
EXPLAIN IN DETAIL THE P2SH AND P2PKH, SHOW THE DIFFERENCES BETWEEN BOTH DIRECTION

Prior to the implementation of P2SH, senders were clueless on the standard way to implement the scripts. Although they could easily lay their hands on the customized scripts which weren't user friendly and at worst, time consuming for most users to write. This complexities was simplified by P2SH by a simple to use script hashes.
P2SH is one script format th toat allow users to lock up their Bitcoin cryptocurrencies in a script hash and then provide the full script on the other hand at the time of transaction when the bitcoins will be unlocked. One exciting thing about this feature is the fact that with allow transaction without conventional programming. From the year 2012 till date, many cryptos including bitcoins have adopted the pay to script hash rather than a public key hash.
Advantages
Security: The inclusion of complex set of instructions in P2SH transaction ensures the script maintains a high level of security.
User friendly: It reduces the workload on senders having to write complex logic on the recipients behalf. on that note, transaction on P2SH can be carried out by simply sending to an address starting with number 3.
Computationally efficient: Less RAM is required for the unspent transaction output and this increases the speed of transaction.
Limitation
- Single signature: P2SH was specifically developed to salvage the multisig wallet. By this, it insinuates that other script types fits in for single signature transaction.
P2PKH
P2PKH is an acronym for pay to public key hash. This is the type of transaction users engage in when they decide to move a specified amount of Bitcoin through a wallet interface from one address to another. The P2PKH happens to be one of the popular ways to carry out transactions through scripts. The network resorted to the script P2PKH for a guaranteed high level of security and protection in the network.
Just like what we have in P2SH, users in P2PKH has to demonstrate a cryptographic mechanism which is based on proving their true ownership of the public key to get paid and the private key to spend the pay they've received.
In P2PKH, the recipient needs to create a public and private key pair and upon creation, share the public key with the transaction issuer. In the process of encoding the keys, the receiver will need to create a hash of public key to carry out transactions. That hash serves as our crypto address. Now, the issuer will need to prove that the Bitcoin address is really his before he can spend the bitcoins they've received to their owned public address. To do this, they need to provide the exact public and private key to be able to unlock such expense.
Advantages
Highly secured: It reduces the chance of attacks from other quantum computers.
Ease of use
Limitation
- Complexity: In as much as the P2PKH addresses are simple to use, the processes to embark on creating those addresses are much more difficult than what we see in P2SH script.
Differences
Its transaction output script in P2PKH uses signature and public key hash in order to spend the payment. While in P2SH its transaction output scripts executed with parameters that Will only result in true or false.
The method of transactions employed in P2PKH transaction coverts the public key in a hash form for more security while in a P2SH, if a miner was able to run the output script with the exact parameters and arrive at "true" the pay will be sent to his desired output.

IT IS REQUIRED TO TRANSFER 10 BTC THAT BELONG TO A 3 OF 5 MULTI-SIGNATURE PORTFOLIO, TO THE MTC COMPANY, FOR THE PURCHASE OF SOME EQUIPMENT.

I will be using the scriptsig and scriptpubkey to explain the steps that are followed.
For this transaction to executed, there are certain conditions to be met which is that 3 addresses out of the 5 must sign the transaction of 10 BTC. The 3 addresses will require their private keys to execute such transaction. The process of executing such transaction could be scriptsig and scriptpubkey.
Illustration:
If 5 addresses are to be used for transactions of 10 BTC to the MTC, the private key of 3 out 5 addresses will be required to authenticate the transaction.
The confirmation of the 3 addresses which provides their public key are done through OP-CHECKMULTISIG. Upon confirmation, there scripts unlock the funds but in the alternative, the transaction will be cancelled.
What happens if the transaction is made using schnorr signature?
The transaction will take a different mode of it was made using schnorr signature this is because the supposed 5 addresses will be merged together and the outcome of this is a single transaction kept invisible that no one will have a trace of the origin of the new transaction key and this keeps the whole process safe and private.

WHY DO YOU THINK THAT TAPROOT AND SCHNORR FIRMS WILL HELP THE PRIVACY OF THE BITCOIN NETWORK? EXPLAIN.

Firstly, it'd be noted that the schnorr signature and Taproot signature are both incremental changes to the Bitcoin network. So while Taproot facilitates the capabilities of Bitcoin smart contract, schnorr signature reduces network fees as well as increase privacy basically for multi signature transactions. With Taproot transaction made through P2SH and P2PKH cannot be distinguished thereby making the transactions more private.
I believe Taproot and schnorr signature firms will help the privacy of the Bitcoin network firstly being that Taproot offers such improvement that facilitates the capabilities of Bitcoin smart contract. Also, for schnorr signature which increases privacy for multisig transactions is of great impact to the privacy of the Bitcoin. By this, users need not make physical scripts other than the ones used in signing transactions.
Again, the Taproot signature will simplify the Bitcoin Blockchain data and this feature will attract alot of persons to sign up for the project in lieu of seeking opportunity to create smart contract in the Bitcoin network.
With schnorr signature, large transactions can be compressed by reducing the size of transaction while signing in the address and this makes transaction more secured, easier and cost effective.
In all, the Taproot and schnorr firms aims to help the privacy of the Bitcoin network by doing away some problems like lack of security and privacy which has posed a threat to the Bitcoin network.

USING THE BLOCKCHAIN DEMO, WRITE EXACTLY THE FOLLOWING MESSAGE: SCHNORR SIGNATURES, GENERATE THE MESSAGE SIGNATURE AND VERIFY THE MESSAGE

To do this, I have to perform this operation using Blockchain demo for which upon visiting the website, I clicked on signature and then inputted schnorr signature on the message space and then click on sign.
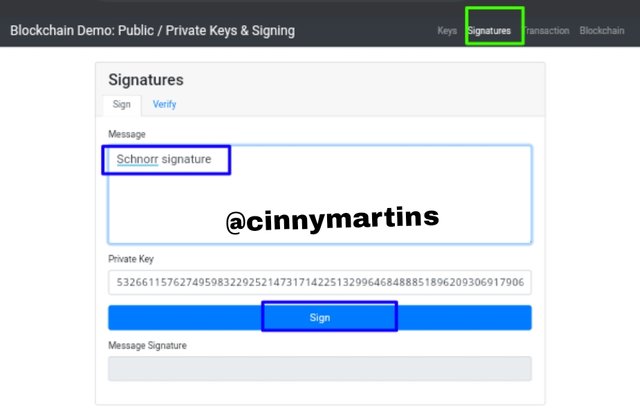
Upon completion, a verify box pops up with a code
304502204a4813318f850e15472ee2df02cd69c5cc15ef5064a9254f205bfb1656a1e19f022100e8473d9f66c7a9079ff6ff62511e1615c1260f0c9cef1d36df942706e9620253
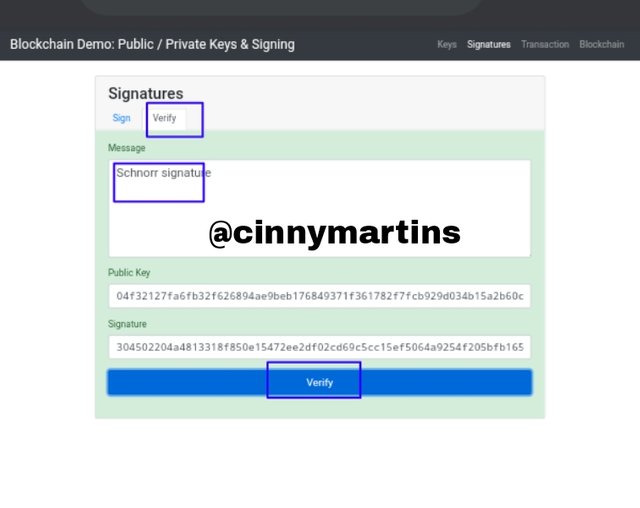
Now, upon clicking on verify you would notice it was successful evidenced by the green background as seen above.
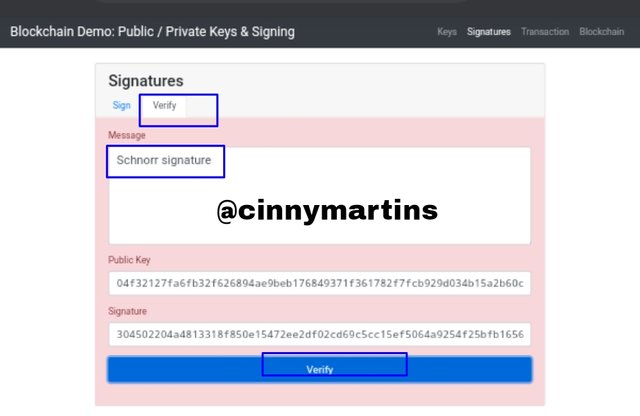
But the image below had a red background because I edited the last alphabet from the code which made it wrong meaning that the code was not verified.

CONCLUSION

Actually, was a nice lecture from Prof @pelon53. I must say that before now, the subject was blurred to me but going further, I learnt about the principle of pay to script hash and P2PKH the aim behind the development of these two projects. I also learnt about the Taproot and schnorr signature and their effects to the Bitcoin Blockchain.
Finally, I'd like to say a hearty thank you to the professor for such an erudite rendition.
Merry Christmas
Cc.
@pelon53