
INTRODUCTION: Pleasant greetings to every wonderful people of this community, I welcome each and every one of us to the third week of this contest. it is such a great privilege to be a participant.
Before I proceed, I would like to thank the brains behind this contest as it has been really helping me in a lot of ways. Also, I am commending all the communities for handling their role effectively. Well done!
Today, I am going to be taking us through some blockchain concepts and I can assure you that, you are going to enrich your knowledge having read this post.
Let me give you a hint. I am going to talk about *******. Interesting right? 100% yeah.
So, my advice for you is just to grab a glass of water and sip through as you read because it is going to be a long ride.


From the hint given above, I am sure some of us can guess the term I want to talk about. So, let us get started.
My favorite term is Cryptography. Yeah, you guessed right.
What is Cryptography? Before I go ahead to write on this, I think it will be better if I briefly explain what blockchain is.
Simply put, a blockchain can be defined as a system of recording information in such a way that makes it very difficult to hack, modify or cheat the system. It is a digital ledger of transactions that is distributed as well as duplicated over the entire network of computers (node) on the blockchain.
Technically, it is a distributed ledger technology that records transactions with an immutable cryptographic signature known as hash.
Moreover, we need to know that there are four ways in which a blockchain is being structured and these are given below.
Public blockchains: Permissionless, complete decentralization.
Private blockchains: Permissioned, there is a central authority.
Consortium blockchains: Permisiioned, controlled by a group of organizations and so some decentralization is still enjoyed here.
Hybrid blockchains: These are controlled by a single organization but with some public blockchains features.
So, let me now go back to defining cryptography.
Generally, cryptography can be defined as a way or method of securing data from authorized access. In relation to blockchain, cryptography is a method of securing transactions that take place between two nodes in the blockchain network.
Blockchain technology makes use of two types of security methods for the successful and safe working of the network. The two types are cryptographic techniques (key-encryption) and hashing. Just as explained earlier, the cryptographic protocol does the encryption of messages in a point-to-point network more like an external layer of protection and the hashing protocol is what does the securing of block information more like an internal layer of protection. Hashing also links blocks in a blockchain network.
Here, I will be focusing on cryptography. There are actually two main concepts behind cryptography and these two concepts are Encryption and Decryption.
So, what do these two terms mean? Encryption is the act of hiding or coding information in a way that one cannot know what it means by merely looking at it while Decryption is the direct opposite i.e the act of decoding the already coded information. Do we understand? Yes. Good, let us proceed. The encrypted information is known as ciphertext.
Earlier on, I mentioned key encryption or key cryptography. Key encryption which is one of the cryptography techniques levels is a method of securing point-to-point transactions using a key. This key could be a series of numbers or letters or alphanumeric and it acts as a password.
At the sender node, key-encryption encodes the information that is to be sent to the other nodes in a format that is not unreadable and the receiver node will have to use the same key or a different key depending on whether it is asymmetric or asymmetric cryptography to decode the information and render it in a readable format.
Key cryptography is categorized into two types based on the number of keys used. We have Symmetric cryptography and Asymmetric cryptography which is also known as Public-key cryptography


This type of cryptography was the first key cryptography that blockchain technology make use of. Here, both the receiver and sender nodes make use of the same key to encrypt and decrypt. Let me give us an illustration.
Let us take for instance that Mr. A (Node 1) wants to send a message to Mr. B (Node 2), to encrypt the information, Mr. A will use key1 and the decrypt the information, and Mr. B will use the same key key1 and this means that both Mr. A and Mr. B will have the same key. If Mr. A (Node1) want to send a message to Mr. C (Node 3), they will both have to make use of a new key let us say key2. This is how symmetric cryptography works.
Looking at the illustration given above, we can see that if Mr. A wants to send messages to 30 different nodes, that means Mr. A will have 30 keys in his possession. This is a major setback of this type and this is what brought about the other type of asymmetric cryptography.

The image above is the diagrammatic representation of symmetric cryptography.


In asymmetric cryptography, each node has two keys which are known as private key and public key. These keys exist in pairs. The public key is used to encrypt the message and it is known or visible to other nodes while the private key is used to decrypt the message and is not known by any other node. let me also give us an illustration. of how this works also
Suppose Mr. A wants to send a message to Mr. B, Mr. A will encrypt the message using Mr. B's public key and Mr. A will also sign the encrypted message with his private key, and this is what we call a digital signature (signing of transactions digitally).
Having done this, all the computer networks on the blockchain will have to verify Mr. A's signature and then send the message to Mr. B after successful verification. Mr. B will also verify the digital signature of Mr. A by making use of Mr. A's public key too.
The last thing to do is for Mr. B to decrypt the message using his private key and after all, this is done, the message will be recorded on a new block in the blockchain permanently and so, nobody will be able to alter it or deny the transaction.
This is basically how asymmetric or public-key cryptography works.
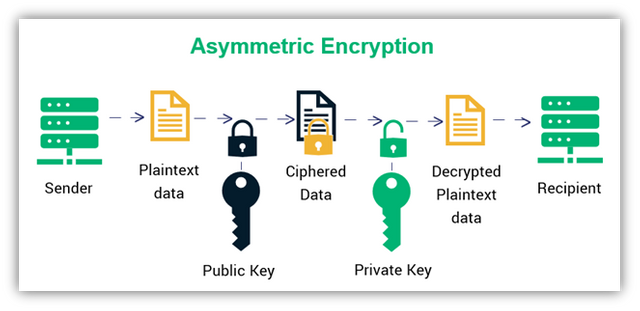
The image above is the diagrammatic representation of asymmetric cryptography.


Don't forget the other level of cryptography is the Cryptographic hashing which is also very important in securing a blockchain as mentioned earlier. Cryptographic hashing is also an act of coding information into an unreadable or unhackable text.
It is a one-way mathematical function that maps an input to an output. Bitcoin as a study case makes use of a hashing algorithm SHA-256 to create a 32-byte long hash value that cannot be mapped back to the original input.
Irrespective of the input, the hash value is of the same length and it differs for every change in the input this also means that hashing compresses information no matter how long it is. Also, once information goes through the cryptographic hash function, it cannot be undone.
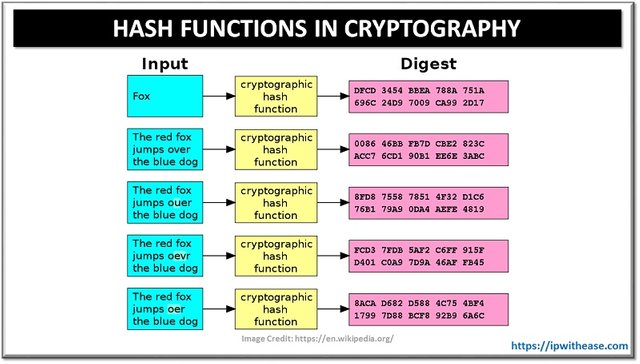
The image above is the diagrammatic representation of cryptographic hashing and we can see that despite the input length, the output is different and of different length.


Do not forget that we defined blockchain as a digital ledger that stores every transaction that is made on the blockchain. We can see how large or numerous the information will be and this is where cryptographic hashing comes in.
Cryptography is a very important term in the blockchain and it is even among the three main pillars of blockchain technology with the other two beings Distributed ledger and Peer-to-peer network. The following are some of the reasons why this term is important to the blockchain.
Security: Cryptography is what secures the blockchain ledger. We can see how important that is right? Each user is able to buy and sell their cryptocurrencies securely by using their private and public key
Scalability: It is cryptographic hashing that allows the recording of unlimited transactions on the blockchain.
Reliability: I said earlier that Cryptographic hashing is irreversible and so, nobody can undo or modify transactions once it has been hashed. This process makes the blockchain safe from any form of threat and this is also what makes users rely on the accuracy of the ledger.
It provides confidentiality and Immutability.


NO.
Blockchain technology builds on cryptography technology as it is what provides rooms or tools to encrypt, decrypt, transfer cryptocurrencies securely, record transactions unlimitedly, add blocks without limit, and so on.
Also, blockchain is the technology behind cryptocurrencies and we need to know that without cryptography (security and recording power to be precise), cryptocurrencies would have no real value and this is because anybody can create any amount of money they want.


Yes, I believe cryptography can be improved on though it is still working pretty fine now.
One aspect I believe this can be improved on is to provide a way to access one's fund even whenever one loses his or her private key. Just as we all know right now that losing one's private key means losing one's fund. I am sure improving on this will as well aid the adoption of blockchain globally together with some other benefits.
Also, encrypting and decrypting of data is limited to a certain size data and this means that if a large number of data is to be encrypted or decrypted, the algorithm will run slowly and consequently demands or consumes higher computational power. So, there is a need for an improvement too.
Even though cryptography is very essential for security, we must know that cryptography is not directly equal to security unless it improves on key leakage, software bugs, side-channel attacks, as well as phishing attacks.

CONCLUSION
Cryptography is one term that cannot be done away with whenever we are talking about blockchain and this is why it is important to know about it. Cryptography in cryptocurrencies does three things, securing transactions, controlling the creation of additional units, and also, verification of the transfer of assets.
Thanks for reading up and I would appreciate it if you can drop a nice comment and an upvote.
I am inviting @ojerindejoel @bolaji001 @olawole111 to participate in the contest.
GRACIAS
You made a good choice by speaking on cryptography. It is among the pillars of a blockchain that helps in security. Good luck friend.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thank you for reading and I believe you enjoy the post.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Before, I used to find it difficult to understand description and encryption even cryptography. But with researches and learning, they are now at my finger tips and this your post has helped me more. Thanks a lot for being detailed. Steemit is becoming more interesting with contests like this. Success in your entry
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
I am happy that you got to understand some new things from the post. Thank you.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Hello @kennydavebobo,
Your article is well detailed and I am sure you did a lot of research for this work.Thats very impressive.
I have learnt a lot from your work on Cryptography.Encryption and decryption ensures that only the authorised node can access the information from the sender.This is a high level of security.
Goodluck in the contest!!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Yeah, it hasn't been ling that I started out with blockchain technology so I had to do some research in order to be explanatory enough.
Thanks for reading through and the review.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Hi @kennydavebobo,
Alright I am sure that you will learn more about cryptocurrency in the course of your stay on Steemit.Keep up the good work.
Regards!!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thank you.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Wow! You have explained cryptography very well and I have learned a lot from your post. I also like the way you structured the post. Well done.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thank you friend for the compliment and yeah, cryptography is very important.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Wooow I love your article because you have chosen a very nice Blockchain terminology which is cryptography and I Know how this cryptography is important to the Blockchain because it is the method of securing information and communication through codes known as encryption so that only the reciever can be able to receive and read the information
You have done a great job in explaining it and I salute you for that. Good luck in this contest
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Without cryptography, there won't be cryptocurrency which is the major use of blockchain technology.
I am happy thay you enjoyed the post. Thanks so much friend.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit