Hello prof. @fredquantum, thanks for lecturing us on Mimblewimble Protocol, i must say i have really learnt so much. Below is my submission.
Mimblewimble was created by unknown people under the moniker Tom Elvis Jedusor, which is the French equivalent of "Voldemort." Mimblewimble, as per Jedusor, is intended to provide excellent protection and scalability than Bitcoin. Few blockchain developments made as much noise during 2018's crypto winter as the unveiling of Mimblewimble and its first cryptocurrency application, Grin, which saw its value skyrocket after its debut in premature 2018.
The Mimblewimble protocol gives privacy to its blocks using a special security structure that is very different from the ones implemented by other blockchains. Transactions are normally stored on a distributed ledger but with the Mimblewimble protocol these transactions are made very private as only participants of the transactions have the ability to access the details of the transactions. Details such as wallet addresses, amount, are hidden from the general public hence making it very confidential.
As read from prof. @fredquantum we got to know that the mimblewimble blockchain uses the Elliptic Curve Cryptography (ECC) methodology which is simply discrete maths which is just our usual logarithm we used to do. In this a number multiplies itself several times to equals a certain figure. This methodology is now used generate the private keys for transactions. Lets see some example of the mathematical theory.
2^10=1024 which can be written in the log form as log2 (1024) = 10
With the mimblewimble blockchain protocol the sender will have to encrypt the amount he or she desires to send into what we call blinding factors. These blinding factors are random chosen numbers assigned to the token that is been exchanged. The bling factor serves as proof of ownership so for the receiver to also receiver this token he is required to enter the blinding factor in order to validate the transaction.
In a case where I receive 3 btc from massachussets and 4 btc from john, It means that I now have 7 btc which I later send to Ibrahim the whole transaction will appear as a single transaction which will be Ben to Ibrahim. This technology is known as the cut-through technology.
Confidential Transactions (CTs) is among the permutations used by the Mimblewimble protocol to improve its privacy while also improving its platform.
Its implementation procedure does not include any cryptographic constraints and has a low and controlled runtime.
The Confidential Transactions (CTs) employ the Pedersen Commitment-based fundamental tool. However if the dedication is linked to a foreign entity, guessing the masking element and information would really be tough, but if both the data and the numbing component are exposed, they can perform the Transaction with the desired outcome in mind.
The blinding variable is always required because it adds an extra layer of security to the network; there without, the records can be quickly predicted and the pledge contained within can be revealed. Similarly, pledges can be established using the standard Pedersen obligation technique by adding the entire agreements and the content, which also includes the summation of the blinding factors.
This is achieved using the blinding factor, in this case the sender will assign the amount of crypto to be sent with random values that cannot be predicted by anyone, He then makes this blinding factor available to the receiver who will be required to enter same values to take ownership of the asset.
Nodes will verify the transaction by the blinding factor but will not see any further details of the transaction. Only the sender and receiver will have the opportunity to know the full details of the transaction.
In past years Bitcoin network has had issues with scalability and anonymity. These issues prompted the introduction of the SegWit fork. In all these attempts a lot can still be done in that aspect and the Mimblewimble protocol could help improve that effectively. In the following ways.
Bitcoin: Every transactions in the Bitcoin system are logged and publicly disclosed to the digital realm beginning with the blockchain network, but the donor and recipient's identities remain hidden (Privacy).
Mimblewimble: This just stores the relevant data, and that is to unload multiple data offshore, but it takes a step further by ensuring that the transfer specifics (Account identities, transfer Quantity, etc) stay between both the source and destination exclusively.
Bitcoin: The system has become less flexible in terms of the financial processing attributed to the prevalence of an Expanded Blockchain size Of data. (As a result, the Mimblewimble protocol is still required as a shoulder way of improving the bitcoin environment.)
Mimblewimble: Eliminates the existence of Bitcoin's programming mechanism, which permits it to retain all transaction history in its system. This offers for the elimination of certain transaction records, resulting in reduced stability congestion in its platform, giving it an advantage over Bitcoin due to the limited network data volume.
The Flash System can be configured in such a way that all of its segments and sub keep a low profile not just for the transmitter and recipient, but also for other data records such as account identities and quantity sent. Despite the lack of workers, the Off-chain system keeps its great scalability because there are accessible servers to connection with the acquisition.
SCALABILITY
One of the treasons accounting for the low scalability of the Bitcoin network is its block size. The Mimblewimble protocol has a feature called cut-through.With the cut-through feature the scalability of the Bitcoin network will be improved.
ANONYMITY
Transactions been anonymous is one advantage the blockchain has over the traditional banking system. With Bitcoin network some information of transactions are made public, like the wallet addresses involved. This can be improved by making use of the Mimblewimble protocol feature called confidential transactions. This feature makes good use of the blinding factor which has already been explained above. Details like amount are known to people involved in the transactions. The transactions are verified by nodes using the blinding factor but no detail is seen. Using this feature the anonymity of transactions on Bitcoin network will be improved.
PROS
- PRIVACY
Due to the confidential transactions feature that is used by Mimblewimble protocol transactions are very confidential and kept private. The addresses and amount in the transaction are hidden from the public and hence people get the desired privacy.
- IMPROVED SCALABILITY
One advantage of the Mimblewinble protocol is that scalability is improved because redundant data is scrapped off making transactions faster.
- FUNGIBILITY
It makes it impossible for the origin of coins to be tracked and the value of coins are maintained
The Mimblewimble protocol is also relies on digital signature and this makes it vulnerable to cyber attacks.
With the cut-through feature it slows down the transaction process which is a disadvantage.
BEAM
Beam is a cryptocurrency that is based on the Mimblewimble protocol and it is been headed by Alexander Zaidelson it was launched in 2019. It makes use the proof of work algorithm for its mining. A block contains up to 1000 transactions.
The beam blockchain is solemnly run on the proof-of-work system where members of the network have to solves some computational mathematical problems in order to maintain the security of the blockchain and prevent third-party or malicious activities or keep the network safe from hackers.
Taking a very good look at the beam blockchain we find out that it is built on the basis of the Mimblewimble protocol since it is able to offer both anonymity and scalability on the beam blockchain.
The Mimblewimble protocol do not use addresses like most blockchains do, instead they have what is known as the Unspent Transaction Output Model ( UTXO) . This is a form of encrypted transactions keys that only users have access to. These Output models are secured with keys known as “blinding keys”. So lets imagine the UTXO to be a safe, the blinding keys are what secured the safe and is therefore needed in order to successfully have access to the UTXO. The UTXO is very key in transactions of the beam blockchain.
For a successful transaction on the beam network, both wallets of the sender and the receiver has to be connected by means of communication. Both parties then enter their transaction information just like any other blockchain, enter the UTX and when the two are connected, the transaction is processed.
Features of the beam blockchain
Transactions on the beam network are anonymous or highly confidential.
Easy accessibly. The beam blockchain can be accessed on any smart ranging from laptops to even mobile phones.
The beam blockchain also offers different types of transaction methods.
The beam blockchain is also high in scalability . It possess a cut- through feature which makes the size of transactions smaller for easy completion or execution.
Some Statistics of the beam cryptocurrency
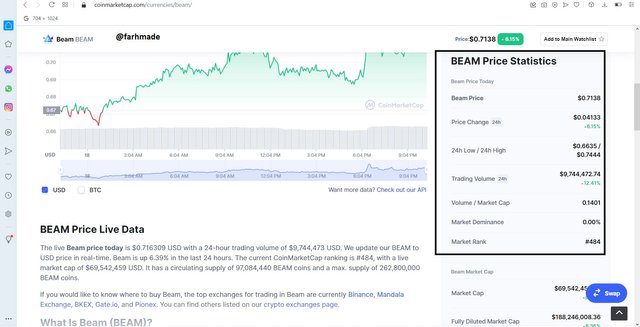
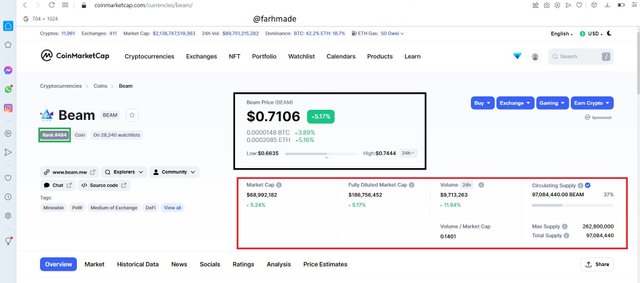
From the above screenshot we can the Beam cryptocurrency currently occupies the #484 position according to coinmarketcap in terms of its market cap and size. At the time of writing, its price was $0.7106 with a 24 hour price change of $0.0413. With a current trading volume of $9,713,263 , a market cap of $68,992,182 and a circulating supply of $97,084,440.
Per my own analysis I can see that the beam network has potential, so I believe we should take time to monitor this very good potential crypto asset, as it can be beneficial for a future hold.
Conclusion
Thanks so much @fredquantum for this wonderful lecture about Mimblewimble Protocol. As we learnt already that Mimblewimble was created by unknown people under the moniker Tom Elvis Jedusor, which is the French equivalent of "Voldemort." Mimblewimble, as per Jedusor, is intended to provide excellent protection and scalability than Bitcoin. The Mimblewimble protocol gives privacy to its blocks using a special security structure that is very different from the ones implemented by other blockchains.