Introduction
Hello everyone, I am glad being a part of this great lecture room by Prof. @stream4u, it really is an education lesson.
.jpeg)
Source
1. Blockchain
Blockchain is a decentralized database where transaction datas are securedly stored. The security of blockchain is optimum in that anyone who tries to hack the system will find it so difficult and laborious to break into the database. The datas or information in the database are always distributed to every individual blocks. This therefore means that whenever a new information is introduced to the blockchain, every block in the chain automatically receives the information too. This is because each block is connected or linked to each other, making the distribution of information to every block in the chain faster.
There three main features that constitutes the blockchain, these;
- The blocks in the chain
- The nodes of the chain
- The miners of the blocks
Block: Information in the blockchain are recorded and stored in individual blocks. Each block is given a particular timestamp which when it is filled, passes the information to the next block in the chain. Each block is made up of data, the Hash of the block and the previous block’s Hash. Blocks in the Bitcoin network for example has the data of the sender, the data of the receiver and the amount that was actually sent to the receiver. The Hash helps to disclose a block and all the content contained the block. Hash of the previous block links a particular block to another block, making the information stored in the blocks to be more secure.
Nodes: Nodes are connected computers where blocks are mined. These computers do not necessarily have to be in a particular building, they could be in different locations but are all linked up to each other to create a blockchain.
Block Miners: Miners are individuals who operate the computers (nodes) and tries to create new blocks. Each miner has a puzzle to solve. The first miner to get the puzzle solved in the blockchain always emerge the winner and gets rewarded.
Blockchain Categories
Blockchain are categorized into several groups which are;
- Public Blockchain
- Private Blockchain
- Hybrid Blockchain
- Consertium Blockchain
Public Blockchain: This type of blockchain was created to be accessed by everyone, provided the person has an internet connect device. This is to say that public blockchain as the name implies does not put any restriction on anyone. It is open for everyone to connect and begin validating blocks and also initiate a transaction. Anyone who successfully validate blocks in the chain always gets some reward. The Public Blockchain uses the proof brain and the proof of stake consensus algorithm.
Pros of Public Blockchain
- It doesn’t depend on any particular organization to thrive because since it is decentralized.
- It has optimum security
- There is transparency in every transaction done in the blockchain.
Cons of Public Blockchain
- Since the access of users can’t be restricted, and it is open for everyone, the network sometimes gets slower because there are a lot of nodes that join the network.
- It uses the prove of work consensus algorithm, therefore there are complex puzzles to be solved.
Use Case of Public Blockchain
Bitcoin, being the first ever cryptocurrency, uses the public blockchain for mining. It is also used to record and save salient information.
Private Blockchain: This type of blockchain mostly work in a closed network under the authority of a private entity, making the access of the network restricted to a particular group of persons or individuals. This type of blockchain can also be referred to as permissioned blockchain.
Pros of Private Blockchain
- There is a level of orderliness in the connected computers because there is a central authority controlling them.
- Private blockchains can most times process transaction faster because there are limited number of connected nodes in the network.
Cons of Private Blockchain
- They are most times not trusted because it is of lesser transparency.
- There is less security in the private blockchain because of the closed and proprietary source code of the blockchain.
Use Case of Private Blockchain
They are best functional in private asset ownership and during internal voting
Hybrid Blockchain: This type of blockchain is oriented by the elements of the public blockchain and the private blockchain. Both the private permission-based structure and the public permissionless structure are employed to regulate restrictions on who accesses some information in the ledger and what information is allowed to be accessed by the general public.
Pros of Hybrid blockchain
- There are both privacy protection and public interaction with third parties.
- It is of better scalability than some other type of blockchain like the public blockchain.
Cons of Hybrid Blockchain
- There is no complete transparency in the system
- Users in the blockchain are some times not rewarded.
Use Case of Hybrid blockchain
Companies can use this type of blockchain to privatize some salient information and allow users to access some which are not private.
Consertium Blockchain: this type of blockchain is almost like hybrid blockchain but the difference is that there is some kind of multilateral collaboration in the network.
Pros of Consertium Blockchain
- Security is optimum
- It is scalable
Cons of Consertium Blockchain
- There is less transparency
- If one of the node in the network is compromised, it will affect the functionality of the network.
Use Case of Consertium
It can be used in many sectors, one of which is banks. Two or more banks can use this blockchain to validate their transactions.

2. Benefits Of Blockchain
Blockchain has offered so many benefits to different sectors and below are some of them;
Decentralization: Decentralization being one of the core characteristics of blockchain has made it possible for every node in the network to individually see every data stored in the ledger. Because every one in the network has access to the ledger, transparency has really permeate every transaction carried out in an organization.
Cost Effective: Before now, centralized system like banks had been the only transaction media, with so much cost attached to every intended transaction. But the emergence of blockchain has really curbed the high cost of carrying out transactions. Someone from the any Asian country can send funds to some in Africa at a very low cost, thanks to blockchain.
Security: Blockchain has proven to offer optimum security to information, records and transactions done in the blockchain network. With the Hash, altering or hacking information in the blockchain is a laborious task for the hacker.
Verification: Blockchain has minimized the verification processes carried out in the centralized systems. It allows transaction to go through without inquiring for the personal details of the user for verification purpose.
Trust: Each node in the blockchain network really do not necessarily need to know each other. But every transaction carried out is on the bases of trust which the blockchain technology has offered.
Transparency: Different sectors ranging from the Agricultural sector, medical sector, construction sector, financial sector, etc can embrace the Blockchain network because of the transparency it offers. It lets transactions to be seen by everyone who has access to the network used by any sector.

3. Blockchain Distributed Ledger
Source
Blockchain distributed ledger is a decentralized database allocated to multiple nodes or computers where each of the user can process, execute and update transactions on their own without depending on any third party. Every participant is in control of every transaction execution. No central authority is needed in the Blockchain distributed ledger.
Blockchain distributed ledger ensures the security of records in the network, as opposed to the centralized network. Every information in the network is protected by cryptography and can only be accessed with the use of either keys or cryptographic signatures.
Features of The Distributed Ledger
Every participant execute transactions on their own without any intermediary.
The datas in the distributed ledger are safe and cannot me meddled with.
Every participant have access to every information in the ledger.
Transparency in all transactions or record or update on the ledger is paramount in the blockchain distributed ledger.
There is no verification process required for participants before they can access the network.
Each node interact with another node in a peer to peer manner, even without getting to know who is behind the computer on the other end.
Advantages Of Distributed Ledgers.
Hackers finds it very difficult to hack or attack the records in the network.
It makes the circulation of information very easy and concise
There is greater reduction of cost of operation as opposed to centralized systems
Completion of transaction are pretty fast.

4. Blockchain Double Spending And How Bitcoin Handles This Problem
Double-spending is the fraudulent act carried out by hackers so that digital currencies are spent twice. This act is done by someone who has a very good knowledge about blockchain. This double spending is easily carried out in digital currencies because they can be replicated. This issue is however far from traditional fiat because the authenticity of fiat currencies are always verifiable.
The hacker or attacker first sends a transaction to the network, while the transaction still awaits confirmation, the attacker send in another transaction to the network which looks so real but it is not. When the confirmation is now done on both transactions, payment is made to the hacker’s address and the funds sent to that address are never retrievable. This double-spending issue is really done in the Bitcoin network because it uses a timestamp of 10minutes to confirm a particular transaction in a block.
There are three major attacks of double-spending which are;
Vector Attack 76: this attack is carried out as a result of existence of bugs in the consensusnof the Bitcoin system. Hackers maneuver their way into the network through this bugs.
A Finney Attack: This attack is successful as a result of the non-confirmation of transactions in the network.
Race Attack: This attack is carried out when the attacker creates double conflicting transactions. If payment is made without confirmation, then the attacker makes away with the funds.
How Bitcoin Handle Double Spending Attacks.
Bitcoin handle double spending by ensuring that every node in the network have a pre-knowledge of all the transaction in the network. That way, they will agree on to take note of the history order which transactions were received. Now if the majority of the nodes come to agreement on which transaction was first received, the preceding transaction will be considered invalid. That way, double spending attacks can be curtailed.

5. How Block, Hash Work In Blockchain and What Will Happen When Any Of Middle of The Block Gets Changed
First I visited andersonbrownworth.com
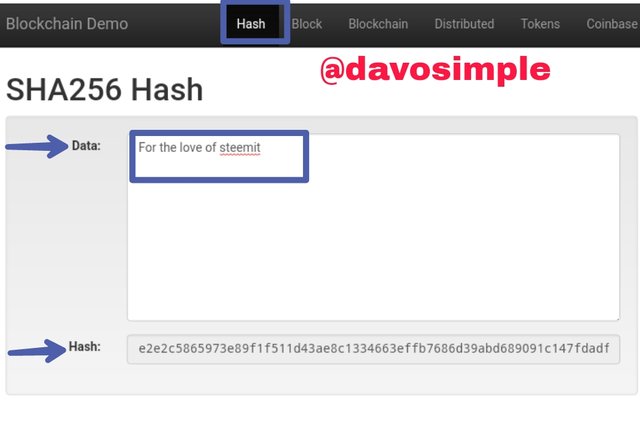
Here, we have the Hash feature. Every input in the Data field automatically generates a Hash for the input. Every data has its own Hash, meaning that no two datas can have the same Hash.
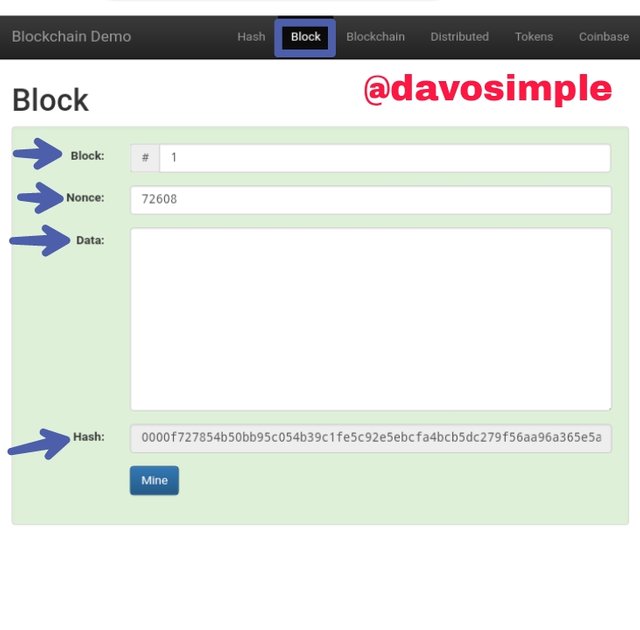
The next feature is the Block. Here we have the Block number, we have the Nonce, the Data and the Hash. The Nonce is what makes the block here valid or invalid. As it is now, the data field is empty but if i type in data in the data field, if the data is not valid, the whole block color will change to red.
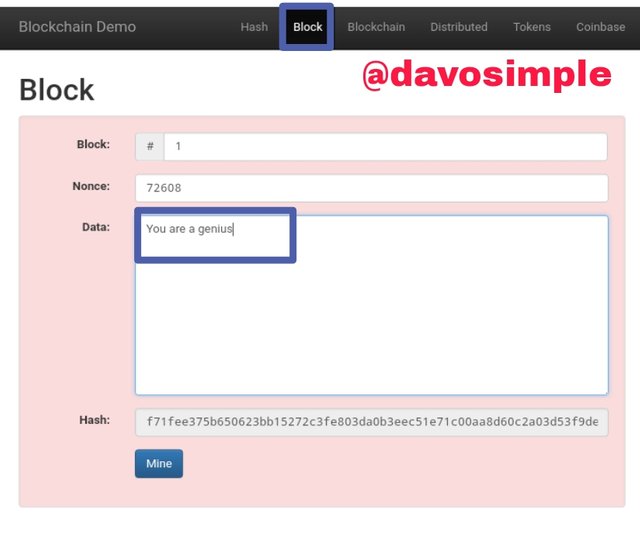
Here I have typed in data in the data field. The block has become red indicating that it is invalid. That is because value of the Nonce is not corresponding with the data i inputted. I will have to click on Mine to process the data and generate the corresponding Nonce for the inputted data.
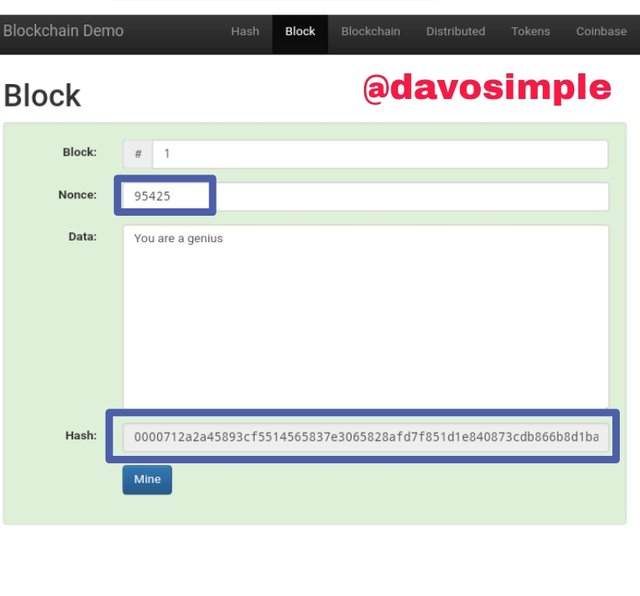
The new and corresponding Nonce has been created which is
0000712a2a45893cf5514565837e3065828afd7f851d1e840873cdb866b8d1ba
and the corresponding Hash also which is 95425 has also been created. The color of the block is now green, meaning that the block is valid.
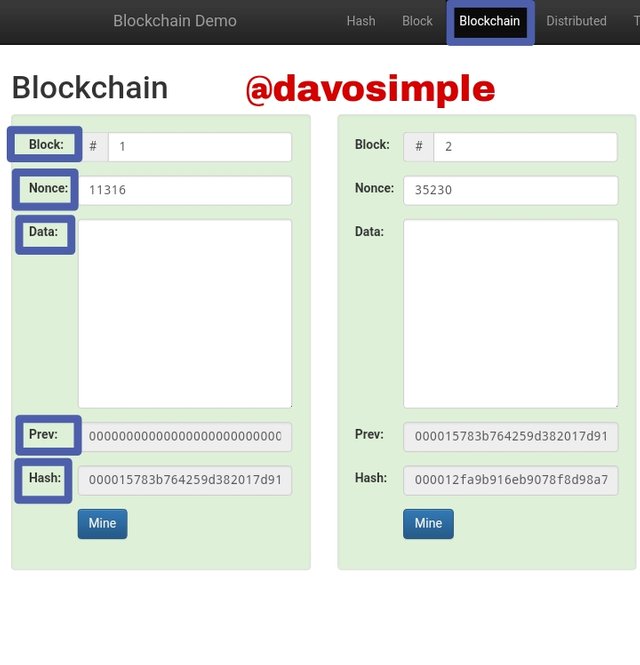
The Blockchain has about five parameters which are Block number, Nonce, Data, Previous Hash, and the new Hash. So there is Block 1, Block 2, Block 3 etc, each having its correct Nonce and the previous block’s Hash and also its new and corresponding Hash. The validity of Hash in the Blockchain is determined if the Hash starts with 0000.
If The Data Input Is Changed.
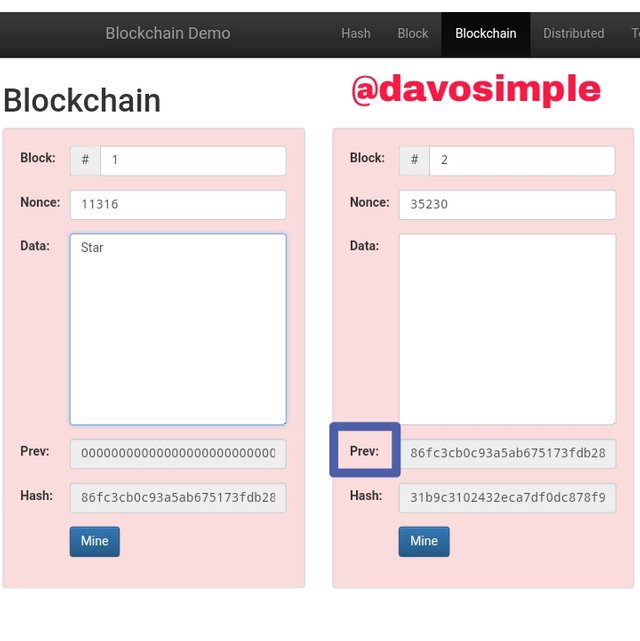
If the data input in block 1 is changed, it will render itself and the other blocks as invalid by changing the blocks color from green to red.
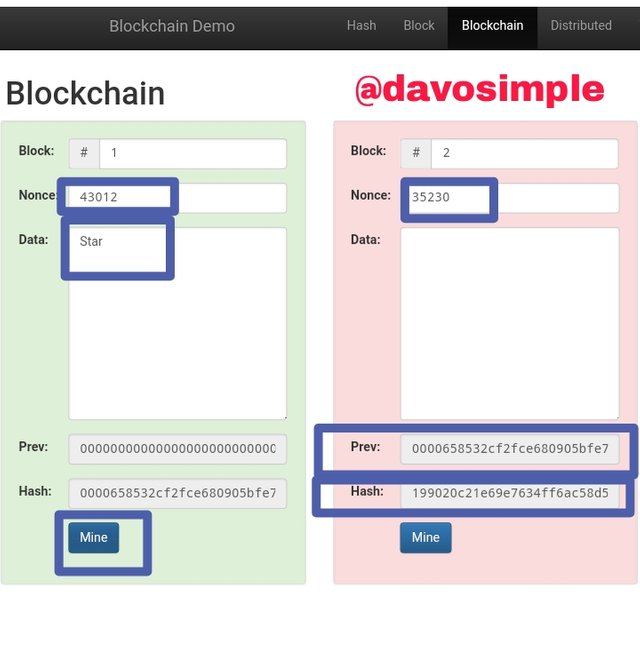
To validate the blocks, I will have to click on mine and it will automatically mine block 1, generating its correct Nonce. But the other blocks which are block 2, block 3 etc still remains invalid until they are also re-mined.
This therefore proves the point that change in any block data in the blockchain will alter and invalidate other blocks. That is why the blockchain is so sensitive to alterations, ensuring that datas are secured and safe.

6. Race Attack.
This attack is carried out when the attacker creates double conflicting transactions. If payment is made without confirmation, then the attacker makes away with the funds.
Assuming traders are ready to pay for goods or services. The hacker sends two transaction to the various traders where one transaction will contain the real asset and the other transaction will be fake. If a trader in the trail immediately makes payment or sends the goods without waiting for a clear confirmation, it means the hacker has succeeded in invalidating the transaction information of the trader.
The easiest way to get over this type of tricks by hackers is to always wait for transaction timestamp to be completed in order for confirmation to be made before any decision is taken.

7. Limitations Of Blockchain.
Scalabilty: One of the major limitation of blockchain is scalability. In the Bitcoin network for example, a lot of computers or nodes always get to join the network and it always makes transactions go slower. So the more nodes joins the network, the slower it seems to become. The network gets congested.
Energy Consumption:Some of the network in the blockchain that make use of the prove of work consensus algorithm always consume so much energy. When an update is introduced to the ledger, miners always have to solve some laborious puzzle which before a particular block gets mined, a lot of energy has been consumed.
Data Immutability: Whenever data is entered in the blockchain, it cannot be altered or changed which has somehow breached the privacy right of some information which should have been kept private and confindential.
Risk Responsibilties on users: Users are left to bear the risk of the security of their funds by taking very good care of their private keys, not exposing it or allowing anyone to see it. If a user fails to take responsibilities of their keys, then their wallet is at a high risk.
Cost: The cost of getting the blockchain implemented is very high. Cost ranging from hiring developers, to cost of maintenance are very high.
Management: Managing a blockchain requires an expertise knowledge manage the complexities embedded in the technology.
There many other disadvantages or limitations of blockchain but these are a few salient ones I have gathered from my research.

8. Conclusion
Blockchain is a baby technology which has in the few years of existence revolutionize the world and positively impacted the world.
With its cryptographic function, it has given optimum security to every information recorded or stored in the system. Its wings has also spread to cover every sector ranging from economy sector to the financial sector, agricultural sector, politics, etc.
Blockchain, even though still young and yet to be embraced my so many has some limitations which are still being worked on by developers. Some of the challenges the blockchain technology have are the scalabilty problem which arise from so many nodes joining the network at a particular time, thereby slowing down the transaction process, the high cost of management challenge, the huge cost of maintenance challenge and several other challenges. But the good news is that these challenges are being brainstormed on everyday and in the nearest future, the challenges we see today, we shall see them no more.
Thanks for having me.
CC:
Prof. @stream4u
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Hi @davosimple
Thank you for joining The Steemit Crypto Academy Courses and participated in the Homework Task.
Total | 8/10
Your Homework Task verification has been done by @Stream4u, hope you have enjoyed and learned something new.
Thank You.

@stream4u
Crypto Professors : Steemit Crypto Academy
#affable
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit