
QUESTION 1: Explain the Blockchain Cryptography and mention few names which are the Blockchain platform (Few names of the Blockchain platforms)?
Background of the study
The word cryptography means coded information.
This method of information communication began thousands of years ago. It is a method of communication that the Egyptians usually used to pass information but called it scribes.
However, an Italian by name Leon Battista A. discovered something similar to cryptography called cipher in 1470 and it was adopted by United State Army as well.
Famous Julius Caesar used it as well.
It can be seen that this technology didn’t began recently.
However, let me proceed to what cryptography is really all about. Stay tune
Explaining Blockchain Cryptography
The word blockchain cryptography means a secure way the blockchain record and and encrypt datas sent to it such that the data becomes immutable in operation/nature. The operators have access to it through the help of their own private keys.
Just like a damaged document, the alteration of the documents automatically renders it invalid hence attracts.
It is this method that is used to protect the blockchain from hackers. Although it can be hack but apparently, the operation will be too expensive both in finance and operation as the initiators have to fulfill a minimum amount of 51% control of blockchain.
Furthermore, in the blockchain cryptography there are things which plays important roles. This includes hash, public keys, private keys.
It is the hash that contains the datas which was embedded into the block and gives an output display in an alphanumeric format which can’t be altered without it rendering itself invalid. The private keys and public keys serves as login keys and link verification keys respectively.
It is the applicable of cryptography on blockchain that fortifies pseudo-anonymous operation but yet accurate between the initiator and receiver without an iota if leak to a third party.
To comprehend above explanation better than expected, let’s check it features.
The features of blockchain cryptography
■ Unrejectable/undeniable: Datas sent can’t be rejected by the receiver. Neither the sender can deny it as well.
■ Reliability: Ones data is initiated and hashed, it remains immutable as such any iota of attempts renders it invalid hence alerts the initiator/receiver.
■ Sensitivity: Only the initiator and receiver gets the data and understand it as well. No leak to a third party.
■ Authenticity: The initiator and receiver can verify the identity as well as source of information.
The few names which are the Blockchain platform are;
a. Open ledger
b. Open chain
c. Ripple
d. Ethereum
e. EOS
f. Steem
g. Neo
QUESTION 2: Explain the public key cryptography
In a nutshell, public key is just like a bank account number which is used to verify the receiver.
Enumerating further, the public key is an alphanumeric lengthy key that is generate using the private keys. This keys can be shared to anyone just like an account number. It is the public key that generate public address through hashing.
However, from the above, it can be explained that the public keys is a link that the information will use to get to the receiver. It is the public key that is been recorded on the block.
How does this key works;
An initiator login with private keys, there’s a creation and sharing of public key in order to transfer the information. The initiator then pass the information to the receiver through it which will be encrypted automatically then the receiver access it using private key.
Some basic functions of it are
a. it is shareable unlike the private key.
b. The public key is generate using private key but it can not be used to generate private key.
c. it is a key that hashes public address that the initiator will use to send the data (cryptocurrency as well) to recipient.
d. it is alphanumeric in nature.
e. it is recorded in the encrypted block.
f. it offers recipient and initiator authentic security of the information against hackers
QUESTION 3: Explain the private key cryptography
The private key is the major key in cryptography. In fact, it can be regarded as the ancestral key.
It is the key that is used for encryption of the information and further perform the decryption as well. The private key is not shareable as it name implies hence it remains individual property. Whoever have access to it have a control of the fund in the wallets I.e capable of sending and receiving cryptocurrency in the wallet.
Private key is a lengthy alphanumeric key issued to wallet owner when the wallet is been created.
For a simple explanation, the private key cryptography is similar to Automatic Teller Machine (ATM) card pin issued to a user by bank after opening the account which he/she can use to perform a transaction (send/withdraw money) on the machine anytime and anywhere.
Some key points private key cryptography;
a. It is a key that secures the account against unauthorized access.
b. It contains a lengthy alphanumeric characters.
c. It is a key that is used to generate the public key.
QUESTION 4. Explain the Digital Signatures Cryptography and what is signing of transaction/messages?
Digital signature cryptography:
This may sound a little complicated to a random user so let me break down to a lowest level.
When a vital agreement is been made and a document is created, it is a signature that is used to fortify authenticity of the document. Same is applicable to digital signatures cryptography.
When a transaction is initiate using the private key, transaction is been signed and broadcast to miners who will then verifying the transaction by performing a validation on it using the public key.
Some of the importance of this includes;
● Time saving: Comparing to any analog means of signing, this method is very fast and less stressful as it is done on hash at ones.
● immutability: This automatically renders altered document invalid as it hash will not be different from initial.
● Authenticity: It further proves that the data is from the right source since it is achieved after login with private key.
Signing of transaction/transaction
Aforesaid, when a data is initiated, it is signed as well using the digital signatures format. The beginning and finishing of this has a two phase. The first is signing and the last is verification.
Signing: The data is been initiated and authorized by initiator using private key to create a public key that includes hashes which is broadcast to a miner. This covers the signing level of the transaction/message
verifying: At this second phase, a miner receives the public key and vet it authenticity. After a successful vetting and validation, the transaction is added to block and encrypt.
Basic difference between symmetric and asymmetric cryptography;
| Symmetric cryptography | Asymmetric cryptography |
|---|---|
| This cryptography makes use of one key for both encryption and decryption of text which is shared among the initiator and recipient/receiver | This cryptography make use of multiple keys. A private key for generating the information, a public key which will be the link for encrypted information to get to the recipient and the recipient’s private key as well which will be used to decrypt the information. |
QUESTION 5: What is symmetric and Asymmetric cryptography
SYMMETRIC CRYPTOGRAPHY:
Otherwise known as Secret-key cryptography This is the using of one key for encryption and decryption of data by initiator and receiver thus eliminating private key and public key.
When the data is changed to a cipher text(encrypt) using a symmetric key, the same key will be used to convert it again to readable text/data through decryption by the receiver.
This method of data security is always been use when two or more parties circulate information within themselves.
Furthermore, the alphanumeric character are generate using a secured technique program called Random Number Generator (RNG).
Basically, there are two types of symmetric cryptography algorithm.
They are;
- Block algorithm
- Stream algorithm
Block algorithm:
In this symmetric cryptography, the data are retained and encrypt in the system memory while waiting for completion of the blocks. Furthermore, data are encrypt in blocks base on it key length.
Examples:
- Advance Encryption Standard (AES) also known as Rijindael.
- International Data Encryption Algorithm (IDEA)
- Blowfish
- RC5 (Rivest cipher 5) etc
Stream algorithm
As it name implies, data is not retain on the system but streams and encrypt as well. The data is encrypt byte by bytes i.e one byte after another.
Example:
- RC 4 etc.
The symmetric cryptography have some features which are;
a. It 128 bits characters fortify it security by having a total of 34x10^37 combination.
b. Same key is used for encryption and decryption of sent and received data.
c. It has a minimum of 128 bits and a maximum of 265 bits characters.
Advantages and Disadvantages of symmetric cryptography
Advantages
Highly secured: Even if the computer launches brute-force attack against it, it can never be hack. Thus the symmetric algorithm is unbreakable.
Key sharing: Both party have to own the same key before they can pass information to each other.
Speed: Comparing it to counterpart, it is relatively fast and there is no need for a miner to validate the block.
Disadvantages
Risk of compromise: The larger the group, the greater the chance of the key been expose by one person
Asymmetric cryptography:
otherwise known as public-key cryptography. unlike the symmetric cryptography, it is a cryptography that make uses of multiple keys for it operation.
In asymmetric cryptography, the initiator of the transaction uses the private key to generate another alphanumeric code which will be use for validation and on receiving the transaction, the receiver uses the private key to decrypt the information to readable format.
The public key is recorded on the block and known to both parties while the private key remains a private property just as it name implies.
Analyzing the above explanation in practical;
a. Mr Joe wants to pass a confidential information/document to Mr Simon.
b. Mr Joe and Mar Simon will share the public key among themselves.
c. Mr Joe will send the confidential information/document to Mr Simon in an encrypted format through the public key which was shared.
d. On receiving the information in encrypted format, Mr Simon will use his private key to decrypt the confidential information/document into a readable format.
Examples of asymmetric cryptography are;
a. TLS/SSL protocol
b. Digital Signature Standard (DSS)
c. Diffie-Hellman exchange
d. Rivest Shamir Adleman (RSA) etc.
Features of asymmetric cryptography;
a. The private key is used to generate the public key which will serves as an address that the information/data will through to it received
b. The private key is not shareable but the public key is shared among the party involved and recorded on the block as well
c. Receiver uses his/her own private key to decrypt the message to readable text.
Advantages and disadvantages of asymmetric cryptography
Advantages
Highly secured since there’s no need for sharing of encryption and decryption keys
Disadvantages
Slow when compared to it counterpart (symmetric cryptography)
QUESTION 6: How Blockchain wallets cryptography works and explains the available types of crypto wallets.
First, let’s understand what a blockchain wallet is all about.
Blockchain wallet: This is a digital base wallets that stores/holds the cryptocurrency of it user and protects it using the private key.
The terms digital base means that it recorded online and can only be accessed using a phone or computer.
Unlike a standard bank account whereby the identity of it user can be traced through it, the blockchain wallet offers anonymous but yet a save operation of the user in a decentralized way.
(Design here)
How Blockchain wallets cryptography works:
Aforesaid in the last paragraph about blockchain wallet, this wallet works using the private key which is used for protection of the wallet and public key operation that’s gives a hash output called wallet address which serves as a link for sending/receiving cryptocurrency.
Let’s enumerate this three keys individually according to their operation;
wallet private key: The primary key that controls unauthorized access to wallet and used to generate the public key as well.
This key is also used to facilitate a transaction by initiating a digital signature in order to broadcast it to miners nodes.
Furthermore, this key can be used for regaining the fund if it owner loss his/her device that the wallet was installed on.
The private key is lengthy and contains alphanumeric character.
Wallet address: An address for sending/receiving the cryptocurrency which is generate as a result of the hash output of public key.
In reality, this is similar to a bank account number which can be used for transferring fiat currency.
Wallet public key: This is an alphanumeric character key that is generate using private key and used by miners by validation.
In summary, the cryptocurrency wallet doesn’t operate on verification of the users identity as such rendering sender’s/receiver’s anonymity. Furthermore, lost fund can’t be recovered.
There are basically different types but all falls on 2 categories which are;
a. The hot crypto wallet
b. The cold crypto wallet
Hot wallet: This cryptocurrency wallet is an online base wallet as such it is vulnerable to attack by hackers hence owner of the wallet are always advised to safeguard their private keys.
Unlike it counterpart, the hot cryptocurrency wallet is faster in operation thus offer an easy spending of the funds in it. The hybrid wallet e.g BTCpay, desktop wallet e.g Electrum and mobile wallet e.g Coinbase falls under this type of wallet.
In fact, the hot wallet is the most used and easy to operate cryptocurrencies wallet.
Advantages
♤ Unlike it counterpart (cold cryptocurrency wallet), hot wallet is easy, fast and simple to operate as such it facilitate easy spending of the funds in it.
♤ Hot crypto wallet cost less to own and operate
Disadvantages
♡ vulnerable to attack as such large amount of funds are not advisable to be stored on it.
♡ |The real aim of Nakamoto Satoshi was to make cryptocurrency decentralize in nature without any iota of intermediate but the wallet tends to eliminate this because of the exchange as such the owner of the wallet doesn’t have total control of the wallet.
Cold wallet: This is an offline base cryptocurrency wallet that operates in form of USB storage which is been connected when a transaction is needed. The cold cryptocurrency wallet is the most save and secured wallet for cryptocurrency.
The types of this wallets are;
a. Hardware wallet
b. Paper wallet
Hardware wallet: This are type of cold cryptocurrency wallet that have both offline private and public keys but their operation are done online. A typical example is Trezor etc.
Paper wallet: Considered as the most secured and critical to understand as such rated by many as outdate wallet. The own have a hardcopy (paper format) of the keys (both private and public) but unfortunately, not all cryptocurrency can be stored on this wallet.
Advantages | Disadvantages
This wallet is highly secured from hackers since it is not an internet base wallet | Compared to it counterpart (hot wallet), this wallet is very slow in operation and not suitable for everyday transaction.
It is a wallet that is suitable for storing large quantities of cryptocurrencies | This wallet requires high protection of the hardcopy by it owner.
Hot cryptocurrency wallet | Cold cryptocurrency wallet
It is the wallet for day to day transaction.
Exchange links such as Coinbase, trustwallet etc are typical examples of it.
Users are not in total control of the wallet as there is an intermediates (exchange agent) that safeguard it.
This wallet is vulnerable to hack | it’s the best wallet for safekeeping large quantities of funds.
The cold wallet offers users total control of their funds.
This wallet is slow in operation and not support by many cryptocurrency.
QUESTION 7: What is the Merkle trees and what it’s importance in blockchain.
Invented by Sir. Ralph Merkle in 1979, used for arranging data in a blockchain using a tree like nature. It is the merkle tree that performs an act of compressing and reducing the size memory that node need to execute it operation on the block.
Merkle tree consist of three basis things which are; the Merkle root, the Merkle leaf node and Merkle branch.
Without Merkle three, the node will encounter a time consuming challenge of validation due to the large size of files. This tree is achieved when the hashes of the block are continuously merged till it remains one which becomes the root.
Merle tree appears in even number I.e double pairs. Any odd Markel of transaction is regenerate to have leaf node of even number. Summarizing of the all hashes to a single hash in a block of a blockchain is done by markel tree.
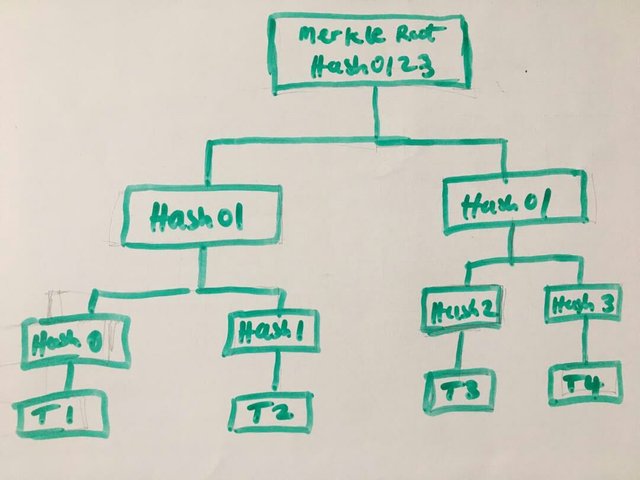
From the diagram above, Transaction which is denoted as T is independent to the next but it hashes relates them as they approach the Merkle Root I.e T1 relates to T2 and they approach hash1 of which same is applicable to T3 and T4. This formate is what makes the markel tree to reduce to a large data to small size but all can be accessible from from.
Any odd outcome is regenerated to have an even number as everything is in two pairs.
In fact, comparing it to mobile phone, it is folders inside a folder (Root folder) which the root folder have access all the folders.
- Provision of more space on the memory.
- Any attempt on it alters everything and render them invalid.
- Helps to speed up operation of node on the blockchain.
QUESTION 8: Practical + Theory, do some practical research, study on Blockchain Demo: Public/Private Keys & Signing and then explain the functionality of key, signature, Transaction, Blockchain and proper screenshots of your practical.
KEYS:
As aforesaid, this alphanumeric key is used in asymmetric cryptography. The demo site will show a practical proves of how this keys (private and public keys) relates to each other.
First step: I login to the website. This is the interface below and as you can see, there are YouTube videos that one can gets to learn more from.
I clicked on the key menu shown above. It took me to the keys (public and private) interface of the site.
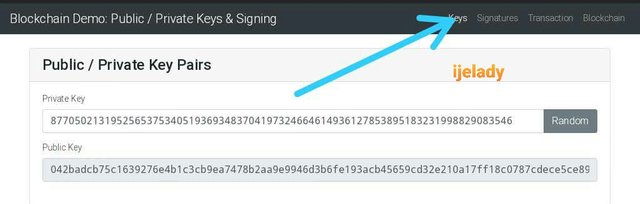
Checking closely, you see a private key that relates with public key as the are interlinked.
Below are the details.
Private key:
87705021319525653753405193693483704197324664614936127853895183231998829083546
Public key:
042badcb75c1639276e4b1c3cb9ea7478b2aa9e9946d3b6fe193acb45659cd32e210a17ff18c0787cdece5ce89018157040ab3f8d46d44a8aabd9d13d33ee12577
To see how this keys relates to each other, I clicked on Random
As seen below, the private key changes and the public key does same immediately.
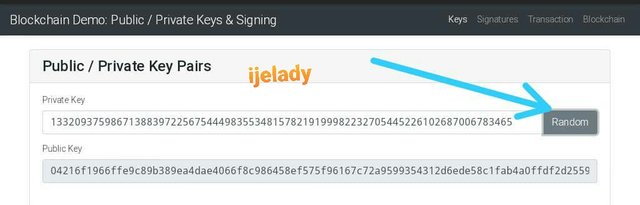
Private key:
13320937598671388397225675444983553481578219199982232705445226102687006783465
Public key:
04216f1966ffe9c89b389ea4dae4066f8c986458ef575f96167c72a9599354312d6ede58c1fab4a0ffdf2d25599acb302ee6fb7e93ab597d771eeb4ef8f0ff147a
Every click on the Random button keep showing it.
Let’s change the private key manually and see what will be it outcome.
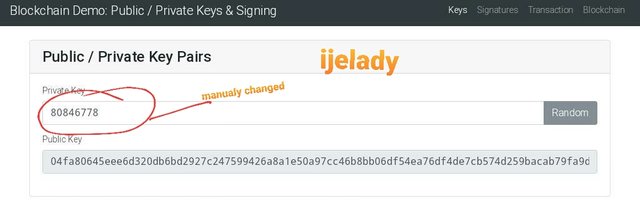
Private key:
80846778
Public key:
04fa80645eee6d320db6bd2927c247599426a8a1e50a97cc46b8bb06df54ea76df4de7cb574d259bacab79fa9dc9b3343ec3d323398154a43aad2e95b39d987b40
Based on what is seen on the above illustrations, it proves the practical view of asymmetric cryptography where two different keys works together but one depends on the other.
Signature
In this practical, I’ll be illustrating how a message is be signed using digital signatures.
First, i clicked on signature menu and Proceed to input my message that I want to sign as seen on the message interface which is Crypto academy assignment, followed by my private key which is 80846778 and proceeded to sign it by clicking on the sign button.
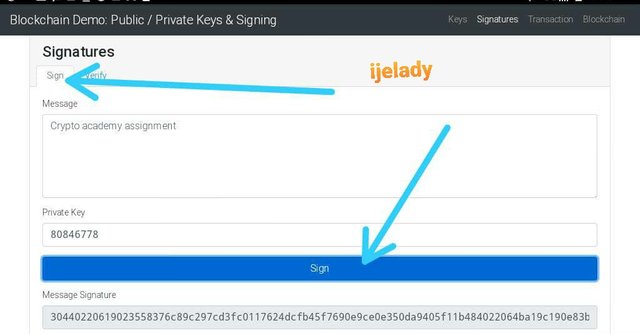
As seen above, the signature of my transaction have been achieved which is
Message signature:
30440220619023558376c89c297cd3fc0117624dcfb45f7690e9ce0e350da9405f11b484022064ba19c190e83ba8b122a5f2a5a443ce16c03b20116cf51918006b66d5952480
At this point, the miners attention is needed for verification of the signature hence adding to block.
I proceed to click verify
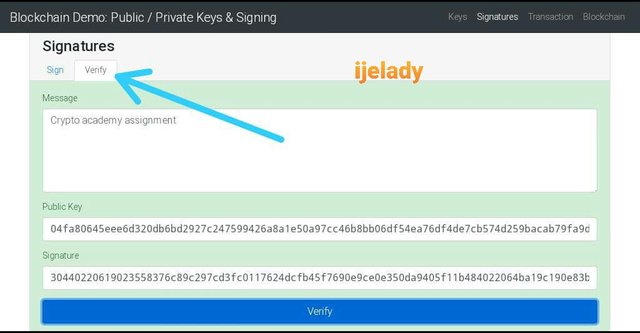
The transaction is completely verified and recorded on blockchain that’s why the demo change the color to green as well.
Public key
04fa80645eee6d320db6bd2927c247599426a8a1e50a97cc46b8bb06df54ea76df4de7cb574d259bacab79fa9dc9b3343ec3d323398154a43aad2e95b39d987b40
Signature:
30440220619023558376c89c297cd3fc0117624dcfb45f7690e9ce0e350da9405f11b484022064ba19c190e83ba8b122a5f2a5a443ce16c03b20116cf51918006b66d5952480
Transaction
In this practical, I first click on transaction menu and put my $30 that will be sent to the receiver through the public key.
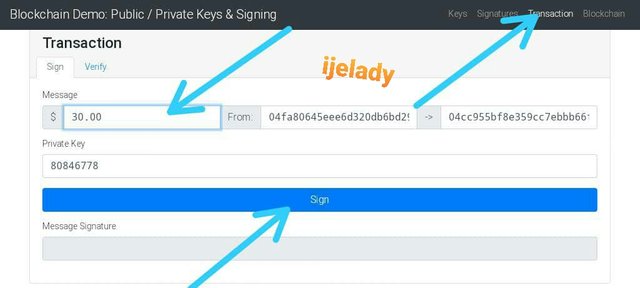
I clicked on sign and the message signature is generate as seen below.
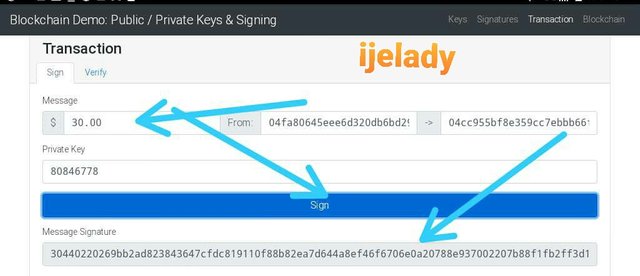
Since my public key have been broadcast for a miner to validate and verify the transaction, I clicked on verify
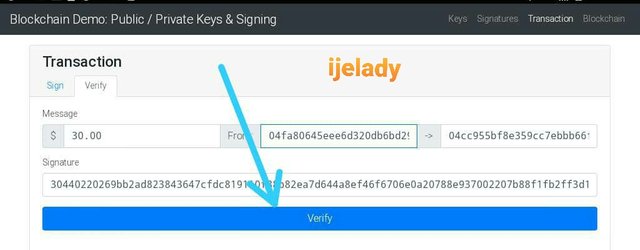
The transaction is confirmed and received.
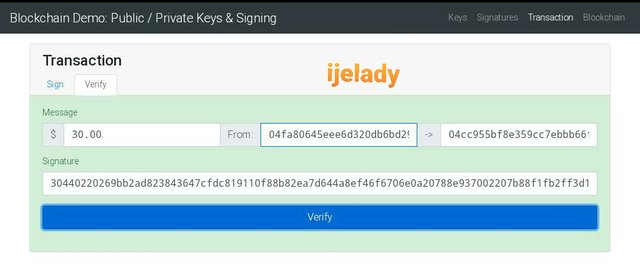
The demo website change it color to green* as a proof.
The above transaction have been recorded on the blockchain with hash immediately the miner validated it.
Blockchain
Let’s proceed to the blockchain in order to check out it is and make few alterations to see the outcome.
Here is the blockchain interfaces. All the blocks in it are valid. The first is the genesis block and it has a previous hash of zeros while other blocks are connected to each other by copying hash of the previous block.
For a block to become a valid block, it hash must begin with Zeros
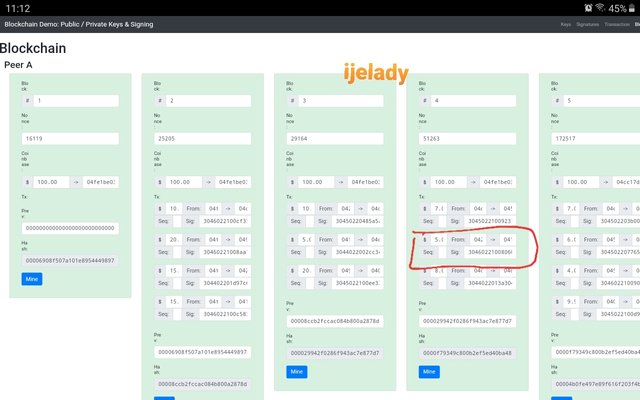
After understanding the block in blockchain from the above little explanation, let’s proceed to edit a block
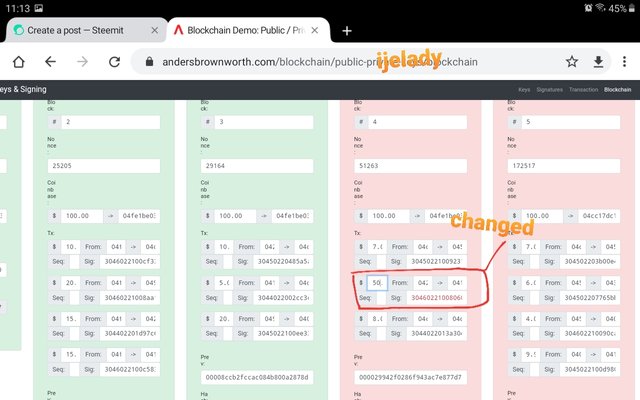
As seen above, block 4 is edited and it automatically becomes invalid. This affected block 5, since copies of block 4 previous hash is in block 5.
To revalidate this blocks, a suitable nonce will be used. To get the nonce, I click on mine and repeat same on block 4 and 5 respectively.
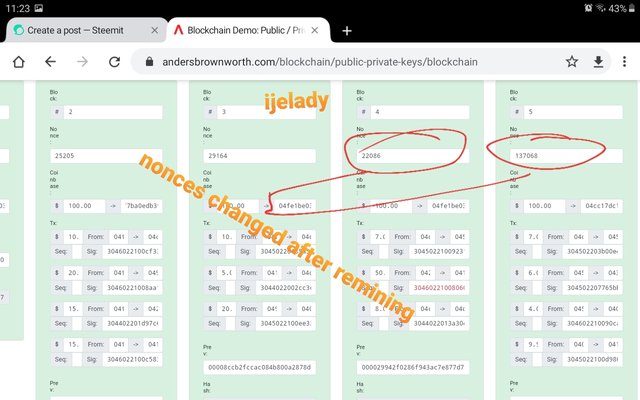
As seen, I’ve successfully remine the two blocks and they are all valid again.
This is achieved by having a valid nonce
Conclusion
The advent of cryptography remains the best solution for transaction of data without and iota of leakage. The ability to execute this is base on it encryption of plain text and decrypt when received. The private key remains the primary key that generates public key.
The hot wallet uses asymmetric cryptography for it security. Here the private keys generates the public key and render digital signature as well.
On the blockchain, every block are connected to each other by copying the hash of the previous block and any changes makes the block invalid hence need to be remine.
Much respect to Prof. @stream4u for this amazing lecture.