Great time steemians, it's yet another great time out and we're seriously advancing in time for this season and this time we're considering a very frenetic and important aspect of the bitcoin technology called the Taproot technology and Schnorr firms. These factors just like the lesson explained, are answers to the issues of scalability, privacy and issues related to smart contracts in Bitcoin technology..Here's my assignment professor.
Following the lesson properly and before i delve proper into the lesson, ill love to trail factors leading to the topic I'll be explaining to ensure better understanding of it.

Firstly we see the Taproots, to be solutions to the privacy issue of Bitcoin in that transactions being run on the bitcoin could be seen by anyone and the solution to this, is the running of these transactions in scripts which increase privacy since the programming language on the Bitcoin network could be blocked or unblocked through these scripts.
And these scripts which have several types and abilities to authorize scripts and when things get tough, we'll learn about it below!

1.) Explain in details the P2SH and P2PKH showing the differences between the two directions
The P2SH :
The P2SH fully known as the Pay to Script Hash could be seen as a pattern of scripts implemented on the Bitcoin's transactions network which allows for users to secure a part of the script hash and when it's time to collect and unlock the bitcoins at the end of transactions, the original script must be provided.
So dropping a concise definition of what the P2SH addresses are, we could term them as unique addresses that allows for the further creation of addresses and sending and reception of transactions that demand the adherence to a pattern of steps before the balance that hold the addresses could be accessed.
This pattern of scripts allows for intense security since users are able to create unique scripts that would be shared to receivers of transactions which they would need to perform a set of fore-stalled actions before accessing With the use of the P2SH,several crypto currencies like Bitcoin and the others have their addresses in transactions sent to script hashes unlike others that are sent to public key hashes where privacy is reduced.
The transactions on P2SH are sent to addresses beginning with more than 1 and so the addresses here, show an encoded script hash and no longer a public key one (ie multisig addresses)
Let's see an example of a P2SH transaction making use of the ScriptSig and ScriptPubKey to send-secure and receive a transaction.
In a case where, the locker of a transaction makes use of more than one key to lock a transaction eg 2 or 3, and there are more than one signature needed to implement the transaction, there would be need for a code, that would check and confirm that the keys are in line with the signatures of the transaction and that they could unlock the transaction together (this process is seen as the OP_CHECK MULTISIG. A code is also needed to know that a Scriptpubkey would be opened if the hash is in line with the ScriptSig (The OP_HASH160)
The P2PKH :

In the performance and transacting of Bitcoins on its network, the P2PKH is basically important. The P2PKH fully represents Pay to Public Key Hash and in these scripts, the public key and digital signature generated by the relative private key is the basis for transactions here. The two kind of payments used in the payment to public keys are seen as payment to public keys ( P2PK) and payment to public key hash (P2PKH)
The preference of the (P2PKH) which we're considering now is due to the fact that :
It's hash is more little and allows for it to be stored in smaller forms.
There was vulnerability in the public and private keys and so a private key could be gotten from a public key and with the public key been publicised only when the tokens in transaction are spent, a malicious action on it remains useless
Differences between the P2SH and P2PKH :
The difference between the P2SH and P2PKH include the following below :
Generation :Irrespective of the fact that P2SH, and P2PKH addresses are generated in like ways, the former ie P2SH, make use of the hash160 of a script and utilizes a version byte of 0×05 while the P2PKH, makes use of the same hash160 but this time uses a public key and a version byte of 0×00
Cost :Secondly a major difference between the two, is that the Pay to Public Key Hash (P2PKH) is relatively more expensive to use than the P2SH which is a bit cheaper and affordable
Finally, the P2PKH begins with a one and is the highest compatible with bitcoin while the P2SH begins with a three and allows for multiple transactions on it

2.) It is required to transfer 10 BTC that's owned by 3 of 5 multisig nature portfolio to ths MTC company for the purchase of some equipment
Using the ScriptSig and ScriptPubKey to explain the steps that are followed
Firstly, from the look of things we see that this transaction is a multi signature transaction and to perform this transaction, there would be three keys (3 keys of the image) and we have it too that there would be 5 signatures of participants that are needed to complete the transaction.
Therefore we make use of the OP_MULTISIG which would confirm that the 5 signatures are correct in relation to the 3 keys involved here in the transaction and that they would ne eligible to validate the transaction
The script to unlock the 10BTC is gotten the MTC company when this steps goes appropriate but then we need to get the Script Pub key where we need the OP_HASH160 as the code that generates the SHA-256 and RIPEMD-160 and shows if the Scriptpubkey would be accessed if the generated hash, is in line with the scriptSig.
We could from here use the SHA-256 and RIPEMD-160 and the output would be checked with the Scripthash in the pub key and if the result is same, the MTC company, successfully receives the bitcoin
Explain what happens if the transaction is made using Schnorr signatures
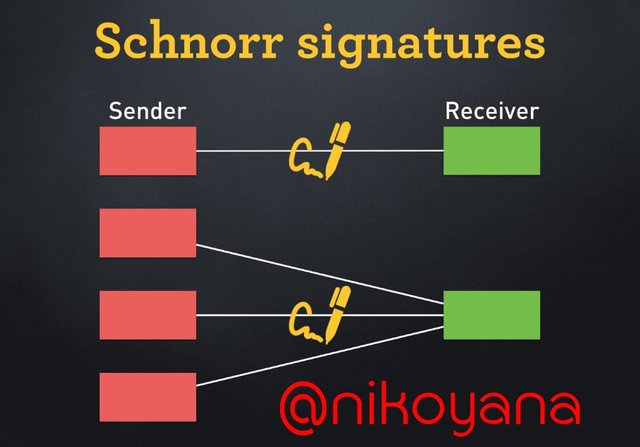
Now, if this transaction was made with the use of Schnorr signature, we know that this is a multi-signature transaction and so there would be delay during the process of making the transaction.
Further more, the transaction volume would be increased due to multiple signatures required and more than signature that validates the spending. There would also little issues on the network since there could be holds and pauses and increased time for the processing of the transaction.
The solution of the Schnorr signatures to this, is to convert all the signatures into one since they are all elements of same entry

3.) Why do you think taproots and Schnorr signatures would help the privacy of the Bitcoin network?
Clear as crystal, the aim and sole purpose of the Taproots and Schnorr signatures is to increase privacy on the bitcoin network.
The question is how?. This is it.!
The Taproot functions as way to increase users privacy since it helps make sure that user transactions which are originally displayed on the network are made private and more secure for example, the basis of the lightning network is on 2-of-2 multi-signature and this Taproot,allows for the securing of Bitcoin to several scripts ie it makes it unable for users to ascertain the particular transactions that create lightning channels
From here, we'll need to consider, the effective role taken by the Schnorr signatures to keep the Bitcoin network more private :
Firstly, the Schnorr signatures leave users of the network without knowledge of a transaction being single or multiple which helps users with the privacy of their transactions which they need
One of the major problems of transactions which is double spending is averted since the nature of Schnorr signatures allow them to be be very secure and avoid it's manipulation by any one on the network

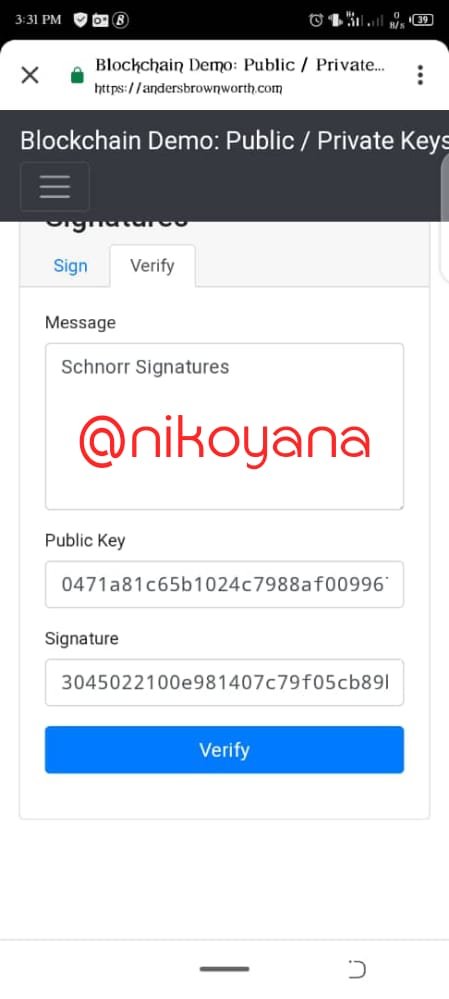
4.) Using the Blockchain demo, write the following message :Schnorr signatures, generate the message signature and verify the message. Then delete the first character from the message signature and check again. What happened??
- I used the blockchain demo link in the work and got to the blockchain platform where there are features like Message, private key and private signature
- I typed in the Schnorr Signatures in the message box
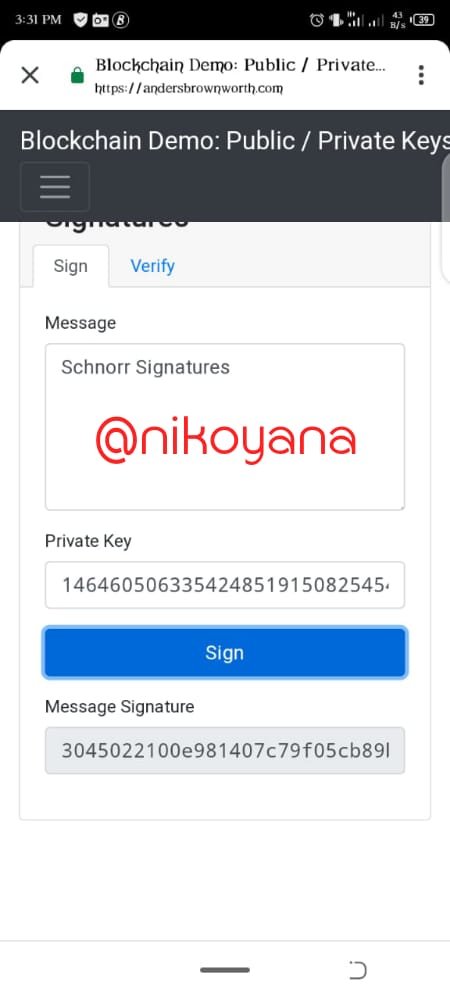
- After clicking on sign, im able to generate the message signature for the message
- Then to verify it, i go to the right hand part that's next to the sign bar, that says "verify"
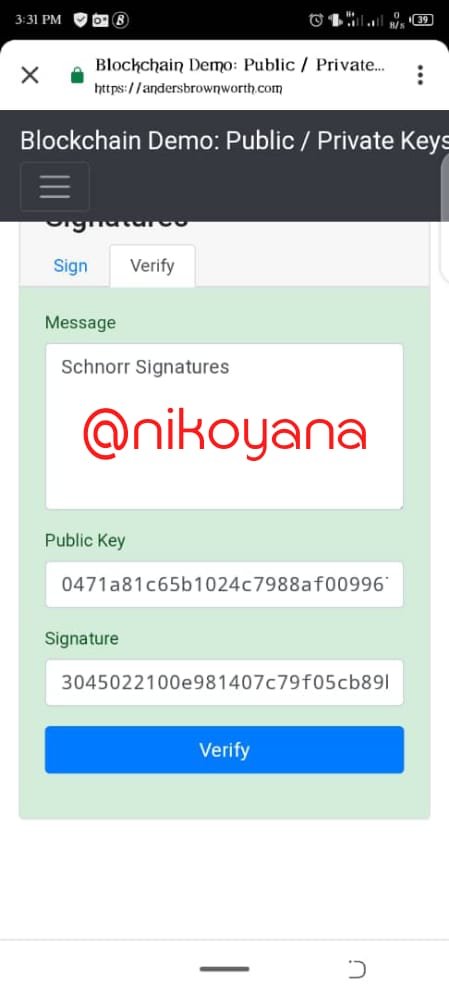
- The background gets green to show success in the verification of the transaction
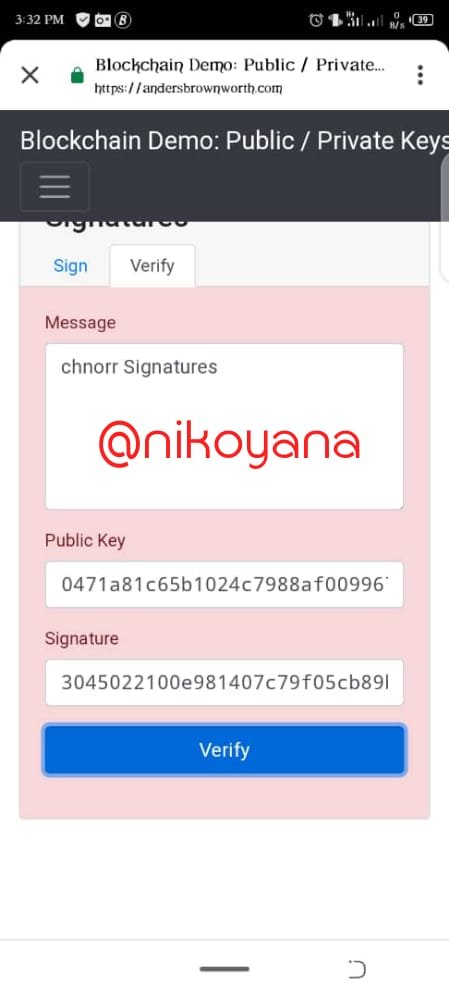
- Now when I take away, the first character ie "S" from the Schnorr, the transaction gets red which shows its no longer verified and the public key and signature is changed

CONCLUSION
I've come to the end of this expository work of mine based on advancing the privacy of the transactions ran on blockchains and we considered the Taproots, Schnorr signatures and other forms of advancing Bitcoin transaction privacy including examples showing how these transactions could be done..
We finally get to the end of it that, the public display of transactions on the network, could be changed and privacy, increased on the Bitcoin's network

cc
@pelon53