Hello steemian ...
This is my new post in the Steemit Crypto Academy community, on this season 5 week 6, I will be working on a homework from professor @pelon53 with the theme "Taproot and Schnorr Firms”.

we will discuss it through the homework below:

1. Explain in detail P2SH and P2PKH, the difference between the two directions.

Definition of P2SH and P2PKH
P2SH
P2SH stands for Pay To Script Hash, which is one Bitcoin address for anyone to send money to. P2SH is a bitcoin address in the form of a script where the script is a list of instructions that always accompanies each confirmed transaction output, here the script has a role to manage access to how people after using their bitcoins.
The script (which always accompanies every confirmed transaction output) is also known as the Public Key Script or the lock script or also the scriptPubKey code. At addresses with P2SH format, bitcoin recipients or account owners will generate an opening script in the form of a signature script or scriptSig. ScriptSig is a parameter in the form of data that is used to fulfill each confirmed transaction output. A scriptSig or digital signature is required to authorize transactions.
P2PKH
P2PKH stands for Pay to PubKey Hash which means this format has a system of paying from the recipient's public key to a hash, this is one of the bitcoin addresses. P2PKH is a bitcoin address that can be said to be a traditional address where the P2PKH format usually starts with the number 1. In addresses with P2PKH format, bitcoin recipients or account holders only have limited access to unlock the Pubkey Script. Then they can also receive the funds they receive from the senders by providing PubKeySig and PubKey Hashes, both of which are the scope of the PubKey Script instruction.
Difference between P2SH and P2PKH
P2SH has an address with a format that starts with the number 3, while P2PKH starts with a format that starts with the number 1. This of course distinguishes them in terms of identity.
P2SH has a lower shipping cost than P2PKH, this is because P2PKH is an old format so it is possible that the shipping size is longer and of course requires a long and expensive delivery time.
Segwitly P2PKH addresses are not compatible, although there is no problem with sending from P2PKH addresses to other addresses, it's not a problem, but it's still worrying. While P2SH addresses have received widespread support and P2SH addresses are well compatible with sending to other addresses such as bech32 and P2PKH.

2. Required to transfer 10 BTC held by 3 out of 5 multi-signature portfolios, to MTC company, for purchase of some equipment.
Use ScriptSig and ScriptPubKey to describe the steps to follow.
To transfer 10 BTC held by 3 out of 5 multi-signature portfolios, we compare 5 portfolios with the designations 1,2,3,4, and 5. Of the five portfolios, it must be ensured that they all have and hold their private keys each. Then 3 of the 5 people have to authorize the transaction because the 10 BTC to be transferred belongs to 3 of them. The transaction process that will occur will produce an unlock script, namely scriptsig and scriptPubKey.
In the transaction process, scriptsig will use the OP_CHECKMULTISIG system, the system functions to check the transaction and confirm the transaction if the transaction made is correct and meets the requirements, which in this case the condition referred to is 3 out of 5 portfolios must have signed hand. If the requirements are not met then OP_CHECKMULTISIG has the right to cancel the transaction process that occurred.
After OP_CHECKMULTISIG confirms that, then via Scriptsig the transaction will be opened and generate an SHA-256 hash. After the transaction is opened, then the next is the authority of the ScriptPubKey. Here, ScriptPubKey will lock funds until the generated SHA-256 hash matches the SHA-256 hash derived from scriptsig . if the generated SHA-256 hash matches, then the transaction will be successful and the 10 BTC funds will go to the MTC company wallet.
Explain What happens if a transaction is made using a Schnorr signature?
If transactions are made using schnorr signatures, then it is schnorr transactions that can take multiple signatures (eg 3 out of 5 signatures) on every transaction on the bitcoin network and turn them into complex signatures that are very unique and result in a feature called signature aggression. . then schnorr transactions make it more secure because it prevents anyone from being able to detect the transaction.

3. Why do you think Taproot and Schnorr companies will help with Bitcoin network privacy? Explain.
As we know that Taproot is a soft fork, which is an enhancement in the bitcoin network that serves to help increase privacy within the bitcoin network. In the bitcoin network, the taproot improvement includes three BIPs (Bitcoin Improvement Proposal), namely BIP340, BIP341, and BIP342, each of which is schnorr, taproot, and tapscipt.
Then, schnorr is a digital-based signature which is the output of the schnorr signature and schnorr is part of the taproot upgrade (ie BIP340). For now, schnorr has functions in terms of verification, key generation, and digital signatures.
The benefits of Taproot and Schnorr in helping privacy of the bitcoin network
As I said earlier, the benefit of taproot in helping the privacy of the bitcoin network is in an increase in the bitcoin network. This improvement includes a Bitcoin script that functions to fix factors related to complex transactions which in this case use complex features such as multi-signature and timelock. In addition, the Bitcoin script also functions to increase the level of privacy on the bitcoin network.
In essence, in helping the privacy of the bitcoin network, the taproot can hide every transaction process that continues to branch on the bitcoin network or in other networks such as lightning networks, smart contracts, or peer-to-peer where in this way taproot can make all branches transactions in the bitcoin network. being like a single transaction thus preventing anyone from detecting the transaction, this is one of the taproot's biggest assistive innovations in supporting the privacy of the bitcoin network.
To make privacy even better on the bitcoin network, Taproot is combined and implemented with schnorr signatures which can take multiple signatures on every transaction on the bitcoin network and turn them into complex and very unique signatures. Both can be done simultaneously whereby combining the two, will produce a feature called signature aggression.

4. Using Demo Blockchain, write exactly the following message: Schnorr Signatures, create message signature and verify the message. Then remove the first character from the message signature and check again What happened? Explain. Screenshot required.
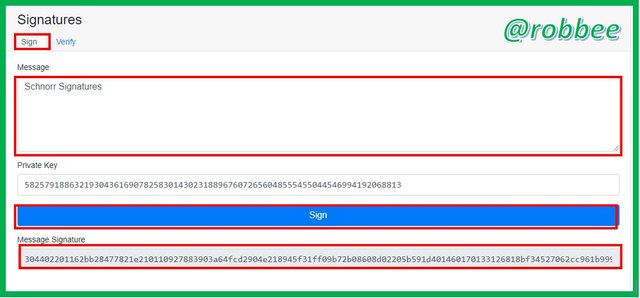
For this stage, we have to make sure to enter the Blockchain Demo, then in the sign menu, to be precise in the message column, you must write the message “Schnorr Signatures”. After entering the message, click sign then you can see the contents of the message signature, namely:
304402201162bb28477821e210110927883903a64fcd2904e218945f31ff09b72b08608d02205b591d401460170133126818bf34527062cc961b999bb1803d35ffdf05070e4a
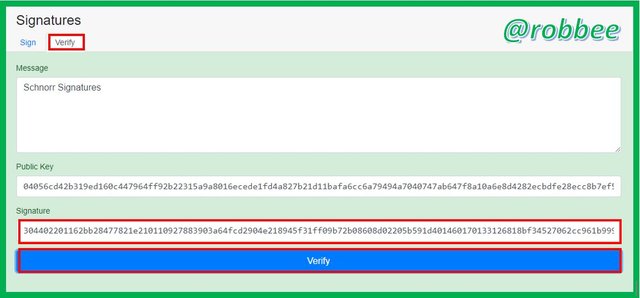
Then to verify the message, select the verify menu. In the verify menu, click verify, then the display will be green which means that the message is correct and verified.
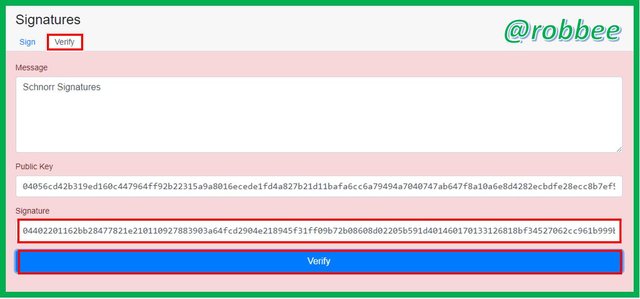
Then, like the command in question number 4, I also tried to remove the main character message signature which is the number 3 at the beginning, then the display will be red, which means that the message does not match and cannot be verified.

Conclusion
P2SH stands for Pay To Script Hash, which is a bitcoin address in the form of a script where the script is a list of recorded instructions that always accompanies every confirmed transaction output, P2PKH stands for Pay to PubKey Hash. At addresses with the P2PKH format, bitcoin recipients or account holders only have access to unlock the Pubkey Script. Then they can also spend the funds they receive from senders by providing PubKeySig and PubKey Hashes, both of which are scopes of PubKey Script instructions.
in helping the privacy of the bitcoin network, the taproot can hide every transaction process that continues to branch in the bitcoin network to prevent anyone from being able to detect these transactions. To make privacy even better on the bitcoin network, Taproot is combined and implemented with schnorr signatures which can take multiple signatures on every transaction on the bitcoin network and turn them into complex and very unique signatures. Both can be done simultaneously whereby combining the two, will produce a feature called signature aggression.
Reference
https://easycryptoinfo.com/p2sh-pay-to-script-hash/
https://academy.binance.com/id/articles/what-is-taproot-and-how-it-will-benefit-bitcoin
https://zipmex.com/id/learn/apa-itu-schnorr-signature-definisi-dan-cara-penggunaannya/