IMAGE MADE BY ME
Hello crypto friends,
I believe you are all doing great. I wish to use this medium to welcome you to the week6 of the season 5 of the steemit crypto academy.
This week's lecture was given by our amiable Prof @pelon53 on the topic Taproot and Schnorr Signatures
Please don't miss out, join us as we begin our adventure
EXPLAIN IN DETAILS THE P2SH AND P2PKH, SHOW THE DIFFERENCES BETWEEN BOTH DIRECTION
EXPLAIN IN DETAILS THE P2SH AND P2PKH, SHOW THE DIFFERENCES BETWEEN BOTH DIRECTION
The P2SH, being an acronym for Pay-to-script-hash is refered to a scriptpubkey type which permits the creation of addresses which can be used to send or receive transaction, provided that a set of laid down instructions are strictly adhered to, which in turn, unlocks the balances that are contained in those created addresses.
The P2SH can also be referred to a script format that is used on the BTC network which permits a user to lock BTC in the script hash and then make available the original script of the transaction after the BTC has been unlocked.
This feature, however, make the creation and distribution of redemption scripts easy and possible, and it also gives room for the creation of addresses with unconventional programming, and the only way to unlock it, is by adhering to the rules and regulations behind it.
The P2SH was implemented into the BTC network in the year 2012 and through this implementation, transactions are sent, not t a public keys hash but to a script hash.
This means that the transactions are made only to addresses that begins with 3 and not 1.
As earlier stated, the transaction is no longer made to a public key hash as it used to be, instead, it is now made to the script hash on the chain and thus accomplishes the following:
It keeps the locking script hidden untill the coins are moved elsewhere by the payee.
It enhances funds saving by saving an annotated version of the locking script rather than the script itself
It brings about a complete turn around to the logic of validation of BTC.
It is also of importance to note that the P2SH was brought to the BTC network on the 1st of April 2012, which was at the mining period of block 173805.
The introduction of the P2SH permits users to send BTC with a lesser worry about how the access to the payment will be unlocked by the receiver.
It also makes room for senders to push the burdens of making extra payment on the receivers rather than on themselves.
Before the introduction of P2SH, there was no standardised method to ensure the implementation of these scripts, the only available means was the use of a customized script which was time consuming and complex for most users. But this challenge was solved by P2SH through the use of recognisable bitcoin wallet address and easy to use hash formats.
WORKING PRINCIPLE OF P2SH
The method of operation of P2SH is similar to that of p2pkh, in that, both ensures that the payment made to a specific hash is locked.
A hash, also known as digest is the output of a cryptographic hash function.
To make P2SH payments, additional digital signatures from different private keys will be needed alongside the ordinary pubkey verification.
These additional signatures is what is known as a script, and it's hash is needed to lock a payment in the P2SH transaction.
Also, once a hashed script posseses some locked funds, they can only be unlocked and used when the original script initially used to create that hash is inputted, this script is known as the redeem script.
ADVANTAGES OF P2SH PAYMENTS
SECURITY:
The P2SH ensures a very high level of security like the p2pkh, through the use of cryptographic hashingSPEED:
The P2SH makes use of a lesser ram than of p2pkh for it's operation, and this thus guarantees high speed of transaction validation.SUPPORT OF SEGWIT AND NON-SEGWIT:
Another advantage of P2SH is that it is highly compatible with segwit(Bech32) and non-segwit(p2pkh) addresses, and this makes it possible for users to transfer BTC stored in P2SH format to any of the above mentioned format.Another advantage of the P2SH is it's ability to support a multi-signature transaction, and this also helps to enhance it's security.
The introduction of P2SH has help to reduce the burden of writing complex logic before a transaction can be made.
P2PKH ( PAY TO PUBLIC KEY HASH)
The p2pkh which is an acronym for Pay-To- Public-Script-Hash is a kind of scriptpubkey whereby BTC are locked to the hash of a public key(an address).
The P2PKH plays a vital role when it comes to BTC transactions. It serves as guidelines on the blockchain for users with the intention of making a BTC transaction to another.
In P2PKH transaction, a complex cryptographic mechanism is usually demonstrated by users which aims at proving that such users are the true owners of the public and private keys, which is used to receive and spend payments.
The P2PKH was developed as an improvement to the p2pk, which was vulnerable to the attacks imposed by quantum computers.
The working principle of p2pkh and p2pk is quite similar, the only difference is that the p2pk doesn't require the full public key of the scriptpubkey, at the point of receiving transaction.
This difference has really helped to improve the security of the BTC network and also provide more privacy to such transactions.
WORKING MECHANISM OF P2PKH
The working mechanism of P2PKH starts from the point where the sender and recipient are ready for a transaction.
At that point, a public and a private key is created by the recipient, in which the public key will be shared to the issuer of the transaction.
In the act of encoding the keys, the hash of the public key is created by the recipient and such hash is then sent to the sender as the popularly known BTC wallet address.
Now, after the address has been sent to the sender, the process of transaction creation is ignited, which further leads to the use of BTC script, that is now used to derive a sub-script that will later be contained in the P2PKH.
The generated sub-script, which is also known as the script sig serves as a verification that the issuer is the true owner of the asset he is about to spend. And once the verification is complete, the issuer can then proceed with his transactions.
Let's examine a good example, to better aid our understanding.
Let assume that I want to send tokens to @pelon53 using the P2PKH format.
Pelon53 must initiate the process by sending his wallet address to me, of which, I will input his address, alongside other details into my wallet.
This inputted data will be translated into p2pkh script, of which I will click on the send icon to begin the transaction process.
From the moment I clicked on the send icon, the transaction will be sent to the network, which will then be added to a block by the block miners.
Once it has been added to the block, the individual action of the submitted transaction will then be performed by the network nodes at the end of the block validation.
Then, after this has been done, the nodes will carry out the p2pkh script, transferring the full ownership of the asset to @pelon53.
ADVANTAGES OF P2PKH
The p2pkh is a very secured mechanism that helps to decrease the chance of threats from quantum computers.
The p2pkh is very easy to use and also reduces the chance of making errors when inputting transaction details
DIFFERENCES BETWEEN P2SH AND P2PKH
| P2SH | P2PKH |
|---|---|
| It stands for pay to script hash | It stands for pay to public keys hash |
| It's address always begin with the numerical character "3" | It's address always begin with the numerical character "1". |
| Its payment are usually made to a script hash | It's payments are usually made to a public key hash |
| It is highly compatible with segwit | It is not compatible with segwit |
| Its transaction process involves the use of a low fee | It's transaction processes requires the use of higher fees. |
| It supports multi-signature transaction | it doesn't support multi-signature transaction. |
IT IS REQUIRED TO TRANSFER 10BTC THAT BELONGS TO A 3 OF 5 MULTI-SIGNATURE PORTFOLIO, TO THE MTC COMPANY, FOR THE PURCHASE OF SOME EQUIPMENT.
USE THE SCRIPTSIG AND THE SCRIPTPUBKEY TO EXPLAIN THE STEPS THAT ARE FOLLOWED
IT IS REQUIRED TO TRANSFER 10BTC THAT BELONGS TO A 3 OF 5 MULTI-SIGNATURE PORTFOLIO, TO THE MTC COMPANY, FOR THE PURCHASE OF SOME EQUIPMENT.
USE THE SCRIPTSIG AND THE SCRIPTPUBKEY TO EXPLAIN THE STEPS THAT ARE FOLLOWED
It is of best interest to understand what the scriptpubkey and the scriptsig are before we can use them to explain the transaction process as required.
The scriptsig can be explained to be part of a transaction which contains of the useful scripts and Signatures which is capable of unlocking a UTXO for spending.
To spend an asset using scriptsig, the owner ought to provide answers to the riddle. These produced answers is known as the script.
On the other hand, the scriptpubkey can be referred to a locking script that is kept on the output of a transaction of BTC, and requires a user to meet some certain conditions before he can spend his BTC.
In a nutshell, both the scriptsig and the scriptpubkey are programming languages used for the construction and execution of btc transactions.
Now, for a transfer of 10btc that belongs to a 3 of 5 multi-signature portfolio to be made, 3 addresses out of the 5 possible addresses of an account must be available to verify the transaction before it can be executed, otherwise such transaction will be nullified .
For instance, suppose a trader of five V,W,X,Y &Z wants to make a payment of 10btc to the MTC company, the five traders will need to hold their private keys, then the keys of any three of them will be required to verify the transaction.
The process of carrying out this transaction requires the operation of the two types of scripts; the scriptsig and the scriptpubkey.
- The scriptsig as explained earlier, helps to unlock funds through the operation of OP_CHECKMULTSIG. The OP_CHECKMULTSIG happens to be the hash code of the transaction which helps to ensure and check if the 3 provided signatures corresponds with the private keys used in the transaction.
Once this conditions has been verified by the OP_CHECKMULTSIG, the funds will then be unlocked by the script but if the verification fails, the transaction will be immediately nullified.
- The scriptpubkey comes into play after the verification by the scriptsig.
The scriptpubkey remains locked until the SHA-255 hash that was created by the OP_HASH160 is verified to align and correspond to the scriptsig.
After that, the OP-HASH160 code will be compared to the to the OP_EQUAL code, and if they corresponds, the transaction will be successfully executed and the ownership of the 10btc will be transferred to the company's wallet.
EXPLAIN WHAT HAPPENS IF THE TRANSACTION IS MADE USING SCHNORR SIGNATURE?
EXPLAIN WHAT HAPPENS IF THE TRANSACTION IS MADE USING SCHNORR SIGNATURE?
The development of the use of Schnorr signatures have helped to solve the challenge of late transaction caused by the implementation of multiple signatures.
The use of Schnorr signatures helps to join all Signatures into one signature which will be used to execute a transaction.
If traders V,W,X,Y,Z wants to send a total of 10btc to the MTC company by using schnorr signature, all 5 traders must be present to submit their public keys, these submitted keys will then be merged to a single signature that will be used to execute the transaction.
By so doing, it helps to improve the security of the blockchain by keeping the addresses of the traders anonymous, thus making it difficult o detect whose address was used to validate the transaction.
WHY DO YOU THINK THAT TAPROOT AND SCHNORR FIRMS WILL HELP THE PRIVACY OF THE BTC NETWORK? EXPLAIN
WHY DO YOU THINK THAT TAPROOT AND SCHNORR FIRMS WILL HELP THE PRIVACY OF THE BTC NETWORK? EXPLAIN
The BTC network has recently undergone several enhancement which will help to improve many of it's functionalities.
Among this enhancement is the development of the Taproot technology.
The Taproot enhancement happens to be one of the most important changes that has been implemented to the BTC network ever since segwit changed its block capacity in the year 2017.
The taproot enhancement contains three enhanced proposal, amongst which is the introduction of a new digital signature scheme, known as Schnorr.
Schnorr plays a vital role in helping BTC transactions become more private and more efficient, alongside, enabling users perfom more complex smart contract.
The taproot was introduced to the blockchain on the block number 709632 which happens to be on a Sunday.
Personally, o believe that the taproot and schnorr firms will help the privacy of the BTC network because of the following:
Taproot enhances transaction and multiple signatures together, meaning that the verification of btc network requires digital signature unlike the era before the implementation of taproot, where the verification process is very slow because the public key was validated by each digital signature. Hereby increasing the amount of time spent on transaction verification.
Taproot also allows for the aggregation of signature, this makes the validation of multiple signatures possible and thus help to condense transaction with different inputs into a single one.
Taproot also makes possible the combination of multi-signature and single-signature into a single verification process. And this affects the privacy, because it makes the distinction between the single-sig and the multl-sig very difficult to ascertain. Thus making it difficult to recognize the participants of a btc transaction.
In a nutshell, we can say that taproot helps the privacy of btc network by making it very difficult to identify the participants in a btc public blockchain transaction. This Is done by bringing out multi-sig transaction as a single-sig transaction.
Also the implementation of taproot helps to decrease the cost of transaction and at the same time increase the number of transaction processed.
USING THE BLOCKCHAIN DEMO , WRITE EXACTLY THE FOLLOWING MESSAGES: SCHNORR SIGNATURE, GENERATE THE MESSAGE SIGNATURE AND VERIFY THE MESSAGE.
THEN DELETE THE FIRST CHARACTER FROM THE MESSAGE SIGNATURE AND CHECK AGAIN. WHAT HAPPENED? EXPLAIN. SCREENSHOT REQUIRED
USING THE BLOCKCHAIN DEMO , WRITE EXACTLY THE FOLLOWING MESSAGES: SCHNORR SIGNATURE, GENERATE THE MESSAGE SIGNATURE AND VERIFY THE MESSAGE.
THEN DELETE THE FIRST CHARACTER FROM THE MESSAGE SIGNATURE AND CHECK AGAIN. WHAT HAPPENED? EXPLAIN. SCREENSHOT REQUIRED
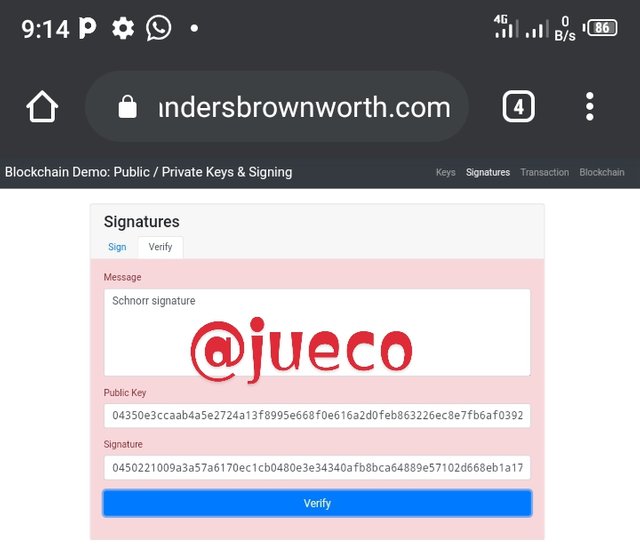
To perform this task, I explored blockchain demo.
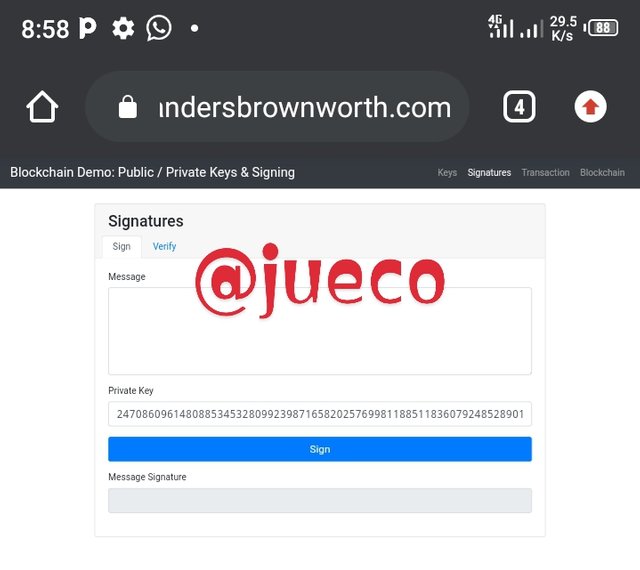
- The first thing I did was to visit the blockchain demo and the below appeared
- Next, I imputed schnorr signature in the empty message Bo's and then clicked on sign in and a message signature was given as seen below
INPUTTED MESSAGE = Schnorr signatures
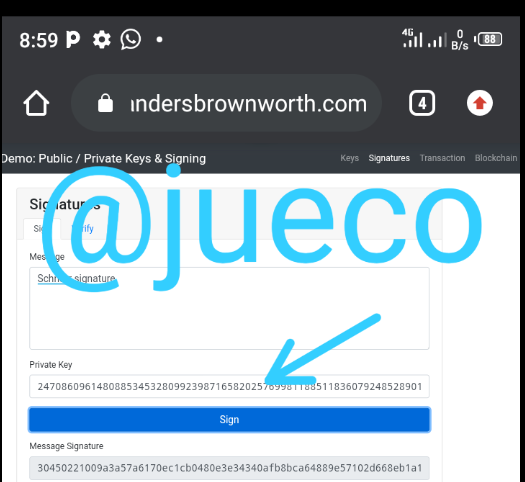
MESSAGE SIGNATURE:
30450221009a3a57a6170ec1cb0480e3e34340afb8bca64889e57102d668eb1a17bdebac5802204e0ae36cf490d11603a2774a4cfcf53bde74da304b0461c0c25820ae8c2ff5e6
- I then proceeded to verify the signature by clicking on the verify icons.
As seen above, when I clicked on the verify icon, the display changed to green which indicates that the signature corresponds to the input message.
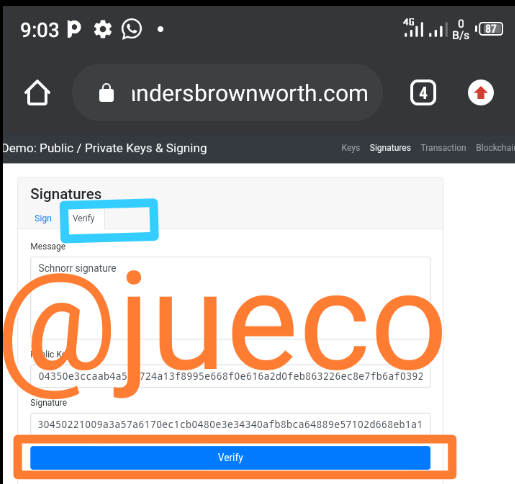
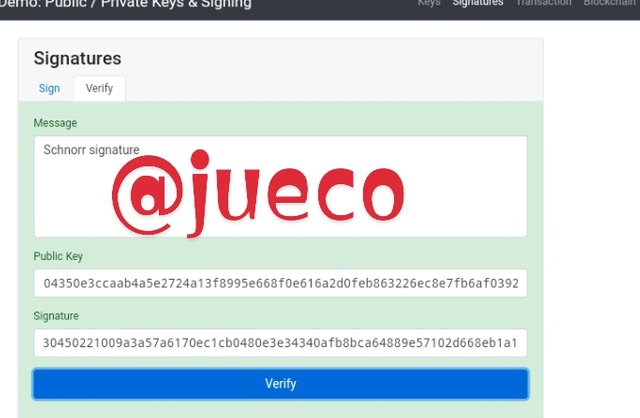
- I then proceeded to remove the first character from the message signature and I then clicked on the verify icon and the below displayed
As seen above, the display changed to a red colour, this signifies that the signature does not corresponds to the imputed message.
CONCLUSIONS
The taproot and schnorr signature is indeed a very good innovative to the BTC network, as it helps to improve it's privacy, it's security and it's scalability.
The taproot also helps to increase transaction verified and at the same time reduce the cost of such transactions.
I sincerely thank Prof @pelon53 for this wonderful assignment, I look forward to your next assignment Prof