Here comes another beautiful week with wonderful lectures from you our dear steemit cryptoacademy professors. It has been another week of expository classes. Thank you more professor @pelon53 for your lecture on #root hashes and merkle tree. Thank you for this class.

INTRODUCTION.
Blockchain and it's application in cryptocurrency has been applauded for it's transparency and security. Despite being decentralized, people feel very confident to do transactions. Such confidence is achieved by the very core algorithm followed by the first cryptocurrency builder Satoshi Nikamoto.
Blockchain is a form of distributed ledger; whenever a transaction occurs in the Blockchain, the transaction record is copied and distributed to every node in the chain. Miners have a task of assembling transactions into blocks before adding it to the Blockchain. Before a block can be added previous blocks will need to be verified to ensure order and then new block will be created to bundle in new transactions.
In bitcoin, new blocks are created every 10 minutes; there are up to 1500-4000 transactions contained in a block; there are up to 692,357 blocks as at today. Just imagine a node trying to verify a transaction, it will need to download all the transactions running into billions. This will be almost impossible within the limited timeframe and imagine the speed of the computer to calculate this enormous task. It will mean that it might be impossible to mine Bitcoin given the many transactions going on every minute. That is where Root hash and merkle tree comes in. Nodes use hashes of files instead of the full files and this hashes are constructed into a binary structure, summing up the total hashes of the block to one hash known as the root hash or merkle root.
In this task, I will show how to form hashes, how to build merkle tree and how to get the root hash.
Let's get started.

EXPECTATIONS OF THIS TASK:
1.- Explain in detail the hash rate.
2.- Make the following Merkle Tree:
Transaction (tree leaves): Steem1; Steem2; Steem3; Steem4; Steem5; Steem6; Steem7; Steem8.
I made it to the Root Hash. And put every hash generated using SHA-256 , show screenshots.
Tell the steps to follow to verify if Steem6 is included in the Markle Tree.
3.- Using the SHA-256; you must place each complete hash in the Merkle Tree.
Transaction (tree leaves): SCA1; SCA2; SCA3; SCA4; SCA5; SCA6; SCA7; SCA8. Explain each step, show screenshots.
If the number of leaves on the tree is odd, what should you do? Explain.

HASH RATE.
Simply put, hash rate has to do with the computational speed of a node or a miner to complete mining process.
As I stated above, there are lots of transactions going on every second in a blockchain. This transactions need to be bundled into a block. And before that is done, previous blocks need to be verified. That verification will need lots of computational power to verify hashes of the previous blocks before creating the new one. Therefore a miner will need high computational power to solve the hash algorithm in other to find a new block and earn a reward. This is especially so in the proof of work consensus algorithm employed by Bitcoin. The faster the computer or the node, the faster it solves the mathematical algorithm required before finding a new block; and the node will only be rewarded if it were able to be the first to solve the mathematical algorithm and find the new block.
Bitcoin mining is quite competitive and very expensive. The reason is not far fetched. Bitcoin is a rare asset now valued into thousands of dollars. The more individuals or groups want to mine Bitcoin, the more tasking it becomes because we see many nodes competing to be the first to find the mathematical solution and therefore win block reward. So the more competitive it becomes, the more higher hash rate a node needs and the less competitive, the lesser high rate.
At the early age of Bitcoin it was possible to mine Bitcoin with a personal computer with high graphics card or GPU ( video processing unit). As Bitcoin receives more adoption and as different nodes compete for block rewards, the possibility becomes never. It is only high efficient and expensive computers that can do that. And that is equally so in all Blockchain's using proof of work consensus algorithm.
While working to have a high computational block is important for miners, it could equally pose a challenge when a node or group of miners has much high computational powers controlling more than 50% of the mining network. This is know as the 51% attack.
51% attack
This is a problem for Blockchain due to the havoc it can cause. Having more than 50% control of the network mining hash power can lead to the attackers doing some series of manipulations. For example they can monopolize the mining, not allowing other miners to mine new blocks and therefore taking all the rewards for themselves. They can equally stop transactions of some users or all users, they can reverse the transactions they made making it appear it has never been made leading to double spending.

Merkle tree
This is a structure deployed in crytography to store data more efficiently and securely. It is binary in nature. It's goal is to get the root hash of a block.
Meckle tree has the leafs, the branches and the root hashes. It is gotten from top to bottom. That means to construct merkle tree, we will first get the hashes of the leafs, then the branches and lastly the root. We will examplify using two set of examples.
1
Steem1; Steem2; Steem3; Steem4; Steem5; Steem6; Steem7; Steem8.
2
SCA1; SCA2; SCA3; SCA4; SCA5; SCA6; SCA7; SCA8.
I will make use of #sha-256 password generator.

First example
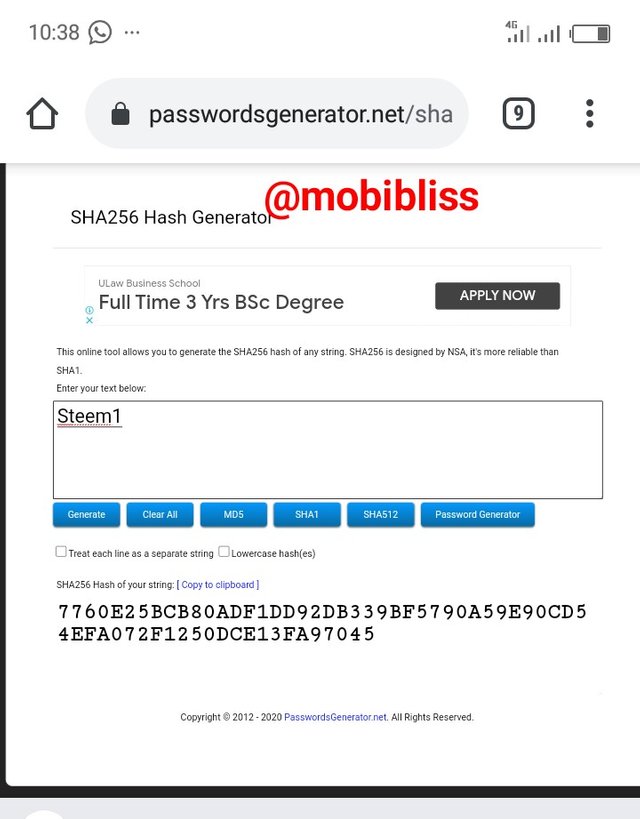
Steem1Hash
7760E25BCB80ADF1DD92DB339BF5790A59E90CD54EFA072F1250DCE13FA97045
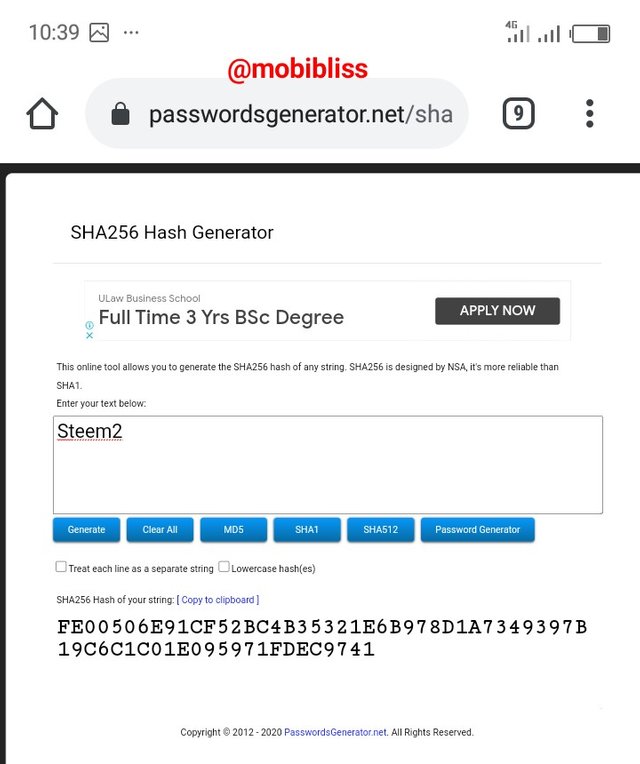
Steem2 hash
FE00506E91CF52BC4B35321E6B978D1A7349397B19C6C1C01E095971FDEC9741

Hash
A9418332E0C351D6A50C835AA9E57D514F0573C231D491E97726DB8A5844F2DC
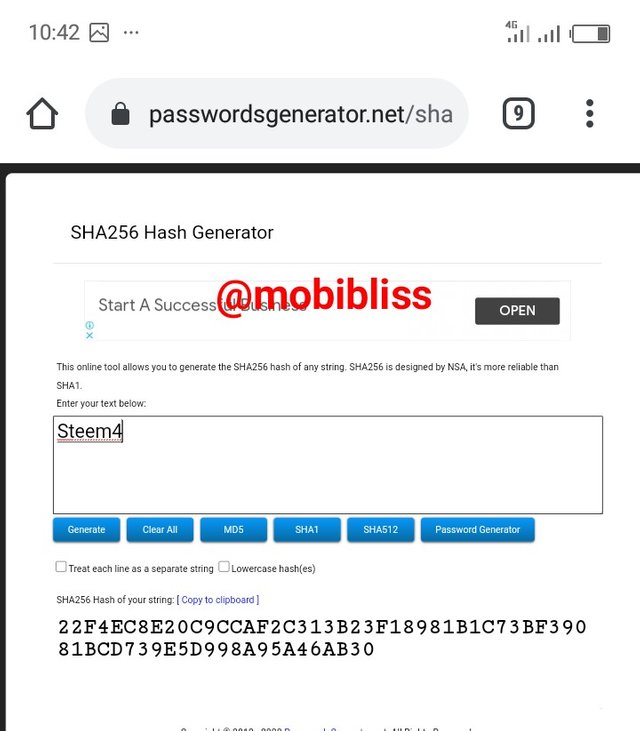
Hash
22F4EC8E20C9CCAF2C313B23F18981B1C73BF39081BCD739E5D998A95A46AB30

Hash
2A3C87336683AB0DDFA56AFEFC740E6C13A02FEA0A43D6797343B26D7AF0C57B

Hash
A7BAA6DE0C0658E9E3681966E542BACD116529F5AE9A2D9126CDB1C1D5BC1278
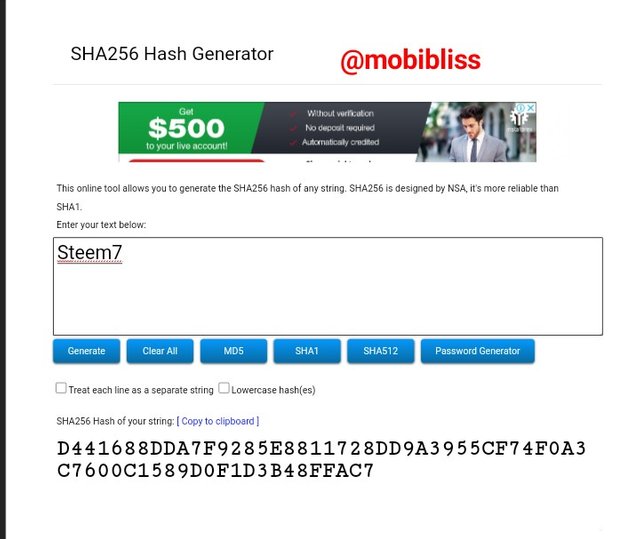
Hash
D441688DDA7F9285E8811728DD9A3955CF74F0A3C7600C1589D0F1D3B48FFAC7
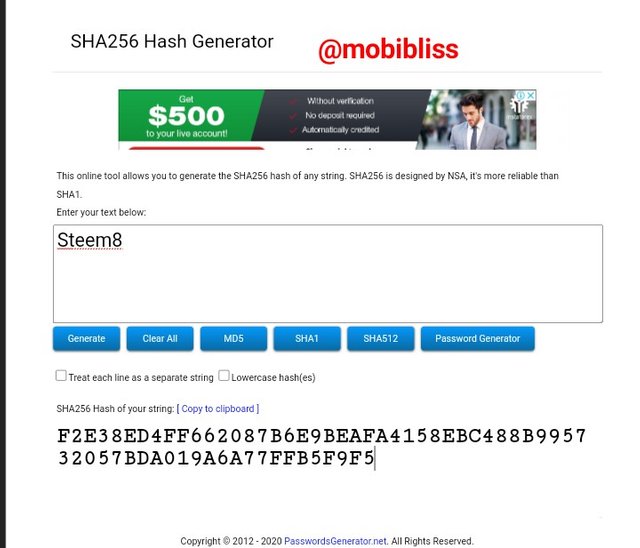
Hash
F2E38ED4FF662087B6E9BEAFA4158EBC488B995732057BDA019A6A77FFB5F9F5
Let's now get the branches

Hash steem1steem2
F4FCF07549A6B77DC09016E658822703D1784B34307F1D2B2D45A26F3E9B2EF8

Hash steem3steem4
DAFF9EB1160CBA951ED6B3C33A8D09AC22D32B6706EF90A4014C4BC864D3D664

Hash steem5steem6
9A27534620A5D081FF88B64CAC0140F09BC9184E71878C64671B0C59DFD040DA
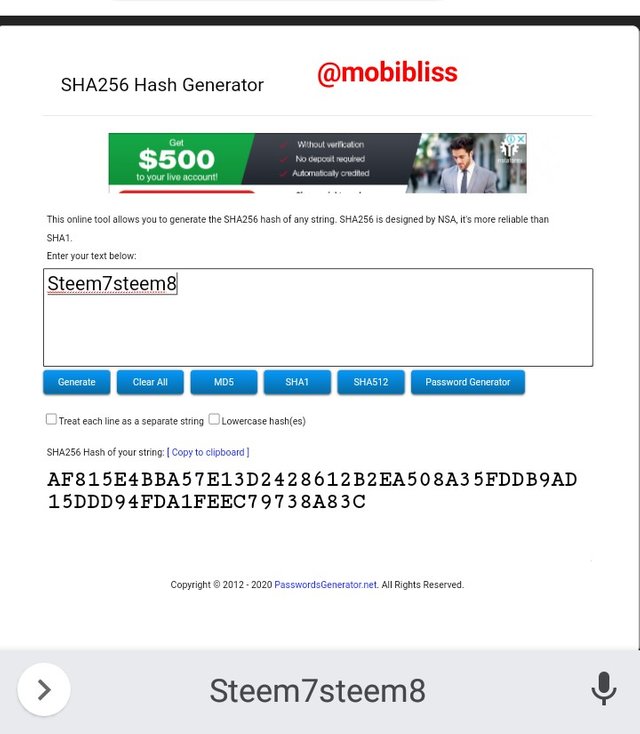
Hash steem7steem8
AF815E4BBA57E13D2428612B2EA508A35FDDB9AD15DDD94FDA1FEEC79738A83C
Next, we will get the second branches

Hash steem1steem2steem3steem4
74E55450887C30B5E697C36454FE859CBB042A844E01D1821F07023C68E8510F
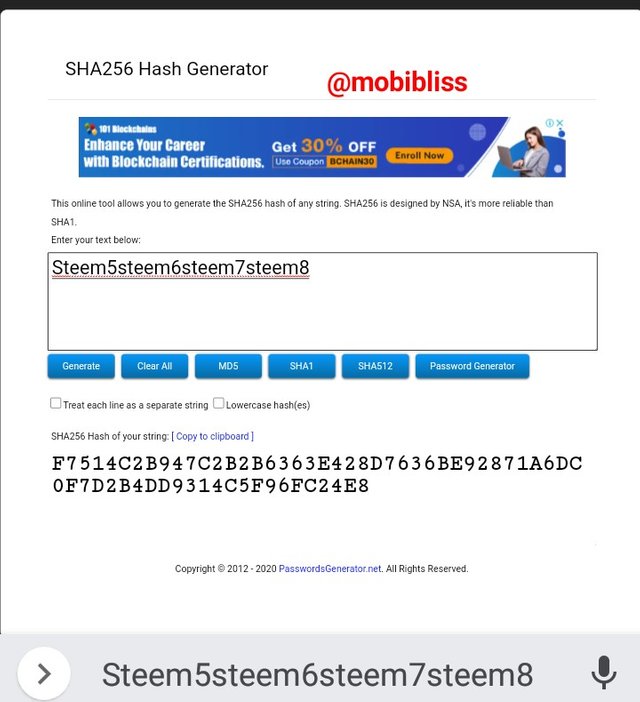
Hash steem5steem6steem7steem8
F7514C2B947C2B2B6363E428D7636BE92871A6DC0F7D2B4DD9314C5F96FC24E8
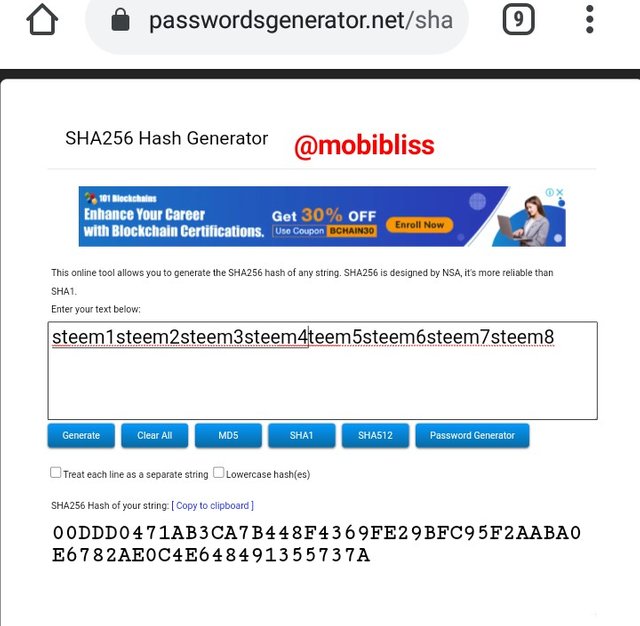
Root hash
00DDD0471AB3CA7B448F4369FE29BFC95F2AABA0E6782AE0C4E648491355737A
Having gotten our root hash, let's show merkle tree sample :
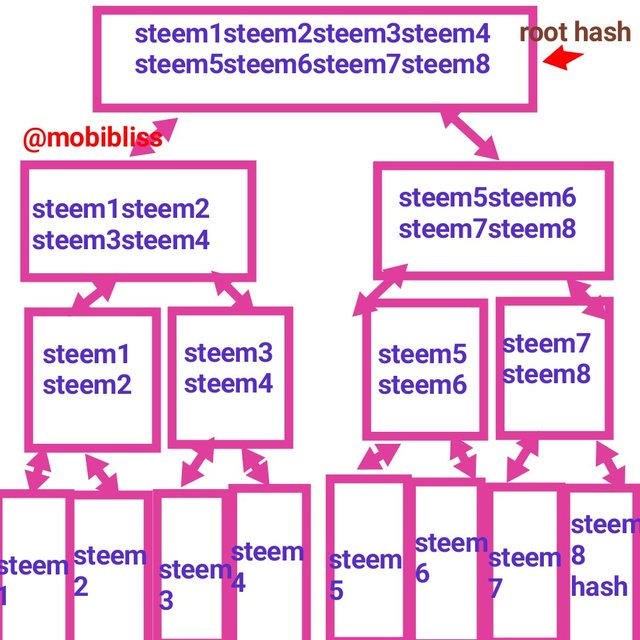
Here is the root hash of this work
CB40CA6DB72DD507CF9118963F94B7740822258E74AFB0FD45D89DB35D24B386

Example2
SCA1; SCA2; SCA3; SCA4; SCA5; SCA6; SCA7; SCA8.
We will follow same process as in the first example

Hash SCA1
13E0A04BB0E669E1C638DBE3A704743F99F162B25245E4D8C064D35BA38FA8C8
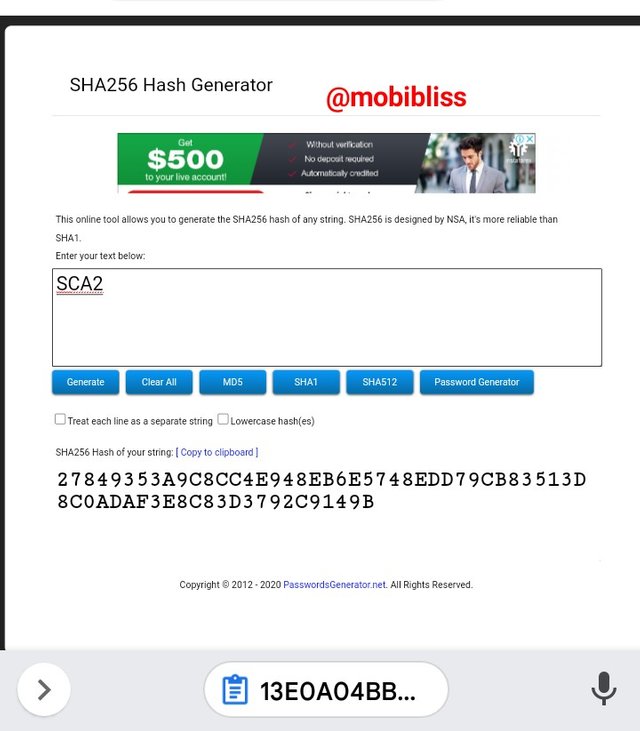
Hash
27849353A9C8CC4E948EB6E5748EDD79CB83513D8C0ADAF3E8C83D3792C9149B
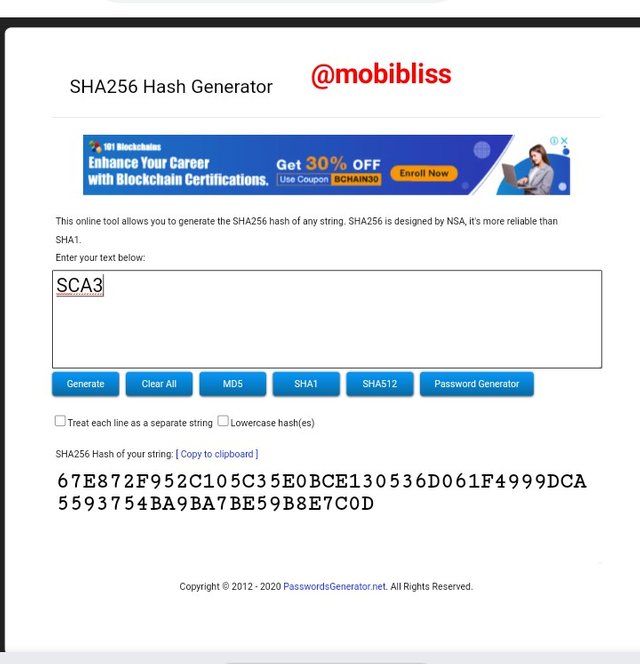
Hash
67E872F952C105C35E0BCE130536D061F4999DCA5593754BA9BA7BE59B8E7C0D
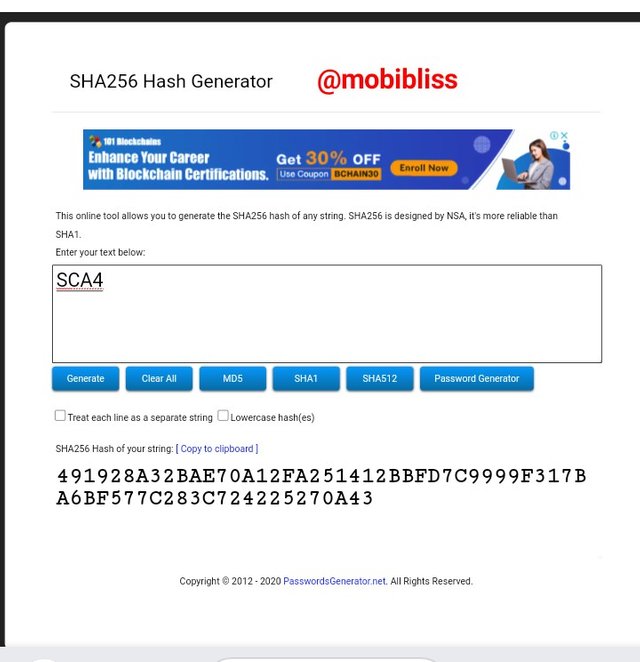
Hash
491928A32BAE70A12FA251412BBFD7C9999F317BA6BF577C283C724225270A43

Hash
99C078C39CDE7F47799E0E8691460A9F3E83E78D498EA989308FCFCC58907B19
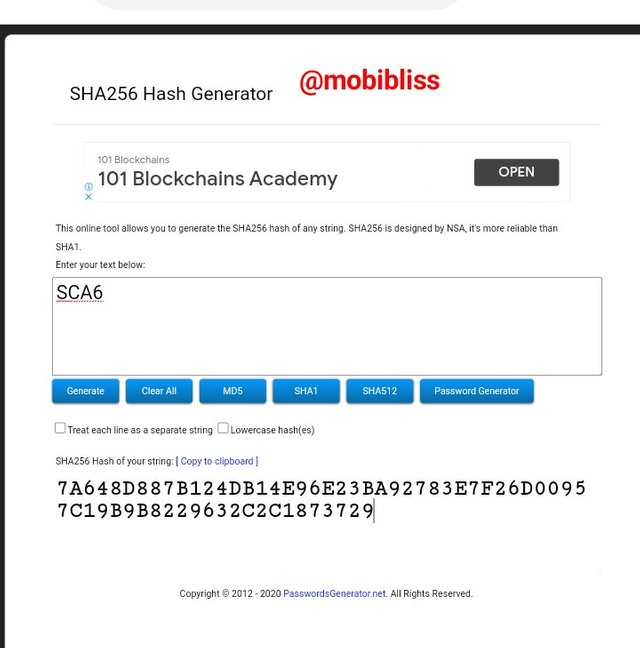
Hash
7A648D887B124DB14E96E23BA92783E7F26D00957C19B9B8229632C2C1873729

Hash
7E0BBD6BA4BA9896F9911AF46B06DD2C47535F9C80B29D693FDF6B9319D0D68E

Hash
562ABCEEB497E1FE7AE275A883FD5EF9D92A05F5C19D82ABAA0DC1571B7DF3AD
Branches
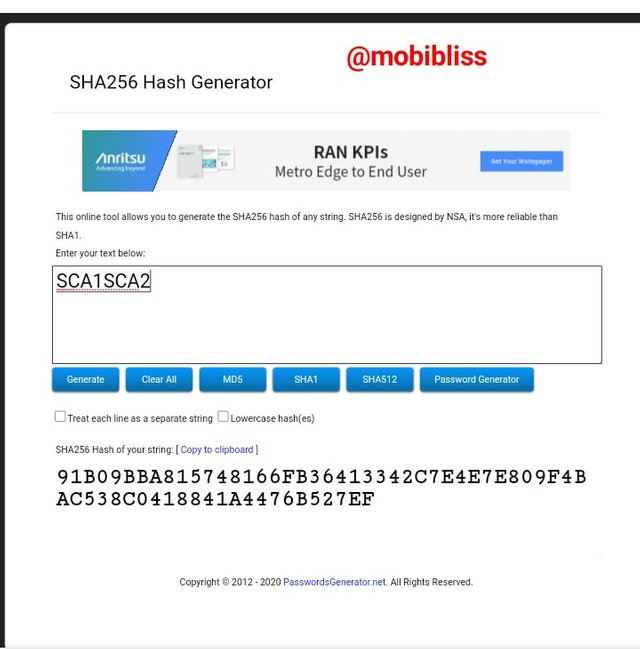
HASH SCA1SCA2
91B09BBA815748166FB36413342C7E4E7E809F4BAC538C0418841A4476B527EF
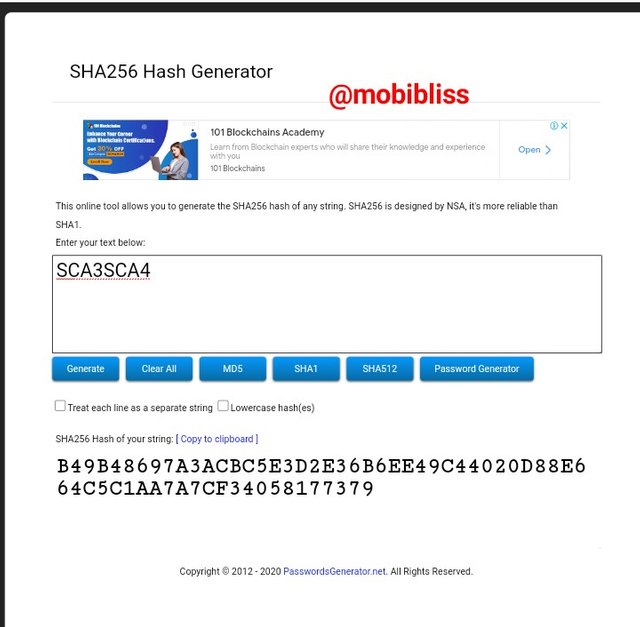
Hash
B49B48697A3ACBC5E3D2E36B6EE49C44020D88E664C5C1AA7A7CF34058177379
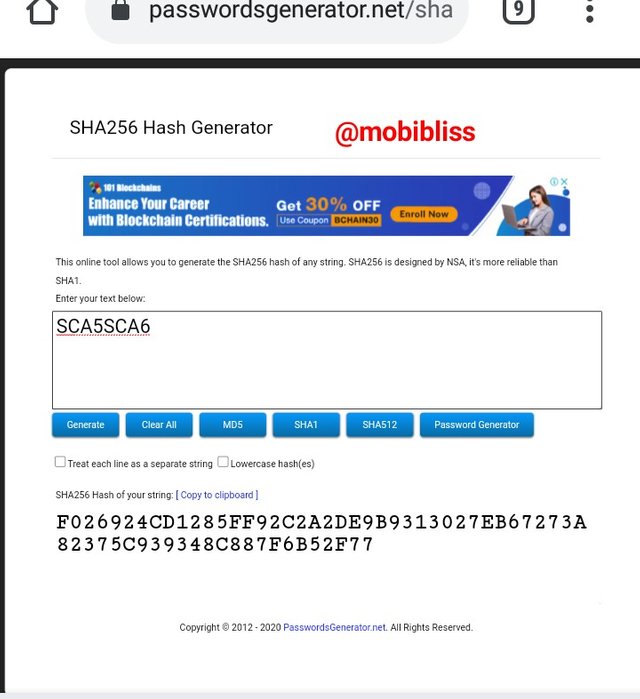
Hash
F026924CD1285FF92C2A2DE9B9313027EB67273A82375C939348C887F6B52F77
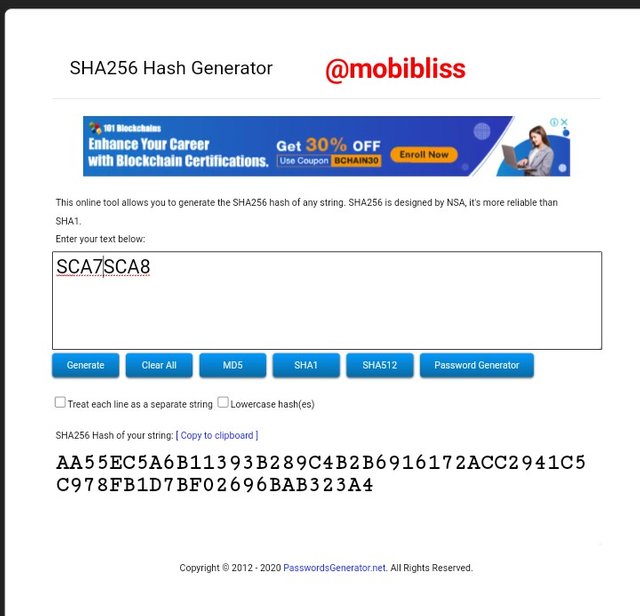
Hash
AA55EC5A6B11393B289C4B2B6916172ACC2941C5C978FB1D7BF02696BAB323A4
Second branches
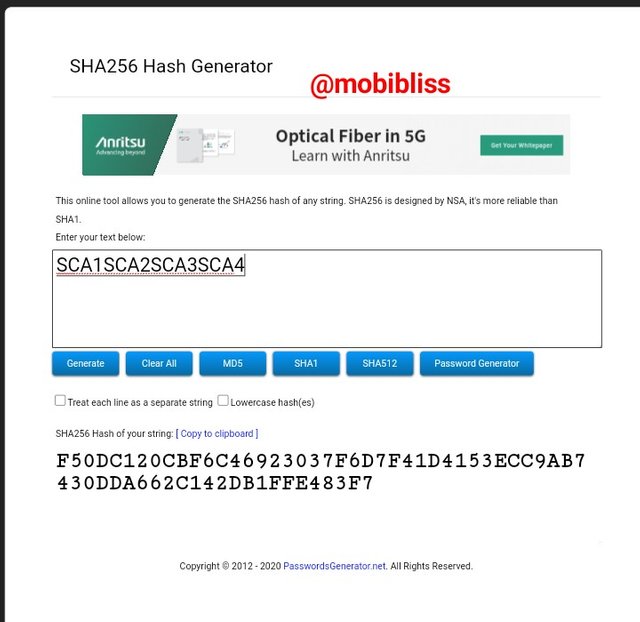
Hash
F50DC120CBF6C46923037F6D7F41D4153ECC9AB7430DDA662C142DB1FFE483F7
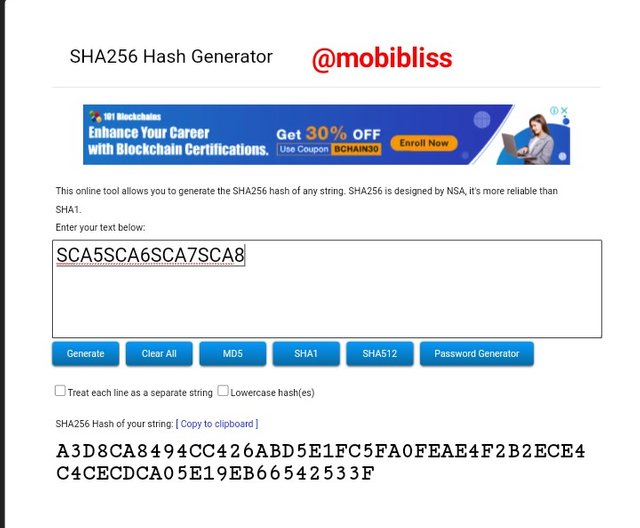
Hash
A3D8CA8494CC426ABD5E1FC5FA0FEAE4F2B2ECE4C4CECDCA05E19EB66542533F
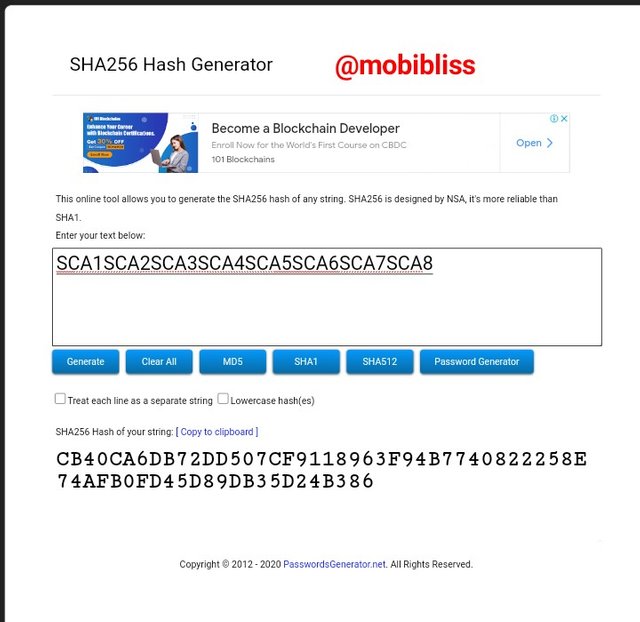
Root hash
CB40CA6DB72DD507CF9118963F94B7740822258E74AFB0FD45D89DB35D24B386
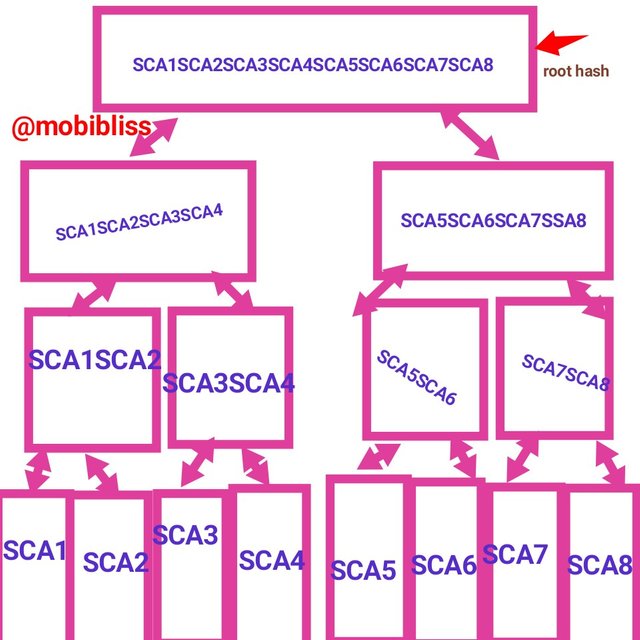
Root hash
CB40CA6DB72DD507CF9118963F94B7740822258E74AFB0FD45D89DB35D24B386

SUPPOSE THE NUMBER OF LEAFS IS ODD
merkle tree is a binary construction. As shown above it works on on 2 pairs closer to each other like ab, cd,ef,gh. Then if there is an "i" which is odd, I will have to make a duplicate of that number to form a binary, which will be "ii".
Suppose in example 1 that there is "steem9" in the merkle tree. I will need to duplicate "steem9", therefore we will have
Steem1 steem2 steem3 steem4 steem5 steem6 steem7 steem8 steem9 steem9
Steem1steem2 steem3steem4 steem5steem6 steem7steem8 steem9steem9

SUMMARY
Hash rate refers to the computational speed of a node. A node is a computer used in mining cryptocurrency. The computer itself is the miner.
It is important to have a high efficient computer with a high computational power for you to mine a block in Blockchains with proof of work consensus algorithm like Bitcoin.
A 51% attack refers to when an attacker or group of attackers has more than 50% control of the hashing rate of a blockchain. While they can not destroy the Blockchain, they can manipulate it to their interest.
Merkle tree are scientific binary construction applied in Blockchain to ensure efficient data storage and security.
Merkle tree pools up hashes of a block to a single root hash.