Hello everyone!
1. Explain the Blockchain CryptoGraphy and mention few names which are the Blockchain Platforms?
Cryptography is a method of developing techniques and protocols to make sure that a third party does not have access and knowledge of the data from the private messages during a communication is going on. Cryptography is coined from two ancient greek words, Kryptos and Graphein, the former term means“hidden” and latter means“to write”. Cryptography is made up of several terms , they are:
Encryption: This is a process of plaintext also known as normal text, to a ciphertext which is also known as random sequence of bits.
Decryption: This is the inverse process of encryption, conversion of ciphertext to plaintext.
Cipher: This is a mathematical function that is made up of a cryptographic algorithm. This is used to convert plaintext to ciphertext.
Key: This has to do with a piece of information that is required to induce the output of the cryptographic algorithm.
The primary focus of cryptography is to ensure the security of participants and transactions, safeguards against double-spending, and lack of influence of central authorities. Most times, cryptography helps to securing different transactions which are happening on the network. Also, cryptography finds applications in verifying the transfer of digital tokens and assets. Cryptography ensures that only the participants for whom the transaction is intended can obtain, read and process the transaction and can verify the authenticity of participants and the transaction. Let's take for instance,a radio communications between two participants . In this kind of communication, it will be highly secure and encrypted, and only the participants that can receive and know the information contained therein. The applications of cryptography is contained in blockchain.
cryptography serves as a technique to transmit a secured messages among two or more participants. The sender will leverages on a specific kind of key and algorithm for encryption of a message before he/she can send it to the receiver. On the hand, the receiver uses decryption for obtaining the original message. Thus, the most important aspect in the cryptography is the encryption keys.
Blockchain Platforms
Applications that are based on blockchain are developed on blockchain platforms. It maybe any centralised or decentralised, permissioned or permissionless blockchain. The blockchain platform also increases everyday due to the fact that, the demand for DAPPS is on the increase. Some blockchain platforms are -
Bitcoin
Ethereum
Steem
EOS
Ripple
Neo
2. Explain the Public Key CryptoGraphy.
A public key is sometimes referred to as asymmetric cryptography. public key cryptography is a kind of cryptographic Protocols which is built on algorithms. This kind of cryptography requires two separate keys, one is private or secret, and one is public. Public key cryptography makes use of a pair of keys to encrypt and decrypt data to protect it against any access that is not authorized. If other participants want to encrypt data, they get the recipient’s public key from a public directory which is used to encrypt the message, and to send it to the recipient. As soon as the message arrives, the recipient decrypts it using a private key, whereby no one else can access it.
The challenges of a public key
One of the challenges associated with public key is speed. This is the common challenge to public key. private key cryptography methods are faster than the public key encryption method that currently is available. One way of curbing this shortcomings with public key cryptography is to combine the public key with secret key systems to offer security to the public key system and the speed of the secret (private) key system. Also, another challenge associated with public key cryptography is that it is susceptible to attacks through spoofed or compromised certification authorities. When these attacks happens, internet fraudsters impersonate by choosing a public key certificate from the compromised authority. This allows the internet fraudsters to have access to a public key to the name of another user.
BENEFITS OF PUBLIC KEY CRYPTOGRAPHY
It increases data security. Public key cryptography remains the most secure protocol because users do not need to transmit or reveal their private keys to anyone. By so doing, lessens the chances of cyber fraud.
Public key cryptography also provides digital signatures that cannot be rejected. Public key cryptography ensures each user to be responsible for protecting his private key, as against what is obtainable in private key systems wherein, users have to share their secret keys and even trust a third party for transmission.
3. Explain the Private Key CryptoGraphy.
Another name for private key is secret key. A private key is usually variable in cryptography, which uses an algorithm to encrypt and decrypt data. Private keys play a hug role in symmetric cryptography, asymmetric Cryptography
A private key is a long and randomly generated character which cannot be easily accessed or known if the party is not the owner of the wallet. In other words, if you have a private key, then you are the owner of the wallet. One of the features of private key is that, it can not be easily attacked by internet fraudsters. Also, private keys are faster than the public keys. Cryptocurrencies can be accessed using a private key.
.png)
Image source
4. Explain the Digital Signatures CryptoGraphy and what is Singing Of Transaction/Message?
In the real world scenerio, signature is usually used to validate and verify transactions between persons. Similarly, in the digital world,digital signature binds the person to digital data. The binding between person and signature is verified by a receiver or using the public key. Digital signature is an element of a cryptographic protocol suites, which are commonly used in blockchain to verify nodes and thereby authenticate the information that is sent.
In blockchain, once a transaction is signed using a digital signature, verification will be done to verify the transaction.
Generally speaking, there are two main functions associated with digital signature which are easily identifiable. They are; Signing and verification. The digital signature ensures the the authenticity of the sender
When a transaction is digitally signed, it is sent to the blockchain network wherein, the transaction is authenticated by the blockchain miners using the Public key of the sender. After the authentication is made, the transaction is sent to the another block where the transaction takes place
Importance of Digital Signature
Authentication: once the message has be verified using the public key of the person who signs the document, it means that, the message is authentic and it is signed by the correct person who has the correct information on the message.
Data Integrity: once there is an attack by internet fraudsters, the receiver of the digital signature will not be verified and thus,the output provided by the verification algorithm will not match and it will fail due to the fact that, the data integrity has been violated.
Non-repudiation: Since it is the signer has the knowledge of the signature key, the unique signature on a given data will be created by the signer. So once the receiver presents the digital signature to a third party as a proof, no dispute may occur later in the future.
5. Explain what is Symmetric and Asymmetric cryptography?
Symmetric Cryptography
Symmetric cryptography is also known also as secret key cryptography. It uses a single shared secret to share encrypted data between two parties. symmetric cryptographye key makes use of both encrypted and decrypted data. This means that, when a data is encrypted,it converts plain text to cipher text using a secret key and when a data can decrypt, it means that, data comes in its original form using the same key. Generally speaking,symmetric cryptographic keys are 128 or 256 bits long, a 128-bit long key has 34x10^37 possible combinations which makes it impossible to manipulate by a third party.
Advantage - No much computational power is needed for Symmetric key algorithms which produces a small file size which ensures faster transfer of file.
Disadvantages
One of the biggest disadvantages with symmetric key encryption is that a user need to have access to the key to the party with whom the user is sharing the data.
Asymmetric cryptography
Asymmetric cryptography is another name for public-key cryptography. Asymmetric cryptography is a process that makes use of two related keys wherein one is called public key and the other is private key. It is is use to encrypt and decrypt a message. It has protection against anyone who does not have authority to access or use the keys. A public key is a cryptographic key that is used by any person to encrypt a message wherein only the recipient with the private keys can be understood. Asymmetric cryptography uses two pair of keys for encryption and decryption so that, If the public key uses encryption, therefore the corresponding private key is used decryption. Also, if the private key is used for encryption, then the related public key is used for decryption.
The advantages of asymmetric cryptography
- There is no problem with distribution and exchanging of keys.
- There is high level of security as the private key is not revealed to anyone.
- It enabled the recipient to verify the message that comes from a particular sender.
Disadvantages include:
- It is very slow as compared to symmetric cryptography.
- Messages cannot be decrypted if the private key is lost.
- public keys are not always authenticated thereby making it difficult to know which public key belong to a person.
- Once a hacker identifies a user's private key, the attacker can have access to the user's messages.
6. How Blockchain Wallets CryptoGraphy works and explains the available types of Crypto Wallets.
Crypto wallet is a kind of software that stores private keys and public keys which are easily accessible by their respective keys. Private key is a proof to that,a user owns a digital wallet. Crypto wallet has an address that is similar to bank account no. in the real world. In real life situation, crypto wallets work the same way as our bank account by having a crypto wallet address.
The bank will require a password before any transactions can take place between two parties. Crypto wallet does not store currency because Cryptocurrency is not meant to store in any location rather, the transaction exist in blockchain. Two bank account number can not be the same with each other. Same applies where there are two crypto wallet addresses. It can not be the same with each other. Now, if I want to send funds to someone, I will require the bank account number of the person I want to transfer the fund to. Similarly, crypto wallet address is needed to transfer the fund to another person. Also, if a bank account password is manipulated and hacked, funds will be at risk vis-a-vis crypto wallet will be at risk if the privat key is stolen.
Types of crypto wallets
There are so many types of crypto wallets which come under three main categories. They are; software wallet, hardware wallet and paper wallet.
Some software wallets fall into the hot wallet category, because they are connected to the internet.
Software wallet
There are many types of software wallets, but the mostly known software wallet are web wallets, desktop wallets, and mobile wallets.
Web Wallets
Web wallets are accessible through a web browser. This means that one can access crypto wallet from anywhere as long as the user has password with a device connected to web browser.
With web wallet, it gives one a little opportunity to control over his/her cryptocurrency.
Desktop Wallets
A desktop wallet is one which allows a user to download the application to his/her computer. After downloading the application on the device, a data file will be generated wherein a password will be created to access the keys.
One of the benefits of a desktop wallet is that, the user is the owner of the holder of wallet.
Hardware Wallets:
A hardware wallet helps to a user's key save on a physical device instead of in software. Some hardware wallets work like to a flash drive. They can be connected to a computer or other device through a USB drive.
one of the major benefits of a hardware wallet is that, it is not connected to the internet, so that it removes a major security vulnerability.
Paper wallet:
A paper wallet is a same thing with cold wallet as it is physically a piece of paper. The document contains all the data that is needed to access one's cryptocurrency.
Whilst cold wallets offer more security, the format of a paper wallet creates a vulnerability.
7. What is the Merkle trees and What its importance in blockchain?
Merkle Trees
The Markle tree was introduced by Ralph Merkle in 1979. He created a process whereby a data could be verified where a computer is allowed work much faster than before.
It thereafter becomes the backbone for any blockchain. It was used in the fundamentals of Bitcoin code. It is concerned with a structure of hashes of different blocks of data, arranged in a tree-like structure wherein the top of the hash, is a hash of all the hashes of all the transactions that are a part of the block in the blockchain network. The position of the tree is an upside-down position.
Importance of Markle Tree in Blockchain
The importance of Markle tree is summarized into integrity and verification of data. It also reduces the space required to keep data in the blockchain.
Integrity of the blockchain: As soon as the root hash is created, it becomes proof and any change in any transaction of the block will change the root hash. so the whole block will be invalidated. Thereby, it ensuring the integrity of any block and blockchain.
Verification of data : verification requires that, a transaction in the blockchain,only the Markle Tree of that particular block will need to be varified. This can be understandable with the help of the example of the Markle tree below.
8. Practical + Theory, do some practical research, study on Blockchain Demo: Public / Private Keys & Signing and then explain the functionality of Key, Signature, Transaction, Blockchain with proper screenshots of yours practical. (Do study well for this topic)
Keys:
We all know that,there are two keys which are the Public and Private Keys
Both of these Keys correspond to each other. Now lets demonstrate it on this [website](We know that there are two keys which are the Public and Private Keys
Both of these Keys correspond to each other. Now lets demonstrate it on this [blockchain(https://andersbrownworth.com/blockchain/public-private-key
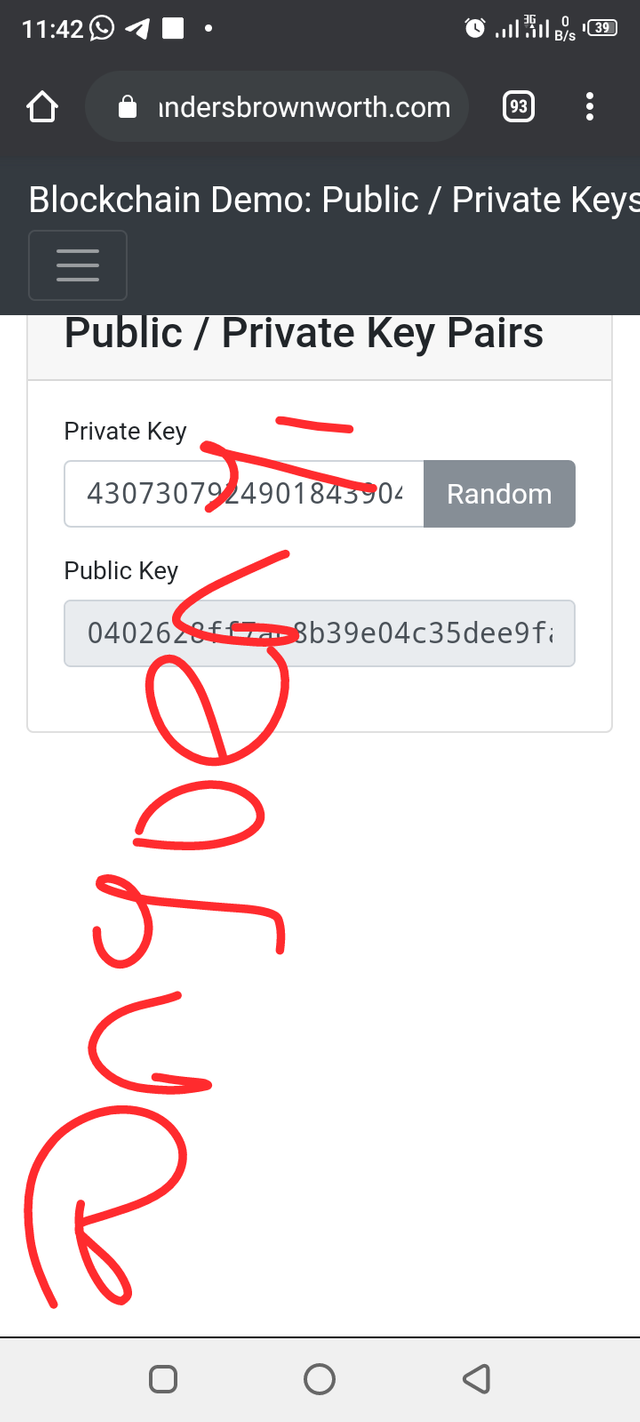
The private key shown above is:
43073079249018439042426348197482375100963271175842924932202017884683464362302
The public key is 0402628ff7ac8b39e04c35dee9fad57b85f576e3914a3b5b40c7adfaf645ba7df5fd2bfa6e7288873d0c699dec58c9cabc00c933fec540a36fd73bb4c001523589.
If I make a slight change in the private key, the public key will change. The public key now is 047e6ecdc265c6253ba82fcc440412156c81a09d1befbb71e06fc39d886c81ea954932bdd8c19ef8d821093d01ff88577c55dd4f6b1cf4d02ef9780b41fb25b986
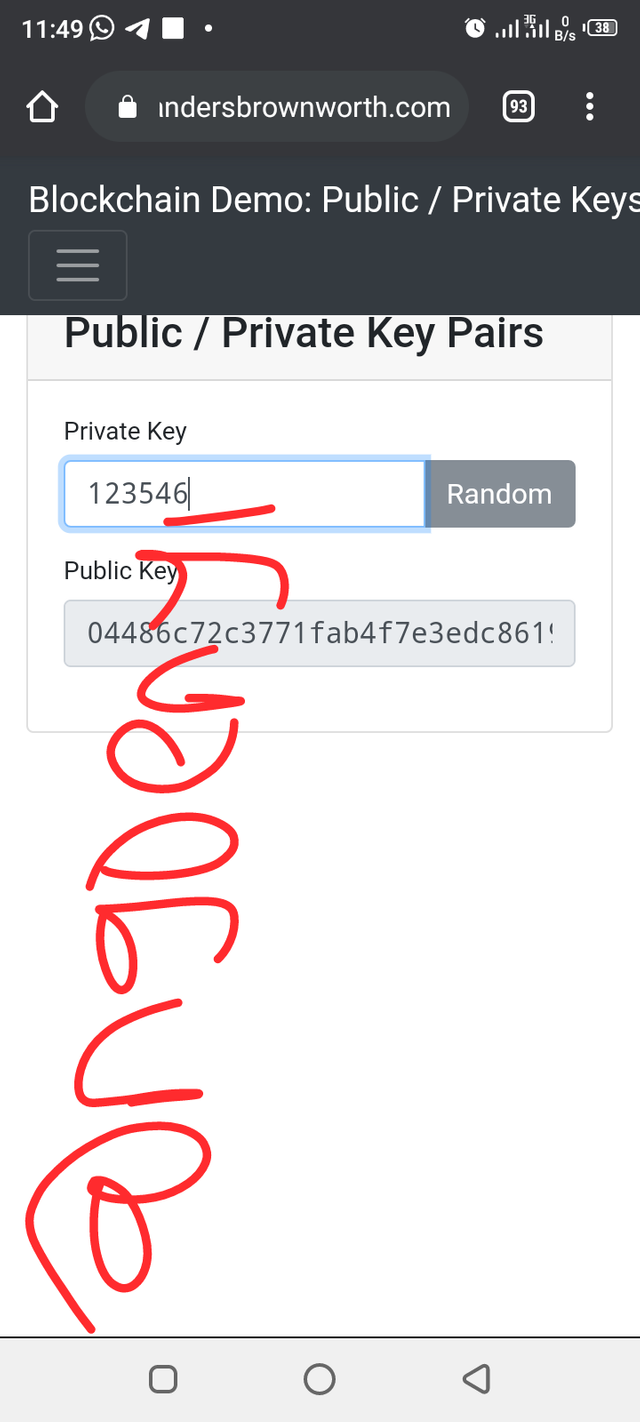
Digital Signature
Now I will practically demonstrate the Digital Signatures on Blockchain demo
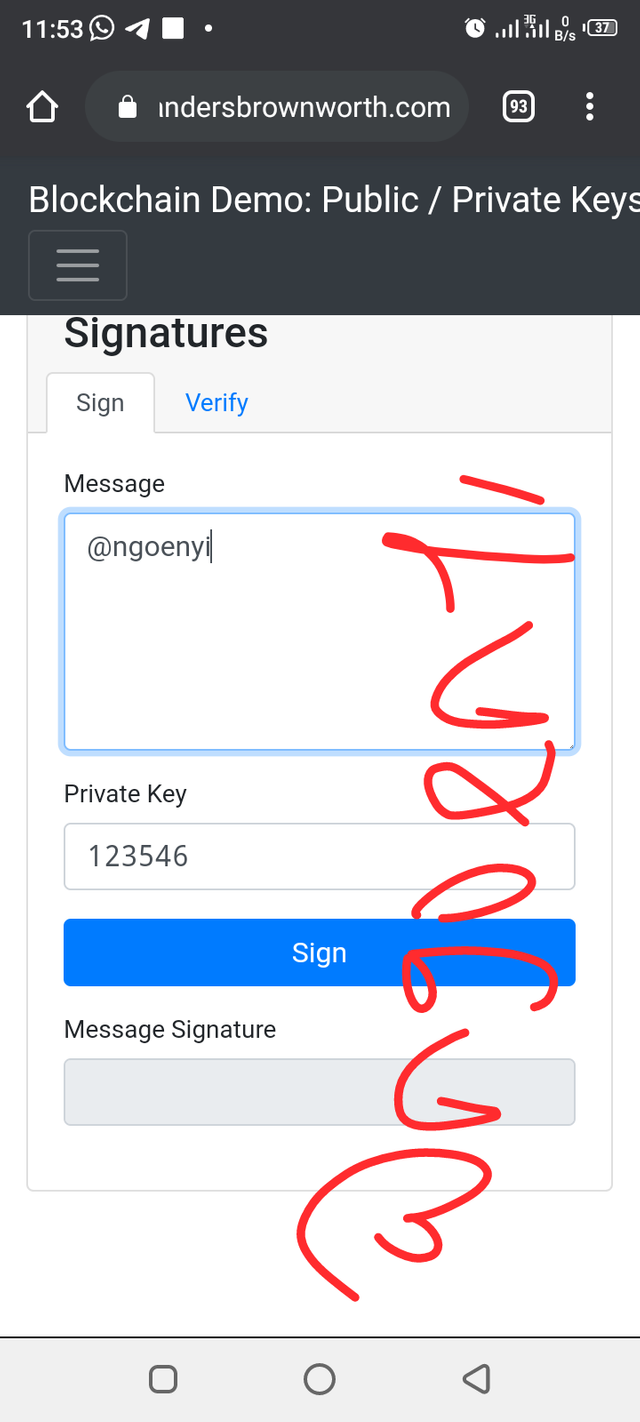
when I click on the Sign option it will digitally sign the transaction and we will get a Digital Signature.
Conclusion
Number one
Cryptography is a method of developing techniques and protocols to make sure that a third party does not have access and knowledge of the data from the private messages during a communication is going on. Cryptography is coined from two ancient greek words, Kryptos and Graphein, the former term means“hidden” and latter means“to write”.
.jpeg)
.png)