QUESTIONS
☆;1》What is a Cryptocurrency?
☆;2》What is Cryptography and how does it make cryptocurrencies secure?
☆;3》 Explore the Steem Genesis Block and Sign in as proof of completion.*
☆;1》What is a Cryptocurrency?
This cryptocurrency we are speaking about is a kind of virtual or digital money, Cryptocurrency has grown to become famous globally, especially with the world first coin Bitcoin /which turns be the most expensive cryptocurrency.
Actually cryptocurrency can't be controlled by any individual or authority like the Government body and it's private, simply as its name implies. However, additionally it's very difficult to forge or fake due to the blockchain ledger interface which regulates the currency.
There are many specific kinds of cryptocurrencies that is actually in existence presently. The number one or the keystone of them is called (BTC) Bitcoin. then there are other ones that follows BTC like (ETH) Ethereum, Bitcoin Cash, and XRP, etc. We store or save out currencies in a crypto wallet or a digital wallet. Anybody can take part and participate alongside the blockchain, with the help of cryptography, all users data or information are secured and protected. For each transaction that occur or process within the blockchain, there’s a digital confirmation method to verify it and as well protect or prevent you from fraud.

☆;2a》What is Cryptography and how does it make cryptocurrencies secure?
For instance, Mr Peter wishes to send a personal message to his dear friend [Mr Paul] and for that he needs no third-party to view the message. Now Mr Peter uses a social outlet just like the internet to execute his message. Let's say that [Mr Mark] a third-party came across the communication medium, with the authority he has he can easily manipulate the message. assuming if Mr Mark has entrance to their private information?. honestly, that might actually course a huge disaster. So now how can Mr Peter ensure that no authority or the third-party could manipulate the message which he sent to Mr Paul? The major goal now is to bring about communication security and here, this is the moment in which cryptography appears or comes in.
This Cryptography we are talking about is said to be the procedure or act of protecting information, and communication, so that only the person who received the message can privately access it.
Now let us see how this cryptography can assist in protecting the connections among the two friends I mentioned earlier. {Mr Peter and Mr Paul} Now for Mr Peter to protect or safeguard his messages, he has to translate the understandable message which he wants send to Mr Paul, in a complicated pattern, he now translate it to a random digits and Immediately its done, he will use a key or a code to encrypt the message and immediately it is done, a recent value is being created named ciphertext. now he had sends the cipher text to a communication medium, without him worrying about a third party coming across his private message, even though the third party does, it will be very tough or difficult to unlock his message, if the authority is not with the correct code.
assuming Mr Mark the [third party] manages
to interfere with that message. so when this message reaches to MR Paul using the right key it will traslate the cipher text into a numerical value coresponding to the range text,So after making use of the key for the decryption, So what he gets is the actual range text message or the error. and this error has indicated that [Mr Mark] the third party has tempered or manipulated the message.
☆;2b》 how does it make cryptocurrencies secure?
Cryptocurrency worldwide, cryptography makes sure that the transactions and partakers withinside the network are protected, additionally it assists in keeping the subjects of information personal, and it assures the value of data, clarifying it was not modified. additionally, it assists in organizing the innovation of the latest currency units, transfer authorization of tokens and assets.
- This Symmetric key cryptography uses the exact cryptography keys for each encryption of the plaintext plus decryption for ciphertext. These keys might look-alike or otherwise. These keys symbolize a split secret among two or many parties that may be employed to protect a private data link. This symmetric key is likewise known as the secret key.
- Asymmetric key cryptography uses two different keys which are [ private and public key] for encryption additionally for decryption of communication. The Public key is circulated widely ] not like the private key that is recognised only by the owner.
☆;3》 Explore the Steem Genesis Block and Sign in as proof of completion.
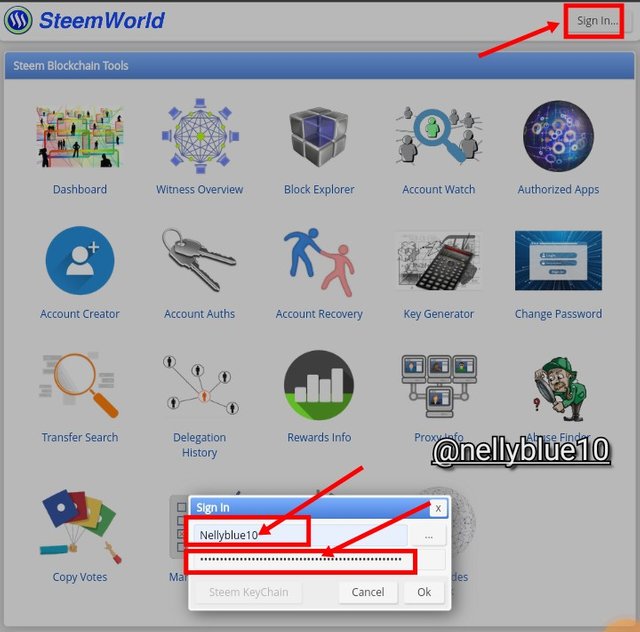
- ☆ Lets vist the website which is
{steemworld.org}
- ☆ We gats to sign in by pressing the sign in icon using my own posting key.
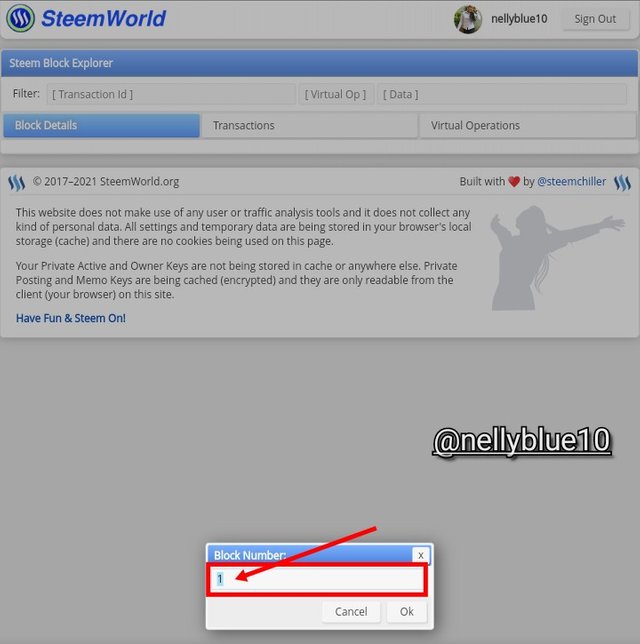
- ☆ Here we have choose or select the icon {block explorer}

- ☆ Inside this box blow, we have to put 1 in there and click ok the to proceed or continue.
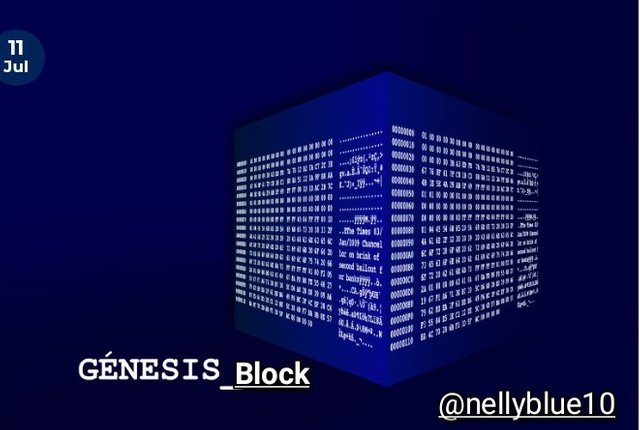
- BOOM 💥 you are looking at steem Genesis block
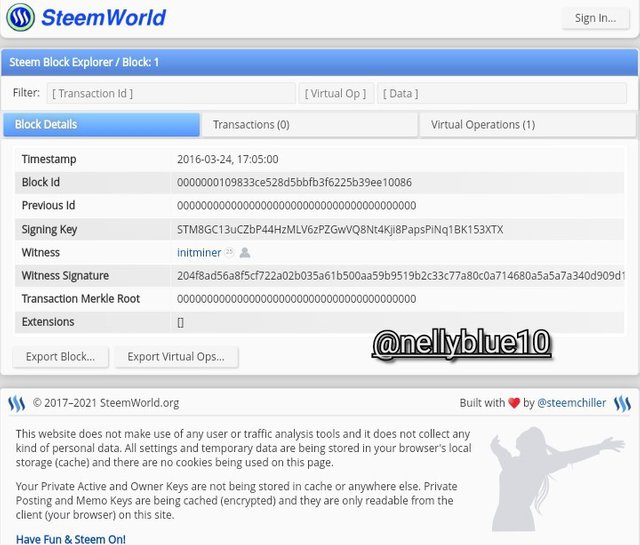
- ☆ I have to sign in to complete this task
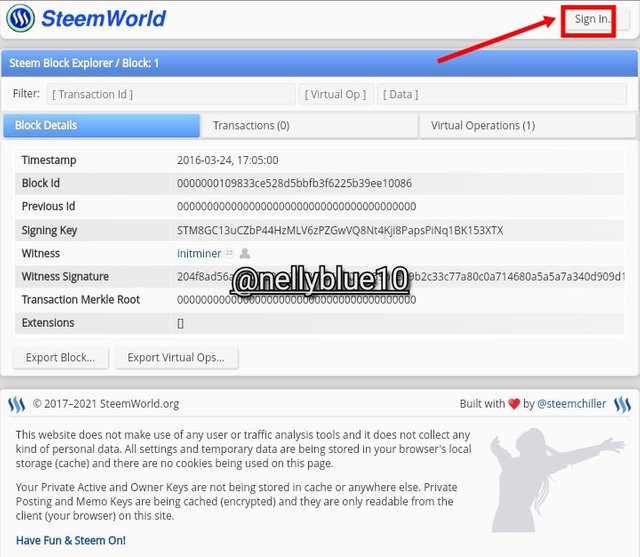
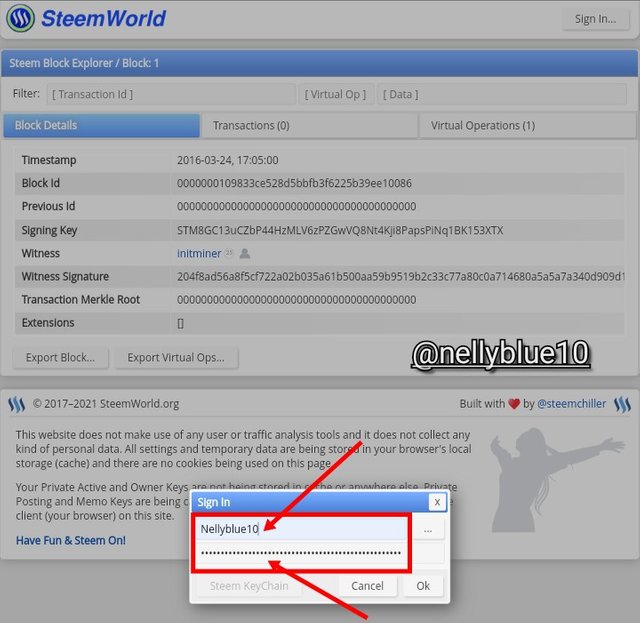
- ☆ Like I said early I have to sign in to complete the task, inside the box blow is my username and my posting key, i click OK,
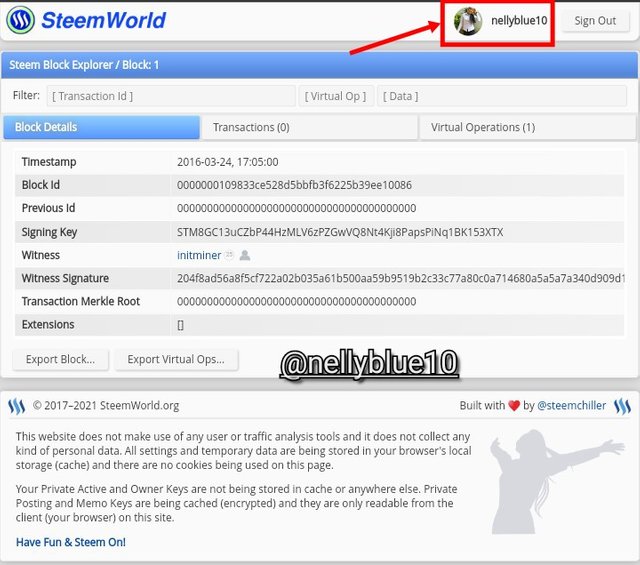
- ☆ I'm logged in now, as you can see from the screenshot below.
CONCLUSION :
Cryptocurrency has skyrocketed globally,
Even some super Market now accept it as payment, due to it volatility we should take precoction when trading cryptocurrencies. and also the
Cryptography which is said to be the procedure or act of protecting information, and communication, so that only the person who received the message can privately access it. This keeps our data private/secure.
All thanks our dear professor @awesononso
For this educative lecture.