Introduction
A Merkle Tree allows computers on a network to verify individual records without having to review and compare versions of the whole database.
They do so by using cryptography that reveals a private record while also guaranteeing that each one of the opposite records within the database hasn’t been changed.
First patented in 1979 by Ralph Markle. Markle Trees are an important key to database verification throughout the history of computers.
Because of the distributed nature of the blockchain, we’d like to secure and fast thanks to confirming everyone on the network has an equivalent ledger.
It allows you to prove that two versions of a ledger are according to minimal computing power and network bandwidth.
Over view
At the top of a hash tree, there’s a top hash (or root hash or master hash).
Before downloading a file on a p2p network, in most cases, the highest hash is acquired from a trusted source, as for example a lover or an internet site that’s known to possess good recommendations of files to download.
When the highest hash is out there, the hash tree is often received from any non-trusted source, like all peers within the p2p network.
Then, the received hash tree is checked against the trusted top hash, and if the hash tree is broken or fake, another hash tree from another source is going to be tried until the program finds one that matches the highest hash
How does it work?
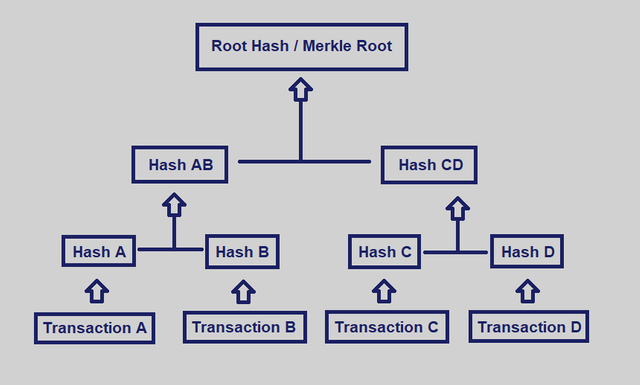
Transactions A,B,C,D.
Hashed H(A),H(B),H(C).H(D)
A Merkle Tree solves the problem of an excessive amount of data by pairing transactions up to and hashing them together.
H(A)+H(B) = H(AB) and
H(C)+H(D) = H(CD)
H(AB)+H(CD)=H(ABCD)
Each Bitcoin block has the Merkle root contains within the block header.
To verify block content and consistency of multiple ledgers. One needs to compare the Merkle Tree of both the block.
Even a small inconsistency would cause vastly different Merkle roots due to the properties of a hash.
Cryptographic Hash Functions
Before we bandy Merkle trees, we need to get a better understanding of the cryptographic hash function.
A hash function is responsible for mapping any form of arbitrary data of any length to a fixed-sized affair. It’s a cryptographic function and hence is extensively used in cryptography.
The hash functions are effective and are known for their one property, i.e., the function can not be reversed. It’s a one-way function that’s designed to work this way only.
Hashing has multiple uses including
Word protection
Train integrity checks and verification
Cryptocurrency
There are many hash families out there including Message Direct (MD), Secure Hash Function (SHF), and RIPE Message Direct (RIPEMD).
Still, we will get the ensuing affair
, If we use a SHA256 hash algorithm and pass 101Blockchains as input.fbffd63a60374a31aa9811cbc80b577e23925a5874e86a17f712bab874f33ac9
To add it up, the crucial parcels of hash functions include
.Deterministic
Pre-Image Resistant
Computationally Effective
Can not be Reversed Engineered
Collision Resistant
Uses
Hash trees are often wont to verify any quiet data stored, handled, and transferred in and between computers.
These are utilized in hash-based cryptography.
Hash trees also are utilized in the IPFS, Btrfsand ZFS file systems.
For more details visit:https://www.technologiesinindustry4.com/2020/09/merkle-tree-efficient-verification.html