We could see how in week 4 we learned a lot about the world of Yield farming, and how interesting and important it can be for our finances, that is why in this task I did not hesitate to join your class, since I am sure that I will learn a lot about this topic.
Let's all learn together, don't miss it!

1) What is Blockchain and what are the types of Blockchain?
• Blockchain:
The blockchain network is a technology that has come to renew the computational world, since it presents us with a more feasible and secure proposal to operate and protect any file, being totally decentralized means that there are no intermediaries or third parties to execute operations, therefore , makes your network much more scalable and efficient. As its name says, it is a chain of blocks that communicate with each other with each of them, where in each block digital information of the network that uses it is stored, such as:
• Smart contracts
• Transaction information
• Important data of the network that implements it
• Blocks information
Whose information cannot be altered, changed, or falsified, therefore, makes millions of users decide to implement their services. We could see it as a digital record where any type of information from the network that implements this technology is stored and protected, and the best of all is that once it is registered in the blocks, its original content cannot be changed and it can be reviewed anytime you want.
We ask ourselves, how is it possible that blockchain is so secure and that no information contained in the blocks can be altered? It is simply very simple, because all the blocks that the chain has are distributed in the same way, and each of the nodes that they have, contain the same information in each of them, therefore, in case of a future attack on the network, they would have to manipulate each of the nodes that each block contains, which can become almost impossible, however if there is the small possibility of hosting a 51% attack.
The information contained in each of the blocks in the chain goes through a meticulous validation process by the nodes, and how much everything is correctly secure, is integrated into the blocks. That is why we can see how blockchain is very safe and reliable, because we can keep our information safe without fear of being altered or stolen, and this is partly because all the blocks in the chain have the same information. of the Hash of all the blocks.
Then we can see how blockchain gives us a more feasible and secure way to protect any type of information, be it personal information, health, business work, data of our workers, of our applications etc. But in a totally decentralized and very secure way, since we can see that this information will not be altered or stolen, and it will be kept in an original way all the time.
• Types of blockchain:
Currently there are several types of blockchain that adjust to the conditions that users require, therefore, we have several options at our disposal to choose the one that is most feasible for us, that is why I will talk to you in detail about some:
• Public Blockchain: As its name implies, it is totally public for users, but without leaving aside the issue of decentralization, since it does not need Intermediaries to function properly.
This type of blockchain is one of the first that has existed and thanks to it, we can see detailed information on any subject, and this is simply through the internet connection, as is the case with crypto assets, where we can look at relevant data such as its development, its software, its project and any significant information relating to it.
The public blockchain works without neglecting security, which continues to guarantee that no malicious entity can alter or change the public information that blockchains have, that is why one of the main tools to combat security is "Byzantine fault tolerance", since it has the ability to verify the information that enters the blockchain, and in the event of any failure or error, it will guarantee that it does not affect the network.
In summary, we can conclude that the public blockchain benefits us in:
• It offers us security and transparency, since being public we can look at relevant data of any subject only with an internet connection, as in the case of cryptocurrencies, however, we cannot alter it or change the original information.
• Being public, it allows mining users to participate in the network to improve its development, without any problems.
• When we talk about public it does not mean that it is centralized, on the contrary, this blockchain is fully decentralized and highly effective.
• It is very accessible in all areas, we can already implement the use of the public blockchain in very common areas, whether for companies, businesses, or to save any information that we do not want to be altered.
• Private blockchain: Of course we also have the case of the private blockchain, where it is totally opposite to the previous one, since here not everyone can be within reach of the required information, since a order as a web interface that gives us the link to get to said information.
In the case of safeguarding very private and secure information, the private blockchain is ideal for this, since not all users are within reach of said information, since its operation is based simply through few nodes that take care of maintaining security and privacy first and foremost. As it is not available to everyone, it makes your security much more effective, preventing malicious attackers from damaging the network.
In summary, we can conclude that the private blockchain benefits us in:
• It gives us greater scalability, since the nodes of the network are not so saturated when verifying that the information is altered, that is why the number of nodes decreases in this blockchain.
• The issue of security increases on a large scale, since being private, it is not available to all users, which makes it more difficult for an attack to occur.
• It is ideal for large companies and businesses that want to protect important information on their network, so the private blockchain gives them security and privacy.
• It is widely used by large government entities to protect files and prevent them from being altered.
• Hybrid blockchain: This blockchain is a combination in conjunction with the two blockchains mentioned above, that is, the public and the private, where it is responsible for uniting a small part of both worlds, to present us with a different alternative where we can implement two services in one.
We will ask ourselves, how is it possible to achieve this? How does the fusion between the public and the private work at the same time? Simply this hybrid blockchain allows us to publicly access the accounting book that contains any type of information on the movements of the network, however, to join it, certain permissions of the nodes are necessary, which means which is totally private, but nevertheless we can access other data in a public way.
Then we can see how the union between public and private is perfectly integrated, therefore it benefits us in some aspects, such as:
• It is an innovative and different way of offering us the integration of both worlds, as is the case of the private and the public.
• We continue to maintain the same security and privacy measures that characterize it, but in a totally decentralized manner.
• The implementation of this hybrid blockchain to new companies or current businesses gives it the advantage of offering two feasible alternatives to operate differently.
• Scalability continues to be one of the main factors of the hybrid blockchain, since having a private part, makes the network nodes less saturated.
To conclude, we can see how each of the mentioned blockchains offer us different alternatives to operate according to our needs and conditions.

2) What are the benefits of blockchain?
After talking in detail about the blockchain and the types that exist, it is important to emphasize the great benefits and advantages that they offer us for our use, that is why I share some of them here:
• Innovation: This blockchain technology presents us with a new way to protect our data and information, but in a more innovative, secure, private way, and best of all, it is totally decentralized, which gives us greater advantage.
• Decentralization: As I said before, blockchain is totally decentralized, which means that it does not have any central entity that regulates it or is aware of its movements.
Blockchain works independently through nodes that are in charge of verifying the information entered, and best of all, the information is never altered or changed.
• Different alternatives: As we could see, this technology offers us several types of blockchain so that we can have different alternatives when we need their services, such as public, private, and hybrid .
That is, we can choose the one that best suits what we are looking for.
• Total security: As we know, once the information is entered into the blockchain, it cannot be changed or altered, therefore it offers us the security that this data is not pirated in other places.
And this is due to the different mechanisms with which the blockchain works, which makes it provide us with guaranteed security, such as:
• The work of the nodes
• Byzantine fault tolerance
• The algorithms it works with, etc.
• More feasible: Current and conventional technologies do not provide us with the same advantages that blockchain technology can provide, for example:
• Greater scalability
• Greater efficiency
• High security
• Speed in transactions
• Privacy
• Decentralization
• Implementation in industries: As blockchain technology spreads throughout the world, more and more industries, companies, businesses, and finance decide to implement their services, therefore making the industry in general, it is updated and developed in a totally different way, helping it to improve in its different areas.
• Financial area: Such is the case in the financial area, we have been able to see how decentralized finances have been bringing many benefits to millions of users around the world, therefore, the use of blockchain technology in Finance has brought us a series of advantages to our economy in a remarkable way.
As we know, there are currently millions of cryptocurrencies that decide to implement their services, and that is why we have been benefiting more and more from the implementation of both worlds.
We have been able to see how there are many benefits of blockchain in different areas, that is why we must make the most of this incredible technology for our daily use.

3) Explain the Blockchain Distributed Ledger.
The blockchain distributed ledger could be defined as the central heart of it, because as its name says, it is a book where all the information that occurs on the network and in each of the blocks it contains is stored in detail. Thanks to the distributed ledger we can check and keep organized control over each operation or information that is executed at every moment, for example in the case of companies or businesses, the ledger gives them many advantages, since they can look in detail and keep a safe control on the operations that are carried out in it.
The ledger registers any movement that takes place on the network, and thanks to the different mechanisms it has, it makes sure that the information cannot be altered or changed at its origin. We can put a clear and consistent example as is the case of cryptocurrencies, where the ledger works to maintain a kind of database where each of the operations, transactions, or movements that are executed in the network of said currency.
So we can say that thanks to the use of the ledger in the blockchain, the network can have better control over the data that enters the blocks at all times, therefore, this makes the network work in a correct and organized way, guaranteeing total security. One of its main characteristics is the transparency it has, since as we know, we can openly look at each of the different operations and information that are handled on the network, but without neglecting decentralization.
That is why the ledger forms a key and fundamental piece in the implementation of blockchain, since the union of both makes the network work in the correct way, guaranteeing that the incoming information of each block is kept completely safe and immutable. . In turn, it also helps the nodes of the network to obtain the necessary and specific information from each of the blocks, in order to have better control over security.

4) What is Blockchain Double Spending and how does Bitcoin handle this problem?
Double spending is one of the biggest and most feared fears that can occur in a cryptocurrency network, as it can lead to major problems and losses in your system. This type of attack is carried out by malicious agents who seek to multiply the same currency several times through various operations, thus managing to obtain more money than they own, through fraud and manipulation.
We will ask ourselves, how is it possible for this type of attack to happen? There are simply many factors that influence this to happen, one of them are:
• It only occurs in digital money, since in physical money it is impossible for a double-spending attack to occur.
• When the buyer accepts a transaction without it being fully confirmed, it makes the double spend attack more prone on the network.
• One of the highest possibilities of a double-spend attack occurs when a cyber attacker mines the blocks of said transaction and changes them in order to create another alternative that can work for the double-spend transaction.
• The information or data of a currency is almost impossible for it to be altered or changed, however, it can happen, and when this happens it is more likely that the double-spend attack will occur on your network.
• When a 51% attack occurs where the majority of malicious nodes agree to falsify information, it is very likely that a double-spend attack will also occur on the coin network.
When the network of a currency does not have adequate security in its system, it is easier for any type of harmful attacks to be carried out, especially double-spending, since data and information are more subject to manipulations and scams. How can we avoid this type of attack? For sure there are several parameters that we can avoid so that this type of attack does not happen, such as:
• Wait for all the confirmations of a transaction to verify that it is completely safe and that we can continue with the rest of the operation. Otherwise, if we don't wait for confirmations, we are very prone to double-spend attacks.
• We must ensure that we work with a currency that is strong enough in its network, and that it works with a good consensus algorithm, so that it can avoid this type of attack that can cause us losses.
• How does Bitcoin handle this problem?
We all know that this currency is one of the most important in the cyber world, therefore you must implement security measures to avoid any type of attacks that may affect your network, that is why name some of them:
• Hash Rate: The BTC or the currencies derived from them have a great advantage, and that is that they work with the Hash Rate which is a computing power that tells us for sure how strong and safe it is the mining network of a coin. The higher your Hash Rate, the lower the level of any type of attacks and errors from malicious nodes, and the lower your Hash Rate percentage, the greater the chances of any type of attack.
The Hash Rate avoids problems that may arise in your mining network, and looks for a solution if there is one, to ensure that no type of attack occurs.
• (PoW): The cryptocurrency with the most dominance in the market works is its consensus algorithm "Proof of work", where thanks to it it avoids this type of double spending errors, since Mining nodes are in charge of validating and verifying each of the transactions, to later be included in the blockchain, where they cannot be changed or modified.
However, one of the most important characteristics is that if a transaction is not confirmed, it will not be included in the blockchain, therefore, this avoids any type of attacks such as double spending.
• Six confirmations: For a transaction to be completely safe and reliable, it is necessary for the BTC operation to have six confirmations, after which it is completely safe and reliable. This is one of the great characterists that this currency has to avoid the double spending attack, and it is that after six confirmations the operation will be completely safe.
• Validation process: When a transaction starts, it has to go through a verification and validation process by the nodes, and then be included in the block chain.
When a cyber attacker wants to carry out a double spending attack on the BTC network, the nodes would automatically confirm and validate the initial operation and it would be sent to the recipient and then to the blockchain, while the other one, being unconfirmed, would be automatically discarded , managing to avoid a scam in the system.
Then we can see how Bitcoin presents us with very feasible alternatives to avoid this type of double spending attacks on its network, managing to avoid large economic losses.

5) Explain in detail how block hashes work in Blockchain, what happens when any central part of the block is changed?
• The first thing we must do is enter your home page:
• We will click on the blockchain section, and it will immediately show us 5 available blocks.
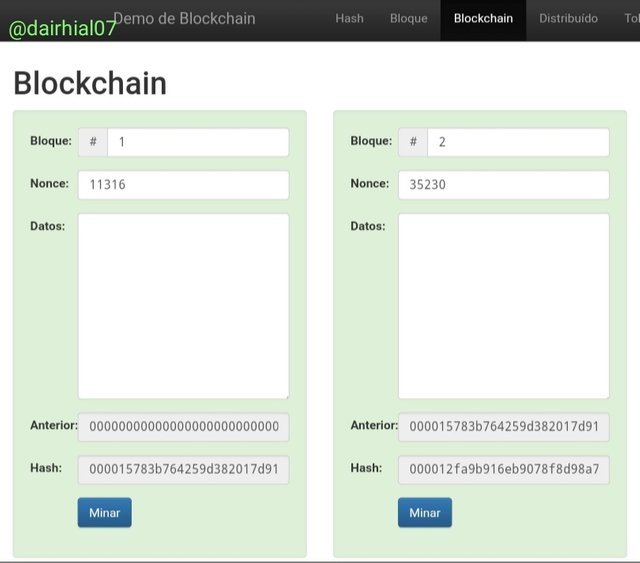
• We can see that each of the blocks have details such as the previous Hash, the Hash of the block, the number of the block and the nonce.
As the teacher told us in his class, when a block is valid and correct, its Hash begins with zeros at the beginning of its alphanumeric series, that is, in the starting number. And as we can see, each of our blocks have zeros in their starting number:
• Block 1 hash:
000015783b764259d382017d91a36d206d0600e2cbb3567748f46a33fe9297cf
• Block 2 Hash :
000012fa9b916eb9078f8d98a7864e697ae83ed54f5146bd84452cdafd043c19
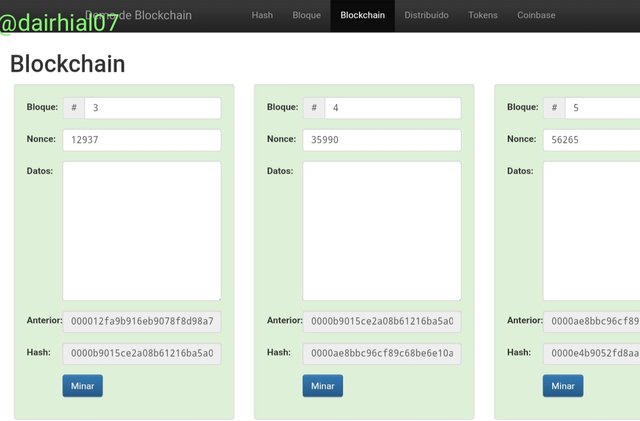
• Block 3 Hash :
0000b9015ce2a08b61216ba5a0778545bf4ddd7ceb7bbd85dd8062b29a9140bf
• Block 4 Hash:
0000ae8bbc96cf89c68be6e10a865cc47c6c48a9ebec3c6cad729646cefaef83
• Block 5 Hash :
0000e4b9052fd8aae92a8afda42e2ea0f17972ea67cead67352e74dd6f7d217c
So it means that our blocks so far are valid, since each of their starting Hash starts at 0.
It is also important to remember that the Hash of the blocks must coincide with each other and then be added to the chain of blocks, for example:
• We can see that the Hash of block 1 matches the previous Hash of block 2:
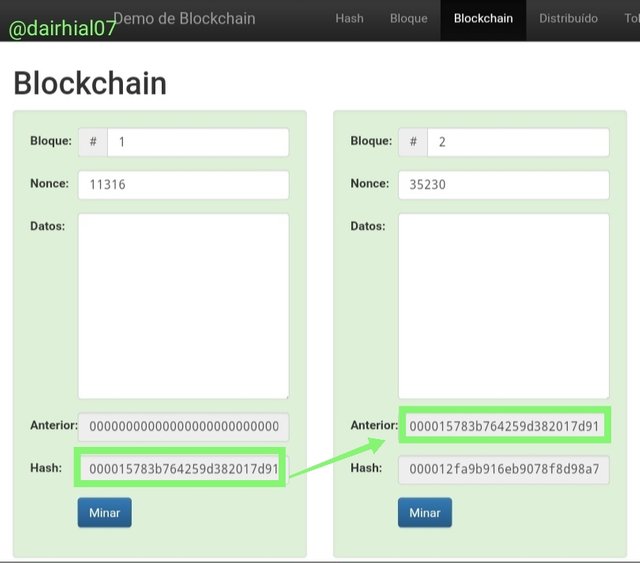
• We can see how the Hash of block 2 matches the previous Hash of block 3:
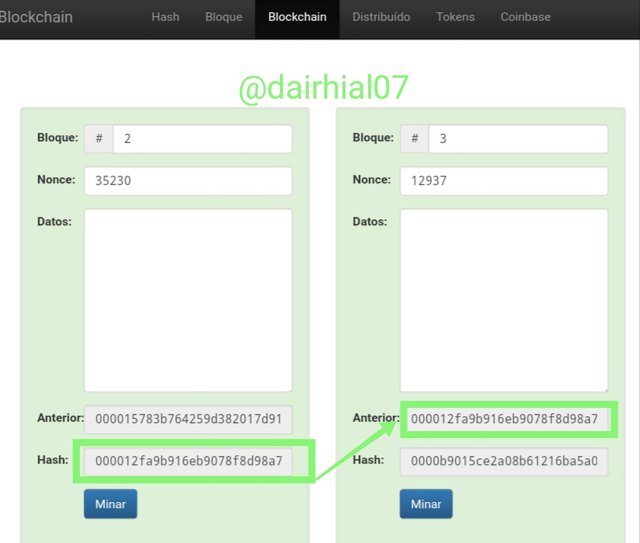
• We can see how the Hash of block 3 matches the previous Hash of block 4:
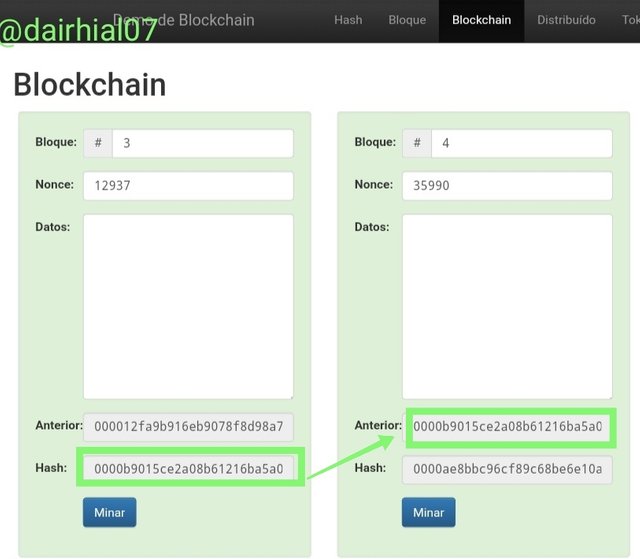
• We can see how the Hash of block 4 matches the previous Hash of block 5:
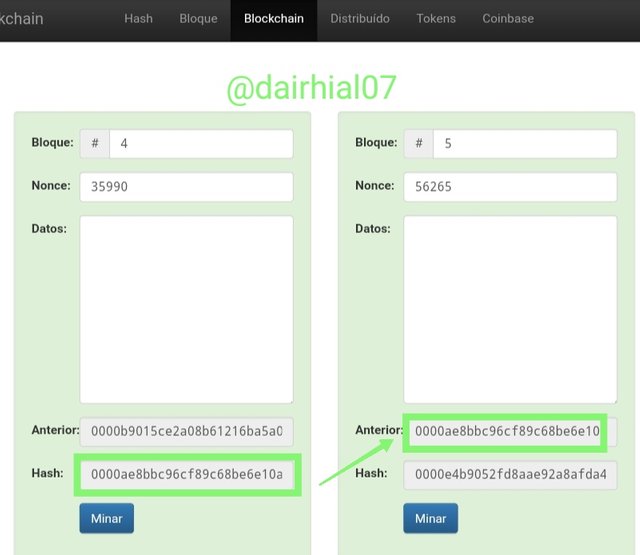
This tells us that each of the blocks is compatible to join the blockchain.
• What happens when data is added to blocks?
When data is added to blocks, automatically the Hash of the block and the number of the nonce change, for example:
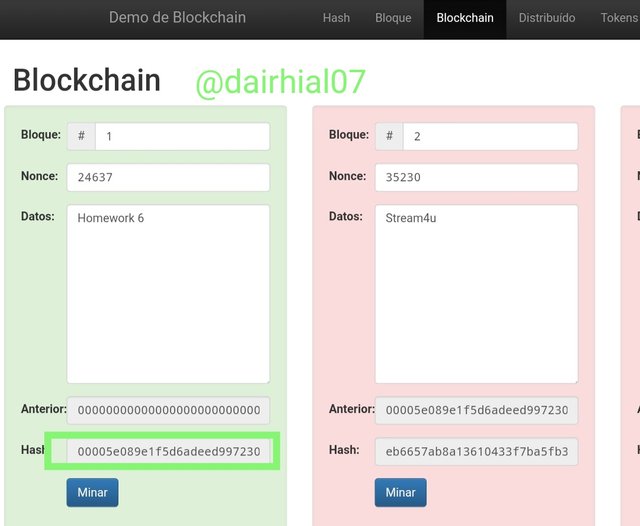
• In the first block I added the data "Homework 6", and I could see how it automatically changed its main Hash, causing the value of the other previous Hash of the blocks to change as well.
His Hash changed to:
9b6082d1e18dc79d9ee0c53217923e084ab288b1f679bf908146c806bcb72155
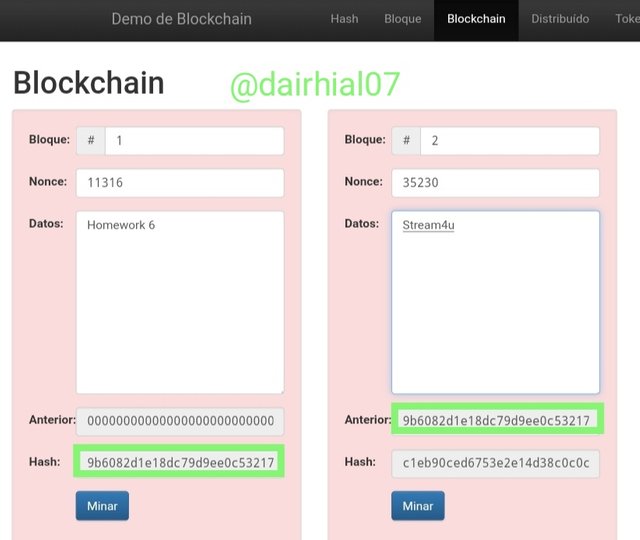
• In block two add the data "Stream4u" and I could see how your main Hash also changed your numbers:
c1eb90ced6753e2e14d38c0c0cfbdcc145763a8b4ae62b57d2eee9588f38ca88
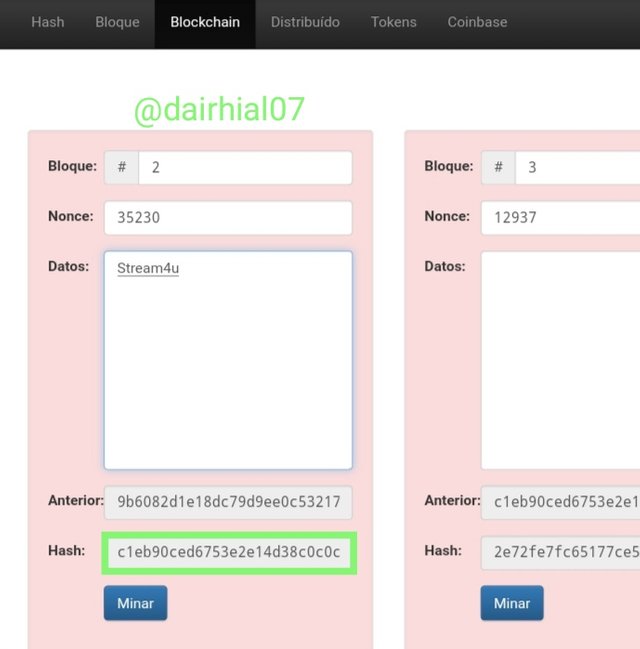
And as we can see these blocks are not valid since in their starting point they do not have 0 in their Hash. To make the block valid, we must change the number of the nonce until we obtain a block that is valid and that can be added to the chain.
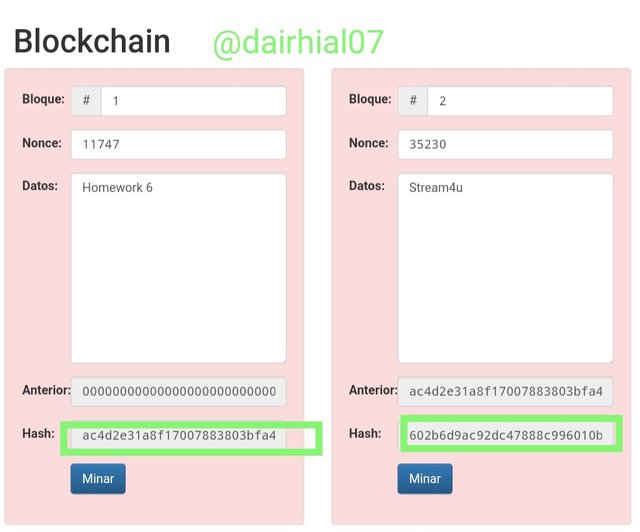
• For a block to be valid, the nonce number has to be changed so that the Hash value starts at 0, that is, its starting point, for example, this is what a valid block would look like and ready to be mined:
• Its initial nonce value with no data was 11316, and its initial Hash was:
000015783b764259d382017d91a36d206d0600e2cbb3567748f46a33fe9297cf
• When data is added to blocks its nonce value changed to 24637, and its Hash changed to
00005e089e1f5d6adeed997230cb34306c33b2828fa57ae2b5f17e5da6927a86
So we can see how adding data to a block automatically changes all the data. If in any case the block is invalid, we must look for the ideal nonce number so that the blocks are correct and can be added to the chain of blocks.

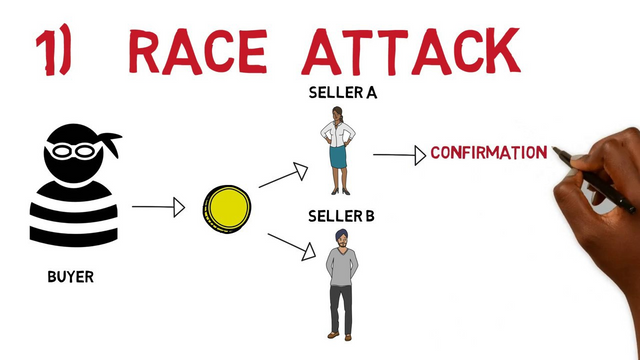
6) What is Race Attack on blockchain? Or What is Finney Attack on blockchain? Or What is Vector76 Attack on blockchain?
• "Finney Attack": This type of attack was discovered a long time ago by Hal Finney, who realized that a double-spending attack had happened on the BTC network for the first time, so so much since then this attack was mastered in his name.
This attack is very difficult to occur, but it is not impossible, therefore it happens when users make the mistake of accepting a transaction without waiting for all the corresponding confirmations, which can become very easy prey for malicious cyber attackers. who seek to scam the network. However, the nodes also play a fundamental role in this type of double spending attack, since they can be in charge of creating another alternative address, so that when the user accepts the unconfirmed transaction, they are prone to accepting the alternative address that the node sent you, managing to scam you immediately.
That is why it is very important to wait for the necessary confirmations that any transaction requires, and then continue with the process. This type of attack is very common in cryptocurrency exchanges, where money moves at every moment, which is an ideal scenario for cyber attackers to carry out the double-spend attack.
For the Finney Attack to be executed successfully, several conspiracies are needed, one of them is to extract precisely the block of the transaction that will be carried out, and then wait for the user to accept the operation without confirming, and that then double spending is run. It is not impossible, but it is a tedious and difficult process, since for sure we will not know if the user will accept the transaction without confirming or not.
It takes a lot of time and dedication to carry out this type of attack, and as I mentioned above, the attacker must have a high Hash Rate percentage so that he can successfully extract the mining block and then create another alternative address that will be sent to the user. We can avoid this type of attack if we take the previous security measures, such as waiting for the necessary confirmations and then operating.
Despite the fact that most cryptocurrencies are of decentralized origin, there is always some minimum error that can lead to this type of attack, that is why we must know that from 1% we can be the victims of the scams that occur in the net. We must take the necessary security measures and be aware of these types of attacks and how we can avoid them, that is why there are currently many methods that help us detect attacks instantly, in addition to the technology that support currencies have evolved. in a conspicuous and constant way, since they have implemented new methods and algorithms to protect us from this type of attack.

7) Limitations / Disadvantages of Blockchain.
As we know, everything has its advantages and disadvantages, and that is why here I will show you some limitations that I consider that blockchain has, which can put us at a disadvantage:
• Immutable network: As we already know, once an information, data or any record of an activity is entered in the blockchain, it is impossible to delete or edit it, therefore this may give us a small limitation when we want to correct some mistake or mistake that we have made, for example:
If we make a mistake in the amount of a transaction, or in the direction of the same, it is impossible that we can correct it, therefore, this can put us at a disadvantage if it happens.
• Prone to attacks: As we saw previously, blockchain is prone to many cyber attacks that can affect us, such as:
• Attack of 51%
• Finney Attack
• Double spending
• Race Attack
All these attacks do not occur continuously, however, when they do occur they can bring us many problems for our finances, so it can be a great disadvantage.
• Public network: As we know blockchain is a network where everything is registered and recorded, and anyone can see the information they want, therefore, this can be a great advantage for cyber attackers who wish to carry out malicious attacks on network.
However, we also know that we can use the private blockchain for more security, just that it is not suitable for everyone.
• Speed: To validate and verify the information that is integrated into the chain of blocks, the participation of many nodes is necessary, therefore this can saturate the network and make it a little slower, which can suppose a great disadvantage if we are carrying out some type of operation or processing.
• Mining: When the mining process is carried out on the blockchain network, this entails high implements and material costs to achieve it, as well as high electricity consumption when mining a block, which can seriously affect the ecosystem.
• Loss of accounts: Being a totally decentralized network, if we were to lose our private key of our account with active funds, we would lose absolutely everything, since it is impossible to recover it, therefore, we would be solely responsible for what happens.
We could not request help from entities that help us recover our password, so we would be losing all our income, and putting ourselves at a great disadvantage.

Conclution
Times have changed, and the arrival of blockchain technology has brought us multiple benefits in our favor, we no longer need to use networks or systems that do not protect us or guarantee absolute security over our data or information. Thanks to blockchain we can work with a new secure and reliable implementation and the best of all is that it is fully decentralized, which guarantees us better scalability than current conventional systems.
It is a very useful tool for the millions of people who decide to safeguard any type of information, whether for their business, for their health, for their work, for their studies, etc. It is also ideal for large projects or smart contracts that want to find a more feasible solution when developing their projects.
What makes the blockchain network so special and safe is its distributed system, since each node that exists in the network makes the information successfully verified and validated, to later be added to the blocks and from there it will not be able to be changed or altered in its originality. In addition, thanks to the use of cryptography, the security in the blockchain network is extremely high, therefore, more and more millions of contracts decide to implement their services on the network.
I thank professor @stream4u for the excellent class this week, where he showed us that blockchain is more than a network, since it offers us millions of advantages and benefits to offer us for our use and disposition. I learned a lot about this class and I look forward to continuing to participate in the next ones.
See you later, it was an honor.

Hi @feliicia
Thank you for joining The Steemit Crypto Academy Courses and participated in the Homework Task.
Total | 8/10
Your Homework Task verification has been done by @Stream4u, hope you have enjoyed and learned something new.
Thank You.

@stream4u
Crypto Professors : Steemit Crypto Academy
#affable
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit