Hello..!!
My Dear Friends
This is @ns-porosh from Bangladesh 🇧🇩
How are you all? I hope you are well by the grace of God.I am well with your prayers and mercy God's grace.At first of all thank you to the sir @pelon. Your lesson provides a lot of information on homework tasks.

1:-Explain what does the resistance to collision mean? And what does resistance to preimage mean?
HASH
A hash is a cryptography function that generates input data as an encoded digit. These encoded digits are unique codes and there is no possibility of finding similar new ways in their ecosystem. That means these hashes are in specific alphanumeric characters which is very secure. Even these hashes are immutable and of fixed length. The hash function translates the input of a given length to the output as encoded to a certain length. Simply put, a hash function is a calculation tool. This computing tool is basically used to create a small data to a larger data.
A hash is the backbone of a blockchain. The hash function is a very efficient function of the blockchain. Which is used to create data for all major transactions in a blockchain. Also the validity of different types of input and validation in blockchain is done using hash functions. Hash only helps to simplify data of 64 characters of a certain length. The hash function is a one-way function. Since it is a one-way function, it is almost impossible to change or reverse it.
RESISTANCE TO COLLISION
Collision resistance is an important fundamental feature of the hash function. A collision occurs when two things collide, but a collision occurs when two separate inputs are produced at the same output during a hash function. Collision resistance does not allow two separate inputs to produce the same output. This generates a separate output to the same input. Collision resistance basically creates a kind of design to prevent against any kind of collision. Collision resistance is a protection function of hash cryptographies. A hash function basically acts as a collision resistance.
We can call collision resistance as HASH property. Simply put, it is impossible to find two inputs that produce the same output to prevent collisions. For example: X and Y values are almost impossible to find due to collision resistance. That is, X is not equal to Y value (X ≠ Y) but H (X) is equal to H (y) value H (x) = H (y).
RESISTANCE TO PREIMAGE
Preimage resistance is a security feature of a hash function that makes it impossible to save hash values to find or recover original input data.That is, it ensures that the input of the hash function cannot be determined by the output of the hash function.The concept of preimage resistance is basically pre-image resistance. The output value is usually repeated due to pre-image resistance. So it enables to make sure that the hash function is distributed in a uniform way. The minimum length of the output must be at least 80 bits to be pre-image resistant.
Also the resistance of preimage is an element in the range of hash functions that makes it qualitatively impossible to find the input that will copy. This makes it impossible for attackers to discover the value of the input, including the hash value.
2:-Use tronscan and etherscan to verify the hash of the last block and the hash of that transaction. Screenshot is required for checking.
Using tronscan to verify the hash of the last block and the hash of that transaction.
Step-1
- Be the first to enter the Link link at Tronscan.
Step-2
- Then click on the three parallel lines at the top right of the screen.
Step-3
- After clicking on three parallel lines, click Blockchain from the base of how many options will come.
Step-4
- Next click on the block option.
Step-5
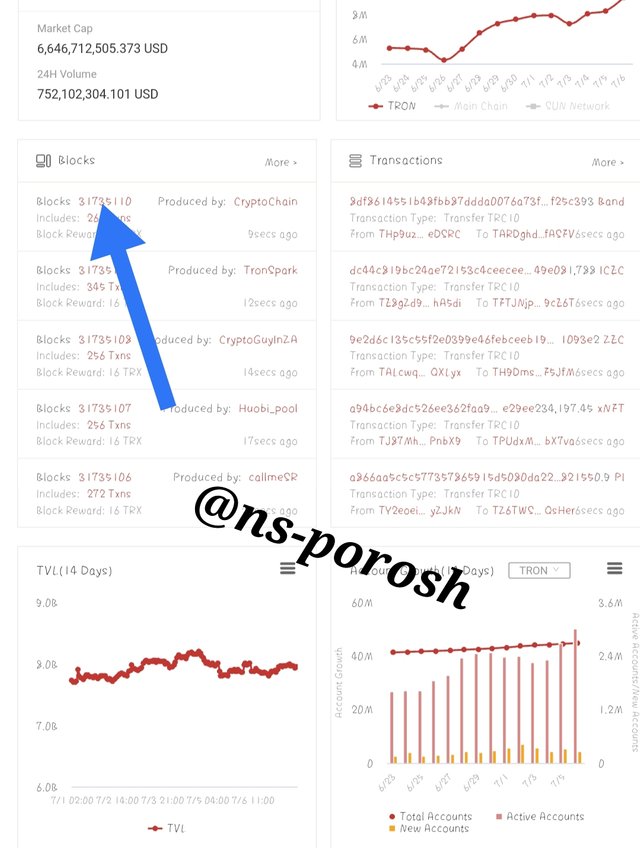
- Then you will see numerous blocks. Ex: The last block here is # 31735110. Click on the last block and scroll down to see the hash of the block.
Step-6
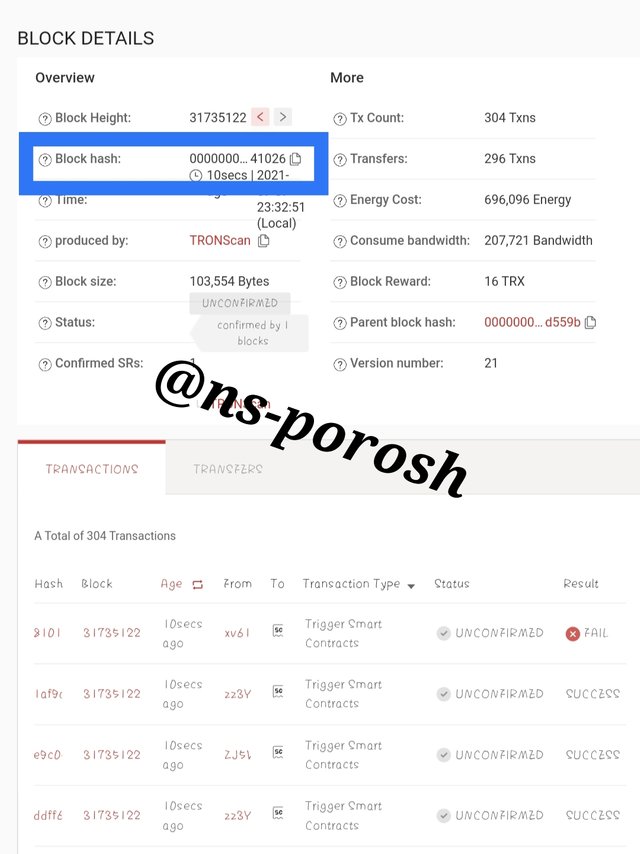
- The block hashtag was- 0000000001e43d52b7f21790d5a9ca7d6cc80123855d1430d073995b60841026
Step-7
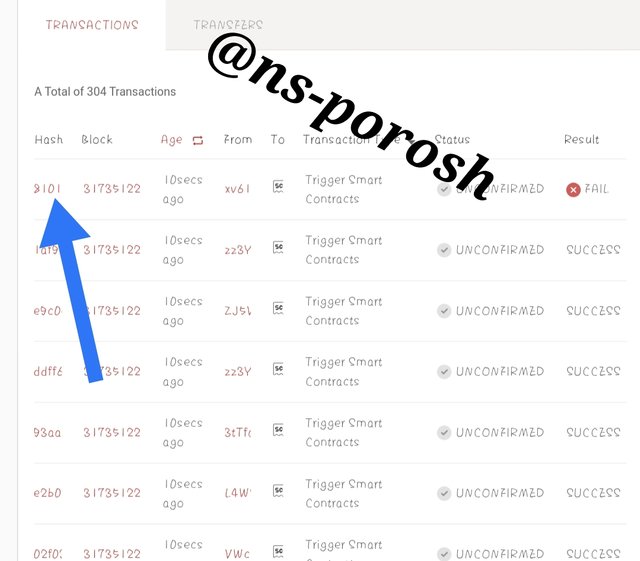
- Next you need to scroll down to verify the hash of the transaction. Scroll down to see the transaction.Then click on the height of the block to verify the hash of the transaction and review the hash of the transaction to see the details of the transaction.
Step-8
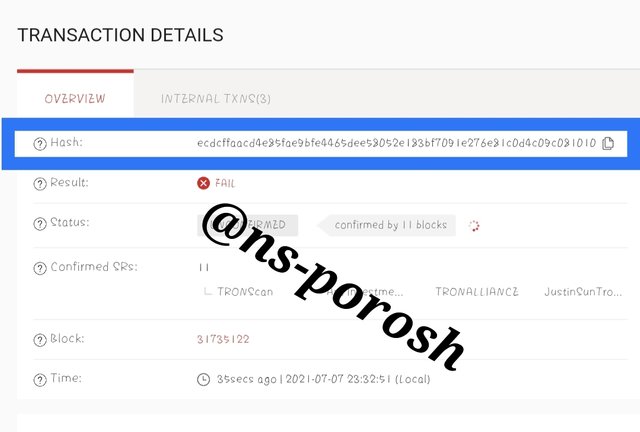
- The hash of the transaction is: -ecdcffaacd4e85fae9bfe4465dee58052e183bf7091e276e81c0d4c09c081010
Using etherscan to verify the hash of the last block and the hash of that transaction.
Step-1
- First enter this Link .
Step-2
- Then proceed by clicking the three parallel lines at the top right of the screen.
Step-3
- After clicking on the three parallel lines, click on the blockchain from the base of how many options will come.
Step-4
- Next click on the View Block option.
Step-5
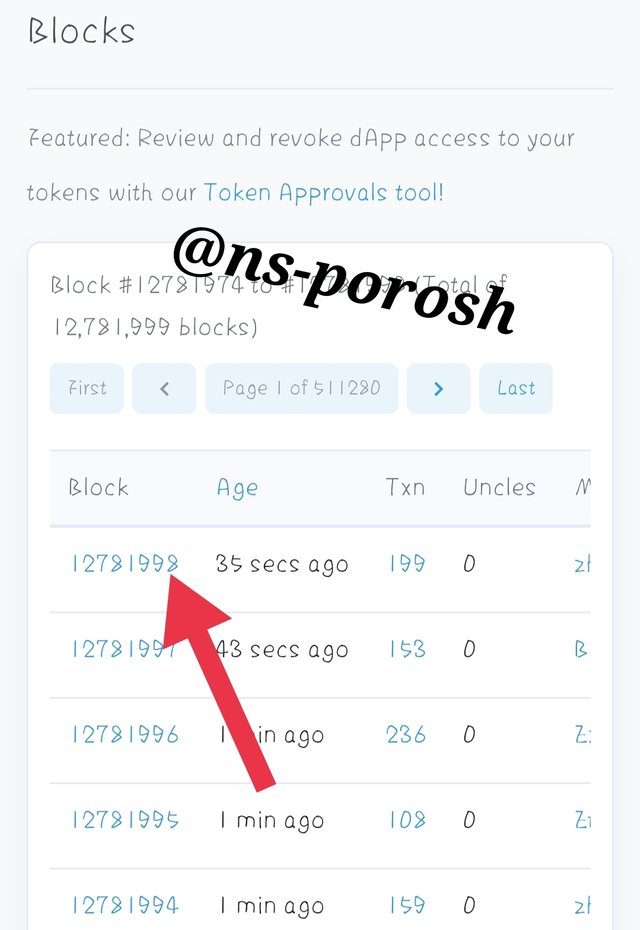
- Then you will see numerous blocks. The last block can be seen on # 12781998. Then click on the height of the block and scroll down to see the hash of the block.
Step-6
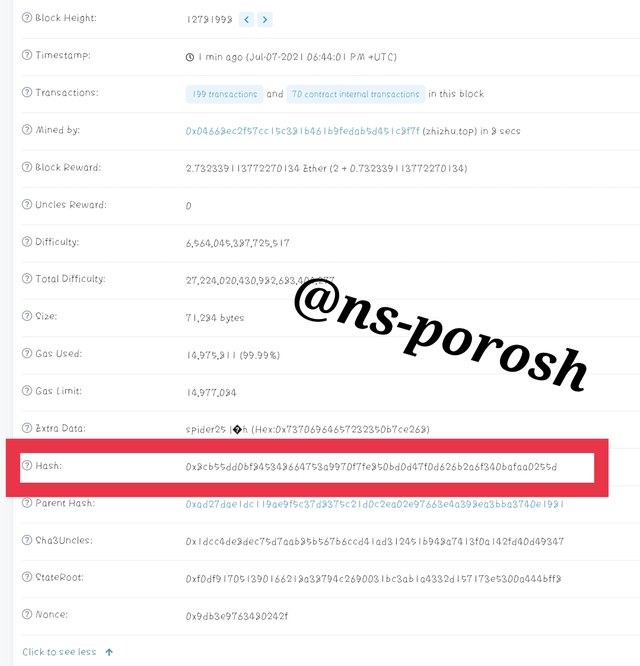
The block hash was -0x8cb55dd0bf845348664753a9970f7fe850bd0d47f0d626b2a6f340bafaa0255d
Step-7
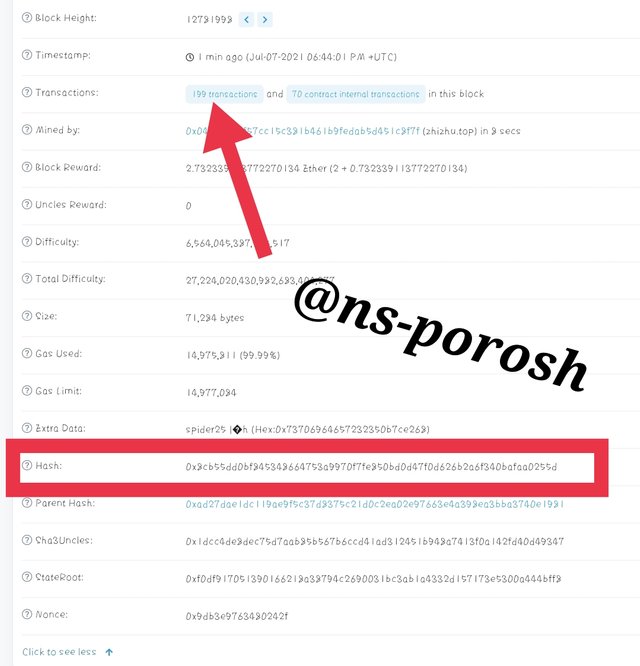
- You will then need to click on Transactions to see the latest block transactions. There are two transactions in this block. One is 199 transactions and the other is 70 contract internal transactions. I clicked the first transaction.
Step-7
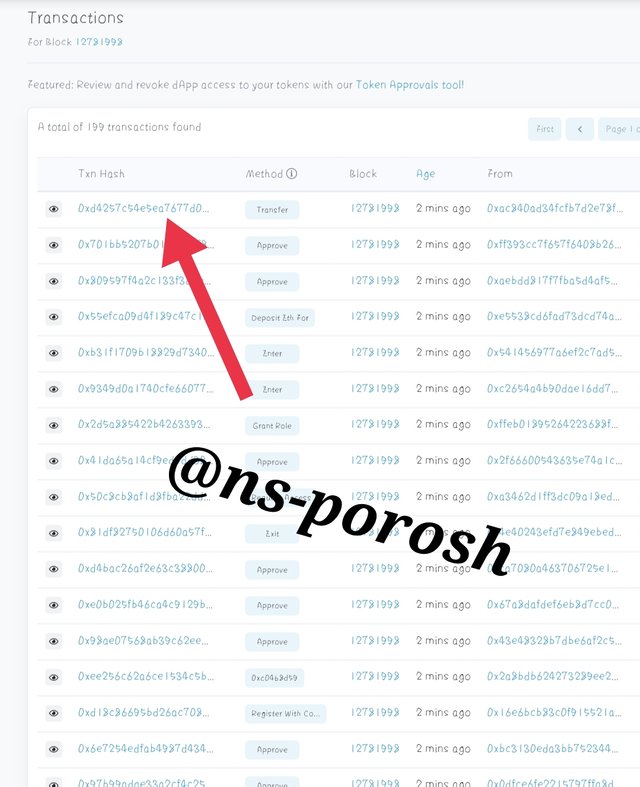
- Then click on the height of the block to verify the hash of the transaction and review the hash of the transaction to see the details of the transaction.
Step-8
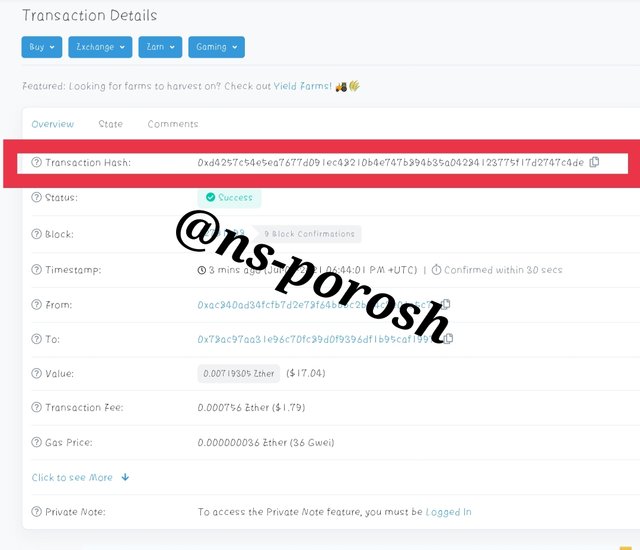
- The hash of the transaction is -0xd4257c54e5ea7677d091ec48210b4e747b894b35a04284123775f17d2747c4de
3:-Generate the hash using SHA-256 , from the word CryptoAcademy and from cryptoacademy. Screenshot required. Do you see any difference between the two words? Explain.
I will create a SHA-256 hash from the word CryproAcademy and cryptoacademy by entering this link Link . As shown in the screenshot below:
I got the following hash of CryproAcademy using SHA-256.As shown in the screenshot below:
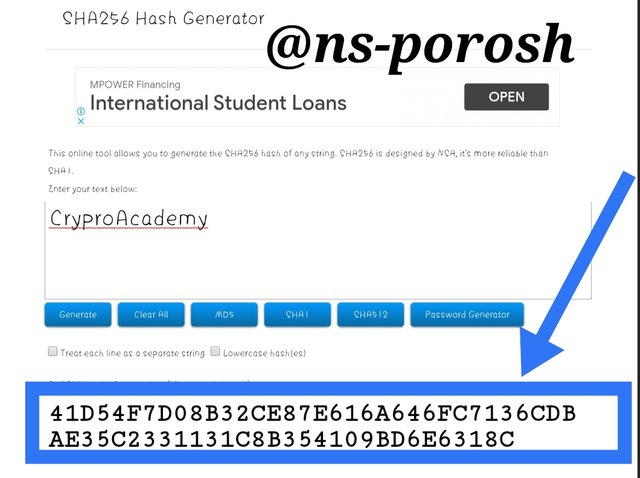
I got the following hash of cryptoacademy using SHA-256. As shown in the screenshot below:
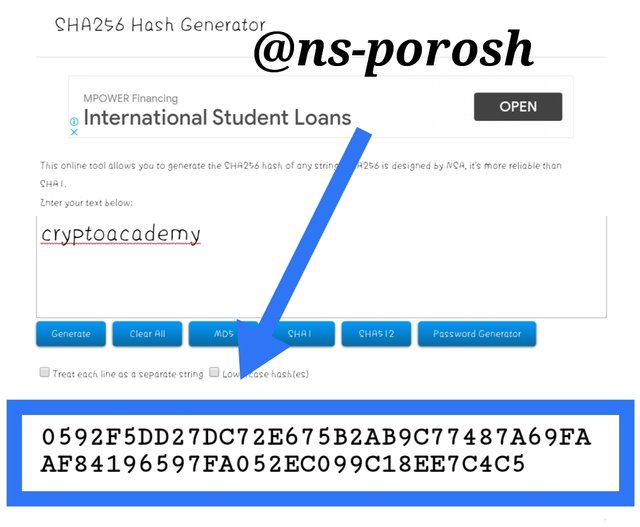
From the screenshots above we can see that the two hashes are completely different. The word CryptoAcademy has two uppercase letters. On the other hand, all the letters in the word cryptoacademy have lowercase hash algorithms. The hash of two different words cannot be the same because of the resistance of the hash collision.
4:-In your own words explain the difference between hash and cryptography.
CRYPTOGRAPHY
The main goal of cryptography is to preserve information strictly so that the beneficiaries do not change any of the information. It strictly protects sensitive data transfers and transactions. Originally those who invented cryptocurrency invented this powerful cryptography through engineering computers and advanced mathematical principles. So that the use of cryptography codes ensures that any important information is sufficiently encrypted and also ensures that important information cannot be hacked by third parties. The meaning of these codes is revealed only to those who are approved by the data foundations. This means that only the sender and receiver can understand these codes and the information through them.
| HASH | CRYPTOGRAPHY |
|---|---|
| A hash is a cryptography function that has a certain length. | All cryptography is a hash function. Which has no fixed length. This adds additional information to the blockchain which increases the length. |
| The hash function does not require the use of a key to operate, and its output length must be at least 80 bits. | Two types of keys are required for the cryptography function to work, one is the public key and the other is the private key |
| The hash function remains separate, meaning that no one can find two different inputs of the same hash output. | A cryptographic is basically a store of data and information based on security patterns and strictly warns against any third party interfering in any way. |
| It is impossible to recover encoded data after converting input data into output content. | Cryptography converts all input data to encrypted and maintains confidentiality by ensuring that the information is encrypted. |
| If any information is given by hash function, that information cannot be duplicated. For this the hash function is used to store data in the blockchain and the stored data helps to increase security. | Cryptography is the transfer of sensitive data to a blockchain and protects transactions. The keys to cryptography encodings can be retrieved by data. |
Conclusion
The importance of hash and cryptography in the world of cryptocurrency is immense. A hash is a cryptography one-way function. Which converts an input data into a unique length of output data that is irreversible. That means two inputs are unable to generate the same hash output. Both hash and cryptography are important in blockchain technology because both hash and cryptography encode with data protection. From this lecture I gained a lot of knowledge about hash and cryptography. I also learned to verify the hash of the last block and the hash of the last transaction using Tronscan and Etherscan.Thank you very much Sir @pelon for this beautiful lesson.

En la pregunta 3 hay una equivocación con la palabra CryptoAcademy, cambias la t por r. Generando un error en el código.
Buen trabajo, felicitaciones.
Recomendaciones:
Debes leer con detenimiento y responder minuciosamente, para evitar caer en errores, que se pueden evitar.
Calificación: 8.3
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit