as the 4.6 TPS rate of transaction in Bitcoin cannot be compared to the 1700 TPS in Visa network.
(3). The operation of some blockchains require the input of mulch energy with may not even be eco-friendly
(4). Blockchain transactions are immutable and this could become disadvantageous in a case where an individual may decide to update details of a record for the sake of privacy
(5). Some blockchain networks may become inefficient and untimely due to congestion
(6). The fact that blockchain technology is regarded to be more secure than other technologies does not mean it is completely immune to such security threats as 51% attack, double spending, cryptographic cracking, etc.
(7). Users have to act as their own bank and take steps to safeguard their own assets with the use of private keys and this may not be very good for people who are carefree
(8). The cost of operating some blockchains by organisations that may wish to could be significantly huge
(9). In operating some blockchains like the consortium blockchain, companies may require additional expenses in employing experts with the technological know-how.
(10). Blockchain still lacks maturity and if you look at concepts like consortium blockchain you discover that companies have to rely on their own novel initiatives to develop them.
(11). Blockchains have a problem of low Interoperability as different blockchains employ different distributed ledger technology strategies that may not be feasible in an interlinked operation with others
(12). Some companies are recognised for initiating the technology with which they operate. Such companies may not be willing to subsume their legacy into the larger concept of blockchain even if their desire to deploy them for their operation

CONCLUSION

Blockchain technology is conceptualized as a peer-to-peer network that makes it possible for the same forms of a database or ledger to be shared by different networks of people across different devices and location at the same time. It comes with quite a lot of advantages and has an underlying structure that improves security, transparency, immutability and trustlessness. Equally, there are different types of it that all come with their own particular advantages and use cases.
A lot of importance has been attached to this novel technology including its use for the hosting of smart contracts, financial services, cryptocurrencies, video games, energy trading, supply chain management, as well as some other benefits. However, it is not immune to security attacks like the Finney attack. One notable possibility of these attacks is the issue of double spending. Interestingly, some blockchains including the Bitcoin network already have mechanisms like mining and proof-of-work consensus mechanism to handle this particular issue. All the same, blockchain through its distributed ledger technology has so much to offer and we should seek ways to improve and adapt them to the already existing systems for better functionality.

Cc:
@davchi
Hi @bukkyi4u
Thank you for joining The Steemit Crypto Academy Courses and participated in the Homework Task.
Total | 9/10
Your Homework Task verification has been done by @Stream4u, hope you have enjoyed and learned something new.
Thank You.

@stream4u
Crypto Professors : Steemit Crypto Academy
#affable
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit