Introduction.

Image designed by me on Snappa
I am very excited to be a part of professor stream4u's class this week on let's open a blockchain. This week prof has explained to us what blockchain cryptography is, what digital signatures are, what public and private keys are, what and how a Merkle tree works, among others. He has also given us a task to perform.
I would now like to submit my answers to the task given.

The Blockchain Cryptography And Some Blockchain Platforms.
First of all a blockchain is a decentralized technology that uses a distributed digital ledger to store information and data on it's platform. This data cannot be altered because attempting to alter data on a single block will require re mining of all other blocks on all the computer serves linked on the network.
Cryptography as a term is a method or technology used to provide encryption and security of information between people by hiding the data sent. This way only the sender and receiver can have access to the information. The way this data is secured is through encryption and decryption.
Data is encrypted by the sender and the receiver uses a public key to decrypt the message. This encryption of data means the data is converted from readable form to machine language and decryption is converting the machine language data in random bits to readable form.
Knowing a bit about blockchains and cryptography, blockchain cryptography can be described simply as a way of securing blockchains through cryptography.
Blockchain cryptography is in two forms; the use of hash functions and the use of asymmetric keys.
From last week's lecture we learnt that a hash is responsible for validating blocks. A hash function is of fixed length of 14 alphanumeric combinations that has a huge amount of data which cannot be edited that is to be carried onto a block.
So the way cryptography secures blockchains through hash functions is by making sure that data on a hash is unique, uneditable and of fixed length no matter how huge or small that amount of data is.
Another form of blockchain cryptography is the use of algorithmic asymmetric keys known as private and public keys.
These private and public keys are used for signing and verifying blockchain data digitally. Private keys are specific to each user and so the owner of a private key uses it to secure his or her account and digitally sign transactions while using the public key to encrypt and decrypt data.
Examples of blockchain platforms.
Some blockchain platforms are;
Ethereum blockchain
EOS blockchain,
EOSIO blockchain,
Ripple blockchain,
Binance Smart Chain,
IBM blockchain,
Hyperledger sawtooth,
Tezos blockchain, etc.

The Public Key Cryptography.
The public key cryptography is one of the 2 asymmetric algorithmic keys used by users on the blockchain for identification.
Unlike the private key, this key can be shared with others. The public key is specific to its private key hence it is generated by the private key.
However, the public key is not used to generate the private key. The function of the public key is to serve as verification and identification on a blockchain and as well serve as an account that receives transactions.
To understand this better let's compare the public key to a bank account number. When making a transaction in a bank, you have your account number and password and the user you're sending the funds to has same. Here, everyone can see you and the other user's account number because that is what each user is identified by. You also notice that you send funds to that account and receive funds in your account number hence the account number is a public key.
The public key is also used by users to decrypt data sent and verifies transactions after the sender has sent transactions by creating a digital signature with his private key.

The Private Key Cryptography
The private key is the other component of the 2 asymmetric algorithmic keys that secures a wallet or account.
Having a private key signifies your ownership of a wallet because you are the only one that can have access to it.
I'm sure most of us here have one way or the other created wallets where we have generated seed phrases to obtain private keys. Even if we haven't done so, while signing up for steemit we are given both a public steemit key and a private steemit key.
This private key is unique to every user on steemit and is not to be shared by anyone.
We use the private key to perform all kinds of transactions on steemit which shows that we own our wallets because only we have access to our private keys.
Similarly, when making transactions in a bank, you enter a password known to just you to be able able verify and confirm that transaction you're sending to a public account. This bank account password serves the same purpose as your private key.
The private keys is used to generate and sign digital signatures as a means of verifying transactions.
Your private key allows you to have total control of your account and a hack usually occurs from your carelessness or mishandling of the private key.

The Digital Signatures Cryptography And Signing Of Transactions / Message.
When we say signature, what often comes into mind is putting your signature in ink on a paper or document usually to confirm to a contract.
However, signatures can be digital and there can also been cryptographic digital signatures.
Digital signatures cryptography is to verify information cryptographically by using private and public keys for encryption and decryption of data.
How digital signature is done here is by sending data to the hash function to generate hash data when the signer signs by activating the private key.
Cryptographic digital signatures remove the idea of forging signatures because a private key is used to sign and only 1 person has access to the private key.
So messages sent and signed cryptographically are authentic since they are decrypted with public keys.
Another feature or benefit of cryptographic digital signature is 100% originality of data. Data cannot be edited or deleted when it is signed but should there be a case where data has been edited, the hash value of the data becomes unverified and the digital signature verification of the receiver can't go through hence there is no situation of wrong or false data verification.
Digital Signatures authenticates data received with private keys and removes doubt or dishonesty by verifying data or hash with the public key.
What Is Signing Of Transactions?
--
To understand what signing of transactions is, let's consider the diagram in the image below.
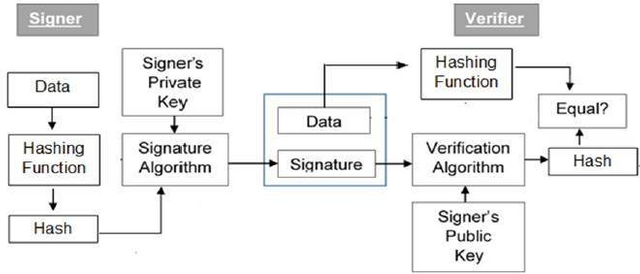
First of all a private and a public key is required for data encryption and decryption.
The process is in 2 forms; signing or identification and verification.
The private key of the sender or signer is used for signing and the public key is used for verification by miners.
The signer sends data to the hash function where a hash data is created.
There is what is known as "signature algorithm" or identification algorithm which receives the hash data created and the signature key.
The signature of the signer is then sent to the verifier along with the hash data.
The public key of the signer is entered into a "verification algorithm" to verify the sent signature which produces an output data.
The hash function that was sent along with the signature is also put into the verification algorithm to receive verified hash value as output.
The hash value and the output data received from verifying the signature is compared and from the results it is decided of the signature is valid or has been tempered with.

Symmetric and Asymmetric Cryptography.
Symmetric and Asymmetric cryptography are the 2 forms of blockchain cryptography that makes use of the private and public keys. Below is an elaboration on these forms of blockchain cryptography.
What Is Symmetric Cryptography?
Symmetric cryptography is a form of cryptography where only one (1) key is used for encryption and decryption of data.
In this cryptographic type, the private key used by the sender to encrypt data from plain text to machine language is the same private key used by the receiver to decrypt the same data from machine language to plain text.
In symmetric cryptography, the computational power used to generate keys, share and store files is less and so it is kind of eco friendly as compared to asymmetric cryptography. There must be trust that exist among those sharing the same private key to avoid problems.
There are 2 types of Symmetric cryptography; block algorithm where data is encrypted as one and stream algorithm where data is encrypted separately one after the other.
Examples of Symmetric cryptography are Data Encryption Standard, Advanced Encryption Standard, Rivest Cipher 4,5, etc.
Asymmetric Cryptography.
Asymmetric cryptography is the second form of cryptography where two (2) keys are used for encryption and decryption of data.
In asymmetric cryptography the public and private keys are used. The private key here is known to only one person or the sender of the data which is used for data encryption but the public key is used for decryption of the data.
Like already explained above, the previous paragraphs, the public key is similar to that of a bank account number and the private key is similar to that of a bank account pin or password.
So if I want to send data to my brother, I would use my private key to convert the readable format of my data to computer form and my brother would use my public key to convert that computer form data to readable form.
In this form of cryptography, there is no need to trust each other because only you have access to your private key and data can't be edited.

How Blockchain Wallets Cryptography Works And The Available Types Of Crypto Wallets.
Crypto wallets are software types or devices used primarily to store crypto assets. However crypto wallets of the modern age do more than just store cryptocurrencies but also allow users to connect to DApps and involve in staking and other activities to earn rewards.
Crypto wallets consists of 3 things or use 3 things to perform transactions. Theses include; wallet address, private active key and public key.
Crypto wallet private active key is used to sign transactions and should be known to only the owner of the account. The private key here is also used to import the wallet should you forget your password and want to open it on maybe a different device.
Crypto wallet public key is used to validate the private key of the signer. Miners use the public key of the sender of transactions or data to verify that the private active key used to sign is valid.
Crypto wallet address is a unique and of to every user. Crypto wallet addresses are unique to every user because these addresses are used to receive funds from other users.
The wallet addresses are shared with other account users who intend to make transactions to that account. Hence crypto wallet addresses are not private.
Before you send your wallet address to a user to receive tokens you must make sure it is correct because lost funds cannot be retrieved. Likewise, you must make sure the address you are sending funds to is accurate.
Types of Crypto Wallets.
Software or hot wallets.
Software wallets are wallets that are used online. They can be referred to as hot wallets. Types of software wallets include;
Mobile wallets where the online wallet is easy to use on your mobile device. Example is trust wallet.
Desktop wallets where the online wallet is on your desktop computer and the wallet can accessed only with that desktop. Example is Binance Smart Chain extension (BSC).
Generally, because software or hot wallets are online, they are vulnerable to attacks since the private keys are stored online. Hackers can develop links so that when you click on such links your private active key is displayed to them.
Hardware wallets or cold wallets.
Hardware wallets store keys of users offline in devices such as flash drives but perform transactions with the help of internet access.
The similarity of hardware wallets with that of software wallets is that they both perform transactions online but the difference is that online wallets store keys online while software wallets store keys on hardware devices.
Hardware wallets are more secure because assets and keys are stored offline and only made available online when transactions are to be made.
Example of hardware wallets are Nano X and Trezor.
- Paper wallets are cold wallets which contains private and public keys as well as QR codes on a printed piece of paper.
Paper wallets are regarded as the most secure wallet types. Transactions from paper wallets to other wallets is easy as you just scan the QR code or enter the key manually to sign and transactions from other accounts is simpler as you just need the wallet address.

The Merkle Trees And It's Importance In The Blockchain.
The Merkle tree since its introduction by Ralph Merkle in 1979 has become very integral to blockchain technologies.
The Merkle tree is aimed to make verification of data faster regardless of the amount of data maintaining the high authenticity and security.
Cryptocurrencies that use the Merkle tree include bitcoin and Ethereum. Blockchains with their introduction have a problem of the computational power used in validating blocks. It is very expensive and energy consuming to validate blocks and that is a problem the Merkle tree has solved.
The Merkel tree ensures that large amount of data and transactions are validated faster, with high security and with less computational power.
The Merkle tree has a Merkle root and Merkle leaf. Each leaf contains a hash data and is at the bottom of the Merkle tree.
The Merkle root is the single output code the Merkle tree produces resulting in a unique root to each block of the blockchain. Let's consider the diagram below;
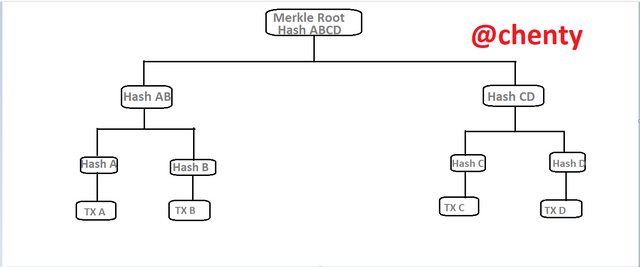
I drew this diagram on paint application
In the diagram of the Merkle tree above, the leaf nodes hash A, hash B, hash C and hash D have their individual transactions; TX A, TX B, TX C and TX D can be found at the bottom of the tree giving us 4 blocks.
These individual 4 hashes are paired to produce hash AB and hash CD in the tree layer giving us 2 blocks.
The 2 resulting hashes hash AB and hash CD are paired to result in the root hash; Hash ABCD in just 1 block.
These method employed by the Merkle tree where individual data hashes of separate blocks are paired to further reduce the blocks and finally result into 1 output hash known as the Root hash is termed as the Merkle tree.
It should be noted that when the individual nodes are uneven, the last leaf is duplicated hence the transaction of the last leaf is duplicated as well. This results in an even root hash.
Considering the diagram above, if there was no leaf hash D, hash C would be duplicated and we would have hash A, hash B,*hash * and hash C again. This pairs to result into root hash ABCC.
This is a very fast and energy efficient way of verifying and validating blocks in a blockchain without security vulnerabilities.
Importance of Merkel Tree.
The Merkle is cost effective as less computing power is needed.
The Merkle tree is eco friendlier as it uses less computational power.
Memory or storage required to store data is not much.
The Merkle tree validates data and blocks faster.
Data on any of the hashes cannot be edited but in the case where one is edited, the other hashes are invalid resulting in an invalidated root hash.

Practical+ Theory Demonstration On Blockchain Demo : Public / Private Keys And Signing.
In this section, I would explore the functionalities of keys, signature, transaction and blockchain on blockchain demo
Keys.
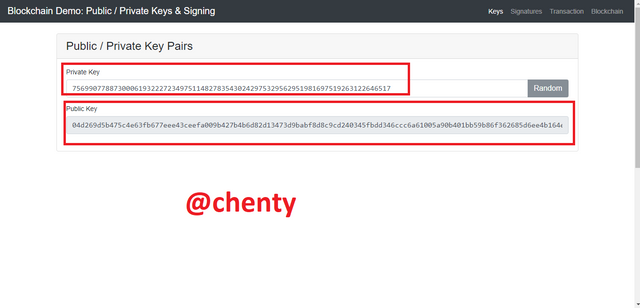
Like already established, public and private keys are used together in asymmetric cryptography. Private keys are used to generate public keys and hence every unique private key has its unique public key.
- For every private key there is a public key. In the screenshot below, the private key; 75699077887300061932227234975114827835430242975329562951981697519263122646517 is randomly generated producing its unique public key; 04d269d5b475c4e63fb677eee43ceefa009b427b4b6d82d13473d9babf8d8c9cd240345fbdd346ccc6a61005a90b401bb59b86f362685d6ee4b164e1283e6dcb78
- To manually generate a private key, I entered 1111 as private key which immediately produced the public key 0428b7f3a019749cce6fc677afa8fae72ec10e811ed4b04e1963143cef87654b75030471eb3245ab391597c881e71f4a1de241ba31a678fe392ced5a63845ec782
Signature.
The signature like already establishes is usage of the private key to encrypt data and sign while the public key is used to validate the signer's private key.
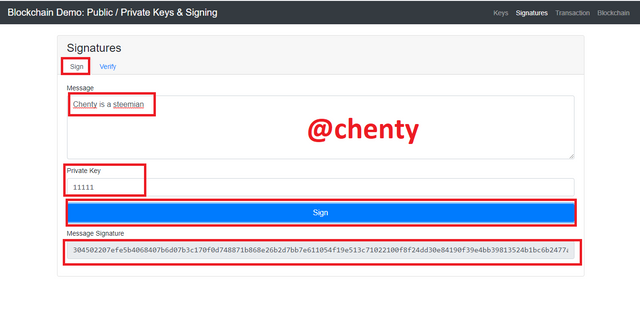
- In the signature section I will be signing the message Chenty is on steem with private key 11111as shown in the screenshot below.
I clicked on sign and the signature was 304502207efe5b4068407b6d07b3c170f0d748871b868e26b2d7bb7e611054f19e513c71022100f8f24dd30e84190f39e4bb39813524b1bc6b2477aed70a8878c1d7f4a8752ecb
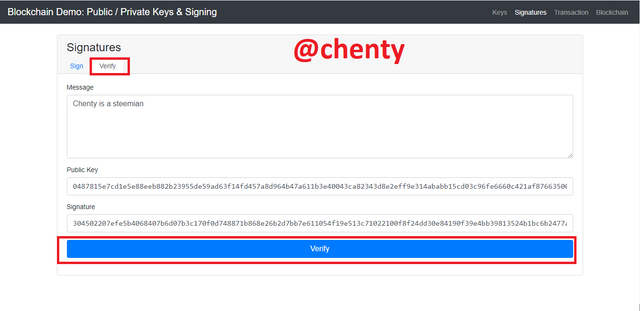
To verify the private key, I clicked on verify beside sign and a public key; 0487815e7cd1e5e88eeb882b23955de59ad63f14fd457a8d964b47a611b3e40043ca82343d8e2eff9e314ababb15cd03c96fe6660c421af87663500d49ade0d492was displayed with my message and signature.
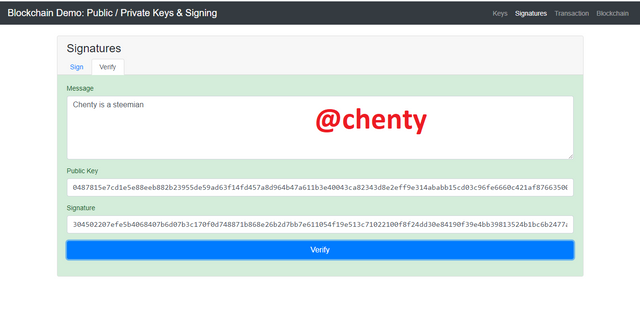
I then clicked on verify and the green indication shows a validation of my private active key 11111.
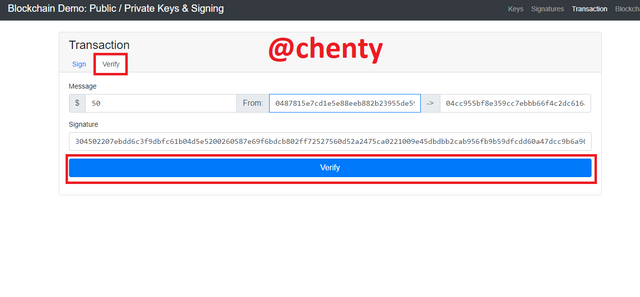
Transactions.
- In this section, I will be making a transaction of $50 with private key 11111 and its unique public key already produced. Click on sign to get the signature message.
The $50 is being sent from 0487815e7cd1e5e88eeb882b23955de59ad63f14fd457a8d964b47a611b3e40043ca82343d8e2eff9e314ababb15cd03c96fe6660c421af87663500d49ade0d492 to wallet address 04cc955bf8e359cc7ebbb66f4c2dc616a93e8ba08e93d27996e20299ba92cba9cbd73c2ff46ed27a3727ba09486ba32b5ac35dd20c0adec020536996ca4d9f3d74
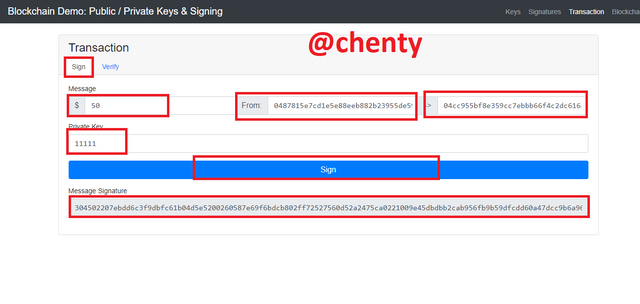
The message signature generated is 304502207ebdd6c3f9dbfc61b04d5e5200260587e69f6bdcb802ff72527560d52a2475ca0221009e45dbdbb2cab956fb9b59dfcdd60a47dcc9b6a96236e56a6119785e7e54845a.
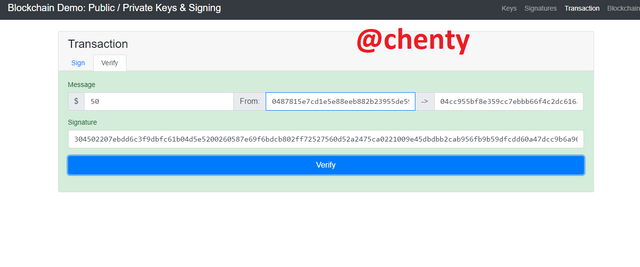
To verify the transaction, click on verify beside sign and click verify at the bottom of the page. The page changed to green indicating that the transaction is valid.
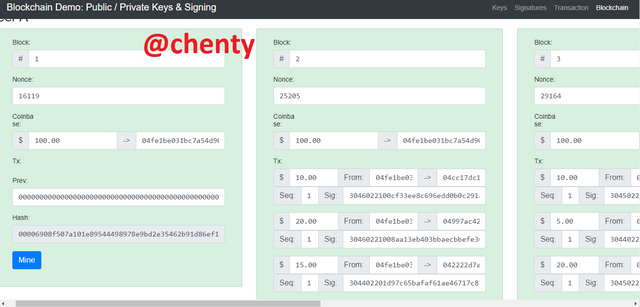
Blockchain.
- When you click on blockchain, by default all the blocks are valid and so appear green.
- I would be making changes to block #2 so that we see what happens. I changed the transaction from $10 to $105 and immediately block 2 and all other blocks after 2 turned red. The indicator of red color means the blocks are invalidated.
The signature also turned red.
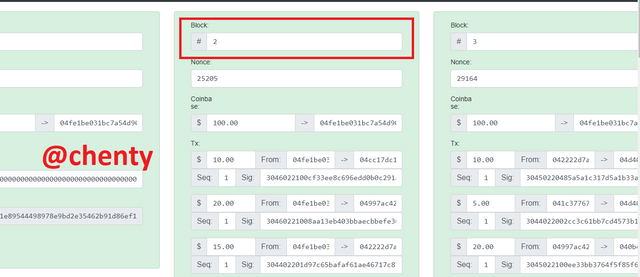
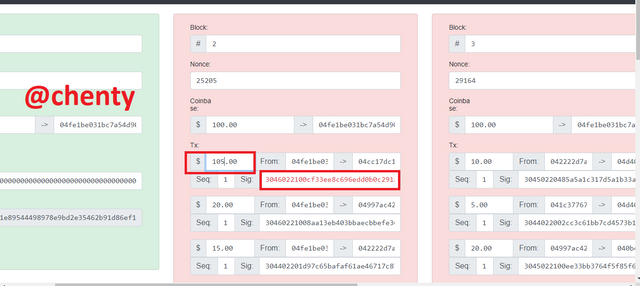
- To validate the block #2 you have to re-mine so I clicked on mine. It is noticed that the color of block #2 changes to green but the signature still remains red. This indicates that there was an alteration in the signature of the transaction. This means that the private key that was used to sign the transaction of $10 is does not match the public key of the valid new transaction of amount $105.
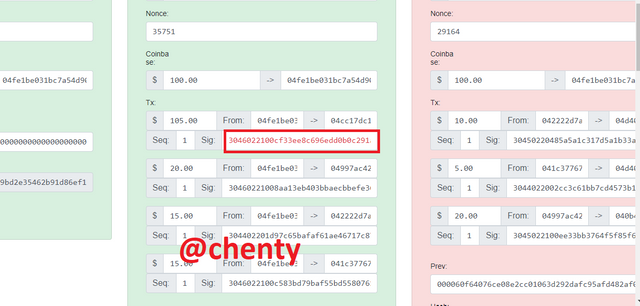
Even with the re-mine and validation of block #2, the blocks after block #2 are still red and invalid.
This proves that when data of a signed transaction is altered, the transaction is not verified in that block and the subsequent blocks because that altered data isn't what was signed by the private key and so the public key cannot verify that transaction.
Conclusion.
I must say thank you to professor @stream4u for this very informative lecture as always.
Cryptography is a means of securing blockchains by the use of private and public keys. Private keys are known to just the owner and public keys are known to others because it is what identifies a user.
Digital cryptography signing is using your private key to sign and encrypt a transaction while using your public key to verify that transaction and the signature of the signer.
The Merkle tree ensures that data is validated faster without any security compromise but using less computer power.
From the lecture, I learnt symmetric cryptography uses only a private key which is not a secret to just 1 person but the senders and receivers where as the asymmetric cryptography uses both private and active key to encrypt and decrypt data.
Crypto wallets are software or physical devices used to store cryptocurrencies. Hot wallets are software wallets that save keys online while cold wallets or hardware wallets make use of saving keys offline.
I was able to practically understand the functionality of keys, blockchain, signature, transactions and blockchain.
Thank you.