HOMEWORK WEEK 8
Entire Question
1) Explain the Blockchain CryptoGraphy and mention few names which are the Blockchain Platforms (Few names of the Blockchain Platforms)?
2) Explain the Public Key CryptoGraphy.
3) Explain the Private Key CryptoGraphy.
4) Explain the Digital Signatures CryptoGraphy and what is Singing Of Transaction/Message?
5) Explain what is Symmetric and Asymmetric cryptography?
6) How Blockchain Wallets CryptoGraphy works and explains the available types of Crypto Wallets.
7) What is the Merkle trees and What its importance in blockchain?
8) Practical + Theory, do some practical research, study on Blockchain Demo: Public / Private Keys & Signing and then explain the functionality of Key, Signature, Transaction, Blockchain with proper screenshots of yours practical. (Do study well for this topic)
9) Conclusion. (The overall understanding of CryptoGraphy)


To illustrate it better, I have attached an image below using Adobe Photoshop Program.

We already know a lot about Blockchain Technology. It can be described as a wonderful creation that led to the emergence of cryptocurrencies in the world. Actually, Cryptography plays a big role in maintaining this blockchain technology. That is, with the help of this cryptography, blockchain technology has been able to transact very securely.
Here Asymmetric Cryptography is the most commonly used method in the blockchain. When we consider this Asymmetric Cryptography, there are two keys that are unique to both the sender and the recipient namely public keys and private keys. Here we use private keys to decrypt information. No one else can access our information because no one else knows the private keys. Therefore, this is the safest method in Blockchain Cryptography.

Here I've included some of the Popular Blockchain Platforms in the world. Some of them are very useful for making everyday transactions more secure, such as cryptocurrency transactions.
Openchain
Tron Blockchain
Ethereum
Stellar
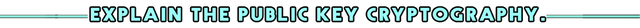

- Public Key CryptoGraphy is the main CryptoGraphy system that uses in Blockchain technology. It is also known as a form of Asymmetric cryptography. So according to this concept two types of keys are used. (Public Key and Private Key).
Then, I will explain this concept through an example.
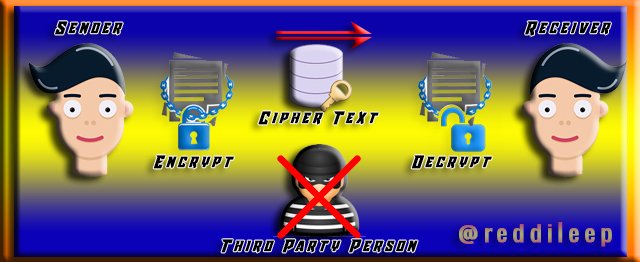
Person "A" has a private key and a public key. And also, a person "B" has a private key and a public key. Here they don't share their private keys with any other party. That is, it is kept secret and safe. But they have to share their Public keys to make any transaction between them.
Here is when "A" person sends a message to "B" person over the Internet, "A" encrypts his message from "B"'s Public key. This encrypted document is known as "Cipher Text". Once the encrypted file goes online and "B" receives it, the file is decrypted by his Private key. The most important factor here is that after encrypting this file, even the encrypted person will not be able to decrypt it.
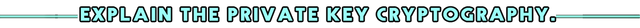
- This Private Key CryptoGraphy is another type of technology. It can be also defined as Symmetric Cryptography. But it is an older technology than Asymmetric cryptography. Here too the relevant message is encrypted and sent over the internet as a "Cipher Text". But, in this case, the encrypted code of the message must also be sent to the relevant person via the Internet or some other external communication process to decrypt the file. This key is generated as random alpha-numeric code using the successive letter replacement method. We can get an idea about that from the below-attached image.

Image Source
- So here the decrypted code has to be sent so that no other external party can get it. Otherwise, with the help of this private key, anyone can retrieve the file and steal the data.


- Digital Signature's purpose is similar to our traditional signature. But the technology of this type of signature is completely different. Actually, this Digital Signature CryptoGraphy is based on Public-key cryptography technology. So, this Digital signature is used as an authentication of the sender. So, the receiver can easily recognize the owner of the message or data with confidence.
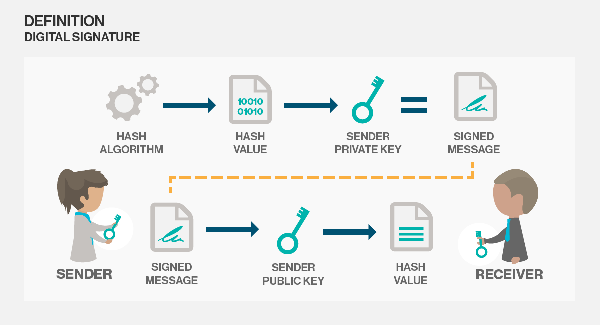
Image Source

- Basically, this process is done by Sender's party using his private key. Here he takes the file he wants to send and inserts it into the hash function. Then he can get a hash code with a fixed length. After that, he has to encrypt it using his Private key to get the Digital signature. Now this original file and Digital signature file together can be defined as a Digitally Signed Document. This is the file we need to send to the recipient
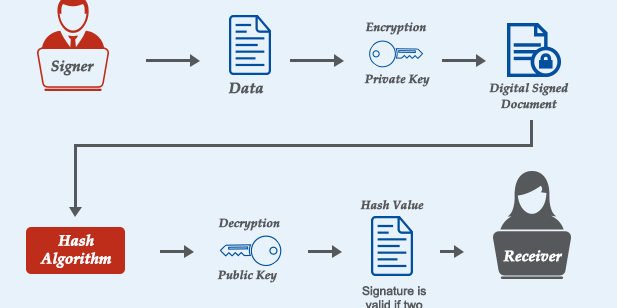
Image Source
- Once the recipient receives the file, he can divide it into two parts, the file and the signature. Now he takes this file and sends it back into the hash function to generate the hash value. At the same time, the signature is taken and is decrypted by the sender's public key. Then he gets two hash values as the hash code obtained from the file and the hash code obtained from the decrypted signature. Finally, the two values are checked to make sure they match.


This time both sender and receiver use a single key to encrypt and decrypt data. This key is generated using a private key. So, when the receiver needs to read the file, he needs the encrypted key. So, the sender should send that key using any communication method. However, here we can encrypt or decrypt data without delay. Because this key is generated as a random alpha-numeric code and its process time is very less as compared to the Asymmetric cryptography method. Below I've included an image to explain it clearly.
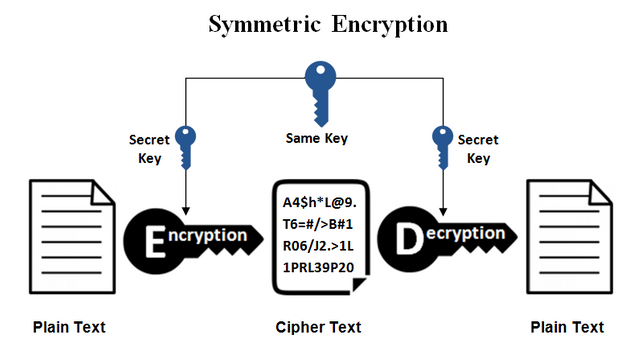
Image Source

Below I've included the Advantages and Disadvantages of Symmetric Cryptography in a Table (This Image is created by me using MS-PowerPoint Program)
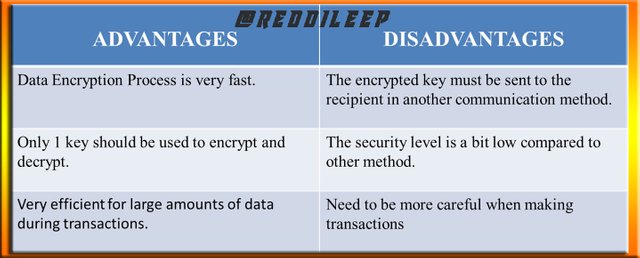
TYPES OF SYMMETRIC ENCRYPTION
Block algorithms
Stream algorithms
EXAMPLES FOR SYMMETRIC CRYPTOGRAPHY
AES
Blowfish
RC5

Asymmetric cryptography is a very secure method as compared to Symmetric cryptography. Because here we have to use 2 keys to send our document or any other data. That is the public key and the private key. We can use this public key as the address to send the data or any other transaction. In daily life, it is like our home address. So, the public key is our own key which we use to decrypt data. It is like our home Door key. Because only the owner has the key. No one will be able to access our data in any other way unless we lose this key.
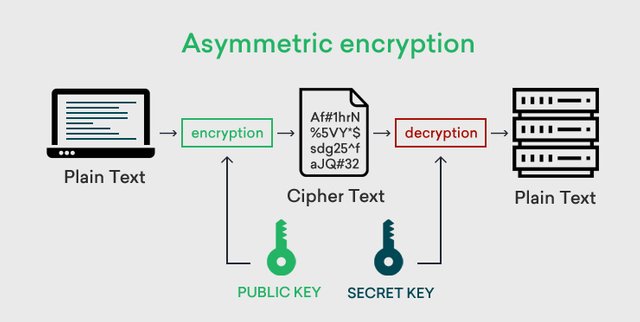
Image Source

Below I've included the Advantages and Disadvantages of Asymmetric Cryptography in a Table (This Image is created by me using MS-PowerPoint Program)
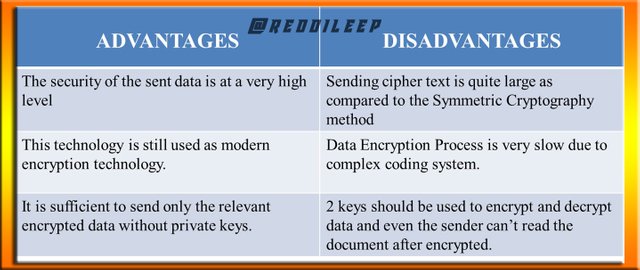
EXAMPLES FOR ASYMMETRIC CRYPTOGRAPHY
ECC
TLS/SSL protocol
RSA


Blockchain Wallets works as a Decentralized system. So, there is no single owner for these wallets. Therefore, it is automatically generating sensitive keys to keep our confidence at a high level. Only we can see our sensitive keys according to our wallets.
Furthermore, according to this CryptoGraphy system, mainly there are two keys in our wallets. That is, the private key can still be retained separately as a public key to share with others. Actually, we use these Public keys to receive coins. And also, we use Private keys to send coins from our wallets.

SOFTWARE WALLETS
- Software wallets are the common types of crypto wallets that we use mostly. We should have an internet connection to use those types of wallets. For example, online wallets can be defined as Software Wallets.
HARDWARE WALLETS
- This is another famous and very secure Crypto wallet. We can use this wallet offline. Most of the time we use our flash drive as a Hardware Wallet. So, when we need to check our transactions or update transactions, we can easily connect this Flash drive to our pc. Then we can use it as a full-featured wallet.
PAPER WALLETS
- Paper wallets are also can be defined as Cold wallets. Actually, this Wallet works as a documentary wallet that keeps records of our cryptocurrency details in peace of paper. However, we have to use this wallet carefully as it is a wallet that is created from types of paper.

We already know that Blockchain works as a data structure of many decentralized Cryptocurrencies. So, it stores transactions as Blocks. But it doesn't create blocks for every transaction by transaction. Because doing so can be expensive. The solution to this is to combine several transactions together and create one block. So when generating a hash that applies to all of these transactions, we need this Merkle tree concept. Here several hashes are combined to form a hash. We can get an idea from the below-attached image.
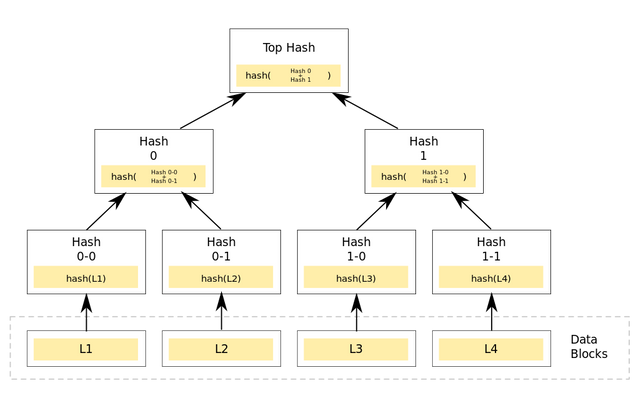
Image Source
This way we can make a few hashes up and generate a big hash and that is known as Root hash.

It helps to Summarize all the transactions and reduce the size of blocks.
It supports generating hash codes very fastly.
It reduces the overload of machine powers. So, it is good for the economy.

Here I've used Blockchain Demo to explain my theory and practical.
Like I described earlier, There are two different keys. One is Private and another one is Public key. So, below I've randomly generated both the keys to demonstrate my practical.
My Generated Public key -
04fb001797e6f54dedb9757f74afa39f7b0b7a9c84c95e1adfabead6a2f7071d375de9f45c5d8c4da14ca40eace725b59ecb4019b11141dffeb92db8a7f0bc8ac3
My Generated Private key -
55680048592152141328678707472720964759733047973027709816588377255920694045183
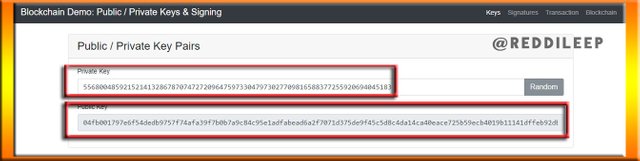
We can clearly see that, we can only change the Private key. So, the Public key is automatically generated by the system. Then let's take another example. Here I've entered 12345 as my private key.
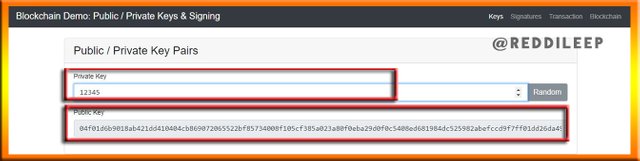
Now we can realize that the Public key is generated through our Private key.

Signature
Here I've selected https://andersbrownworth.com/ site to demonstrate it.
After getting access to this site, We can select signature from the menu section. Then we can enter our message and private key to get the signature. Check the below-attached image to get an idea.
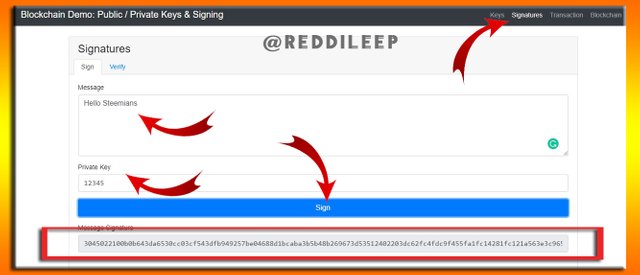
This is my Signature according to the example -
3045022100b0b643da6530cc03cf543dfb949257be04688d1bcaba3b5b48b269673d53512402203dc62fc4fdc9f455fa1fc14281fc121a563e3c965a89ecb5b3495afc22c755c3
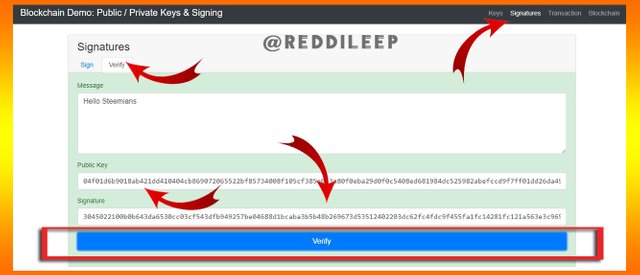
Verification of our signature -
Now we can verify our signature using Verify option. Below, I've attached an image of my verification. We can clearly see it has indicated a green sign according to the verification signal.
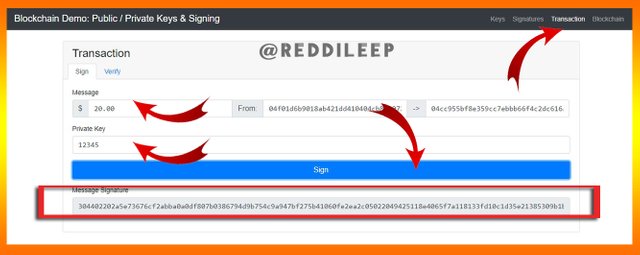
Transaction -
Finally, we can check Transaction related details through the Transaction section. Below I've demonstrated it using this demo site.
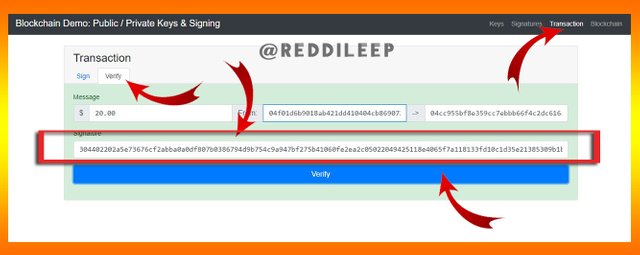
When we click on verification. We can again verify our transaction. Again we can see it has indicated green colour to verify our transaction.

Nowadays, Cryptography is very useful to our day to day activities such as online digital crypto transactions. According to this technology, every user has been able to use a very safe system to conduct any payment or anything. And also, the Blockchain method plays a significant contribution to this field.
This is all about my homework and I really appreciate Professor @stream4u for your valuable lesson and your dedication to creating a very essential lesson for us. Usually, this lesson is really important to my life as I am still trading in the cryptocurrency market.

Thank you