

Hello everyone,
I’m very delighted to the take part of the second week of the season 3 of crypto academy class. This lecture by respected professor @phelon53 is on Hashes and Cryptography.
Prof gave a very detailed explanation that helped me understand the topic very well.

The hash is the backbone of the blockchain network. Any other activities on the blockchain are built on the hash. Hashes are developed based on information available on the block header.
All addresses on a blockchain are built on hashing. For example Bitcoin addresses use SHA2-256 and RIPEMD 160.
Hashes also play a major role in the generation of keys in a blockchain.
One of the series of the most used hash functions is SHA, which include: SHA-0 and SHA-1, SHA-2 and SHA-3, SHA- 256 which is part of the SHA-2 group and the SHA-512.
Hash functions have so many characteristics, these include;
- Irreversibility
- security
- calculating algorithms
- resistance of collision ( pre image and second pre image) etc.
These characteristics shows how tight the security hashes can provide. It demands a lot of effort and maybe I will say it is almost impossible for hashes to be reversed. Hashes are in no way vulnerable to security threats.
When hash functions are violated, collision is achieved. This sends us to question one of the assignment.

1.- Explain what does the resistance to collision mean? And what does resistance to preimage mean?
Resistance to collision
Like I stated earlier, collision resistance is a property of cryptographic hash functions.
We say that a hash function(H) is collision resistant when two input functions cannot be hashed to give one output. Hash operation on random input is likely to find two matching outputs.
Collision resistance is also of different types. These weak collision resistance and strong collision resistance
Weak collision resistance is restricted to a specific input whilst strong collision resistance is applied to any two arbitrary inputs.
Preimage resistance
Preimage resistance of a hash function is the property of the function that is very difficult to invert. This means that when you’re given an element in the hash function, it is computationally impossible to find the input that matches that element.
Preimage is important because in selecting a hash function, it will ensure that it is uniform.
Resistance to second Preimage
In the second Preimage resistance, the attacker is given a message to start. In the second Preimage resistance, the hash function is computationally infeasible to find a second input that has the same output as a given input.
It must be noted that,
A hash function that is collision resistant is consequently resistant to second pre-image attacks.
However, a collision-resistant hash function can be attacked from pre-image, because a single input would be searched from a single output.

2.- Use tronscan and etherscan to verify the hash of the last block and the hash of that transaction. Screenshot is required for checking.

Tronscan
I’m going to demonstrate the verification of hash of the last block at the time of making this publication, as well as the last transaction.
To do this using Tronscan.org, on its home page, at the bottom appears the option of "Blocks" and "more", as indicated below, I pressed "more" to show me the details of the last block, which change very quickly, due to the number of operations carried.
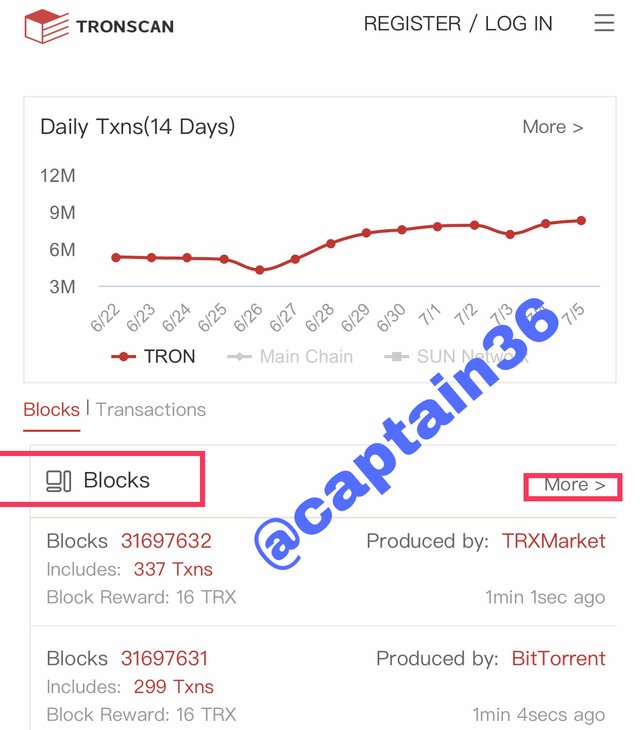
Screenshot: Tronscan.org

Once the last block can be identified on this screen, at the time of making this publication there was block 31698429 , as shown in the second image below, clearly identified in a red box.
To show the details, click on the number of the block, so the rest of the information of the indicated block is displayed.
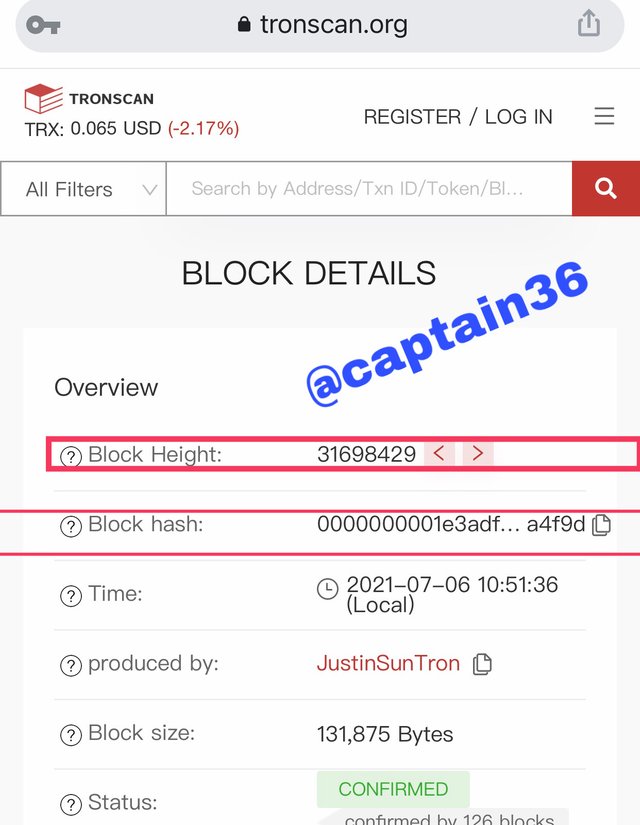
Screenshot: Tronscan.com

To verify the hash of the last transaction, I returned to the main page and in the transaction option that is next to the block one, by pressing you can see the information of the last transaction of that moment as shown below.
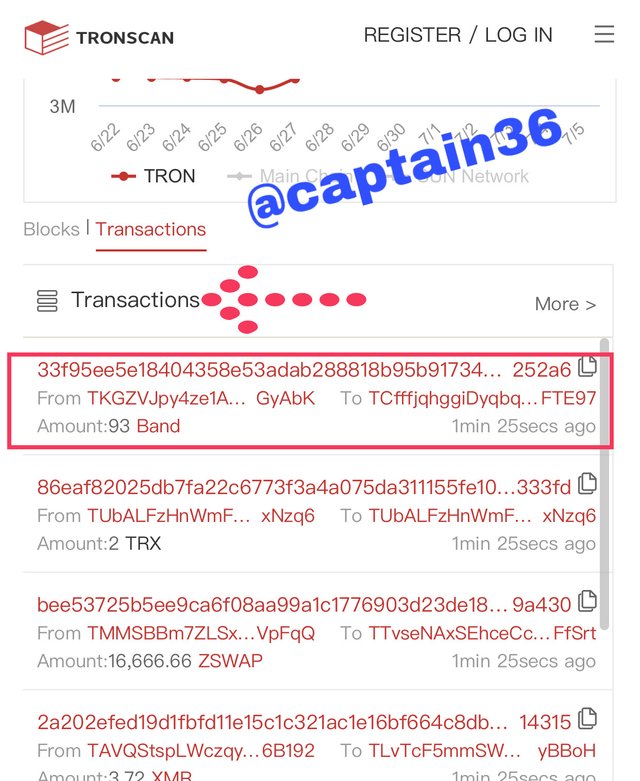
Screenshot: Tronscan.com

At the time of opening the transaction option, the last one was identified with the hash: 39ec712bcd5ee300070297616a6cc78ebe8bf0d329e9ac330d1f491f4ca2aa8c , as shown in the image below.
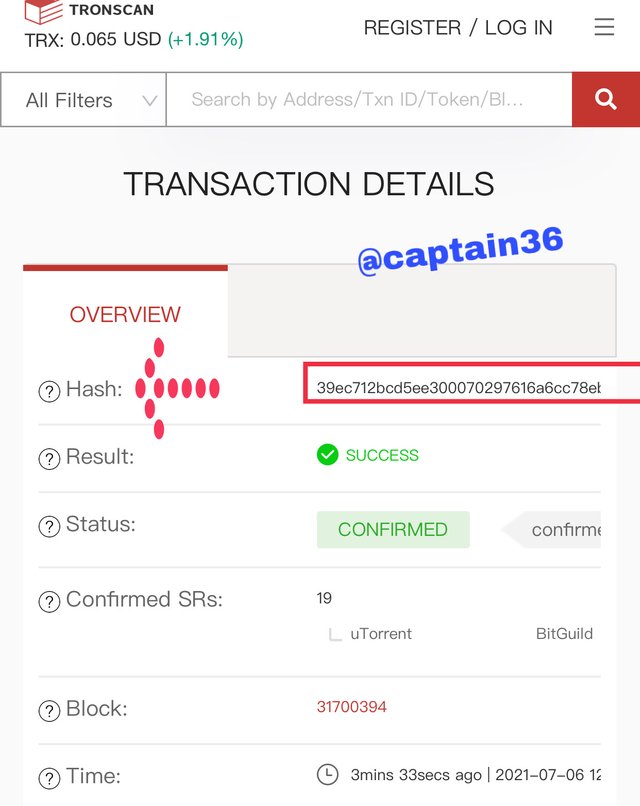
Screenshot: Tronscan.com

Etherscan.io
To verify the hash with Etherscan, I used the following link: https://etherscan.io/ At the beginning you can identify the Blocks and Transactions, by clicking on the last one that is displayed on the screen, you can view the details of the selected one below
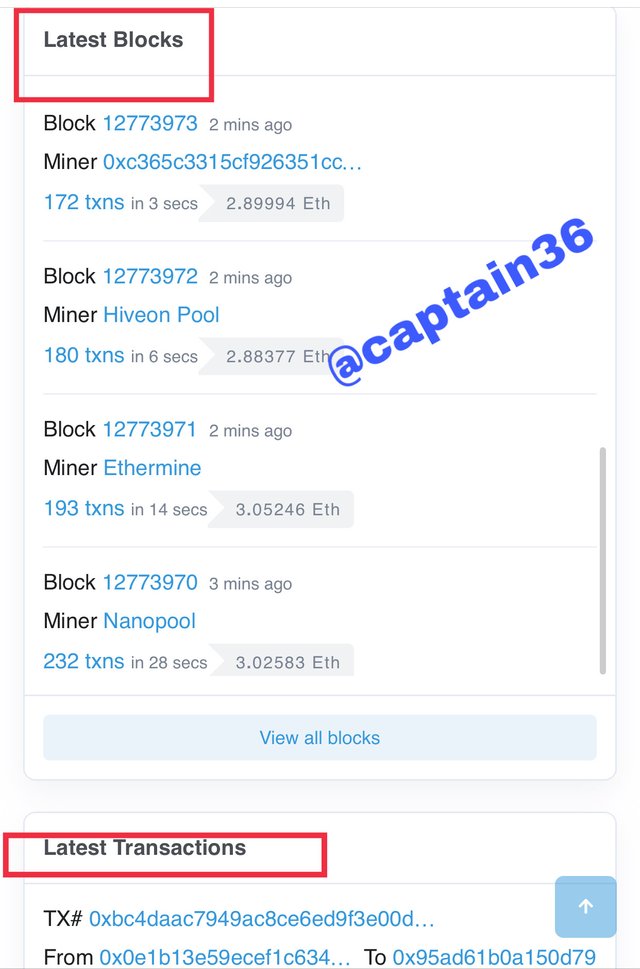
Screenshot source

At the time of publication, the last Block was identified with the number: 12773979, as shown in the image below.
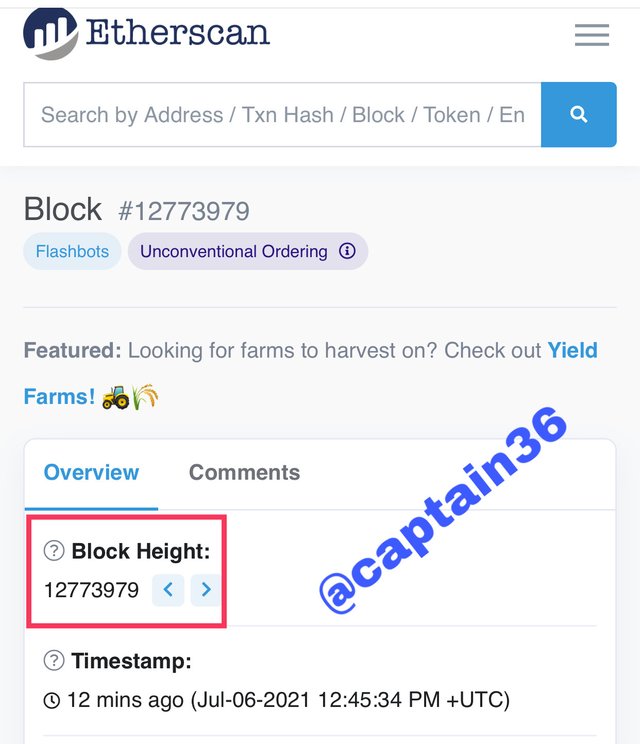
Screenshot: source

To verify the hash of the last block, you must move the screen down, where it shows: 0xf9bf521560cfa8efe2753a72f475cee8fbdfdae6b813fccc0ffaefa64c913ae4
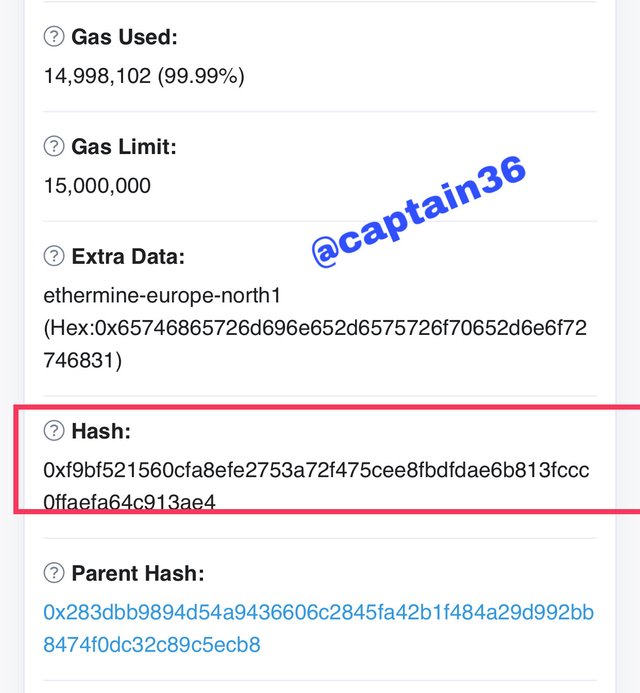
Screenshot: source

Then I go back to click on transaction, the details of the transaction was displayed.
The hash of the last transaction: 0x08fd1f0a02cf205ecdc3cf50c50dcea788807cb9b7d3d0cbfb24e1ce933e6126
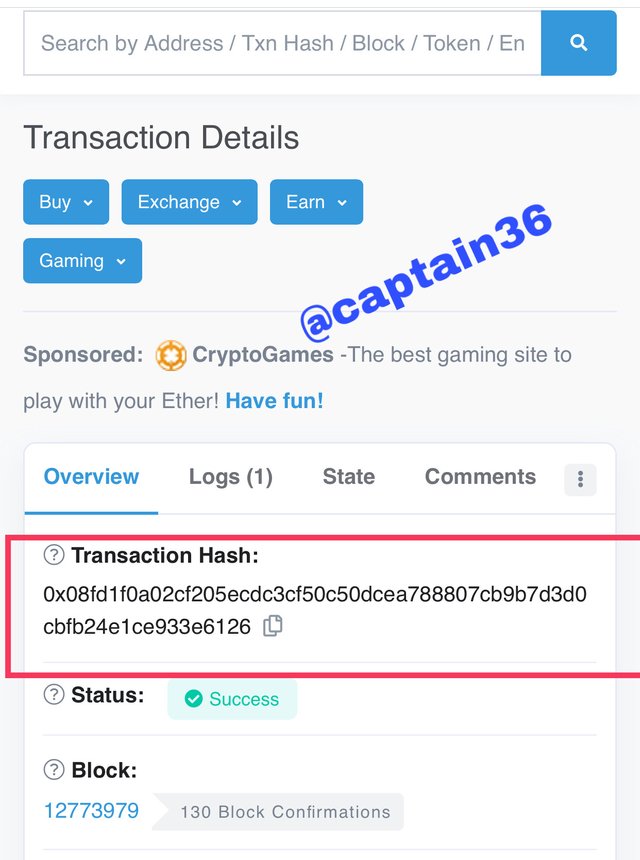
Screenshot: source

3.- Generate the hash using SHA-256 , from the word CryptoAcademy and from cryptoacademy. Screenshot required. Do you see any difference between the two words? Explain.
To generate the hash of the word CryptoAcademy and cryptoacademy, using SHA-256, I used the following link https://passwordsgenerator.net/sha256-hash-generator/
Simply put the word in the box and the hash is generated immediately, for the first word the hash generated was: 7B8ABC5E9238266CBA885E7EE43DB7256F69EC2E120D8706DB2A4AB704E85A43
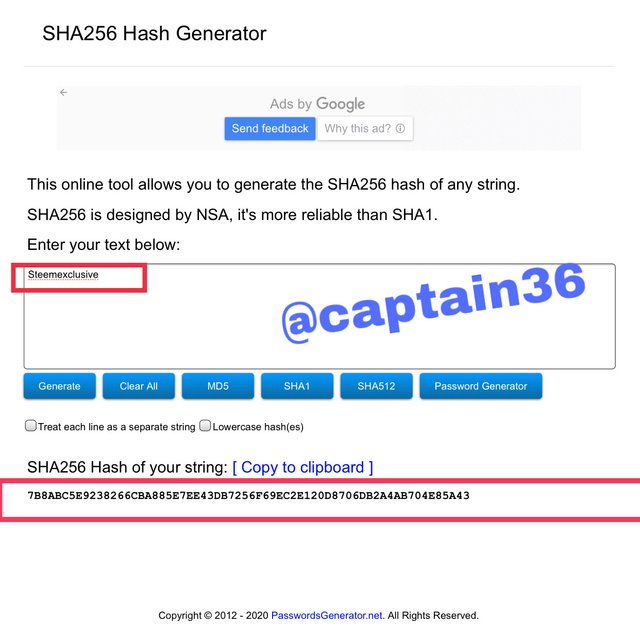
Screenshot:source

For the second word, proceed to change it in the box and in the same way generate the hash: DF12B8F89B61274C73291296EC828EAB61202F5863680EC6003682821D77FD31
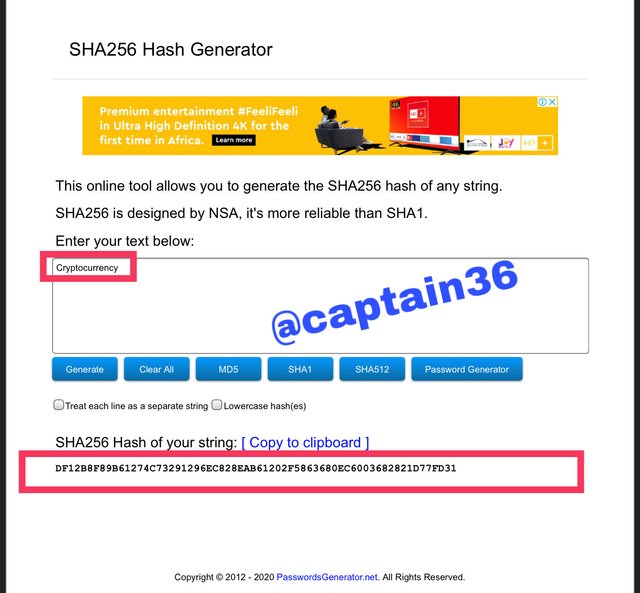
Screenshot: source

In the experiment above, the two different inputs generated hashes that are totally different. The first one was “steemexclusive” which produced a different hash to the second input which is “cryptocurrency.”
This shows the unique and unrepeatable function of hashes which generates a unique hash for each and every input.

4.- In your own words explain the difference between hash and cryptography.
| Hash | Cryptography |
|---|---|
| Hashing is not considered a form of encryption | Cryptography is broad field of study which covers both encryption and secure hashing. |
| Hashing is a one way mechanism | Cryptography is a two way process which involves both encryption and decryption. |
| Hash is a cryptographic function that generates unique and unrepeatable codes | Cryptography aims at preventing data and information based on security patterns |
| Hash is the main foundations of the decentralization of this platform | cryptography is the fundamental pillar of the blockchain for its operation, it can be considered the main axis of the ecosystem. |

Conclusion
From this topic by professor @pelon53, it is clearly evident the hashes and cryptography have been a very fundamental part in the security of the blockchain and cryptocurrencies. They provide security, privacy and anonymity that identify the blockchain.
These hashes have been very beneficial to the blockchain and it’s very crucial in developing this ecosystem.
👆 Esto no es Resistencia a la colisión.
La pregunta 3, no respondió lo que se le preguntó, colocó 2 palabras que no eran la que se le pidió.
Faltó investigar un poco más sobre la diferencia entre el Hash y criptografía.
Puedes mejorar, sigue adelante.
Recomendaciones:
Es necesario que observes bien las preguntas para responder de acuerdo a lo que se le solicita.Calificación: 6.0
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit