INTRODUCTION
Hello good people it's another day to blog again here I attend the lectures of professor @stream4u, here we shall be opening a blockchain, I have gone through your lecture and trust me I have understood alot, thank you very much professor.
Explain the Blockchain CryptoGraphy and mention few names which are the Blockchain Platforms (Few names of the Blockchain Platforms)
Before we go into blockchain cryptography it will be nice we have an overview on what blockchain itself means in real sense, blockchain is a ledger that records transactions and this records are done through the help of blocks, these blocks are married to each other using cryptography, each of the blocks contains what is called a cryptographic hash, courtesy the previous block, from my explanations you will understand that a block-chain can't exist without blocks.
Cryptography can be defined as a process of developing codes that will prevent third party from gaining access to seen your private data, here your data is been fully protected simply because it is coded, the coding can only be interpreted by the person who intend to receive the data.
Informations in there is programmed in such a way that third party will find it very difficult to steal your data that means the informations is encoded, everyone wants an assurance that their information are intact, to avoid a sorry state or hackers. So many organization has their own standards as far as security is concerned. Let me show you an image so you could understand what I'm vividly talking about
I repeat cryptography is very important, it's component is very important to block-chain technology, blockchain due to it's rigidity it makes use of what we call asymmetric cryptography, byou can also call it public-key cryptography, here cryptography is used in different facets we have the wallets, security, and the last one transaction, all this measures is for keeping your data safe and transactions been carried out in the blockchain secured to avoid hackers to gain access.
The roles Cryptography plays is very much important to a blockchain, it gives investors trust, and hope thus intermediaries are been eradicated, we should also understand that public key cryptography makes use of keys in double phases which are the private and public keys, the public keys no problems can be shared with third party, but the private keys remains private just as the name implies, it's not supposed to be given out, public key cryptography is basically controlled between two persons or servers in such a way that it's basically secured.
In blockchain technology it makes use of the one called asymmetric cryptography, this Cryptography helps in authenticating various user's and validate their data's through what we call digital signature.
SOME IMPORTANT TERMS USED IN CRYPTOGRAPHY
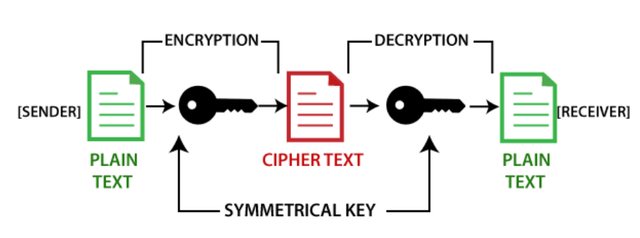
Encryption; this can be defined as the process by which data can be converted into a pool of different alphabetical order, which rearranges it making it to look worthless, but still serves it's aim and objective to the recipient, it's a process by which a well seen text can be encoded changes its original appearance thus ciphertext will be added, at the stage when the encryption is been done the informations here will be seen as plaintext, along the process the data that is been converted will then been seen as ciphertext, let's take for example we have
"HELLO" > Sgiftv+Uzojr+..
From the illustration the hello will be seen as plain-text, while the Sgiftv+Uzojr+.. will be seen as ciphertext, the greather than sign is representing encryption.
Decryption; this seems to be the opposite of encryption, it can be defined as a means by which encrypted data is been converted to real data that means it's original form. It's just the reverse process about what I have discribed earlier, the person who wants to receive that is the receipt in quote can decrypt the data yes it's very possible.
but he has to make use of private keys, now let's say the keys aren't available then there is an option, here programmed software will be needed here in order to decrypt the code, and allogrithm will be needed so that the data can be interpreted and readed, as well, let's see the example below it's just opposite of what I did earlier.
Sgiftv+Uzojr+ > "HELLO"
Explaining what is here the Sgiftv+Uzojr+ will be seen as the ciphertext, while the "HELLO", Will be seen as the plain-text, so it's just in opposite direction, while the greather than sign acts as an encryption.
Cipher; this is basically an allogrithm that carried data, along the process the production of a fixed output called the ciphertext is officially been galvanized, it will intrest is if we know that a ciphertext, just as I have explained is an encrypted facet of plaintext, it's operations are well galvanized together for encryption and decryption to take place.
Keys; for people who are on this platform should be very conversant with how keys works in a Decentralized platform's, or blockchain, no doubt Cryptography needs keys for encryption and decryption to take center stage, keys gives room for changes to happen like the changing of plaintext to ciphertext, with keys you can easily lock, and as well as unlock data's when due, hence keys differs from password.
Digital signature; we know what a signature is, but in this case it can be defined as a vital strategy that is used to create out digital codes, that can be used initiate coded messages and documents too as well, this codes are produced with the use of private-keys encryption.
SOME FEW BLOCKCHAIN PLATFORMS
We have some key blockchain's which is available in the global seen today and some of then includes, the Etherium blockchain, the EOSIO blockchain, the stellar blockchain, the binance smart chain, we have the EOS blockchain, etc.
Explain the Public Key CryptoGraphy
A public key cryptography can at the Same time be called asymmetric cryptography, it's a means by which messages are been exchanged, thus it can be readable between those that Exchanged it that is the both parties. In here the both parties involved any-person can encrypt the message making use of public key, from the both parties again the person who holds the private key can be able to decrypt, as you can see the private key is very important and needs to be kept safe.
We are still talking about public key cryptography, in here each of the user has a pair that consists of the cryptographic keys, which can either be the public, or the private keys, in both the private-key is the most important and it's been kept in a secret place, the public key can be shared theref other person's can make use of it.
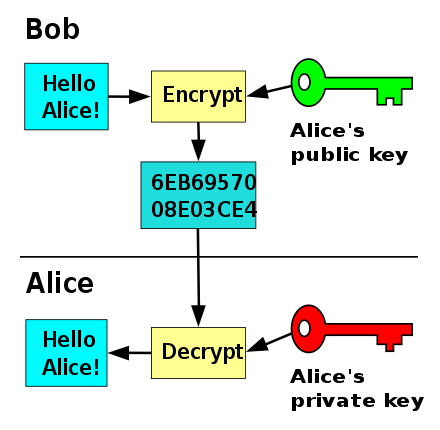
Message coming in can be encrypted making use of the recipient public keys, in this case it can only be decrypted with the use of private-key's, the both keys have the same structure, there will be some infringements when unfortunately private keys are been leaked, public keys has two important branches and they include.
Public key encryption; previously I have talked about encryption so you have an overview of what I will be explaining here, now if a particular message is been encrypted using a recipient public key, that message trust me can't be decrypted, unless you make use of the receipt private key. Here your privacy is pretty guaranteed.
Digital signature; I have explained this before but here I will throw more light, if I'm a sender and I signed my message using a private key the message can be verified by every person provided that you have the senders public key, this is very important here to note this, if me the sender signs the message trust me even juju can't alter it, authenticity is key here.
Explain the Private Key CryptoGraphy
Private key cryptography can be defined as a cryptographic systems that is centralized on encryption, the interesting aspect of this is that the key doesn't change, I mean the same key can be encrypted and decrypted, private key encryption in most ocassion's called symmetrical encryption,
Private key encryption makes use of small keys, this makes it very eazy to be computed with, by so doing there will be adequate systematic computer hardness, the scale is very much important Private key encryption is key because it's personal and it shouldn't be shared within you and the third-party. Your private key is basically used to keep tokens in your wallet safe and secured, that's why it shouldn't be shared.
Your private key makes an investor the governor of he/her assets, transactions in there will be signed after which it will then be distributed to the network, when your private key is generated it does so at the expense of wallet creation, after which you can decide to store it in a safe and secure place.
Highlights of private key cryptography
Private key all round is been centralized on encryption, if you have gotten your private key and you want it safe, before new one will be generated you need provide the previousl existing one.
Every investors needs a private key, just as the name appears private, you don't need to share it with anyone all you need do is to keep it safe so that your token been stored in your wallet won't be made away.
Explain the Digital Signatures CryptoGraphy and what is Singing Of Transaction/Message?
Signing a digital signature in a digital transaction it is seen as an interchange or an exchange of an encrypted message that just plaintext used in order to achieve confidentiality. Let's say in a public encryption scheme a sender is available in a public space by so doing any person can identify he/her identity thus the messag will be sent to the receiver.
At this process it's very impor we employ the PKC, for the supposed encryption so that digital signature can be seeked toward the already encrypted data so that messages been sent will then be authenticated by the process it will be non-repudiated. Achieving this all digital signatures needs to be combined with the encryption scheme, now we have the sign-then-encryption and the encrypt-then-sign.
In the crypto space the sign-then-encrypt, can be implemented in here the receiver will then have to proof the identity prior to the person who sent the message and the data to third party, this process seems somehow and various people doesn't prefer it, now let's look into another process this one is the encrypt-then-send, this process is commonly used all round I will show a table so that you can view and understand much more better.
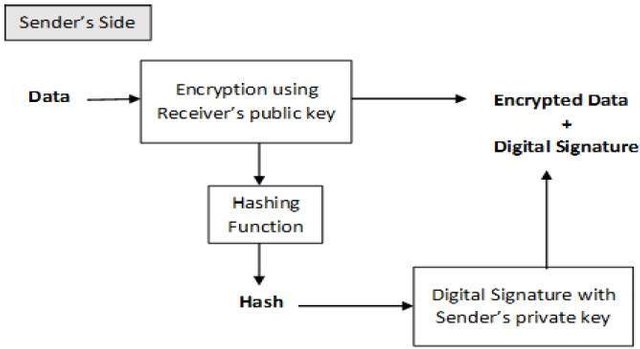
From the image uploaded you will understand that the receiver after he has received the already encrypted data this you will see a signature of it, he firstly verified the signature, this was done using the senders own verified public key. After the signature have been verified and validated he officially retrieves the data courtesy decryption making use of the private key.
Explain what is Symmetric and Asymmetric cryptography
Symmetric christography which can also be called symmetric encryption, it makes use of a particular key, this key can be used to perform two functions they are encryption and decryption, what I just explained here is the inverse of the one we call asymmetric cryptography/encryption, it makes use of a particular key to encrypt, and another key to decrypt, so it's just more like the opposite, in here data is been changed to a format, here you will find it very difficult to translate it.
Symmetric cryptography is been centralized on a particular key, and the parties involved all round knows about it, once again the key can be used to encrypt and at the same time decrypt data. The strength of the regular number that is used to create out new key all insinuates the viscosity of the method, the keys that internet uses today is known as symmetric cryptography, it has so many allogrithm conjugated together that is the blocks, and the stream,
PURPOSE OF SYMMETRIC CRYPTOGRAPHY
Total Effectiveness; this type of Cryptography is very much effective than the asymmetric encryption reason been that courtesy data size asymmetric cryptography finds a way to strain network and how it performs.
Used for heavy encryption; so many burgos encryption because of the fact that it is pretty fast and effective, it encrypts humongous volumes of data, let me give an example, a data on a very large database, note the secret key can only be deployed by the database in order to encrypt data.
Speedy payment; we have so many payment applications around today in our various banking institution's bank purchases are been done too in order to secure key personal identification to avoid hackers or any other form of fraudlent act you need employ the services of symmetric cryptography. By so doing your transactions will be safe and secured.
ASYMMETRIC CRYPTOGRAPHY
Asymmetric cryptography can also be called public key cryptography, this assists in the encryption, and decryption of messages with the help of an identical keys, note this identical key. Here the private key that is not meant to be shared is been kept by a solitary private-key, and a public-key, all this is to prevent anyhow entry of un-recognized key to avoid fraudlent act.
Private key can be used by any person in order to encrypt a particular document, reason been that the receiver can then be able to decrypt by the aid of private key, the generator of the key knows about the key no other person else.
Now let's say I want to submit a message that is encrypt a shared directory will thus be used in order for the recipient public keys to be restored/retrieved, the already sent message will then be decrypted by the receiver with the help of the private-key.
The most interesting aspect of this type of Cryptography is that it all round improves the security of data, you know private keys can't be shared the ability of fraudlent acts is totally minimized.
PURPOSE OF ASYMMETRIC CRYPTOGRAPHY
Serves as an overview for Cryptos; asymmetric cryptography is been used by Cryptos when their public keys are been provided in the public space, cryptocurrencies like Bitcoin and all the rest deploys a cryptographic allogrithm that makes sure that the problem of double spending is limited.
Provision of encryption connectivity; asymmetric cryptography is mostly been used in the SSL/TSL, in the cryptographic space by so doing encrypted connections are automatically been produced within websites, by so doing your Operation in there will be totally secured.
Message Decoding intensivity; asymmetric cryptographic can be applied when many users encrypts and decodes their messages in this case messages you sent attains a public keys, in order for a file to be encrypted a private key helps in decoding messages been sent.
How Blockchain Wallets CryptoGraphy works and explains the available types of Crypto Wallets
Blockchain wallet cryptography can be said to be a digital wallet that gives various user's the opportunity to store, and thus manage their cryptos assets, blockchain wallets are wallets that is been galvanized by blockchain itself, we have so many known blockchain around today, for example we have the Bitcoin blockchain, the Etherium blockchain, the EOS blockchain, etc these blockchain's have wallets that are been provided by then.
Block wallet works in a dramatic fashion, it allows user's to make a quick convert, you can easily transfer your crypto token and you can at the Same time converts then back to local currency. Understanding blockchain wallet cryptography well, let's give an example here the E-wallet, it gives investors the opportunity to store their various Cryptos also other digital assets.
CRYPTO WALLET PRIVATE KEY
Crypto wallet private key is very important in the sense that it is used to sign a digital signature to a particular network, and it shoudn be given to any third party. On like our banking sector where you need a password, name and codes to secure your tokens, but in here you need a private key to carry out those operations, this I how the private keys looks like
EOJF335GDRJM435HIK547447HDSEF853HVXDJJ466HGJHB
CRYPTO WALLET PUBLIC KEY
It is used to validating transactions that are been signed by private keys, this particular address can be shared, but my private wallet key can't be shared because of my security if it's been showned to the third party then my tokens are at risk, for any to compromise my token then the fell need have my private key, although both keys looks familiar with the combinations of numbers and alphabets. For example
5KREEMiUD7cy6NAN1EySCvn9fko5Ph2vkg9WdwJ2Wrg1J6KVmHo
TYPES OF CRYPTO WALLET
Before you think of buying and investing on cryptocurrencies you need to structure the type of wallet you will use in order to store your tokens, we makes use of digital wallet in storing Cryptos like BTC,LTC, we also have the hot and cold wallets let's explore then now.
HOT WALLET
Hot wallet for me it's really hot because you can easily connect it to the internet Courtesy this you might have infringements because connecting it to the internet risks the velocity of the wallet as it will thus become less secured and it will become a free way accessible, the accessibility rate will totally increase, fraud-stars can easily strike because at that time where it is connected it becomes very vonurable, hot wallet in general people makes use of it often and it's very risky and it can be hacked easily by fraudster's.
COLD WALLET
This wallet encourages a rigid storage, just as the name implies cold wallet, one interesting aspect of it is that crypto tokens can be stored in an offline mode by so doing trust me the security is really rigid, comparing it to the hot wallet.
I will advice you go for cold wallet as it seems very improved safe and secured than other forms of cryptocurrency wallets around, you can easily carry out your daily transactions safely and secured without any fear of a fraudster's or fraudlen activities,
What is the Merkle trees and What its importance in blockchain
A Merkle tree can be defined as a structure in form of a bridge that is used for the application of certain computer functionalities, it's functionalities includes Making cryptocurrencies to be upti-mostly secured as a result of the facets they find themselves it's data a pretty encoded in the blockchain, it can also be called a binary hash tree.
Merkle tree is very important in a block-chain, let's take Bitcoin blockchain for example in a blockchain a block is very much important because transac runs on it, through various allogrithms simply to generate hash. It can then be used to for data verification in a given data as a result of the transac been carried out.
Bitcoin blockchain has a software and a hardware too, Bitcoin softwares doesn't run the whole block of the transaction and it's data some designated minutes here like 10 mins on average. The hash functions plays it own vital role here since Bitcoin block software doesn't run the blocks alone transactions are been hashed then all the transactions are galvanized and by so doing hashed in unism.
Let's say has was performed on the whole blocks, if there is any discovery of an odd number in a particular transaction, then the transaction will appear twice/double by so doing the hash will be concatenated.
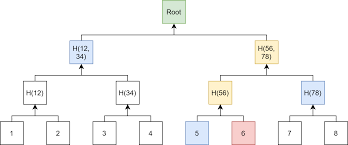
From the image uploaded, you will understand the clear definition of a Merkle tree, it's a structure that gives a clear view on how transactions are been represented, let's say I want to give an overview to preye, that transaction Q happened, it's very simple, what I need do is to present it on a Merkle tree. Doing this I will the provide.
The transaction already carried out it will give me an overview on how it will be represented on the Merkle tree, thereby hash can easily be created.
All missing hashes will be made readily available so that it will give a boost to calculating the root hash.
By so doing I myself will have to verify that the Merkle tree is equivalent with the root hash of that of preye, him on his own needs to hash the transaction himself and galvanize it in the Merkle tree, it will then be represented there.
We know that cryptography hash functions plays a great role as it makes very difficult to find a prolific hash function in order to shape up an image, in here resistance and collision comes to fruition as I won't be able to know which root is been used because I don't have the overall data all together.
Practical + Theory, do some practical research, study on Blockchain Demo: Public / Private Keys & Signing and then explain the functionality of Key, Signature, Transaction, Blockchain with proper screenshots of yours practical. (Do study well for this topic)
We have learnt alot from the lectures above just as the question demands I will explain the various functionalities of keys, signature, transactions, let's get the ball rolling.
KEYS
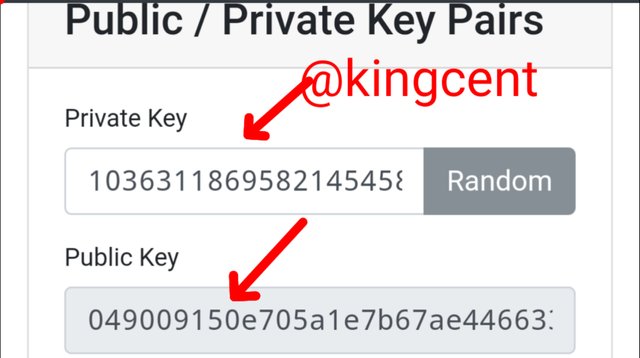
Keys are very much important keys are very much different to password, as it is alphanumeric, in a wallet we have the private-key, and the public keys too as well, although they looks alike but have various functionalities, the most important among the two is the private key, in no ocassion it must not been shared in order to keep your token safe and secured. Just as I said the keys looks identical on the the keys on the Anders brownworth demo I gained access to the webpage and I exploited it this was the output.
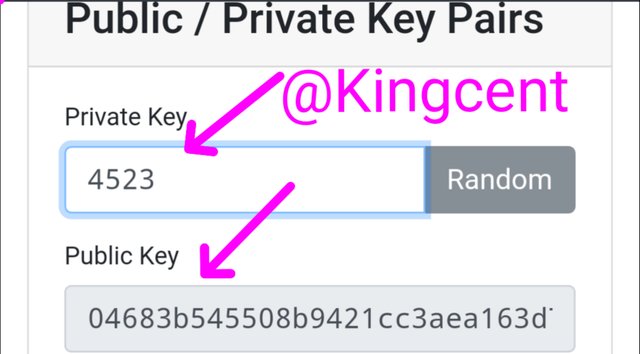
From the image uploaded you can see the private and public keys, now i tried exploring then what I did was to Change the private key, I added a figure 4523, the public key it gave to me was of the same length as to the private key I earlier altered. This is as a result of the asymmetric encryption allogrithm, the keys are very much unique.
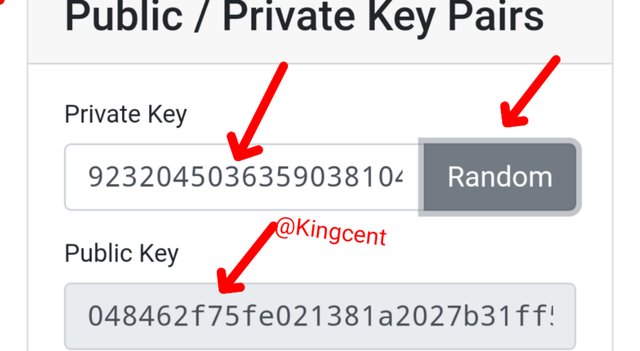
Since the private and public keys are very much unique I thought of what could happen if I eventually clicks on Random, when I did I understood that new private key and public key was introduced, as you keep on clicking on Random they keep changing.
The public key
they are automatically linked to each other and their length are pretty much the same in length
Signature
Signing signature Has to do with the help of a private key, you sign and validate digital signature with the help of a private key, public keys are also very much important because miners needs it to validate transactions and to add your signature to a blockchain.
Let's explore again, to see how the signing will happen, remem by private key is 4523,
At the message body I typed I love Jesus, I will demostrate below so that we can get a clear overview on how everything will officially pounds out
I will try adding my private key, including my message added to the message body then I click on verify people let's see how everything will go.
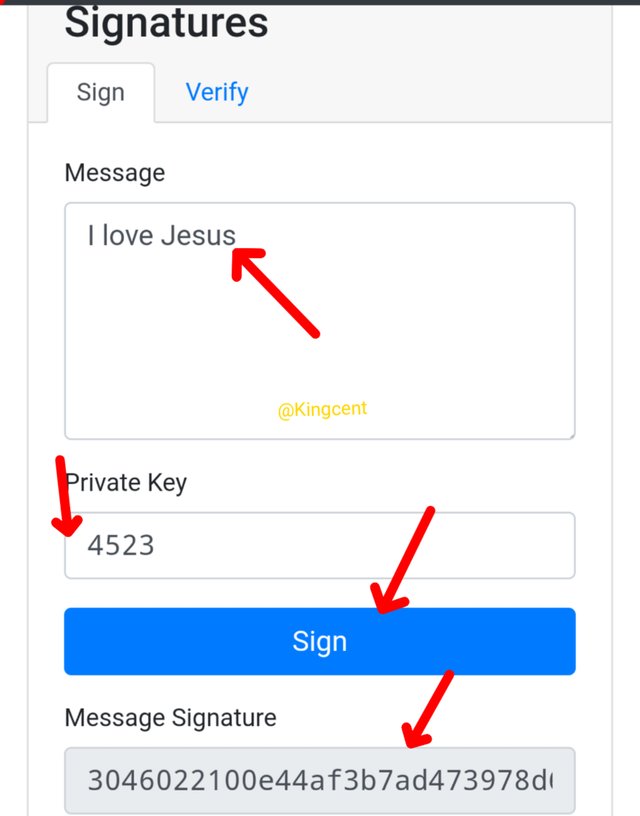
Officially I signed the signature using my private key, and below was my message signature
3046022100e44af3b7ad473978d69188fa4481125791e444b7718a762dfe0449101dce2c07022100916f64ac08ec72db1d1cf8e757573c58f4624600245ddabe190b01adad289df
- Next phase i will try to verify transactions that will be added to a blockchain, here I will acts as a miners, watch and see how this unfolds.
- I have a public key as I earlier generated which is 4523, is already with the miners, what I need do is to verify the transaction and then proceed.
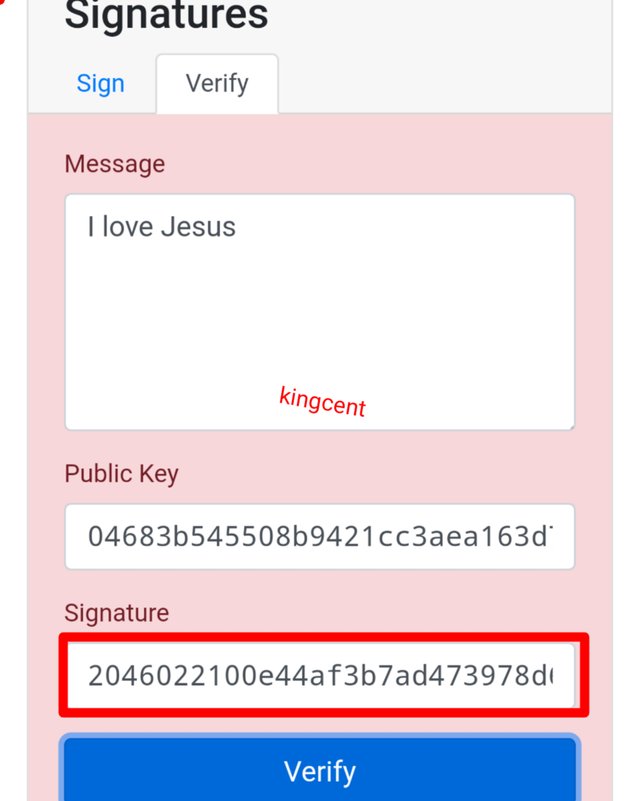
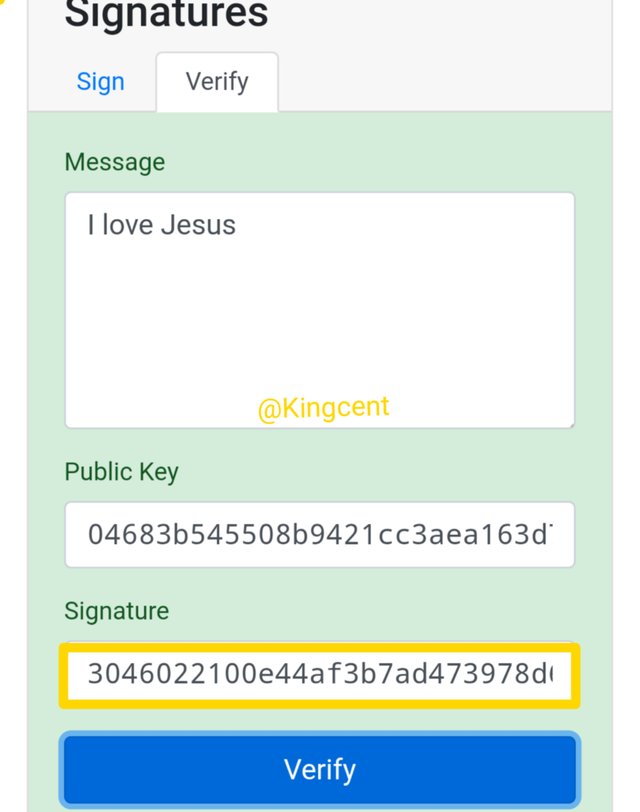
- From the two images uploaded I validated a transaction that was added to a block-chain, then the second one showed red because I changed some alphabets from the signature, so everything changed. The block I mined wasn't valid.
TRANSACTION
For you ta carry out transactions on blockchain you need sign in using your private key, and you will be verified courtesy your public key. I will explore what I have just explained here.
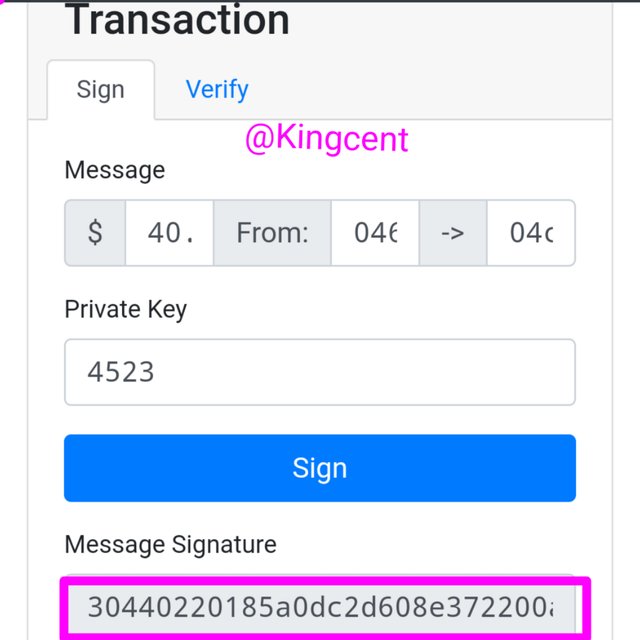
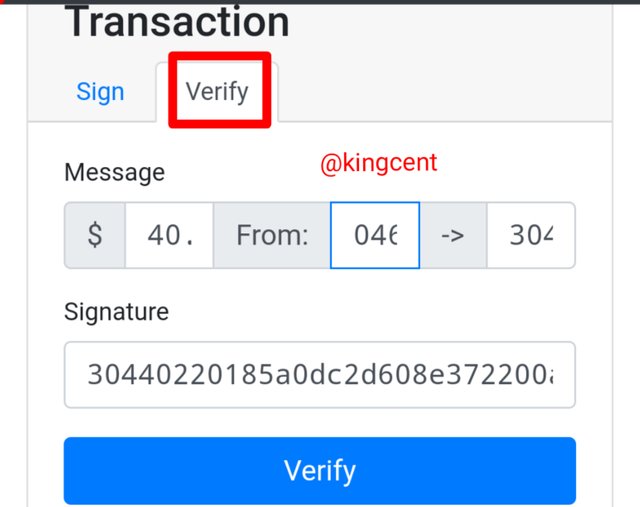
From the image uploaded I signed a signature by imputing the amount I want to send $40, and I included my private key, I clicked on sigh and I got my digital signature, here it is below
30440220185a0dc2d608e372200a97d118cecfdacd25223d5c8db395d902509cee812b60022044f655700015ff2491b9cb96af2a923c3ebf68dcf0d54544e94994cdb27126b8
What I want to do now is to verify the transaction so that it can be added in the block, the transaction needs to be verified.
What I did was to switch over to the verify section, watch and see me finish up the transaction below
BLOCKCHAIN
In blockchain blocks are very important, in here we will have an overview how transactions are been stored here and also how valid hashes are been stored too. Below is the symbol and how it looks like. I will look forward to generating valid blocks that will be added into the blockchain this valid blocks.
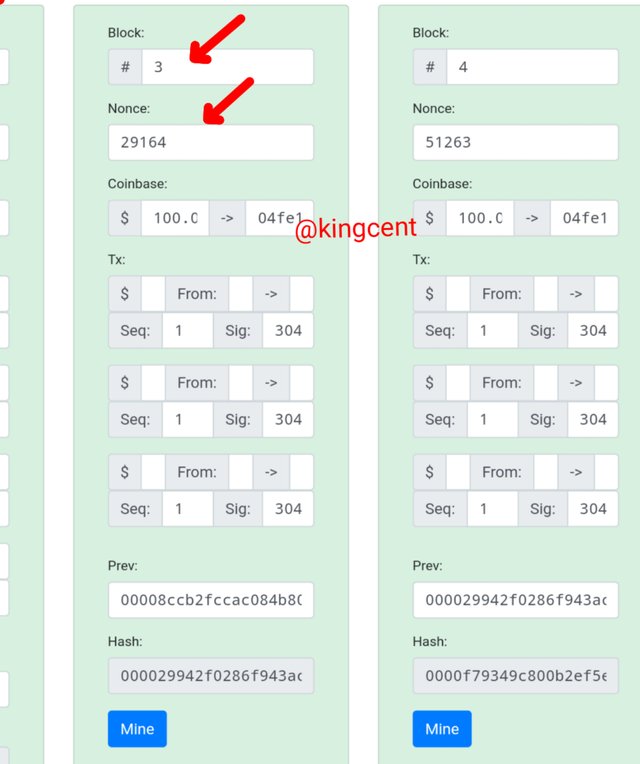
This transaction was very much valid because the hash functions starts with Zero, from the beginning
I tried changing the figure so I could mine another block, but it was invalid because it wasn't the original private key and the transaction hasn't been registered.
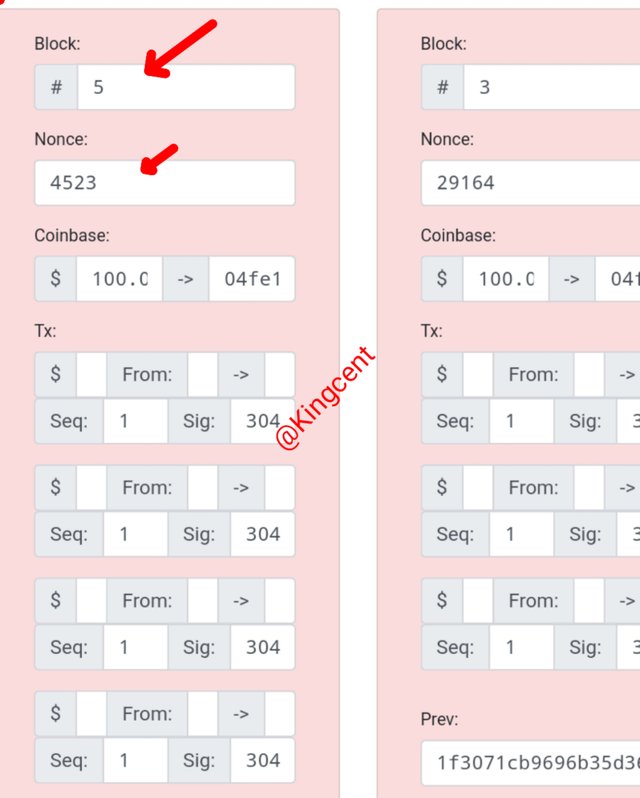
CONCLUSION
From my homework post you will understand that Cryptography is a system that allows the usage of mathematical show down to storing in the same facet transmitting data's in a specific form so that a particular people can access it, so cryptography is very key as it provides total security.
Cryptography isn't a new innovation it has come to lime light for a very long time till now and it uses encryption, it's very important we know all this, encryption makes messages difficult to be read for a person whom the message isn't directed to by so doing the message can only be accessed by the sender, and the receiver alone.
Currently we have three various types of encry that is very much common today, they are the symmetric cryptography, asymmetric cryptographic, and the hashing. Cryptography and it's encryption gives various investors Hope, they believe that their tokens are been kept safe and secured, if you have a wallet.
it comes with a key, private and public key, Private key just as the name implies is PRIVATE, why public keys can be shared, so if you play safe trust me you won't loose your token.
Thank you very much stream4u you really write well, thank you very much for this great lecture, I really learnt alot