

1. Explain in detail the P2SH and the P2PKH, show the differences between both directions.

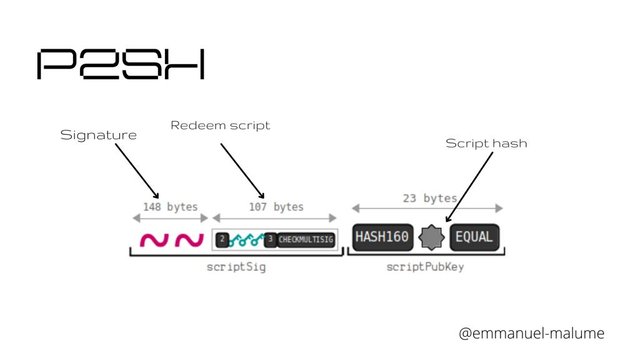
P2SH
P2SH is a standard script introduced to bitcoin blockchain in April of 2012. The script gives you the leverage to secure bitcoins within the hash of a script, and if you need to unlock the secured bitcoins, you will have to present the original script for access.
To make it simpler, it allows you create a personalized “redeem scripts”, and allows you the freedom to share it with others.
P2SH transactions were instituted in BIP16. P2SH gives you the platform to transact with a script hash starting with 3 instead of the regular public key hash that starts with 1.
To gain access to the bitcoins sent through the P2SH, the recipient must show a script matching the script hash and data confirming the script evaluation as true.
WIth the implementation of P2SH on the bitcoin network, you can send BTC to an address that is secured using unique methods without prior knowledge of the security of the tokens. All you need do is send bitcoins to the 34-character P2SH address. The requirements to on the recipients part could be numerous and unique, it might require the signatures of several people to spend these bitcoins, a password, or any customized system.
How P2SH works
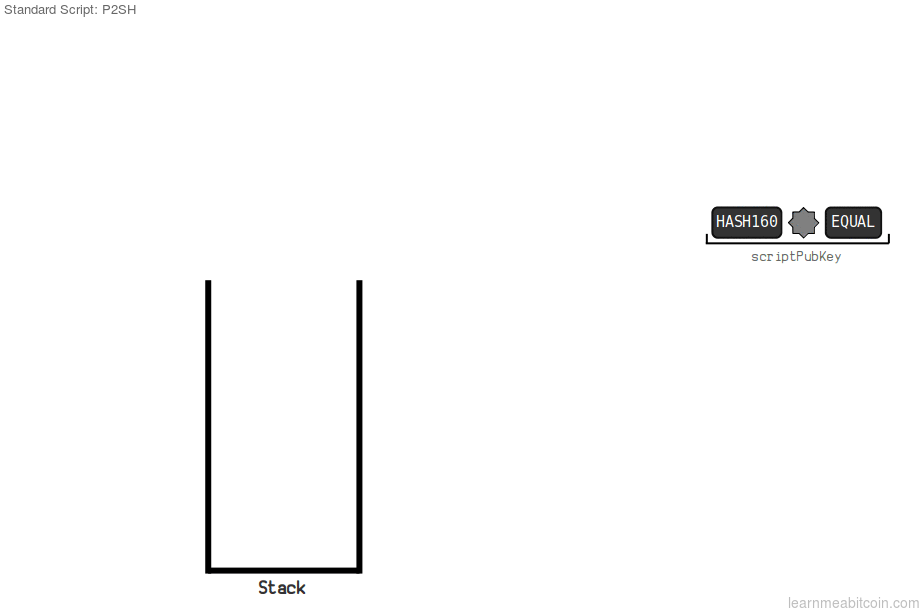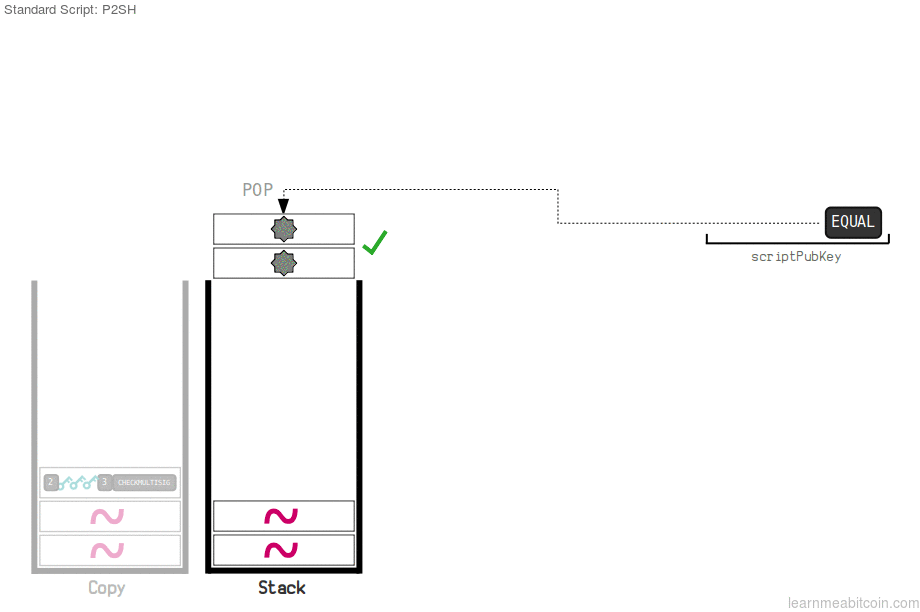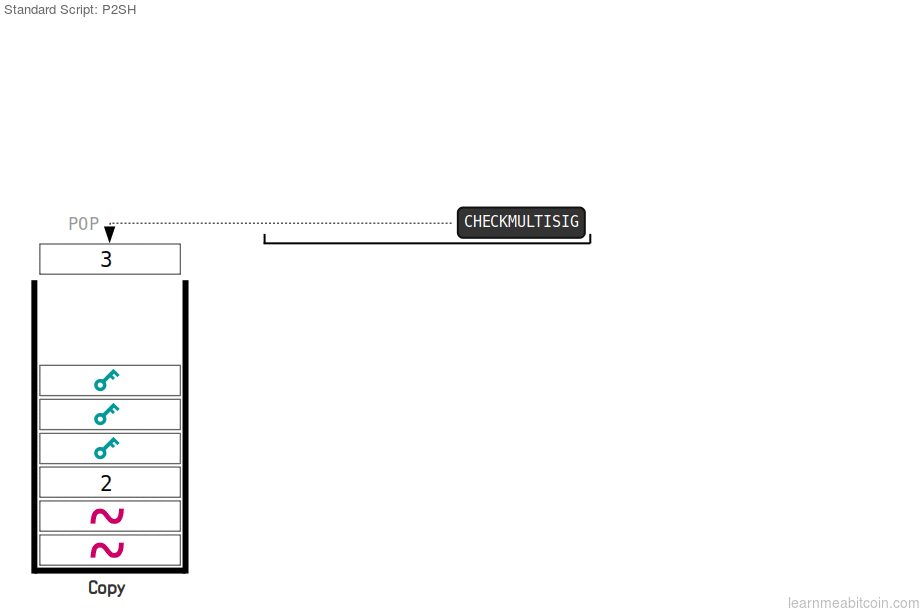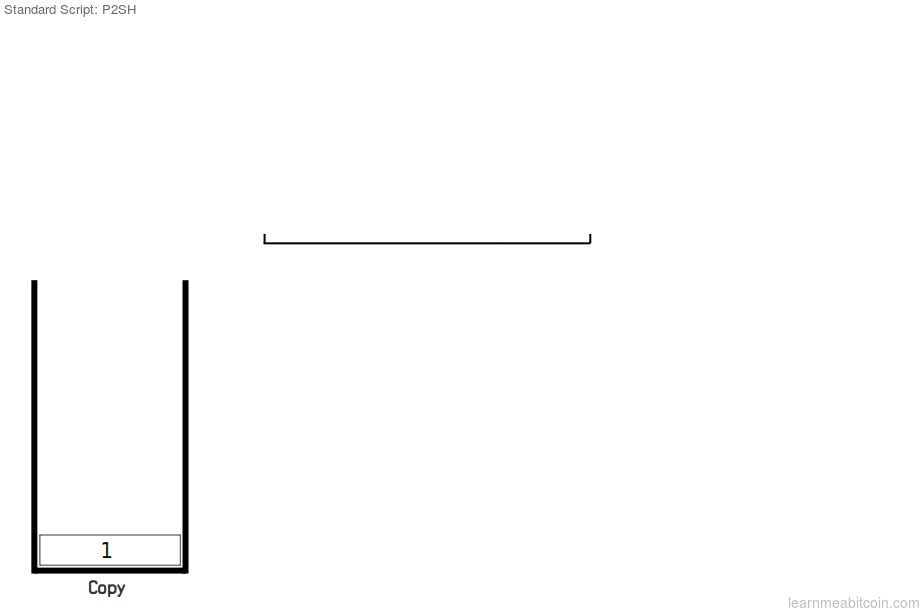
Transactions that make use of the P2SH scripts are dependent on the redeem script hash function. This redeem script hash is similar in function t to he scriptpubkey in the P2PKH modification.
The above mentioned redeem script hash evaluates with the original script, making allowance for the user to be able to spend the available bitcoin. For a user to spend his BTC, he must have the Pubkey script which contains the redeem script hash and the unlocking script. The redeem script replaces the Pubkey in the P2SH transactions, and can be used to show grant of access to funds. Reedem script hash is excluded from the script sent as the locking script.
The redeem script hash, replaces the redeem script and is presented to the locking script. This action, if done with the correct hash equates the evaluation as true, transaction is confirmed as spent, and the original script will be projected as part of the unlocking script.
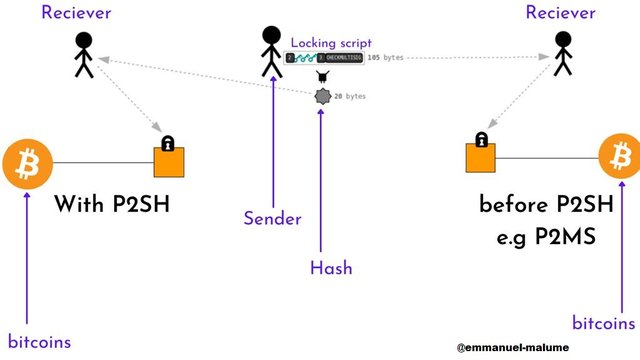
From the image above, we can deduce that until the advent of taproot and Schnorr signature to the bitcoin network, a normal transaction would end when the hash of the redeem script matches the ScriptPubKey. Now, with the use of BIP 16 feature, after the previous process, we allocate the redeem script to operation codes (opcodes), then script will run, sending BTC to multisignature addresses with a single hash.
P2PKH
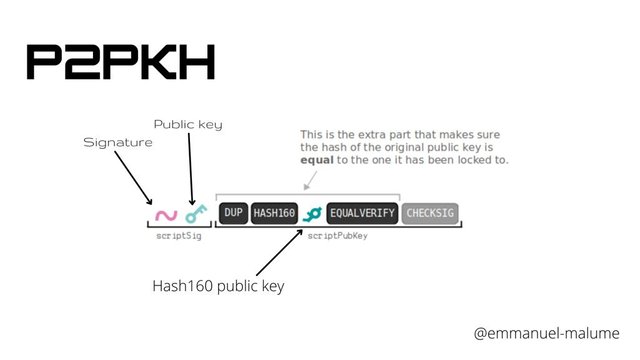
Ever seen something like this?
ScriptPubKey= OP_DUP OP_HASH160 <Public_KeyHash> OP_EQUAL OP_CHECKSIG
ScriptSig= <Signature,> <Public_Key>
Unless you're a programmer or something, you probably haven't seen this code before. This is the default program that runs in the background when we transact our bitcoins, and its called Pay-to-PubKey-Hash. It shares similar features with the P2PK, but the lock is a hash of a public key not the public key itself. Pay-to-Public-Key-Hash (P2PKH) is the default system of making a transaction and is the widely used transaction on the Bitcoin network. Bitcoin transactions contain P2PKH scripts that are evaluated successfully by sending the public key alongside a digital signature from the private key.
How P2PKH works
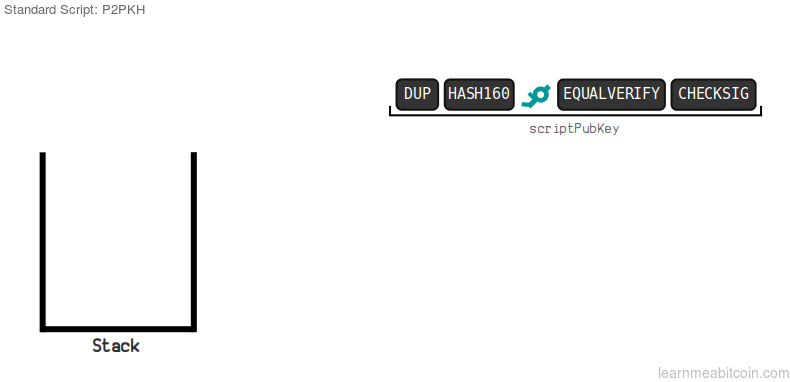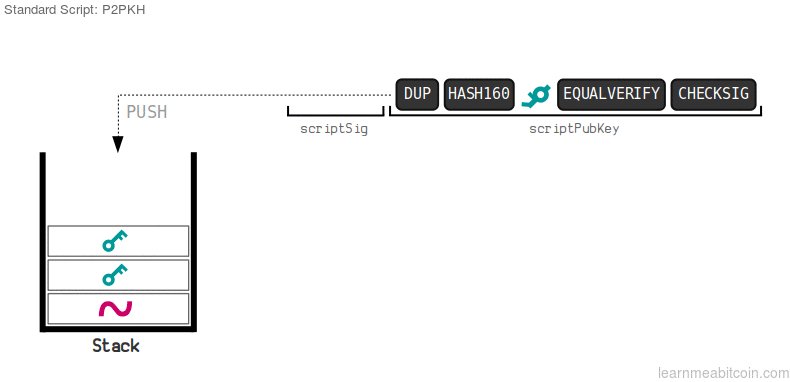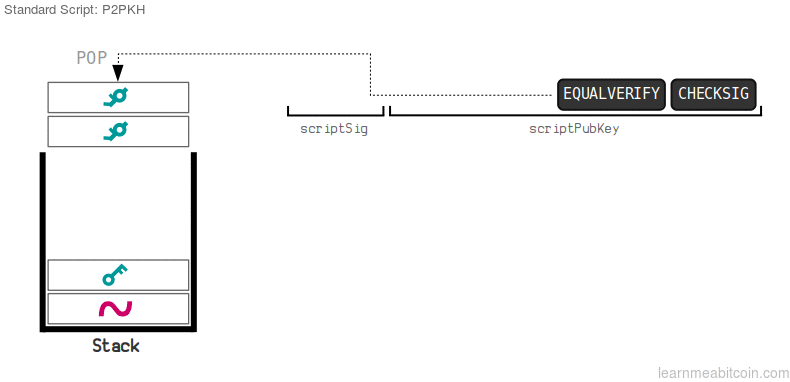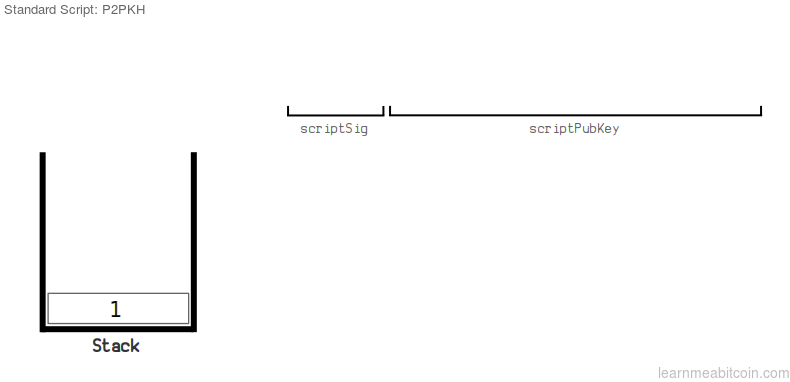
reference
The image above is a gif, showing the modus operandi of the default system on the bitcoin network, the P2PKH.
The owner of the funds provides the ScriptSig, containing the signature and public key. The public key is duplicated, then hashed to a 160-bit code. This hash is hashed value is compared to the hashed public key in ScriptPubKey by the equalverify opcode and if matches, the checksig then checks the signature against the public key

sample p2pkh from here
From the image above we can see:
ScriptSig: The script sig is the script for unlocking the funds. This transaction required one signature, and there is only one key required for authorization of this transaction. After this we see the operation codes.
sample signature:
304502203f004aeef0cef2715643e2f25a27a28f3c578e94c7f0f6a4df104e7d163f7f8f022100b8b248c1cfd8f77a0365107a9511d759b7544d979dd152a955c867afac0ef57839
sample Public key:
044d05240cfbd8a2786eda9dadd520c1609b8593ff8641018d57703d02ba687cf2f187f0cee2221c3afb1b5ff7888caced2423916b61444666ca1216f26181398cScriptPubKey: The scriptpubkey is responsible for locking the funds in, to be unlocked by the ScriptSig.
DUP: This commands a duplication of the original public key
HASH160: This command created a 160- bit, 40 digit hash of the public key
EQUALVERIFY: This opcode compares the hash of the publickey to the new hashed value
CHECKSIG: If the values match, the checksig inspects the signature, against the public key
Differences between the P2PKH and the P2SH
| P2PKH | P2SH |
|---|---|
| This is the default/widely used program for transactions on the bitcoin network | This was introduced in 2012 as an upgrade on the bitcoin network |
| The P2PKH is only for singular signature transactions | This supports multisignature transactions |
| Higher transaction fees | Lower transaction fees |
| Adresses begin with the numeric "1" | Adresses begin with the numeric "3" |
| This code duplicates the public key while running the script | This code does not require duplication |
| The adresses have high compatibility on the network | these addresses are less compatible in comparison |

2.- It is required to transfer 10 BTC that belong to a multisignature wallet 3 of 5, to the MTC company, for the purchase of some equipment. Use the ScriptSig and scriptPubKey to explain the steps that are followed. Explain What happens if the transaction is made using Schnorr signatures?

For a multiple signature portfolio of 3 of 5 signatures to send an amount of 10 BTC, It entails having 3 of those 5 addresses sign the transaction.
A company with 5 shareholders need to invest 10 BTC in the MTC company. Naturally, they all have their private keys, its is required for at least three to authorize the transaction for its success. This transaction will naturally involve a locking and an unlocking script, illustrated below:
- ScriptSig
~~~3️⃣🔑🔑🔑🔑🔑5️⃣CHECKMULTISIG
This code contains 3 signatures out of the 5 that can possibly authorize the transaction.
CHECKMULTISIG : this opcode checks the three signatures against the public key, unlocking the transaction if they are evaluated to be matching.
- ScriptPubKey
[ HASH160✳️EQUALVERIFY ]
The code above has the components, the hashing opcode, the publickey hash and evaluation opcode.
HASH160: This is the opcode for creating a 160-bit, 40 digit hash of the public key.
✳️: This is the public key hash
EQUALVERIFY: This compares the hash to the public key and evaluates it to be true.
Once this is done, MTC gets the has to the public key and therefore access to spend the BTC.
The code looks somewhat like this
{
"txid": "d3adb98d5e118bb856fbea4b1af936602454b44a98fc6c823aedc858b491fc13",
"hash": "d3adb18d5e118bb856fbea4b1af936602454b44a98fc6c823aedc858b491fc13",
"version": 1,
"size": 222,
"vsize": 222,
"weight": 888,
"locktime": 0,
"vin": [
{
"txid": "2b5a3b85fbea789b8b9b3d8a94490006496e6347aebad862da3108afa8e4161b",
"vout": 1,
"scriptSig": {
"asm": "307364504c3da378d8323a7233892b8050f738da69daf765ddc0d9815d9ad352286b70c2022100dff11c19338daa85ec5b124434de3b4378ebe8c56950348d5f66197af1d04f09[ALL] 04910ae6c9b41b04d366ea54e920663c691843bb83ef7336cd6a0f79b0ac82ee38d2ca23a24adc2348d82c8ca13f0db885712493e89d88551118a7e80ff66ab23c",
"hex": "48304502204c3da378d8323a7233892b8050f738da69daf765ddc0d9815d9ad352286b70c2022100dff11c19338daa85ec5b124434de3b4378ebe8c56950348d5f66197af1d04f09014104910ae6c9b41b04d366ea54e920663c691843bb83ef7336cd6a0f79b0ac82ee38d2ca23a24adc2348d82c8ca13f0db885712493e89d86483618a7e80ff66ab23c"
},
"sequence": 4294967295
}
],
"vout": [
{
"value": 10.00,
"n": 0,
"scriptPubKey": {
"asm": "OP_HASH160 b4acb9d78d6a6263844a60484c95de490eaaae75 OP_EQUAL",
"hex": "a914b4acb9d78d6a6256964a87674c95de490eaaae7587",
"address": "3JALUHKvqB7NToPA2jALntCUWmvsgYMyGj",
"type": "scripthash"
}
}
]
}

3.- Why do you think Taproot and Schnorr signatures will help the privacy of the Bitcoin network? Explain.

There are certain features in the Taproot and Schnorr protocol that can potentially increase privacy, some of them are:
Obscuration: Taproot enables different complex transactions (e.g. closing and opening Lightning Network channels, multi-sigs, etc.) to be shown as simple transactions on the blockchain. This process makes it possible for those smart contract transactions to pass along with the “regular” ones and cannot be monitored by an external eye
Anonymity of Transactions: Analysis software is working on creating clusters of wallets that similar yet distinguishable from other wallets, known as anonymity sets. In very simple terms, this entails the bigger (having more addresses) an anonymity set is the easier it is to secure privacy.
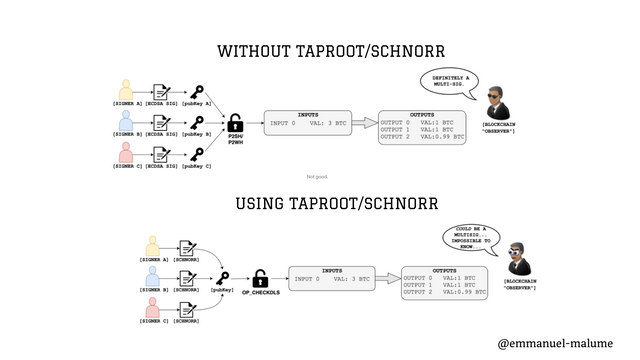
In P2SH transactions,in a 3 of 5 multisig transaction, the network would be aware of the fact that it is a multisig transaction, they will know how many signers validated it, and have access to information as regards the signers are. Thi means zero privacy.
Key aggregation on taproot however, keeps signers anonymous and keeps operational security at a maximal level by not revealing the keys required to unlock the portfolio. Key aggregation is also key to obscuring multisigs as regular transactions.The integration of Schnorr in Bitcoin will make obsolete the OP_CHECKSIG and OP_CHECKMULTISIG opcodes currently used with ECDSA and introduce a new class known OP_CHECKDLS. DLS means Discrete Log Signature and asided allowing signatures to be verified more efficiently with having to employ numerous opcodes., it is also discrete as the name implies.

4.- Using the Blockchain Demo, write exactly the following message: Schnorr Signatures, generate the signature of the message and verify the message. Then delete the first character of the message signature and check again What happened? Explain. Screenshots required.

First I opened the blockchain demo, then I typed in the message "schnorr signatures"
Then a private key was generated
next I clicked on "sign"
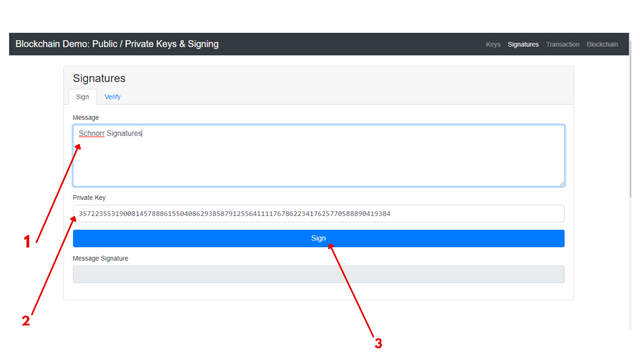
screenshot from here
A signature beginning with the numerical #3 was generated.
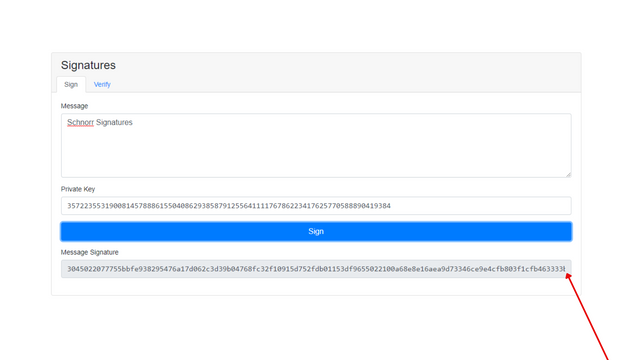
screenshot from here
Switching to the "verify" section
I clicked on the verify button
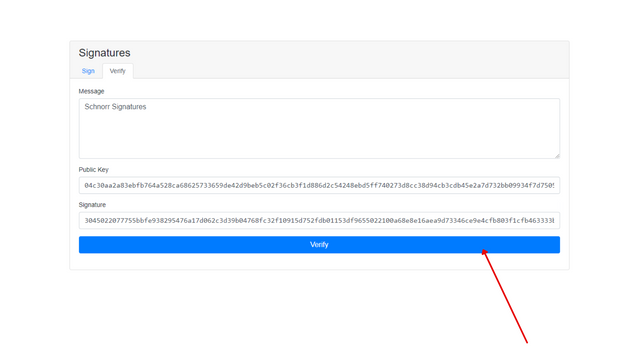
screenshot from here
The program scanned the signature against the key and evaluated it to be true and the background turned light green
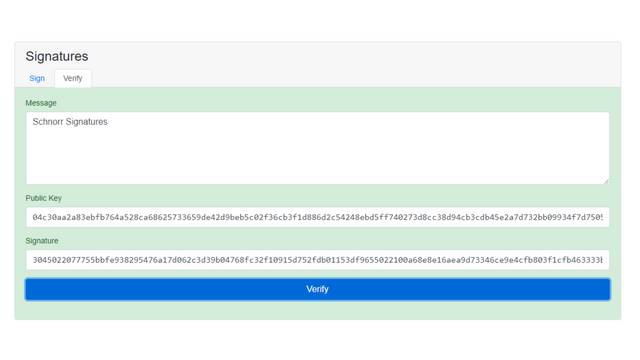
screenshot from here
Next I proceeded to make changes to the signature, by changing the 3 in front to 1, then clicking verify
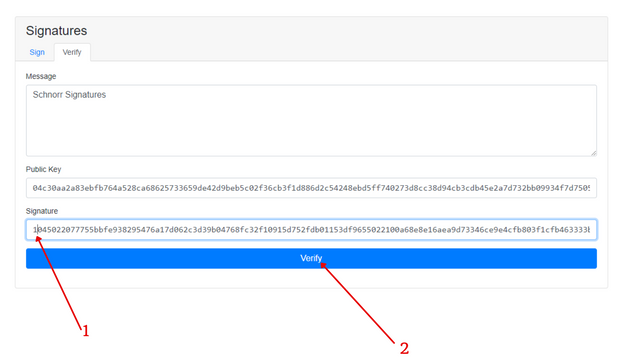
screenshot from here
After running the script, it didnt match, and the output was a light red background.
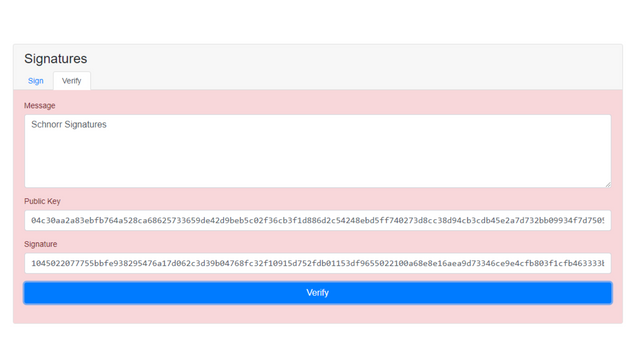
screenshot from here
This simple exercise demonstrated a 1 of 1 Signature transaction, and illustrated what happens when a wrong key is used, and the script is run. The verification proves false even when the change is just one character.

Conclusion

A very interesting topic indeed. We cannot cast aside the disadvantages this upgrade will present, however, the Taproot/Schnorr upgrades will have great impact on the scalability and privacy of bitcoin and I cannot wait for the integration into the blockchain.
This protocol is likely to bring about even wider adoption of bitcoin and cryptocurrencies in general, and the developers working on this deserve a big thank you from all of us.
Thank you @pelon53 for this wonderful lecture.
Good job boss
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit