.jpeg)
HASH
One may be wondering what these groups of numbers and letters represents; they are referred to as HASH. Therefore Hashes are functions or computational algorithms that help to encode information and are widely used in the blockchain technology. Hashes can be generated for any word; generating a hash for that word means that the information about such word is contained in that hash. There are several applications of hashes even in the real world, they can be used to for information that are confidential, as it has been mentioned above, they are widely used for crypto currency addresses, and are also used in the mining of cryptocurrencies et cetera.
As we all know that in the world of crypto or in the crypto world as one may call it; what matters the most is the privacy, secrecy and security. When we look at addresss of a Cryptocurrency, we see a very long word consisting of both numbers and letters which a novice or a newcomer in the crypto may not know it's function or how it is generated.
When we talk about hashing, it is a way of producing an output or inputs with a fixed size from inputs that have different sizes. This can be done with the use of mathematical formulas that are known as hash functions. Be that as it may, hash functions are not only used in cryptocurrency, they are also used for other applications too; the hash functions are the essentials of the cryptocurrency.
What is resistance to collision?
Resistance to collision can is a characteristic of a hash function. We can refer a hash function, say Z as a collision resistant if it is difficult and hard to look out for two inputs that hash to the same output. That is say, two inputs x and y; where x is not equal to y but Z(x) = Z(y).
some cryptographic hash functions are usually developed to be resistant to collision. But be that as it may, some hash functions which were once thought be collision resistant were later broken.
Why do we need collision resistance hash functions?
Firstly, In some systems that have digital signature, a party confirms a document by presenting a public key signature on a hash of the document. Let us assume there is a possibility of producing two documents with the same hash, a scammer or a spammer may get a party to confirm to one and may later claim that the party had attested to the other
Also, there are some systems that are have distributed content, there used to be comparison of cryptographic hashes of files so as to be sure they have similar versions but an attacker may produce two files with similar hash and could trick users of such files into believing they had the same version of a file when unknowingly to them, they are being deceived.
What is resistance to pre image?
As mentioned, a collision ensures when dissimilar inputs produce the exact same hash. This means that the hash function is said to be resistant to collision till the moment when someone is able to find its collision. Collisions will always be available for hash functions because the potential inputs are limitless, while the potential outputs are limited.
Furthermore, a hash function is said to be a collision resistance if the possibility of determining a collision is so little that one may use more years to solve the arithmetic. So, with this, there are no hash functions that is collision free, there are many hash functions that are very strong enough to be referred to as resistant. An example of such hash is the SHA-256. There may be combinations of hash functions in order to get a very strong hash function. Taking the SHA algorithms as a case study, the combinations of SHA-0 and SHA-1 are so weak in terms of security because of collisions but we can say that the combinations of SHA-2 and SHA-3 are said to be resistant to collision because of the strong security built around them.
The collision resistance becomes a necessity when a user depends on the hash functions to be able to generate 2 inputs to 2 varying outputs. when the output space is small compared to the input space, then many inputs will generate the same outputs. although we are certain of the existence of collisions. This is what is referred to as collision resistant hash function.
Collision to pre image
What is collision to pre image?
It is highly important and very necessary for hash functions because it means that the function is will only be one way hash. That is, preimage literally means is related to only one way functions. Preimage resistance in hash function, refers to a situation whereby there is a narrow chance for a person to find the input that may produce the required an output. This is significantly so much different from the security provided by a hash function which is resistant to collision, why? This is because a scammer tries to attack can make a guess on what the input is by merely looking at what the input is. This is not so for a hash that has a collision to pre image because if an attacker or someone finds different inputs that may generate or produce the same output, the input used is necessarily not a major factor to be considered.
The preimage resistance is very important and very much essential in hash functions in order to increase the protection and security of data because just a hash of the message can safely authenticate whether such a hash is authentic or fake even without necessarily revealing important info about the information contained in the hash.
This is an absolute necessity for hash functions because it means that the function is one way, The concept of preimage is related to one way functions. When we talk about preimage resistance in hash function, we are referring to when there is very small chance of a person finding the input that will give an output. This security property is different from the previous one because the person trying to attack will have to guess what the input is by looking at an output. This is not so for a collision as a collision occurs when someone finds different inputs that generate the same output, but the input used is necessarily not a considered factor.
USING TRONSCAN TO VERIFY A HASH
Step 1: On any browser search tronscan.org
Step 2: the homepage of the website will be displayed and you can see the different blocks as arranged according to the time they were processed.
Step 3: as it was requested I clicked on the latest blocked on the website which was 31813428 as it can be seen from below:
Step 4: everything about the block was displayed
And lastly, I clicked on to see the transactions
CHECKING A HASH USING etherscan.io
Open your browser and search for etherscan.io
The latest blocks will be displayed, I then clicked on it, which then displayed everything about the block
And then, transactions were also displayed.
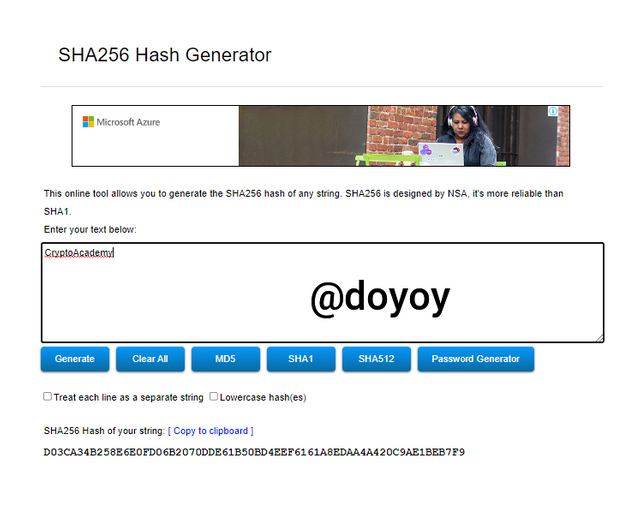
GENERATING HASH USING SHA-256, FROM THE WORD CryptoAcademy and cryptoacademy
Search https://passwordsgenerator.net/sha256-hash-generator/
Using CryptoAcademy, the hash generated is D03CA34B258E6E0FD06B2070DDE61B50BD4EEF6161A8EDAA4A420C9AE1BEB7F9 as shown in the screenshot below
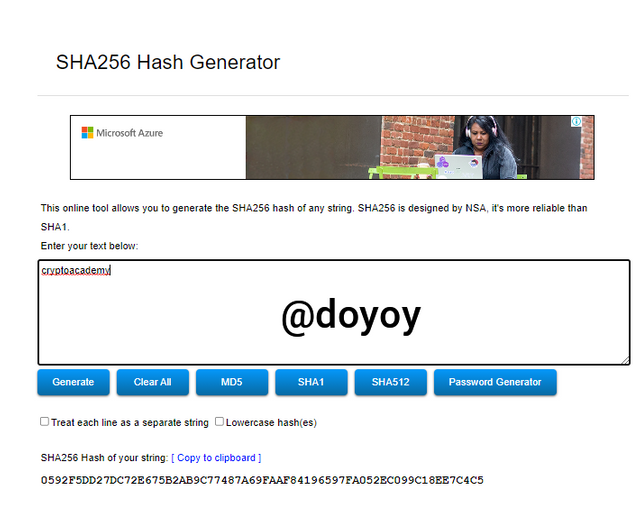
Using the word cryptoacademy:
The hash generated is 0592F5DD27DC72E675B2AB9C77487A69FAAF84196597FA052EC099C18EE7C4C5 as can be seen below:
EXPLANATION;
As it can be seen vividly from the screenshots above,
Different hashes were generated when different words were used, which means that the generation of words using SHA256 is case sensitive.
Differences between hash and cryptography
HASH
Hashing is a method of cryptography that is used in converting data into an exceptional and special string of text. They are used to input and transform data into a unique alphanumeric string, for example: D03CA34B258E6E0FD06B2070DDE61B50BD4EEF6161A8EDAA4A420C9AE1BEB7F9, this is used to enable a very high security and an effective privacy. Virtually, almost all data can be hashed as there is no type, length nor size constraint to what can be produced. More so, the results of hashes that are generated always have fixed lengths. As earlier stated, the hash acts as a one way function. Hashing also is case sensitive as can be seen from the words generated below but if the same data is used, the output generated is always the same.
WHILE
Cryptography enables the security and privacy of both transactions carried out and also the users.
It is the method of sending secure messages among different users, this is done as the sender of the message will encrypt such messages using specific keys and algorithms, and then when the receiver at the other end receives this message, he will have to decrypt the message to be able to get the original message sent.
The encryption keys are very important when it comes to cryptography because messages sent cannot necessarily be read by a wrong recipient as the intended recipient will be the only one who can decrypt the message sent.
Thanks to professor @pelon53 this is my homework post.