1.- Explain in detail the hash rate.
A cryptographic hash function is a sort of hash function with qualities that make it useful in cryptography, one of which being the ability to create something that prevents third parties from accessing information.
Hashing power and speed are critical components of any PoW-mined cryptocurrency, such as Bitcoin.
Blockchains would not be able to function as distributed ledgers without hashes because decentralized processing power would not be directed to a specific function.
The hash rate refers to how quickly a cryptocurrency mining hardware works. To be effective in mining, you must be quick because the miner is essentially trying out many different solutions to the problem of solving blocks. And the more answers given in a shorter amount of time, the more likely it is that this block will be solved.
The hash rate, also known as hash power, is the number of attempts made to calculate the hash at a given point in time.
A higher ratio is better for mining because it increases the chance of discovering the next block and receiving a reward.
The network's complexity is proportional to its hash rate because as the network's power grows, so does its complexity. This is done in order to maintain the 600-second block creation duration.
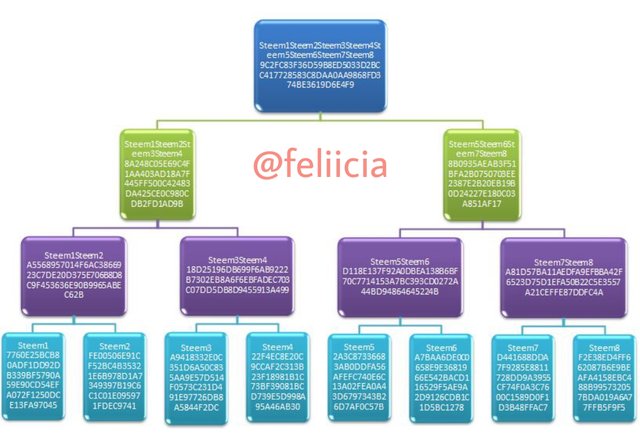
2.- Make the following Merkle Tree:
Transaction (tree leaves): Steem1; Steem2; Steem3; Steem4; Steem5; Steem6; Steem7; Steem8.
I made it to the Root Hash. And put every hash generated using SHA-256 , show screenshots.
Tell the steps to follow to verify if Steem6 is included in the Markle Tree.
Here is where to start
Steem1: 7760E25BCB80ADF1DD92DB339BF5790A59E90CD54EFA072F1250DCE13FA97045
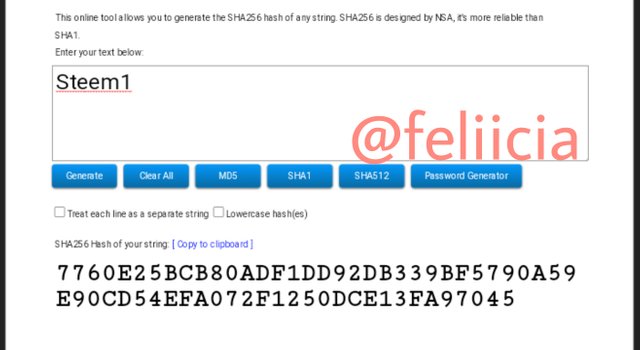
Steem2: FE00506E91CF52BC4B35321E6B978D1A7349397B19C6C1C01E095971FDEC9741
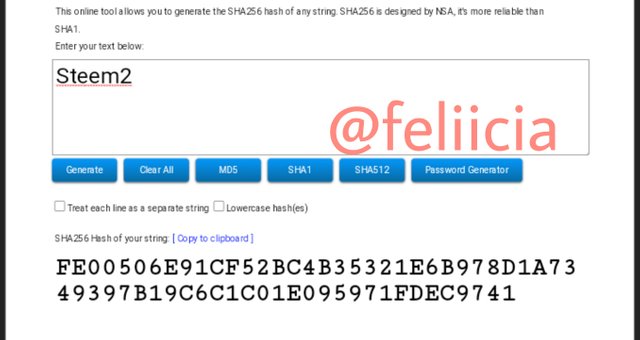
Steem3: A9418332E0C351D6A50C835AA9E57D514F0573C231D491E97726DB8A5844F2DC
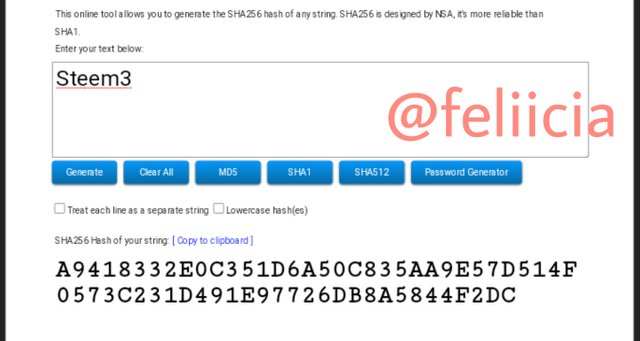
Steem4: 22F4EC8E20C9CCAF2C313B23F18981B1C73BF39081BCD739E5D998A95A46AB30
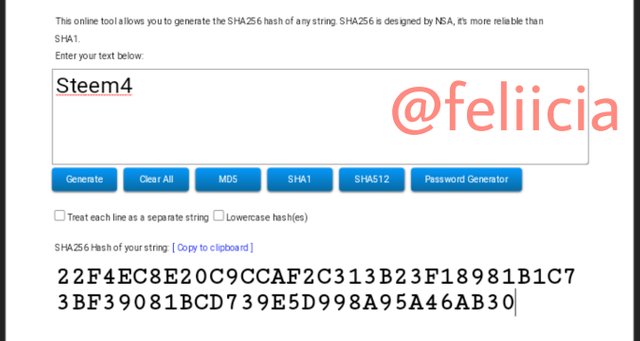
Steem5: 2A3C87336683AB0DDFA56AFEFC740E6C13A02FEA0A43D6797343B26D7AF0C57B
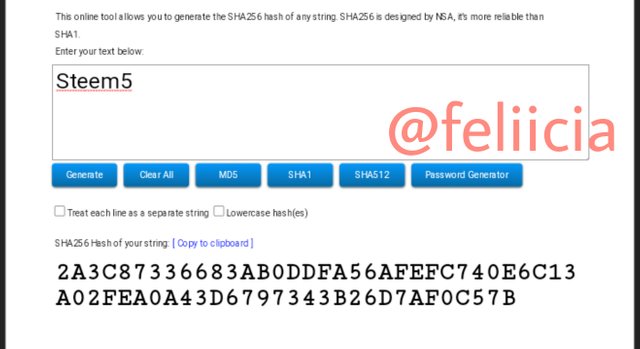
Steem6: A7BAA6DE0C0658E9E3681966E542BACD116529F5AE9A2D9126CDB1C1D5BC1278
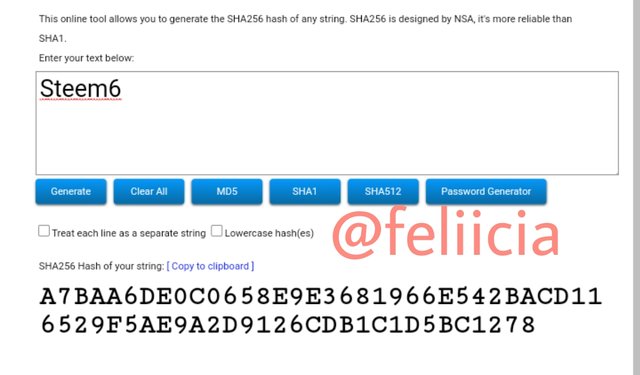
Steem7: D441688DDA7F9285E8811728DD9A3955CF74F0A3C7600C1589D0F1D3B48FFAC7
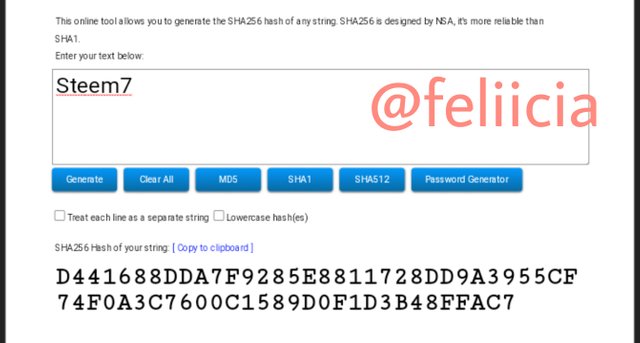
Steem8: F2E38ED4FF662087B6E9BEAFA4158EBC488B995732057BDA019A6A77FFB5F9F5
The next Step are the branches
Steem1Steem2: A5568957014F6AC3866923C7DE20D375E706B8D8C9F453636E90B9965ABEC62B
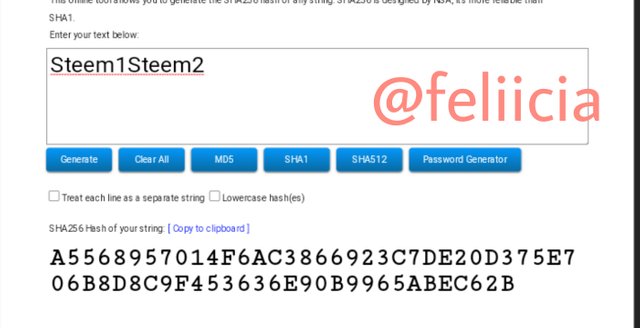
Steem3Steem4: 18D25196DB699F6AB9222B7302EB8A6F6EBFADEC703C07DD5DB8D9455913A499
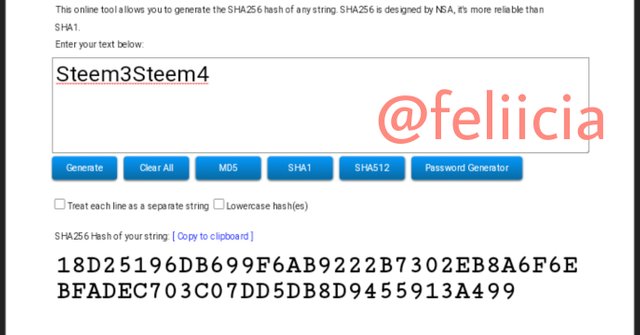
Steem5Steem6: D118E137F92A0DBEA138B6BF70C7714153A7BC393CD0272A44BD94864645224B
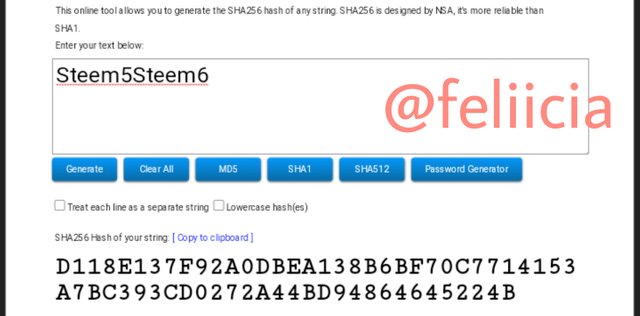
Steem7Steem8: A81D57BA11AEDFA9EFBBA42F6523D75D1EFA50B22C5E3557A21CEFFE87DDFC4A
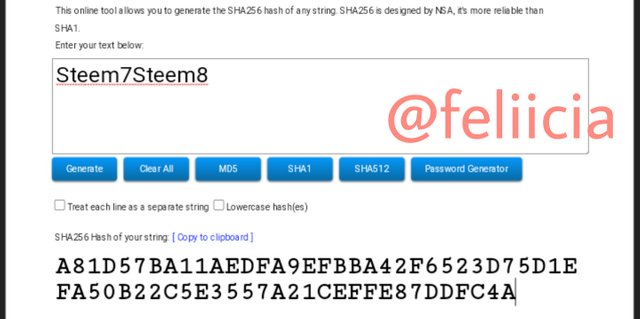
Now, the next level branches
Steem1Steem2Steem3Steem4: 8A248C05E69C4F1AA403AD18A7F445FF500C42483DA425CE0C980CDB2FD1AD9B
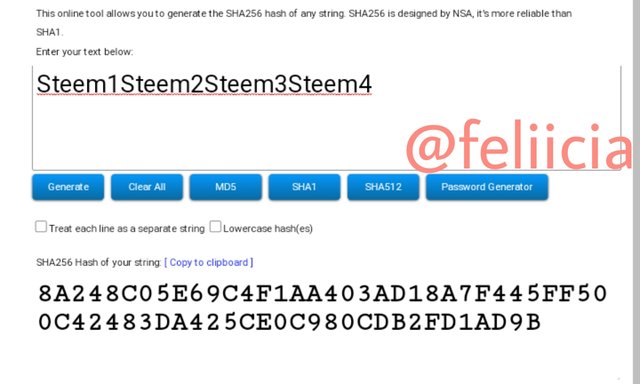
Steem5Steem6Steem7Steem8: 8B0935AEAB3F51BFA2B0750703EE2387E2B20EB19B0D24227E180C03A851AF17
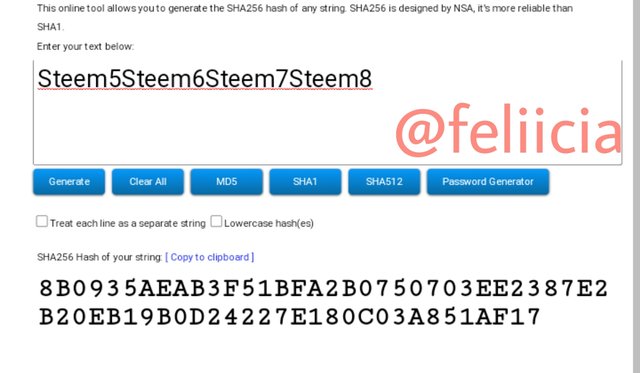
Now, the Merkle Tree Root hash is the next
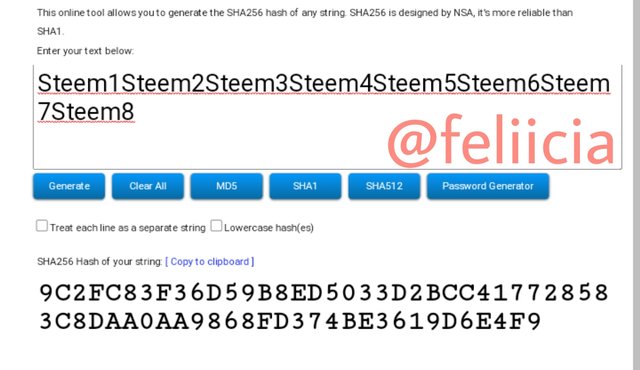
Steem1Steem2Steem3Steem4Steem5Steem6Steem7Steem8: 9C2FC83F36D59B8ED5033D2BCC417728583C8DAA0AA9868FD374BE3619D6E4F9
Merkle Tree
Tell the steps to follow to verify if Steem6 is included in the Markle Tree.
Steem6 can be verified when it has been completed: We must wait for all of the data from several peers to arrive before we can verify its legitimacy. If there are thousands of peers spread around the globe, the best strategy is to gather all of the data before validating if it is correct or included in the first place.
3.- Using the SHA-256; you must place each complete hash in the Merkle Tree.
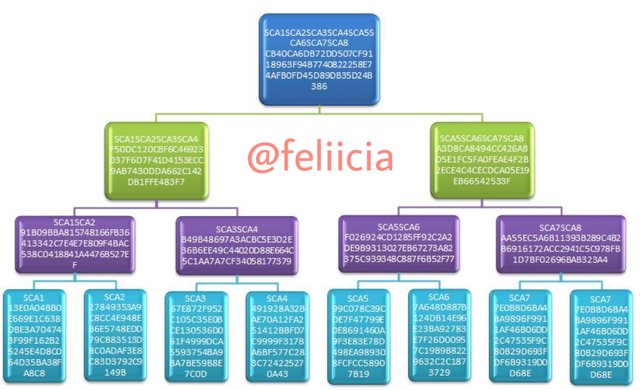
Transaction (tree leaves): SCA1; SCA2; SCA3; SCA4; SCA5; SCA6; SCA7; SCA8. Explain each step, show screenshots.
If the number of leaves on the tree is odd, what should you do? Explain.
SCA1: 13E0A04BB0E669E1C638DBE3A704743F99F162B25245E4D8C064D35BA38FA8C8
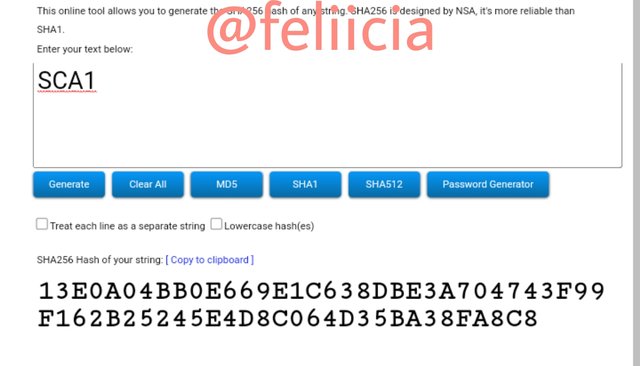
SCA2: 27849353A9C8CC4E948EB6E5748EDD79CB83513D8C0ADAF3E8C83D3792C9149B
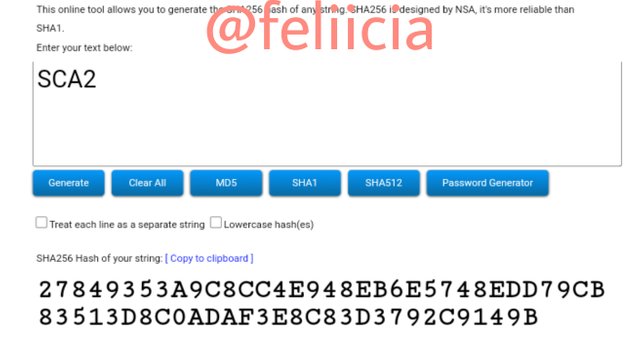
SCA3: 67E872F952C105C35E0BCE130536D061F4999DCA5593754BA9BA7BE59B8E7C0D
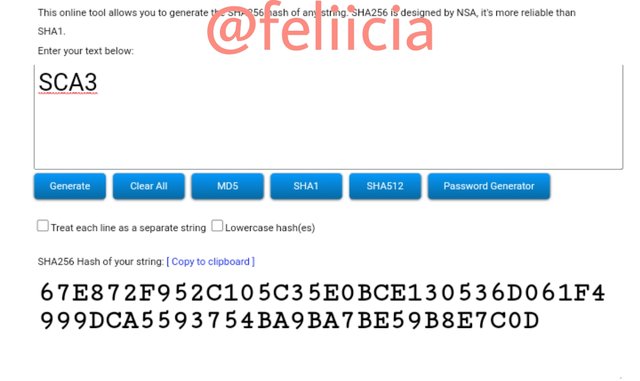
SCA4: 491928A32BAE70A12FA251412BBFD7C9999F317BA6BF577C283C724225270A43
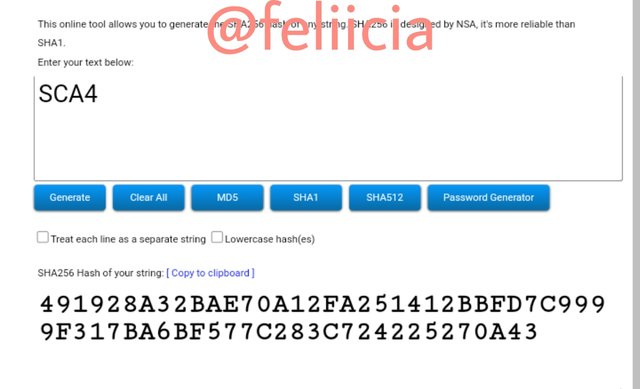
SCA5: 99C078C39CDE7F47799E0E8691460A9F3E83E78D498EA989308FCFCC58907B19
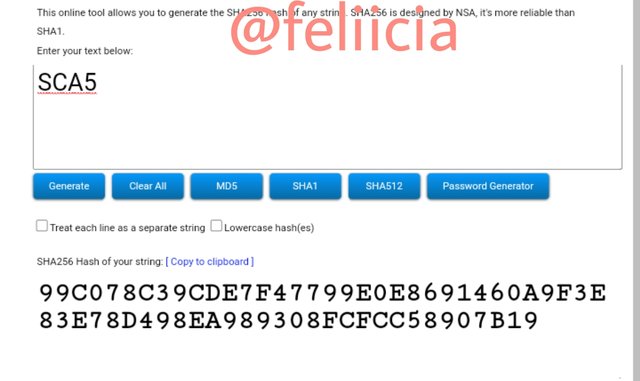
SCA6: 7A648D887B124DB14E96E23BA92783E7F26D00957C19B9B8229632C2C1873729
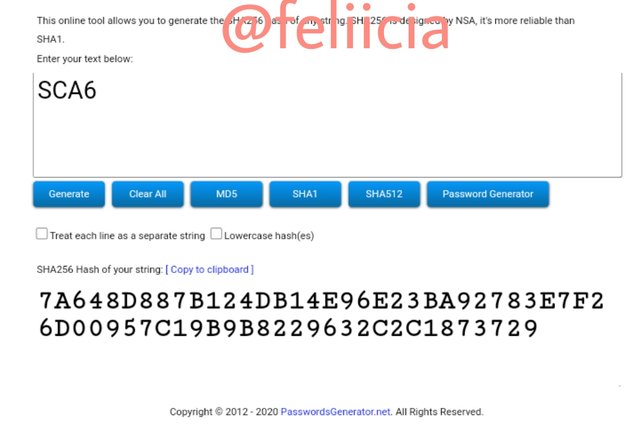
SCA7: 7E0BBD6BA4BA9896F9911AF46B06DD2C47535F9C80B29D693FDF6B9319D0D68E
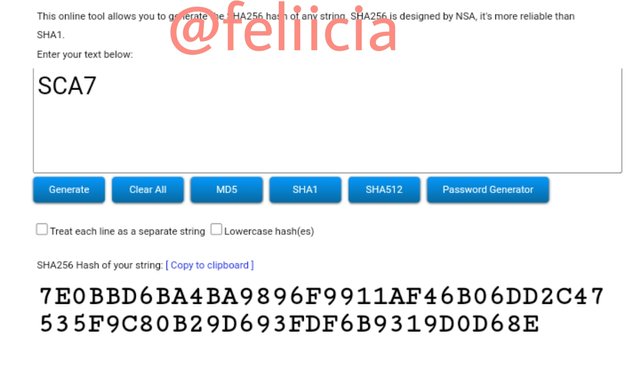
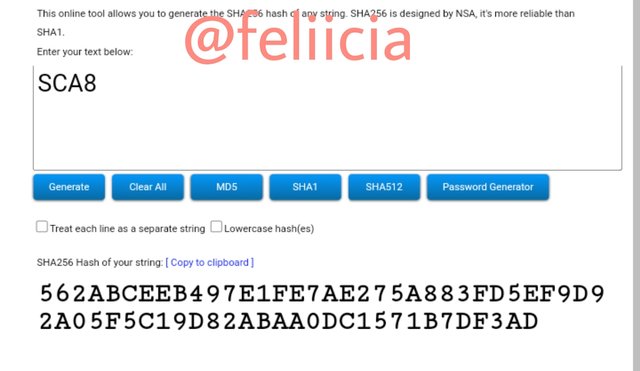
SCA8: 562ABCEEB497E1FE7AE275A883FD5EF9D92A05F5C19D82ABAA0DC1571B7DF3AD
The next step is to generate the tree branches
SCA1SCA2: 91B09BBA815748166FB36413342C7E4E7E809F4BAC538C0418841A4476B527EF
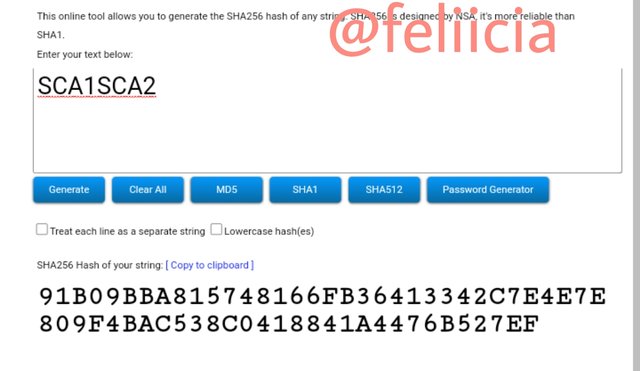
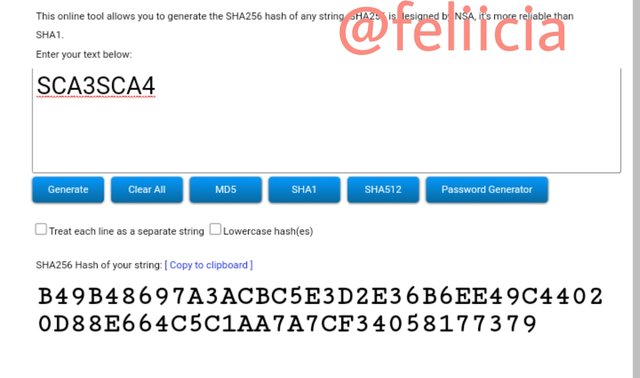
SCA3SCA4: B49B48697A3ACBC5E3D2E36B6EE49C44020D88E664C5C1AA7A7CF34058177379
SCA5SCA6: F026924CD1285FF92C2A2DE9B9313027EB67273A82375C939348C887F6B52F77

SCA7SCA8: AA55EC5A6B11393B289C4B2B6916172ACC2941C5C978FB1D7BF02696BAB323A4
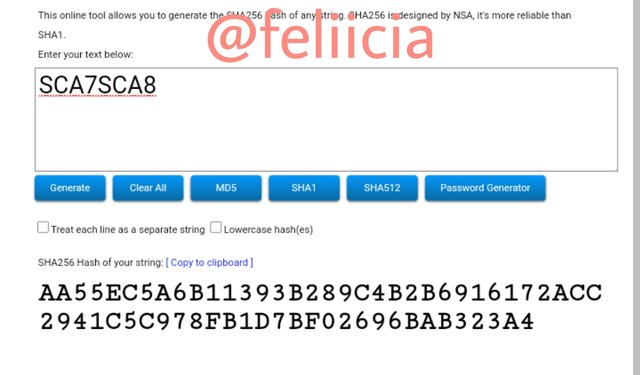
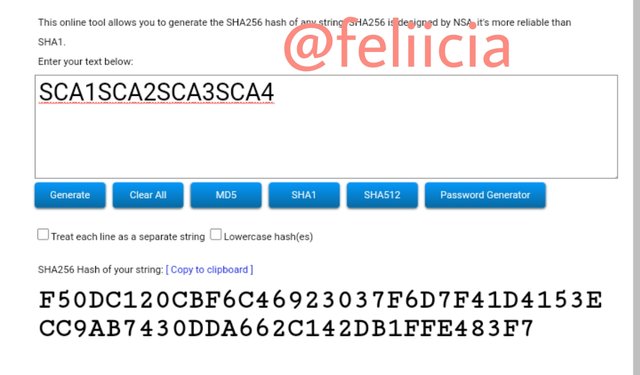
The second branches hashes is the next
SCA1SCA2SCA3SCA4: F50DC120CBF6C46923037F6D7F41D4153ECC9AB7430DDA662C142DB1FFE483F7
SCA5SCA6SCA7SCA8: A3D8CA8494CC426ABD5E1FC5FA0FEAE4F2B2ECE4C4CECDCA05E19EB66542533F
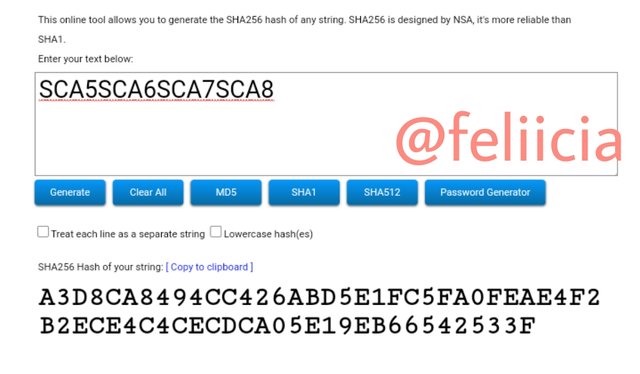
The Merkle Tree Root hash
SCA1SCA2SCA3SCA4SCA5SCA6SCA7SCA8: CB40CA6DB72DD507CF9118963F94B7740822258E74AFB0FD45D89DB35D24B386
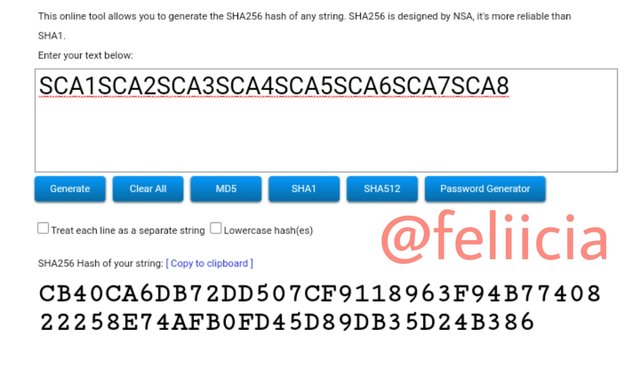
Merkle Tree
If the number of leaves on the tree is odd, what should you do? Explain.
Every successful, and useful merkle tree works in two piers. They don't work alone, working together in 2 piers is how it can perform what it was designed to do.
But possibly, if things doesn't go as programmed and the leaves is odd, while others has been completed in piers, the last number without piers will hash itself.
The last odd leave will come out in 2 places to fill the blank space and balance the equation.
If the leave equation doesn't balance in even number, the computed algorithm will not function.
One of the reason why it is called merkle "tree" is because it all works jointly together from the leaves down to the root.
E.g
If "pelon53" is the last leave and has no pier, and become odd, pelon53 will come in 2 places and hash itself. i.e "pelon53pelon53". Now it has become a pier and in total, the leaves has become even.
Conclussion
Hashing rates are increasing at an exponential rate, as are the ASIC capabilities of miners and users trying to ensure the Cryptocurrency network's security. Best regards to @pelon53 who has taught us a lot
Hash rate critical component of the ecosystem and an issue that every cryptocurrency user, investor, and trader should know and understand how it works.