Hello everyone. What's up these days?
Hopefully, all of you will be good and happy with the grace of Almighty God. Today I am very much excited as this is my first entry in the 3rd season of Steemit Crypto Academy.
I am going to make a homework post for dear sir @pelon53. I have read the whole of the lecture post. The lecture was very interesting and let's start our homework.
Introduction
Before starting the answers to the questions it is compulsory to know about the Hash and Cryptography. So, first of all, I will discuss the concept of Hash. Hash Functions or simply the Hash is the combination of the alphanumerical values that are used to store data or information in blockchain technology. Hash is a developed item in blockchain technology. In the blockchains, all the information of the working of the blockchain and the transactions made on the blockchain are stored in the form of Hash. The whole of the information of a transaction like the sender details, the receiver details, the value involved in the transaction, the time is taken for the transaction and the time on which the transaction is made, all of this information is stored in the form of a combination of alphabets and numbers called as Hash. One can easily access the whole of the information of the transaction simply from these Hash.
Cryptography is a technique in which the data of the users of the blockchain is stored and protected. The sender and the receivers of the data have only access to that data. There is no involvement of the third party in this transfer of data. The data. Cryptography is the real technique or the super hand behind the encrypted messages that are sent in a blockchain from one place to the other. These data and the messages are hidden for the third parties but are only visible to the senders and the receivers of the data. That's all done with the involvement of cryptography in blockchain technology.

Question#01
Resistance to Collision:
The Resistance-Collision is actually a characteristic of the Hash functions in a particular blockchain. In the cryptographic hash functions, the inputs are provided in the form of data or information and the system generates a Hash for the provided data. There will be different Hash outputs for different data and it is impossible that a similar Hash output is generated in response to two or more different inputs. A Hash function is said to be Collision-Resistance if one will find difficulty in distinguishing between the inputs of that Hash.
The Resistance-Collision technique is developed to make the hash functions more secure and safe. Suppose, if someone tries to attack a collision hash then he will get two different outputs by applying a hash at the same inputs. This thing really confused the hackers and they got surprised when they are not able to derive their desired output. So, such types of hash functions are said to be that they possess the Resistance to Collision property of the hash function.
The newly developing blockchains are trying their best to utilize the Collision-Resistance property of the hash functions to make sure their security and to increase the safety of the data stored in the blocks. It is said that MD5, SHA-1, and SHA-2 are proved to be very efficient and secure hash functions that utilize a huge collection of time to break their security using supercomputers.
Resistance to Preimage:
Another characteristic of the hash function is the Preimage-Resistance hash. It is a property of a hash function in which the derivation of the matching input from an output hash becomes impossible for hackers. The hash function that posses the preimage property become computational impossible for the hackers to alter the input as they are not able to seek access to the input of that hash function.
There are further two conditions in the preimage hash functions. First Preimage Hash means that it is impossible to get the input that generates that hash. This thing increases the security and safety of the data that is stored in the form of input in that hash function. Second Preimage Hash means that it is impossible for the attackers to get the identical output hash functions from the identical inputs.

Question#02
As we have discussed the hash function and its properties in the above sections. So, now I am going to discuss the method to verify the hash of the last block and the hash of the transaction by exploring the Tronscan and Etherscan.
Verification of hash on Tronscan:
- First of all, open the official website of Tron blockchain https://tronscan.org/#/ and locate the Blocks and Transactions menus, as mentioned below.
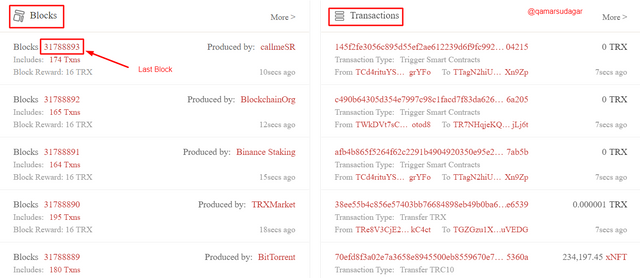
- Now click on the last block that you will see in the blocks menu. In my case, it is 31788893. Click on the last block and a new page will appear in front of you as below.
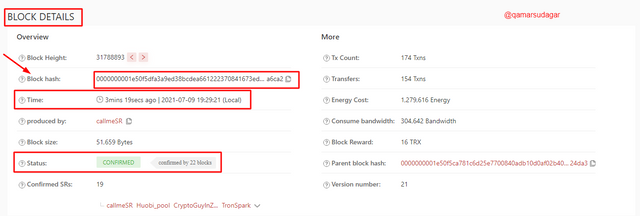
This page contains the Details of the block including the Block Height, Block Hash, Time, Producers, Block Size, Status, etc. But we needed the hash of the block. The hash of this block provided on this page is: 0000000001e50f5dfa3a9ed38bcdea661222370841673ed6d4745258ae8a6ca2
Now, scroll down the page and you will find the transactions menu, as shown in the screenshot below.
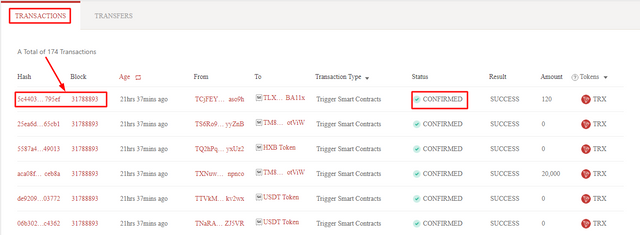
- By clicking on it, you will see a new page containing the Transaction Details as shown in the below screenshot.
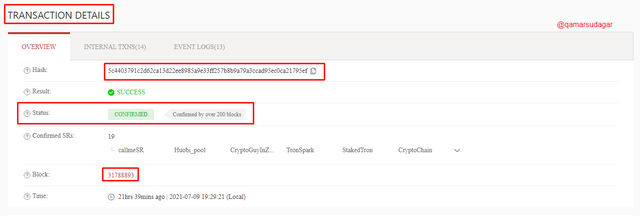
- As you can see in the above screenshot that the transaction has been verified. And the transaction hash which I have found from this page is 5c4403791c2d62ca13d22ee8985a9e33ff257b8b9a79a3ccad95ec0ca21795ef .
Verification of hash on Etherscan:
Now, I am going to discuss the method to verify the hash function on the Etherscan. So, let's follow these steps.
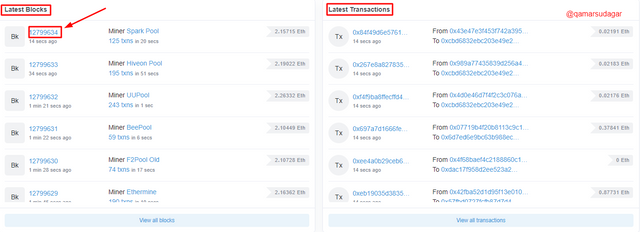
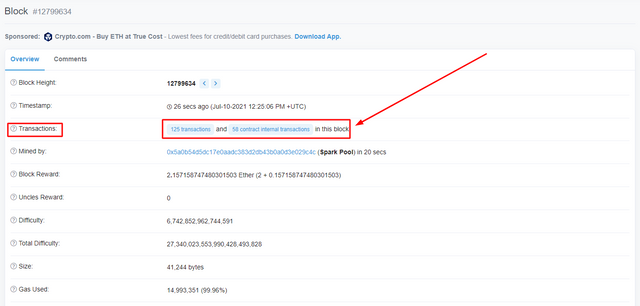
- First of all open the official website of Etherscan, https://etherscan.io/. In the Latest Blocks and Latest Transactions section, click on the latest block which is 12799634 in my case. As shown in the screenshot below.
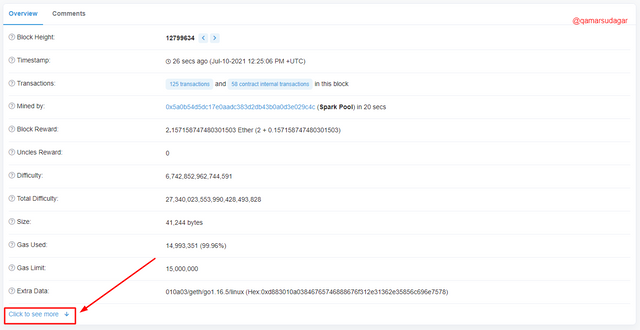
- By clicking on it, you will see a new page containing the details about that block. And at the bottom line, you have to click on the Click to see more option as mentioned here.
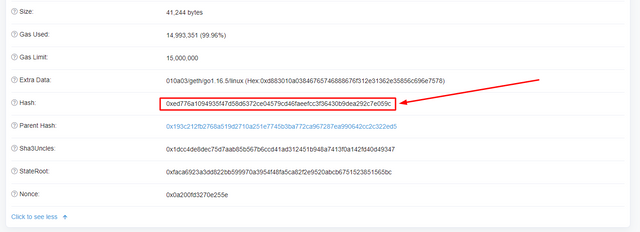
- By clicking on it, you will be able to see the Hash of the block. In my case it is 0xed776a1094935f47d58d6372ce04579cd46faeefcc3f36430b9dea292c7e059c
- Now, click on the transactions option in the Overview menu of the same page, as mentioned below.
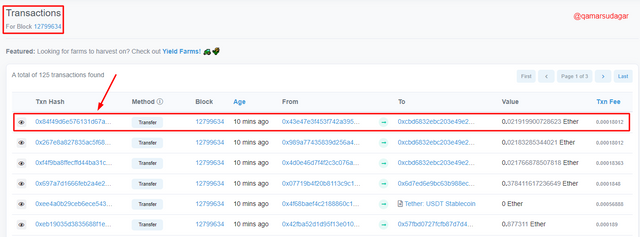
- A list of transactions will appear before you and you have to click on the latest transaction.
- By clicking on the transaction hash, you will be able to see the transaction details.
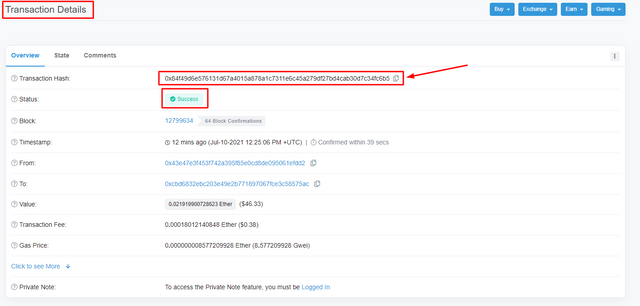
- As you can see in the above screenshot that the transaction has been verified and the hash of the transaction in my case is 0x84f49d6e576131d67a4015a878a1c7311e6c45a279df27bd4cab30d7c34fc6b5.
So, these are the methods to verify a hash in the Tronscan and in the Etherscan respectively.

Question#03
Generating SHA-256 a Hash function for different words (CryptoAcademy and cryptoacademy):
To generate a hash for any of the data or the word. First of all, you have to visit the https://passwordsgenerator.net/sha256-hash-generator website. There you will be able to see an SHA-256 Hash Generator.
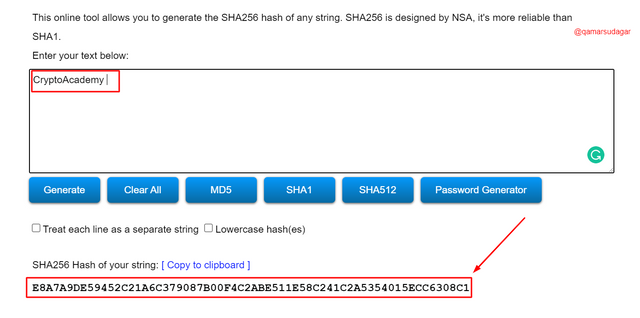
For the word 'CryptoAcademy':
- Type the word CryptoAcademy in the box and you will see the hash. The generated hash for this word is: E8A7A9DE59452C21A6C379087B00F4C2ABE511E58C241C2A5354015ECC6308C1
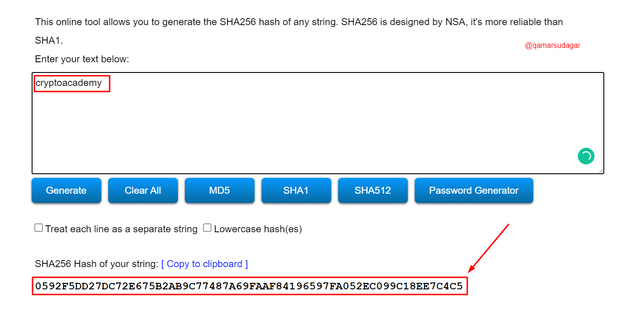
For the word 'cryptoacademy':
- Now, type the word cryptoacademy in the box and the generated hash for this word is: 0592F5DD27DC72E675B2AB9C77487A69FAAF84196597FA052EC099C18EE7C4C5
Difference Noticed:
It is noted that both of the words are actually looking the same but there is a difference in the cases of both words.
The C and A letters of the first word are in the capital while in the second word, all the letters are in a small case.
The output hashes generated for both words are entirely different from each other because the inputs are different.

Question#04
Difference between Hash and Cryptography:
As we have discussed the details about the Hash function and the Cryptography in the above sections. Now, I am going to mention the difference between these terms.
The first and the main difference between both terms is that, in the hash functioning, the output data for all of the inputs have equal length but the arrangement of the alphanumerical characters varies. While in cryptography, the length of the outputs is not fixed. The length of the output increases with the increases in the length of the input data.
Hash function is used to store data and information within the blockchains while the cryptography technique is used to hide the transferred information throughout the world.
In the case of security, the Hasg=h function is more secure and safe than cryptography as it is irreversible in nature.
Another important difference between the Hash function and Cryptography is that the hash function works in one dimension only. This means to say that the output of the hash function cannot be reversed back to get access to the initial input. While in the case of cryptography, the output can be utilized to get access to the input by the use of the right keys or the private keys.
So, these are some differences between both terms.

Final Words
The hash function is a technique that is used to store the precious data in the form of few alphanumerical characters in the blockchain. Cryptography is a technique or science to sending important or private messages or information throughout the world that are only visible to the sender and the receiver, not to all. At last, it is better to say that the hash function and cryptography play a very significant role in improving the security and privacy of the blockchains and make them hack-free.

Thanks to all of you to stop by.
Special mention and thanks to @pelon53
Best Credits: @qamarsudagar

hi, @pelon53 my homework is to be expired in one day. please check it or tell me any reason for not giving me any response
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit