.jpeg)
- Explain the Blockchain CryptoGraphy
and mention few names which are the Blockchain Platforms (Few names of the Blockchain Platforms)?
In our last lecture our professor explained a blockchain to us, let me refresh our memory on what a blockchain is, we said that a blockchain is a block that contains information or data which is connected to next block which is also connected to another block in that order.
Cryptography is a security technology, which is used encrypt a data or information so that people without the decryption key can not read or access the information. This way the information you send is always safe.
Now that we have got the understanding of both the blockchain and the cryptography, I will be explaining what a blockchain cryptography is.
Blockchain cryptography is a privacy technology that is employed on the blockchain such that when I am sending a piece of information to you, the information that gets to you can not be accessed by anyone unless we authorize it. This helps keep the information in the blockchain very safe and secure.
Let’s say for an instance I want to send a love letter to girl and I don’t want her friends to read because it’s going to be embarrassing, what I will do is to encrypt the data (encryption simply means changing the data into codes which is not readable by humans) I then will send the encrypted data to her along with the decryption key ( The key used to change the codes back to readable language) with the help of the key she can decrypt the message and read.
When people without the without the decryption key see the data they can’t read it because it will be written in codes this way your message is safely delivered to the specific target.
What is Blockchain Cryptography?
Blockchain Cryptography means that everything that is placed on blockchain is completely secure. It is impossible to make changes in blockchain after the
- Explain the Public Key CryptoGraphy.
Public key is a part of the asymmetric key algorithm of cryptography. Public key is published such that it can be seen by everyone in the world. It is a public shared key made up of alphanumeric codes which are hashed and produce address for different crypto wallets deposits. The main algorithm used for generating publc key are :
Rivest-shamir-adleman
Elliptic curve crytography
Digital signature algo
Public key is string of alphabets and number, used to encrypt the plain message into coded form known as cipher. Public key has a unique private key which is used to decrypt the message which is encoded by public key.
Public key is a verification tools for digital signature done by user using private key. This verification is done before adding a new block.
Application of public key
Used to secure web server
For digital signs
For identity authentications
3.Explain What is Private Key CryptoGraphy?
Private key is a secret key that has overall control of our wallet. Private key indicates the ownership of wallet. When we make wallet, both keys are generated. We only can access to our wallet, if we have a private key.
Private key is used to transfer and withdrawal our funds from our wallet to other wallets. Private key is consisting of long string which has capital letter and small letter of alphabets and also consists of numeric values. Private key string is too long, this is because no one can hack private key. It is difficult to understand by the human because it is in form of machine code.
If a person (A)wants to send few amounts to person (B). Then, person A first send the public key to the person B. While amount sending process the digital signature is attached with this process. This digital signature helps person B to verify and understand sender using the public key that is sending by person A before the transaction.
Cryptography
Cryptography is a sub-branch of the science of cryptography, which we know as cryptography, so it is sometimes referred to as "Ciphering". When we get down to the origins of cryptography as a word, it welcomes us in Greek. Cryptography is formed by the combination of the Greek words “Kryptos” and “Graphein”. These words mean "Hidden (Kryptos)" and "Writing (Graphein)".
If we take a look at the history of cryptography; It is said that it was first used by Caesar in 58 BC. The cryptography technique Caesar used; It is obtained by shifting (shifting) the letters of the alphabet in a certain order. Thanks to this technique, even if Caesar's military messages were captured, their content was not understood. This technique has been used by many military leaders over the years.
The technical meaning of cryptography today is; It is the whole of the techniques created by using mathematical methods in order to prevent someone else (3rd parties) from accessing the content of the messages or data during the communication between a sender and a receiver. In general, the working logic is; The first data sent is encrypted in random bit format using mathematical methods, then these data must be decrypted in order to access them. At this point, this encryption is decrypted thanks to a private key sent to the receiving party. People who do not have the private key will never be able to decrypt this encryption method.
Blockchain Cryptography
We all know a little bit how the working principle of blockchain technology works. In blockchain technology, data is collected and stored in blocks, then distributed across the entire network in a way that users can access. This is where cryptography comes into play. Thanks to cryptography, the security of the blocks created on the blockchain is ensured, that is, it ensures the security of the data on the blockchain.
In blockchain cryptography, two types of encryption are used while ensuring the security of data. These; Asymmetric Key Algorithm and Hash Algorithm are used.
In Asymmetric Cryptography Algorithm, two different keys are used for password and decryption operations. Each of the two people (receiver/sender) interacting with each other has two pairs of keys. These key pairs are; secret key and public key pair. We will discuss these key types in more detail later. Therefore, we can briefly explain as follows; A private key, a private key, and a key that should not be shared with anyone. A public key is a key that can be easily shared with anyone. The asymmetric key algorithm is also called digital signature.
Cryptographic hashing is one of the fundamental parts of blockchain technology. In the blockchain, each block is linked to the next block with a cryptographic hash. Thanks to this feature, it is directly responsible for its unchangeable feature, which is the most important aspect of Blockchain technology. There is no key usage in this algorithm.
Hashing is a system that produces an input string of any length and a fixed-length output. Many systems use the hash system to encrypt passwords. cryptographic hash At this point, the cryptographic hash ensures the reliability and integrity of the blockchain. At the same time, hash algorithms; double spend, 51% attack, etc. does not allow fraudulent data or transactions.
In short, blockchain cryptography provides the core features of any blockchain, such as security, integrity, and confidentiality.
Blockchain Platforms
There are many popular and unpopular blockchain platforms available. These blockchains can be centralized or decentralized. Some examples;
Ethereum
Tron
Steem
Binance
Question 3
Explain the Private Key CryptoGraphy.
Question 4
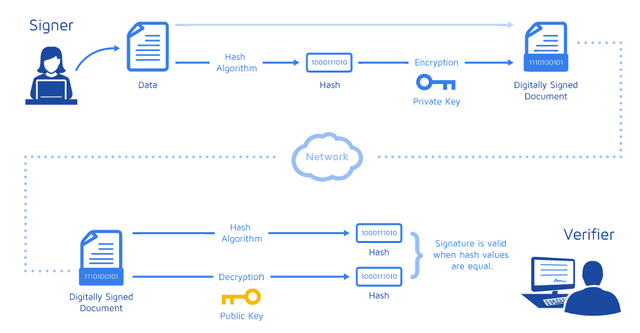
Explain the Digital Signatures CryptoGraphy and what is Singing Of Transaction/Message?
Signatures are used in many transactions in real life. The reason for using signatures in real life is that they are used to show that any shopping or information is verified by us. The purpose of using a digital signature can be considered the same as our real-life signature use.
Digital signatures are used to prove that our information, data or asset transfer transactions are carried out by us in digital environments. In real life, the use of signature is the process we perform using a pen on a document or paper, and although there are billions of people in the world, we were only special to us. Electronic signature is basically unique to us, but its working system is different from real-life signature usage.
Digital signatures are a method that includes mathematical calculations and are based on the use of two keys using an asymmetric encryption algorithm. As we said before, these keys are Privacy keys and Public keys. As we said before, digital signatures are used as proof of who we are for transactions we carry out on the internet and blockchain. By using digital signature during our transactions, we indicate that our transactions are correct and realized by us.
In general, the working principle is as shown in the diagram below.
Explain what is Symmetric and Asymmetric cryptography?
Symmetric cryptography
The word symmetric simple means something made up of the same parts. In this type of cryptography one key is used for encryption ( converting the information into unreadable language) and the same key is also used for decryption ( converting the data/information into readable language). In this type of cryptography we do not make use of the private and public keys to encrypt and decrypt but rather we use the secret key for both cases. We call it the secret key because this key is only known to two people that is the person sending the data and the person going to receive the data.
So let’s say I am going to send information to someone. The key i will use to convert the information to unreadable language will be the same key the person going to convert it back will use. If I want you to read it all I have to do is to give you the secret key I used to encrypt the data. Data Encryption Standard, Advanced Encryption Standard are examples of symmetric cryptography.
There are two main types of symmetric algorithm these include; the block algorithm and the stream algorithm.
1 - The block algorithm symmetric cryptography, is the encryption and decryption of the data into blocks.
2 - The steam algorithm symmetric cryptography is the encryption and decryption of data/information is an orderly manner.
One problem I have observed that this types of cryptography will have is since it’s only one key that will be shared through out assuming you have to share it to 5 people the information might get leaked and you won’t know who leaked it. Because it’s only one key.
From the above image you can see that the same secret key is used for encryption and decryption of the data.
Asymmetric Cryptography
This type of cryptography is the opposite of the symmetric cryptography because instead of using the same key for encryption and decryption of the data, the Asymmetric cryptography uses two keys called the private and public key for the encryption and decryption of the data. As I have been saying please note that the private key is supposed to be your secret and it is the key you will use to convert your data into readable language (decryption ).
So basically the public key is used for encryption whiles the private key is used for decryption.
Summary on Symmetric and Asymmetric cryptography
Symmetric cryptographyAsymmetric cryptographyUses one key for the encryption and decryption of data/informationUses the public key and private key for the encryption and decryption of data/information
How Blockchain Wallets CryptoGraphy works and explains the available types of Crypto Wallets.
Before I jump into how blockchain wallets cryptography works I will take my time to explain a blockchain wallet. Before I start we all in one way or the other use or own a wallet in real life. What we use this wallet to do is to keep our money safe and anytime we want to purchase something we remove from there and buy. Similarly the blockchain also has a wallet which used to store our digital assets (cryptocurrencies) through this wallet we can receive funds and also transfer funds to other people.
How does the blockchain wallets cryptography works?
Whenever you create a blockchain wallet you are provided with two keys namely; the public key and your Private key. The private key is supposed to be kept a secret and it is mostly advised you store it offline to prevent hackers from getting it.
Every wallet needs an address in other to receive funds, the wallet address are generated from the hash function of the public key in other words they are generated from the public keys. Every wallet has a unique address this means that my address will never be the same as your address.
The private key as I have already mentioned before is used to sign transactions before they are broadcasted for validation. When someone gets hold of your Private key he/she can get access to your assets that is why it is advised you do not tell a soul about your Private key.
Types of crypto wallets.
There are two(2) types of wallet namely cold wallet and Hot wallets other sources claim they are four including soft wallet and hardware wallets according to my research these wallets fall under the cold wallet and hot wallet.
Cold wallets(offline)
This type of crypto wallet does not need any internet connection to operate hence earned the name offline wallet. People might ask how can you access a wallet without using the internet. Yes! This can be done in a form of a removable USB drive which contains the owners wallet all you need to do is to connect your USB drive into a computer in other to access your assets.
With this type of wallet it very impossible for hackers to get access to your wallet because it is offline, hackers only hack something when it is connected to the internet. Cold wallets are the most preferred wallets for safety. It is also very convenient you carry you USB drive with you all the time.
I made mention that the hardware wallets fall under the cold wallets. Because when we say a hardware is something you can see, touch and feel and example is the USB drive which proves that indeed the hardware wallets fall under cold wallets.
importance of cold wallet.
1 - it is very easy and convenient due to the small nature of the USB drive
2 - hackers can’t attack your wallet hence hackers free.
3 - it is used to big companies to hold large amount of assets.
Disadvantages of cold wallet
1 - Incase you find you self in a place where there is no computer you can not access your assets
2 - Due to the small nature of the USB drive it can easily get missing.
Hot wallets
This type of crypto wallet is the most used wallet. This type of wallet is connected to the internet unlike the cold wallets. Any wallet that will require you to connect to the internet is a hot wallet. This hot wallet usually sends and receives assets using their unique addresses.
Under this type of wallet the soft wallet is categorized because they require internet data to function. This type of wallet if not being careful Is at high risk of being cyber attacked. So it is advised you store your private keys offline. The advise I have is if you plan on holding your assets from long you should go for the cold wallets because of their security.
Importance of hot wallets
1 - once you have internet connection you can access your asset at any time.
2 - You are given total control of your assets because you will hold your private and public keys.
Disadvantages of hot wallets
1 - They are easily cyber attacked since they are connected to the internet.
conclusion
For now, the blockchain-based predictive market is still unfamiliar among gamblers, this has resulted in the movement of the blockchain-based predictive market moving slowly and not as profitable as the usual predictive market. This can be caused by people's trust in crypto which is still minimal so they are hesitant to bet. However, there is still a long way to go and opportunities are still open for blockchain-based predictive market developers to make blockchain-based predictive marketplaces the top choice in the future.
Hello dear please meet your mentor or any of your country representatives for proper orientation. I know one of your country representative @ngoenyi who can be of good help. You are not supposed to do this homework task because your reputation and SP does not meet the requirements of the task. Go to new comers community and do your achievement program, from there I’m sure you will build your reputation and equally learn more about steemit platform.
#cameroon #affable
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thank you dear for the mention. I hope he can bet to me for the assistance
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
You are welcome ma’am.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit