QUESTION 1
Explain what does the resistance to collision mean? And what does resistance to preimage mean
Resistance to Collision and Preimage
A) Resistance to Collision
This is actually a property to in the cryptographic hash function. When a hash function is said to be collision resistance, it means collision resistance is a one way hash function
Let me use H to represent hash, and two inputs x and y
When it is difficult to find two inputs that are hash to the same output,
With the two inputs not equal to each other,
That is x not equal to y
But H(x)=H(y)
Then we term it a resistance to collision.
Normally, cryptographic hash functions are made to be coalition resistance. But some have however been broken.
B) Resistance to Preimage
The resistance to pre-image talks about the invert-ability of the hash function. It is actually a property that causes difficulty to invert.
With the pre-image reistance, an element in a range should be computational infeasible to find the input map to the element.
The preimage is used to input and output domains of similar sizes for the fact that it corresponds to one-wayness.
For a hash function to be preimage, it must have a minimum length of 90 bits
The preimage is particularly important because it cause the output to repeat it self. Although when an attacker is able to value in the preimage, he wins solely because the attacker is always ask make the selected hash work.
QUESTION 2
Use tronscan and etherscan to verify the hash of the last block and the hash of that transaction. Screenshot is required for checking
Using Tronscan and Etherscan to verify Hashes
1) Using Tronscan
This is achieved in the following steps.
Step 1, visit the tronscan.com website
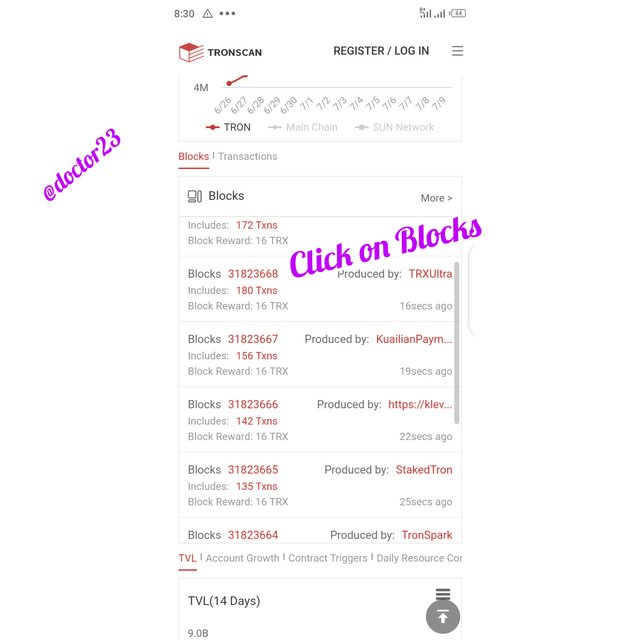
Step 2: click on blocks
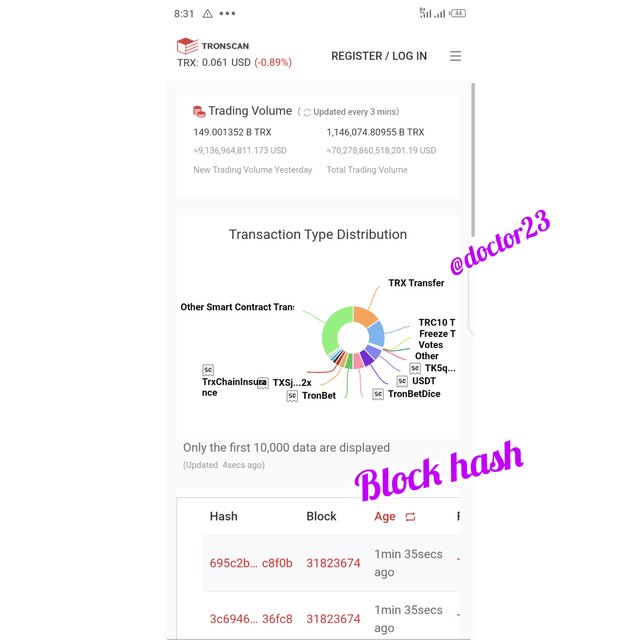
Step 3: We can see the block and transaction, hashes
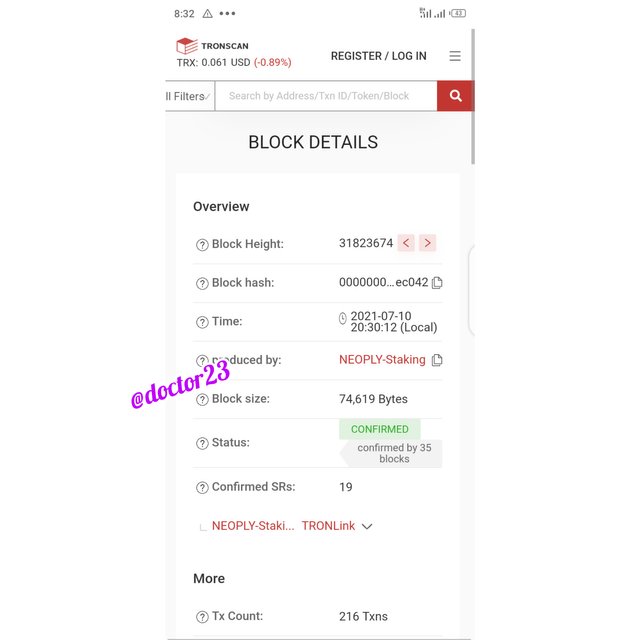
Hash: 0xf50ef6c52e3d8c23f14cb66f3b8579e07f0356e3248be952853257bd3f0a2c44
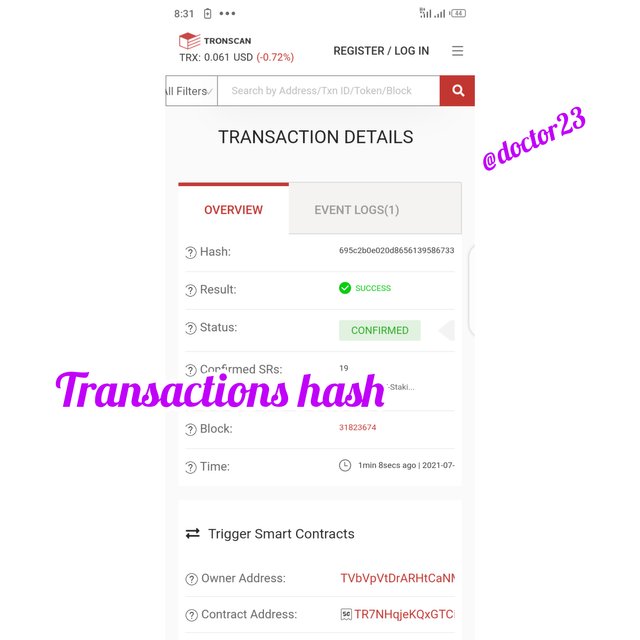
Hash: 695c2b0e020d8656139586733a6ed54534dcc3a3fab681211867922ae9bc8f0b
2) Using Etherscan
This can be achieved in the following steps
Step 1, visit the etherscan.com website
Step 2: We click on transaction
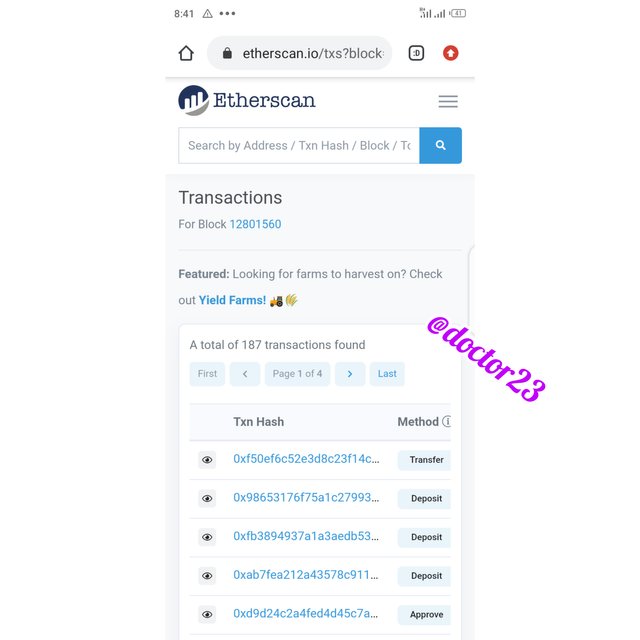
Hash: 0000000001e5973a56b4e0584c7a598da6bd66a5755916e57d5aed8e8cbec042
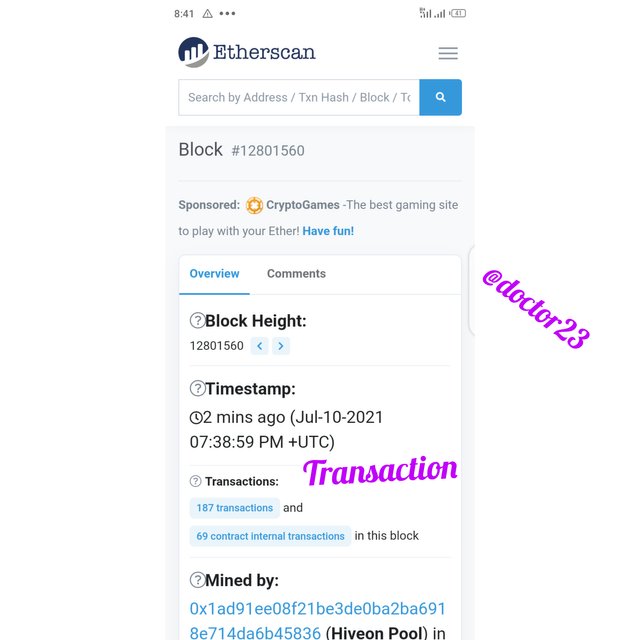
Step 3: we now click on blocks,to view the block hash
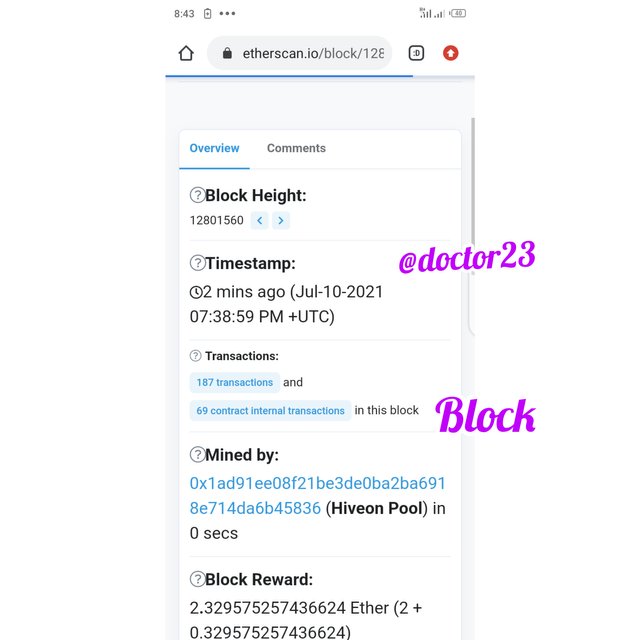
Hash: 0x62a6205a469dc8e4ba72151e13776b0ff4bd5d91ed3e91b15980361630a162ab
QUESTION 3
Generate the hash using SHA-256 from the word cryptoacademy and from cryptoacademy. Screenshot required. Do you see any difference between the two words? Explain
Generating hash using SHA-256
We follow the following steps
Step 1, visit the SHA-256 website
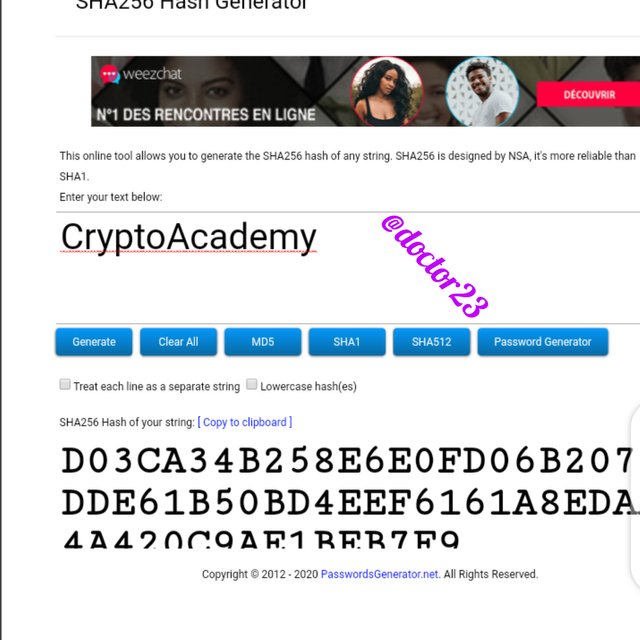
Step 2: We type the word: CryptoAcademy and click generate
Step 3: We type the word cryptoacademy and click generate.
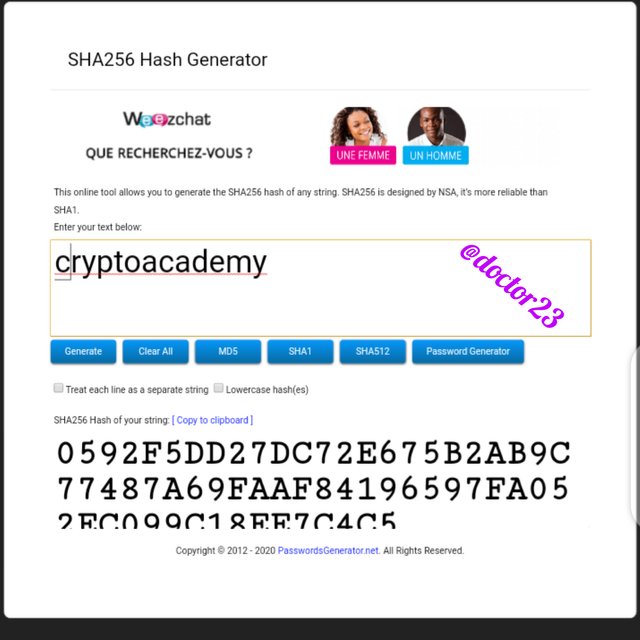
The two words though the same, just differs in capitalisation produces two different hashes.
This shows that a hash is very unique as well as uppercase and lower case sensitive.
QUESTION 4
In your own word explain the difference between hash and cryptography
Difference between hash and cryptography
I will list out the various difference between hash and cryptography in the points below.
- in the cryptography, it is dependent on how users secure it keys for its security, whereas in the hash, is more secure because of its one-way nature.
- hashing is irreversible which makes it impossible for the generation of input from the hash value. Whereas in the cryptography input is generated from ciphertext using private key.
- hashing normally has a fixed value of length, while the cryptography the data length is limitless
- no exchange of keys is required in the hash. While in cryptography, it requires two users to access key for decryption.
CONCLUSION
We can actually use the hashing and cryptography to securely protect our date for transmission.
With this and from above, we have seen that the hash is preferred more because of its irreversible feature which is great for password safety.
We can also visit the tronscan and etherscan to view the various hashes of the blocks and transactions.
Gracias por participar en Steemit Crypto Academy Season 3:
Espero seguir leyendo tus publicaciones.
Explicar de forma sencilla y clara cada concepto solicitado.
No pude hacer seguimiento al hash del bloque y de la transacción.
Recomendaciones:
Es necesario justificar el texto.
Cuando los datos solicitados no se pueden observar, debes copiar y pegar en un sitio visible.
En las captures de pantalla debes señalizar los datos solicitados, como el bloque a estudiar, el hash encontrado. Puede ser con flechas, recuadro u otro sistema.
Calificación: 7.8
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit