Hello steemians how are you? I hope you all are fit and fine in this pandemic time. Today I read season 3 lectures of the crypto academy and I found it a really interesting and creative way to increase quality content and knowledge.
Today professor @pelon53 explain a wonderful lecture on Hash Root and Merkle Tree. After complete analysis and reading now I am submitting my homework post to professor.

HOMEWORK by @rinkisaxena

Question 1:-
Explain in detail the hash root.
Answer 1:-
The speed at which any given mining machine operate is known as a hash rate. In Crypto world block are find by solving Complex computational problems that are considered to be the mathematical puzzles. All these blocks are hidden in mathematical puzzles. Every second mining machines make more than thousand of guesses to find the correct block. The first who solve will get the block and that speed is known as the hash rate.
For example if a machine is mining Bitcoin and it has rate is very high then it is considered to be more powerful and can easily find mining block on blockchain. This hash rate technology is very much useful for the cryptocurrency project that work on proof of work consensus algorithm. Hash rate is only telling about the speed of mining. Its actual SI unit is Hash/second but as the power increase the unit changes in many different units as shown below:
| SI unit | numerical value |
|---|---|
| 1H/S | 1 |
| 1KH/S | 1000 |
| 1MH/S | 1000000 |
| 1GH/S | 1000000000 |
| 1TH/S | 1000000000000 |
| 1PH/S | 1000000000000000 |
More the hair straight more will be the power of mining.
Let us see the Bitcoin network has rate to make our idea of hashrate more clear.
By 20th July 2021, hash rate of Bitcoin network is 82.92M TH/S.
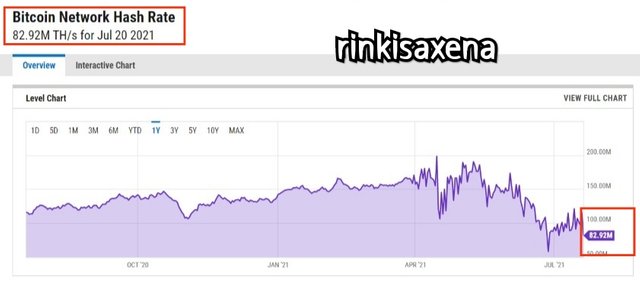
We talk about hash rate but the question arises that why it is important to see hash rate ?
So the reasons of checking hash rate is :
- provide information about the strength of the blockchain network.
- more the hash rate refers that more the number of users joining the project.
- it strength it's security.
Show the good hash rate it will make a secure and user-friendly or miner friendly environment with honest miners.
Whenever the new data is added in a new block always mining machine use hash rate that is the computational power to generate new hashes that are the alphanumeric codes that is somewhere equal to targeted hash. This process is accomplished by changing a single value that is known as nounce.
This is the brief information about hash rate.

Question 2:
Make the following Merkle Tree: Transaction (tree leaves): Steem1; Steem2; Steem3; Steem4; Steem5; Steem6; Steem7; Steem8, Made it to the Root Hash. And put every hash generated using SHA-256 , show screenshots, Tell the steps to follow to verify if Steem6 is included in the Markle Tree.
Answer 2:
To create Merkle tree of the given leaves we are using the platform https://xorbin.com/tools/sha256-hash-calculator.
Merkle tree is an essential part of block-chain Technology with which it in sure security and efficiency off the blockchain. It contain hash codes in a form of tree.
In the given question we have to create a tree E with the leaves named as :
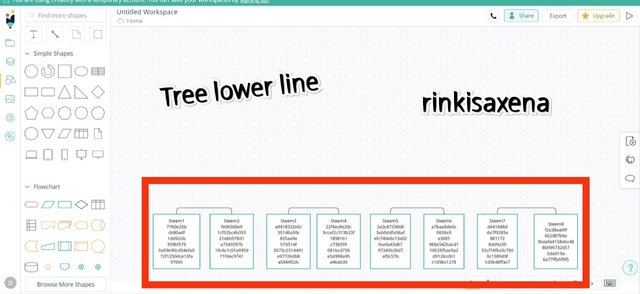
Steem1, Steem2, Steem3, Steem4, Steem5, Steem6, Steem7, Steem8
So let us create the hash of each leaf and complete our tree with hash codes.
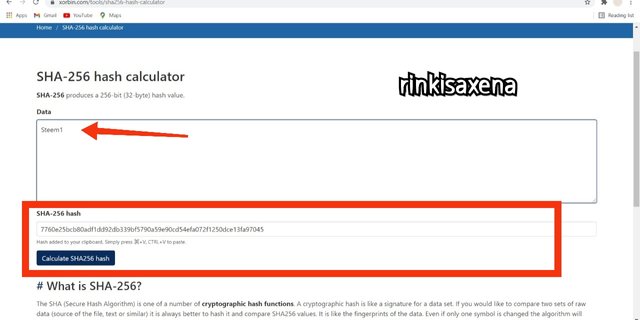
- Type Steem1 on SHA-256 and calculate hash you will get code as:
7760e25bcb80adf1dd92db339bf5790a59e90cd54efa072f1250dce13fa97045
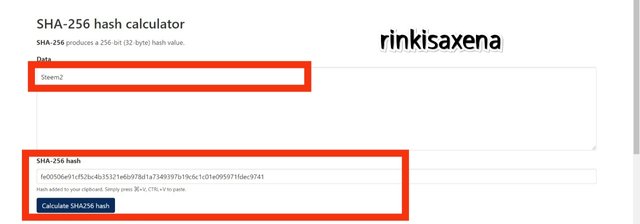
- Type Steem2 on SHA-256 and calculate hash you will get code as:
fe00506e91cf52bc4b35321e6b978d1a7349397b19c6c1c01e095971fdec9741
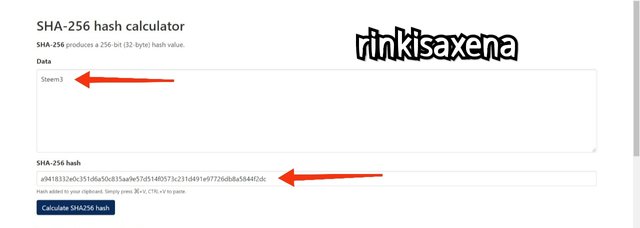
Type Steem3 on SHA-256 and calculate hash you will get code as:
a9418332e0c351d6a50c835aa9e57d514f0573c231d491e97726db8a5844f2dc
Type Steem4 on SHA-256 and calculate hash you will get code as:
22f4ec8e20c9ccaf2c313b23f18981b1c73bf39081bcd739e5d998a95a46ab30
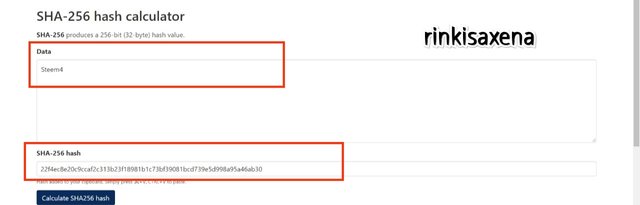
Type Steem5 on SHA-256 and calculate hash you will get code as:
2a3c87336683ab0ddfa56afefc740e6c13a02fea0a43d6797343b26d7af0c57b
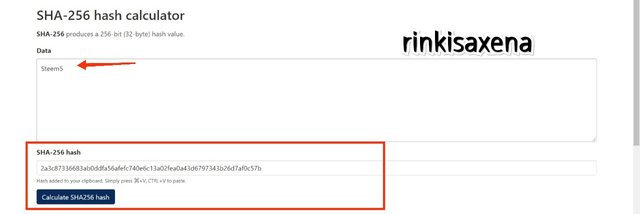
Type Steem6 on SHA-256 and calculate hash you will get code as:
a7baa6de0c0658e9e3681966e542bacd116529f5ae9a2d9126cdb1c1d5bc1278
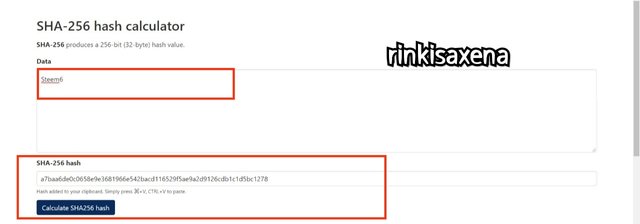
Type Steem7 on SHA-256 and calculate hash you will get code as:
d441688dda7f9285e8811728dd9a3955cf74f0a3c7600c1589d0f1d3b48ffac7
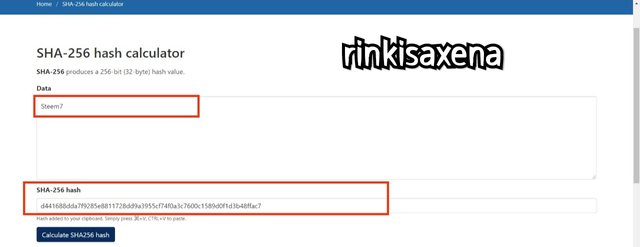
Type Steem8 on SHA-256 and calculate hash you will get code as:
f2e38ed4ff662087b6e9beafa4158ebc488b995732057bda019a6a77ffb5f9f5
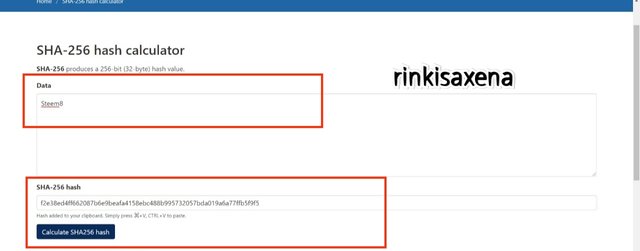
The Lower layer of merkle tree is now complete and shown below:
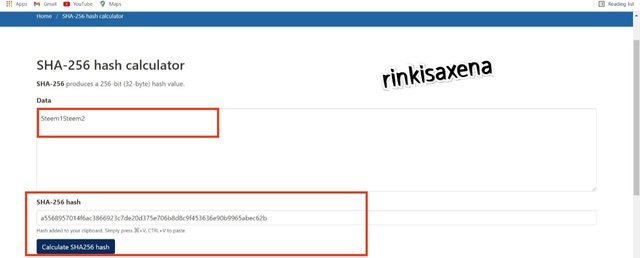
- Type Steem1Steem2 on SHA-256 and calculate hash you will get code as:
a5568957014f6ac3866923c7de20d375e706b8d8c9f453636e90b9965abec62b
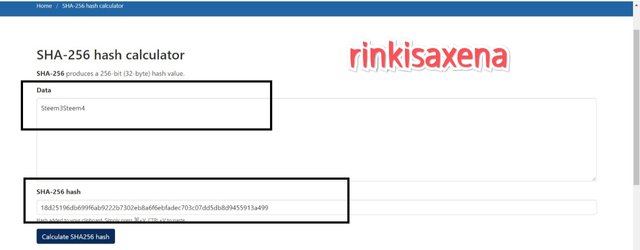
Type Steem3Steem4 on SHA-256 and calculate hash you will get code as:
18d25196db699f6ab9222b7302eb8a6f6ebfadec703c07dd5db8d9455913a499
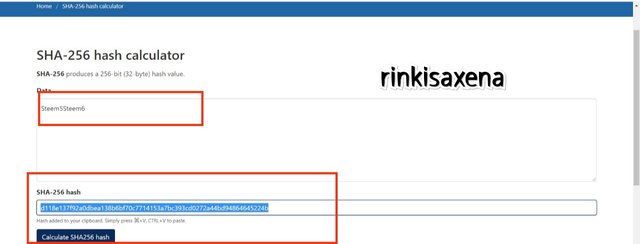
Type Steem5Steem6 on SHA-256 and calculate hash you will get code as:
d118e137f92a0dbea138b6bf70c7714153a7bc393cd0272a44bd94864645224b
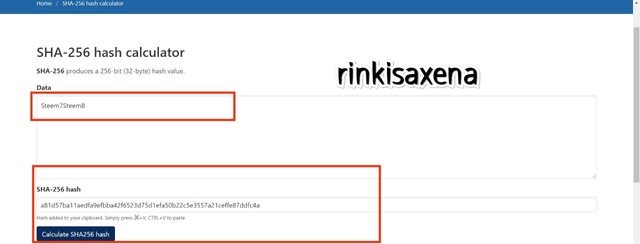
- Type Steem7Steem8 on SHA-256 and calculate hash you will get code as:
a81d57ba11aedfa9efbba42f6523d75d1efa50b22c5e3557a21ceffe87ddfc4a
The second layer of merkle tree is now complete and shown below:
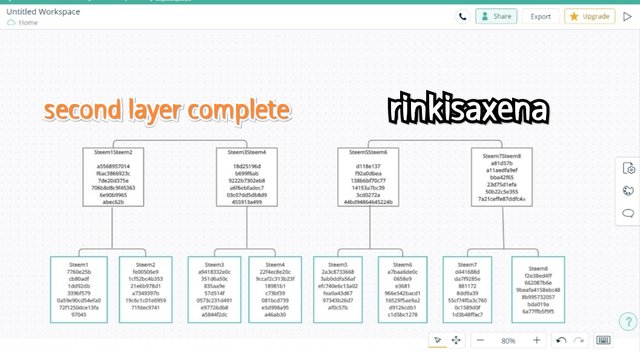
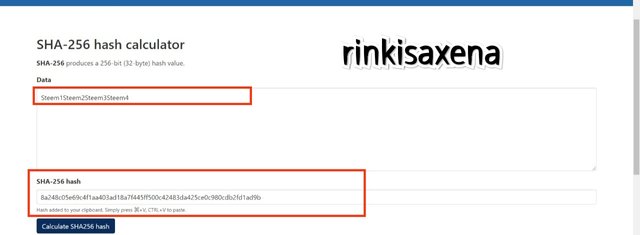
Type Steem1Steem2Steem3Steem4 on SHA-256 and calculate hash you will get code as:
8a248c05e69c4f1aa403ad18a7f445ff500c42483da425ce0c980cdb2fd1ad9b
Type Steem5Steem6Steem7Steem8 on SHA-256 and calculate hash you will get code as:
8b0935aeab3f51bfa2b0750703ee2387e2b20eb19b0d24227e180c03a851af17
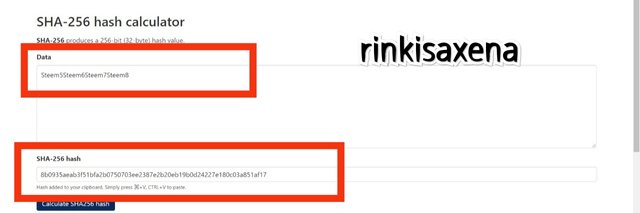
Third layer of Merkle tree is completed and shown below:
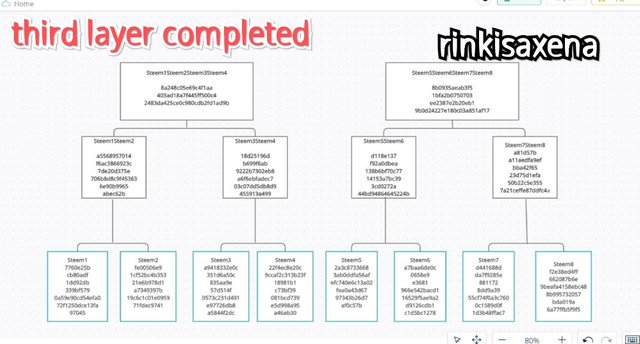
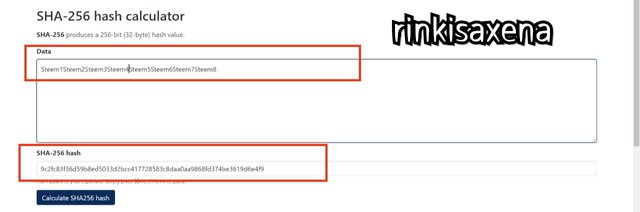
Type Steem1Steem2Steem3Steem4Steem5Steem6Steem7Steem8 on SHA-256 and calculate hash you will get code as:
9c2fc83f36d59b8ed5033d2bcc417728583c8daa0aa9868fd374be3619d6e4f9
- The final merkle tree is now complete and shown below :
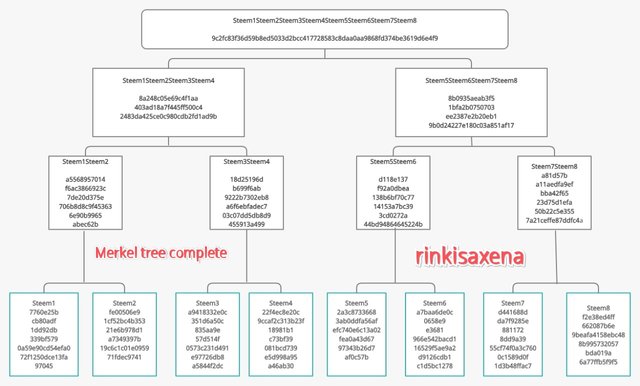
the steps to follow to verify if Steem6 is included in the Markle Tree are follow as :
For this assurance we only need to download aur check the route hash that is the longest hash. To check that we have to follow simple steps :
Calculate hash Steem5.

Then Calculate Hash Steem7Steem8, Steem1Steem2Steem3Steem4.


Now calculate Steem6.

Now combine Steem5Steem6 and calculate its hash.

Now finally Calculate the root hash that is
Steem1Steem2Steem3Steem4Steem5Steem6Steem7Steem8.

After checking the last hash it is now clear that it is a root hash of the merkle tree.
And by this we can say that Steem6 is included in the Merkle tree of Steem leaves.
This is how we have to verify the transaction in merkle tree without checking the whole tree simply download the root hash and verify every node by calculating the root hash.

Question 3:-
Using The SHA-256, You must Place each Complete Hash in The Merkle Tree Transaction (Tree Leaves): SCA1, SCA2, SCA3, SCA4, SCA5, SCA6, SCA7, SCA8. Explain each Step, Show Screenshots. If The Number of Leaves on The Tree is Odd, What should you do? Explain.
Answer 3:-
To create Merkle tree of the given leaves we are using the platform https://xorbin.com/tools/sha256-hash-calculator.
Merkle tree is an essential part of block-chain Technology with which it in sure security and efficiency off the blockchain. It contain hash codes in a form of tree.
In the given question we have to create a tree E with the leaves named as :
SCA1, SCA2, SCA3, SCA4, SCA5, SCA6, SCA7, SCA8
So let us create the hash of each leaf and complete our tree with hash codes.
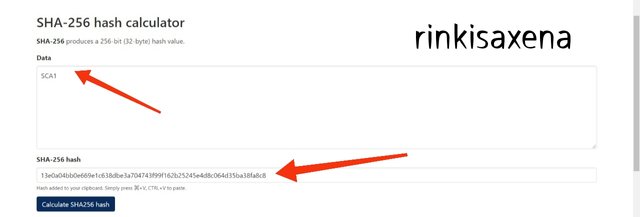
Type SCA1 on SHA-256 and calculate hash you will get code as:
13e0a04bb0e669e1c638dbe3a704743f99f162b25245e4d8c064d35ba38fa8c8
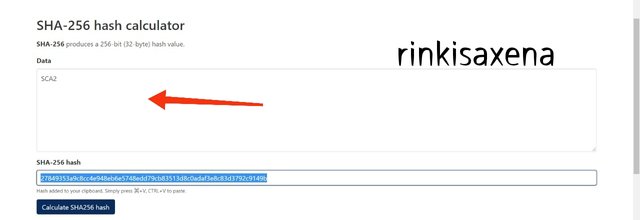
Type SCA2 on SHA-256 and calculate hash you will get code as:
27849353a9c8cc4e948eb6e5748edd79cb83513d8c0adaf3e8c83d3792c9149b
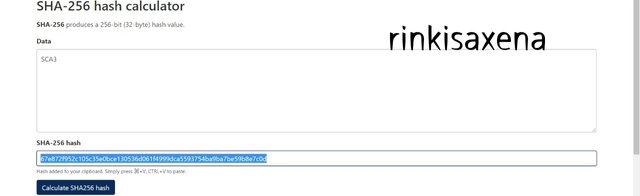
Type SCA3 on SHA-256 and calculate hash you will get code as:
67e872f952c105c35e0bce130536d061f4999dca5593754ba9ba7be59b8e7c0d
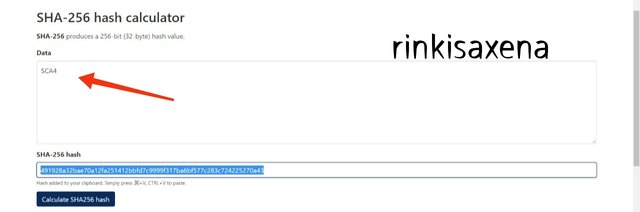
Type SCA4 on SHA-256 and calculate hash you will get code as:
491928a32bae70a12fa251412bbfd7c9999f317ba6bf577c283c724225270a43
Type SCA5 on SHA-256 and calculate hash you will get code as:
99c078c39cde7f47799e0e8691460a9f3e83e78d498ea989308fcfcc58907b19
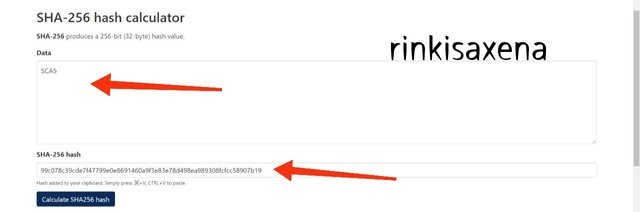
Type SCA6 on SHA-256 and calculate hash you will get code as:
7a648d887b124db14e96e23ba92783e7f26d00957c19b9b8229632c2c1873729
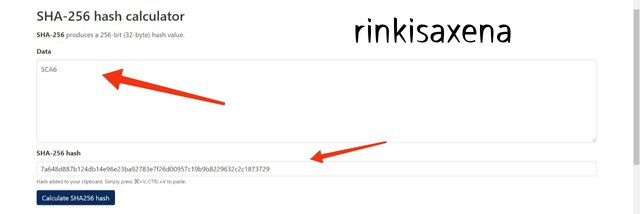
- Type SCA7 on SHA-256 and calculate hash you will get code as:
7e0bbd6ba4ba9896f9911af46b06dd2c47535f9c80b29d693fdf6b9319d0d68e
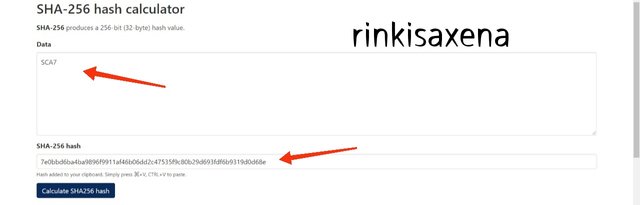
- Type SCA8 on SHA-256 and calculate hash you will get code as:
562abceeb497e1fe7ae275a883fd5ef9d92a05f5c19d82abaa0dc1571b7df3ad
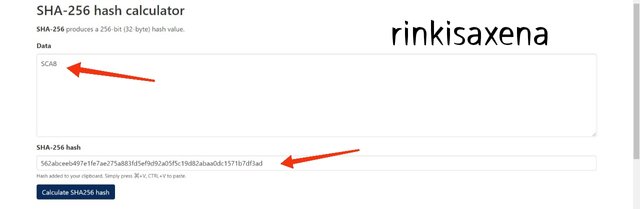
- Type SCA1SCA2 on SHA-256 and calculate hash you will get code as:
91b09bba815748166fb36413342c7e4e7e809f4bac538c0418841a4476b527ef
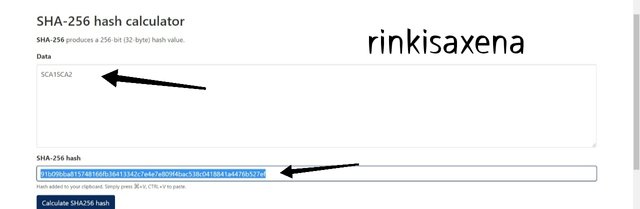
- Type SCA3SCA4 on SHA-256 and calculate hash you will get code as:
b49b48697a3acbc5e3d2e36b6ee49c44020d88e664c5c1aa7a7cf34058177379
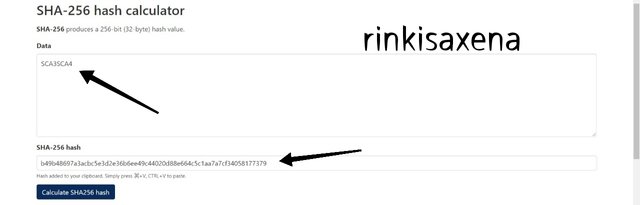
- Type SCA5SCA6 on SHA-256 and calculate hash you will get code as:
f026924cd1285ff92c2a2de9b9313027eb67273a82375c939348c887f6b52f77
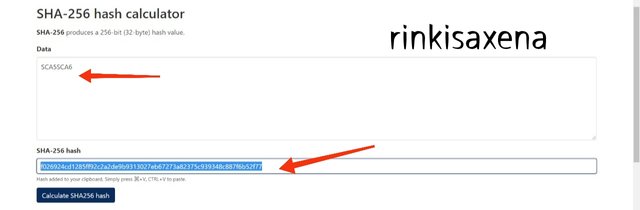
- Type SCA7SCA8 on SHA-256 and calculate hash you will get code as:
aa55ec5a6b11393b289c4b2b6916172acc2941c5c978fb1d7bf02696bab323a4
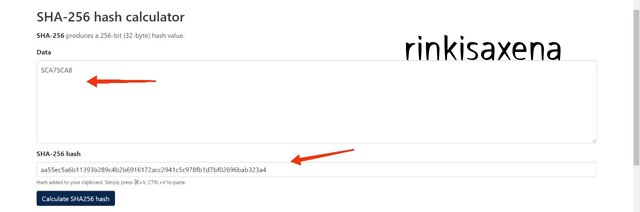
- Type SCA1SCA2SCA3SCA4 on SHA-256 and calculate hash you will get code as:
f50dc120cbf6c46923037f6d7f41d4153ecc9ab7430dda662c142db1ffe483f7
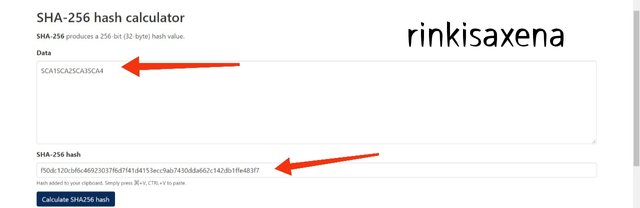
- Type SCA5SCA6SCA7SCA8 on SHA-256 and calculate hash you will get code as:
a3d8ca8494cc426abd5e1fc5fa0feae4f2b2ece4c4cecdca05e19eb66542533f
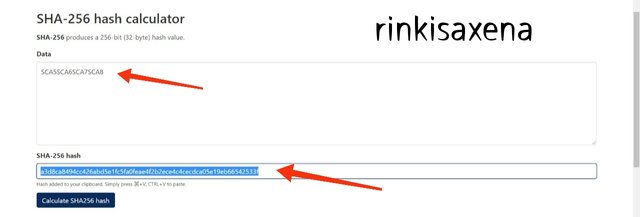
Type SCA1SCA2SCA3SCA4SCA5SCA6SCA7SCA8 on SHA-256 and calculate hash you will get code as:
cb40ca6db72dd507cf9118963f94b7740822258e74afb0fd45d89db35d24b386
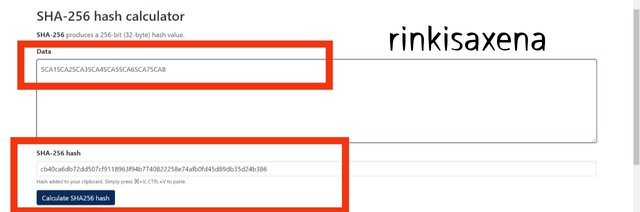
The final Merkel Tree ia shown below :
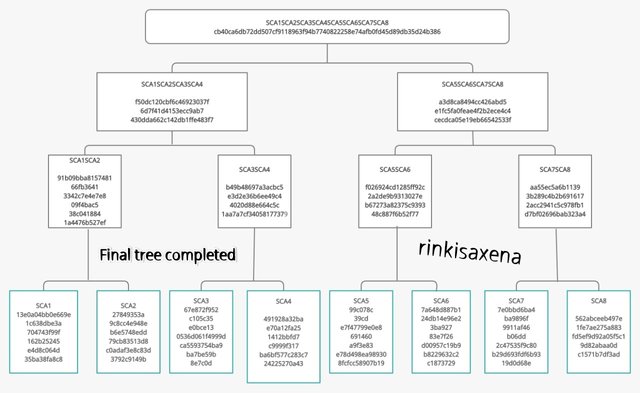
This is how we have to create the markel tree. The last line are the leave the middle are the branches and the top has is known as the root hash.
Now the question is what will happen if the number of leaves on the tree are odd in number. So in that case it will be create a duplicate pair of transaction which will complete the whole markle tree. The last transaction in odd number will get duplicated to create a even merkle tree. Let us see an example how how this will happen in odd pair of transactions.
Odd number of leaves.
Let us take an example A1,A2,A3,A4,A5,A6,A7 that means there are in total 7 transaction or 7 leaves in the Merkle tree.
Generated Hash codes are :-
Type A1 on SHA-256 and calculate hash you will get code as:
16a36e86f6fed5d465ff332511a0ce1a863b55d364b25a7cdaa25db19abf9648
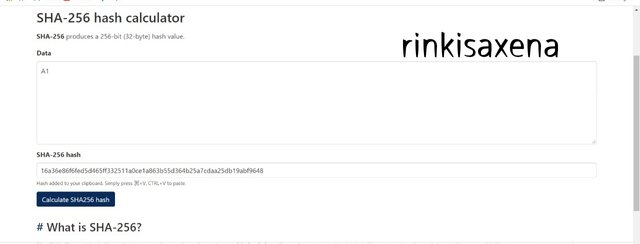
Type A2 on SHA-256 and calculate hash you will get code as:
c8361f9b468e68c86da024270e0949ce139cb704b8d7cce586681b99f3a7ea56
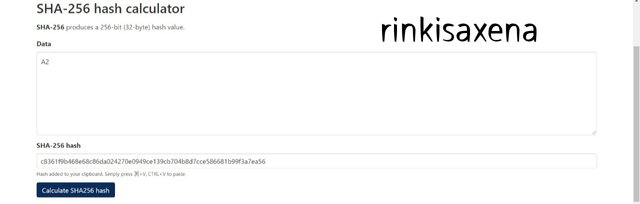
Type A3 on SHA-256 and calculate hash you will get code as:
1398b376fdcce25c5a5399367e76891e85121c010ec919cc243b1a519d95bbc6
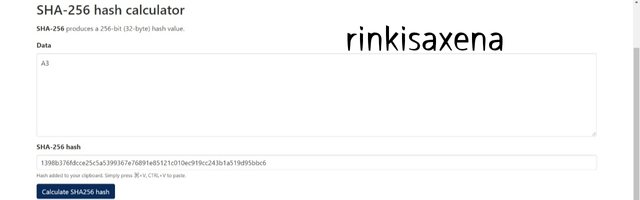
Type A4 on SHA-256 and calculate hash you will get code as:
4e808094851fc2eac7a386fc7d64677b34bda5e41d366ec4943233f9e6f2cd63
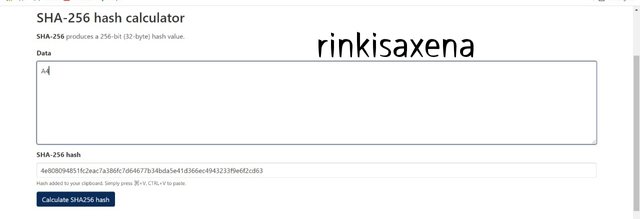
Type A5 on SHA-256 and calculate hash you will get code as:
ea644b359f0b0abde72ab7dbdc03c7d630537bdd0fd7ca1bbb99d41e7f446eea
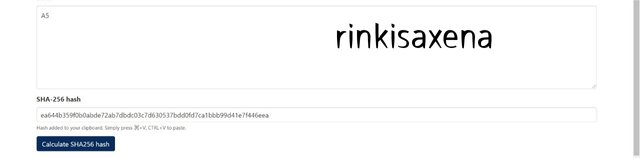
- Type A6 on SHA-256 and calculate hash you will get code as:
d94791a85f88d5f49c3cc06d5557316cf743d60149820c594f389a1b301ff021
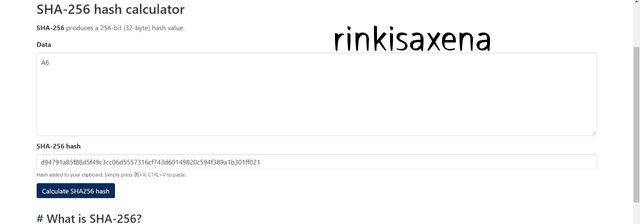
- Type A7 on SHA-256 and calculate hash you will get code as:
724f7bdf7e74a5fe64337203fb8b6ccf4adfc2919665e67a81f02e81752c1c97
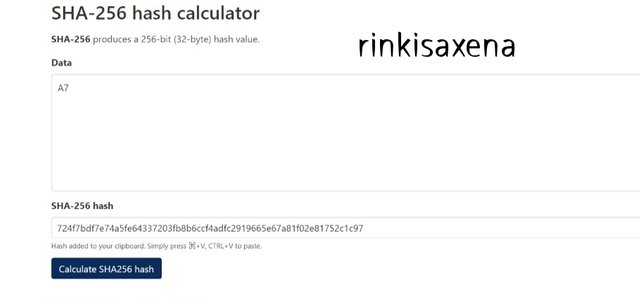
Type A1A2 on SHA-256 and calculate hash you will get code as:
715a38a9be8f0bb3228fbff6b26bf6112513c4c8607bb944c3945e2149e392de
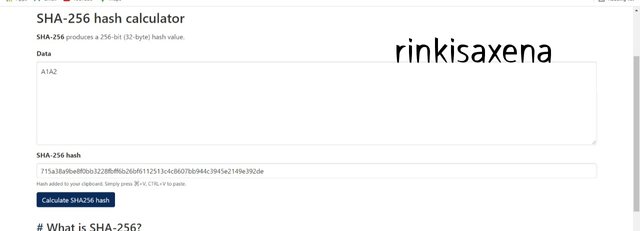
Type A3A4 on SHA-256 and calculate hash you will get code as:
3d348c69c3dbd0eaa92764e925bbb6e542a1625cf48584ad17bd7805b628977c
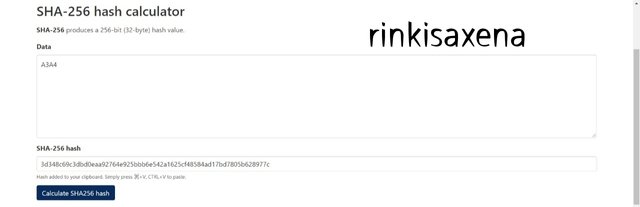
Type A5A6 on SHA-256 and calculate hash you will get code as:
880eaa1f0d20d8d6dae8a7413eae29953d3f53ad41b14ee9d60b99a22441f1b8
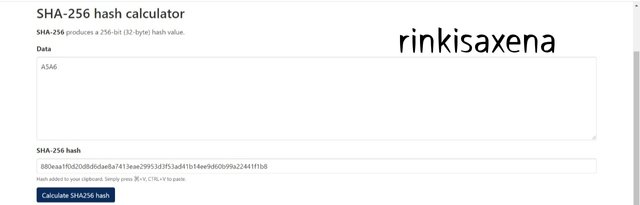
Type A7A7 on SHA-256 and calculate hash you will get code as:
b07f94e8e359222467606be7c7e25bd7ce52d4101cf588cc0671e35e7dbee31b
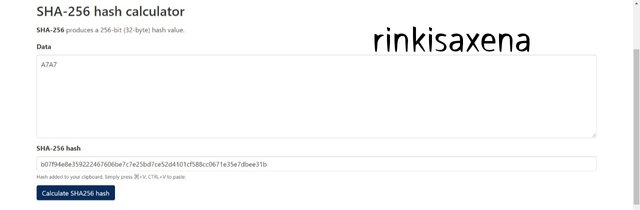
Type A1A2A3A4 on SHA-256 and calculate hash you will get code as:
9983e68d41738bcf03fd59001d4e88d7f6d84f9cc6ee03c48785f4701919719e
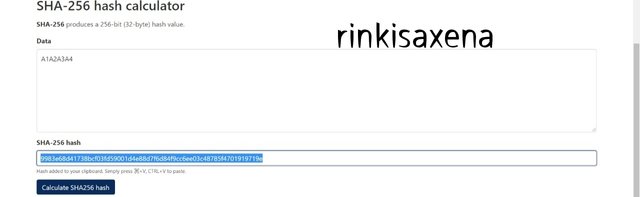
Type A5A6A7A7 on SHA-256 and calculate hash you will get code as:
075ae2f1f018c9597b88a6f4bdf8fad0bcdbee5920fa503fb1af484772906a84
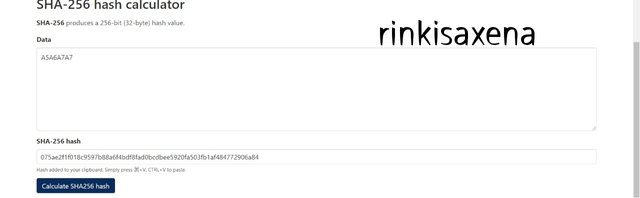
Type A1A2A3A4A5A6A7A7 on SHA-256 and calculate hash you will get code as:
6f9cc0b3e9d846512404388659f80cb12cfc6514dfffa26d10b4e2d7dd0dfb90

The final merkle tree of odd number of transactions is :
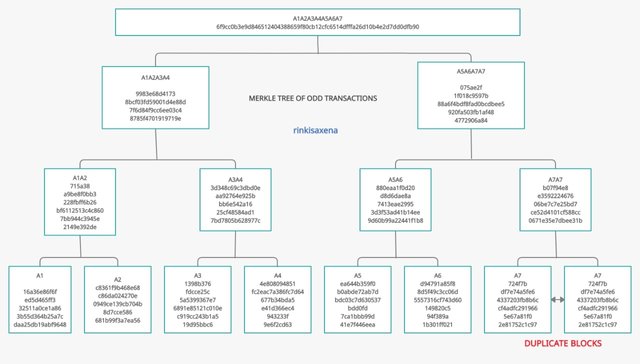
The last odd transaction create a duplicate pair name as A7.
So when there is a odd number of transaction then the last odd transaction will create a duplicate pair that we can see and because of this our Merkle tree form set of even transactions.

Conclusion
Now it's time to conclude our homework post, in this post we discuss about hash rate and merkle tree. The speed at which any given mining machine operate is known as hashrate. In Crypto world block are solved or blocks are hidden in computational Complex mathematical puzzles which one have to solve and get a new block. Hashrate improve and strengthen the blockchain network and create security.Merkle tree is an essential part of block-chain Technology with which it in sure security and efficiency off the blockchain. It contain hash codes in a form of tree. We create to merkle tree of even transactions and also verify how to see single transaction and what happen when the transaction are odd in number. When there is a odd number of transaction then a duplicate block of last order transaction will formed which create and even merkle tree.

Gracias por participar en Steemit Crypto Academy Season 3:
Espero seguir leyendo tus publicaciones.
Pregunta 1, buena información, pero faltaron datos importantes. Como por ejemplo el ataque 51.
Pregunta 2, todos los hash coinciden. Pero para la verificación del Steem, no debes usar ese hash porque es el que vas a verificar.
Pregunta 3, todos los hash coincidieron y tu respuesta de las hojas impar fue buena
Buena tarea.
Recomendaciones:
Calificación: 8.8
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thank you so much professor
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit