Hash is generates an output. A hush is a mathematical algorithm which transforms data into a fixed output. Hashing can be used for so different reasons.
Hashing can be used to compare to files without even opening to check the files word for word. It tells if the two documents are different from each other or the same.
Hashing can also be used to compare the quality of a file When transferred from one place to another. To confirm the transferred file is not corrupted or damaged. To ensure a quilty file we compare the hush values of both files, if they are the some we then know its an identical copy.
Characteristics of Hashes
- They are secured
- They are Irreversible
- They are unique
Hushes are secured such that you cant reverse its computation.
Question 1
Resistance To Collision
Resistance to collision is a property of hush function. Before we undertaker what resistance to collision means lets get to understand what collision is. Collision refers to when two data is inputted to generate the same output. Now Resistance to collision refers to when two input doesn't generate one output or the same code.
Lets mathematically represent X and Y as different two variables which means X is not equal to Y. But then hush X and hush Y are equal.
Resistance to Preimage
Preimage resistance is the property of a hash function which is hard to reverse. It is computational impossible to find an input in a range which matches the element of a hash output. It avoids or prevents attacks on the hash code.
Question 2
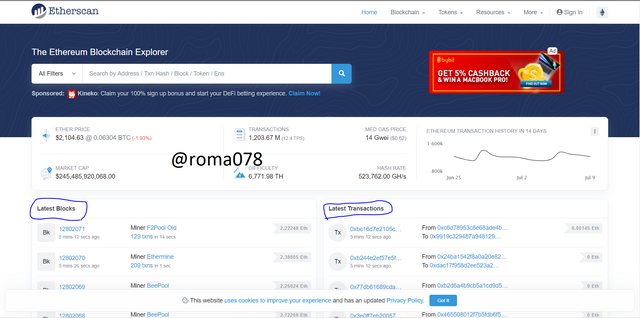
Using Etherscan
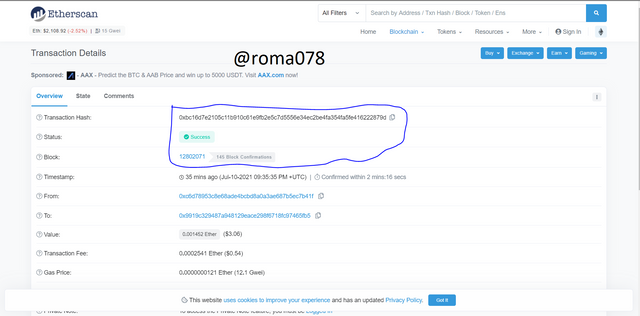
- Navigate to https://etherscan.io/ to view the latest blocks and latest transactions
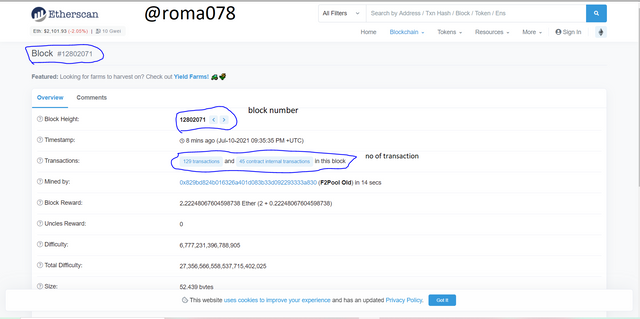
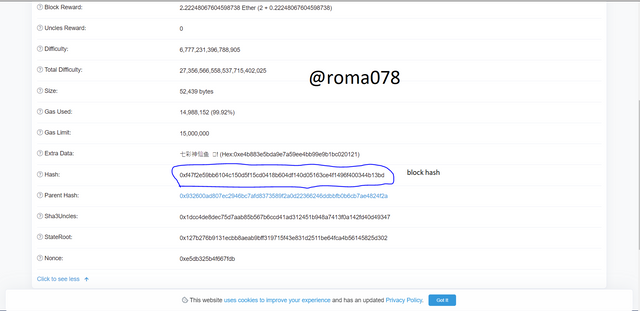
- Lets click on the first latest block to view the block height and block hash which are 12802071
and
0xf47f2e59bb6104c150d5f15cd0418b604df140d05163ce4f1496f400344b13bd respectively.
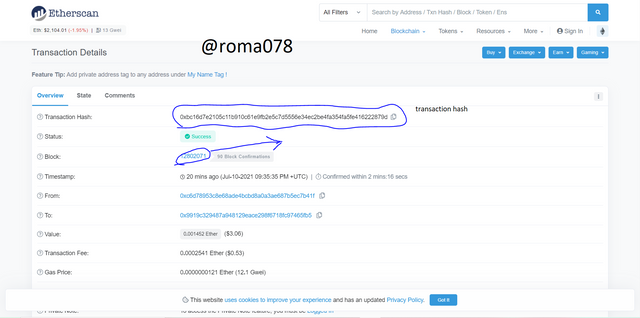
- Lets click on the first transaction to view its details
- We will find the transaction hash and its number which are 0xbc16d7e2105c11b910c61e9fb2e5c7d5556e34ec2be4fa354fa5fe416222879d and 12802071 respectively
- Lets copy the transaction hash and search to confirm. Its confirmed if it appears the same. We can see its the same
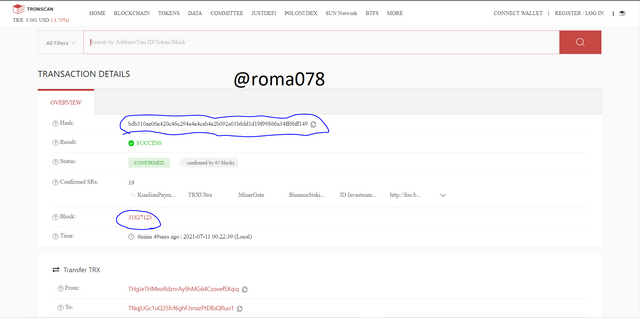
Using TronScan
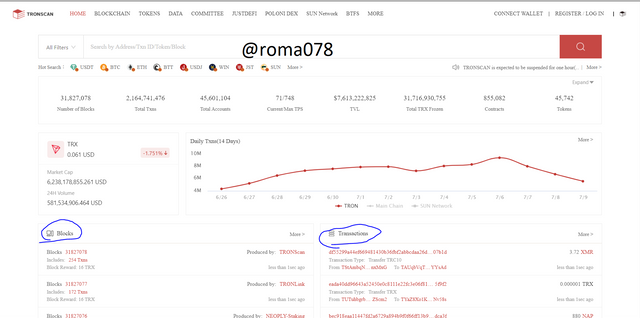
Navigate to https://tronscan.org/
We will see the latest block and transactions
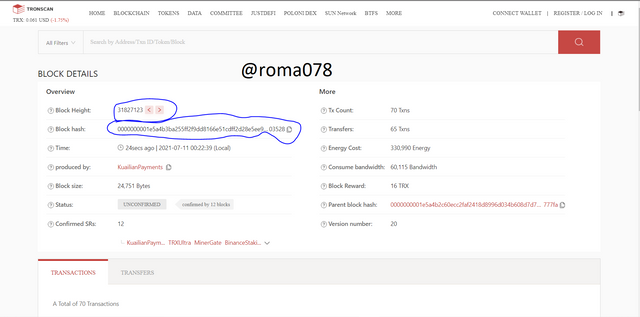
We click on the first block to view the details which we can see in the screenshot
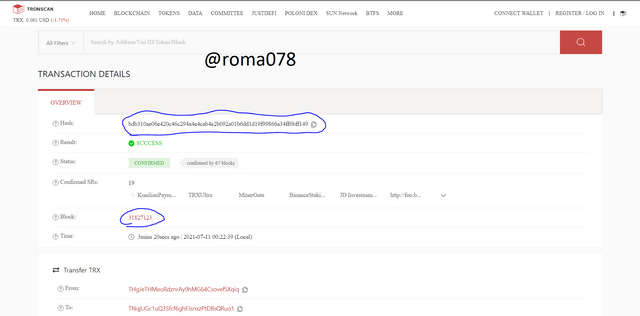
We click on the first transaction to view the details which we can see in the screenshot
Lets confirm by searching with the transaction hash. If the code matches then its confirmed
Question 3
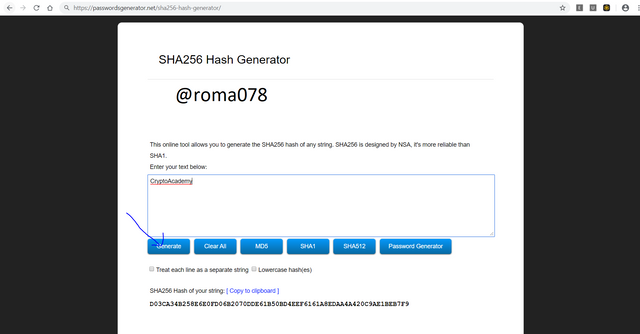
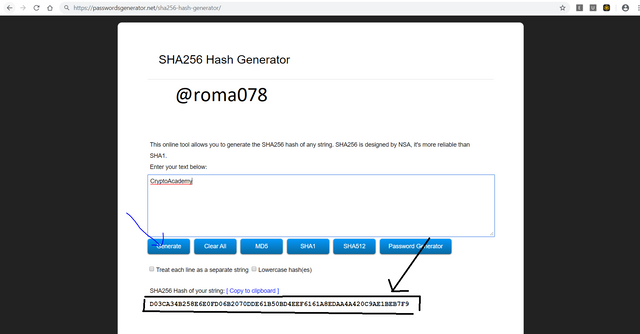
- Navigate to the site https://passwordsgenerator.net/sha256-hash-generator/ and type in the data to be converted. In my case its CryptoAcademy then we click on generate.
- We have gotten our hush key which is D03CA34B258E6E0FD06B2070DDE61B50BD4EEF6161A8EDAA4A420C9AE1BEB7F9
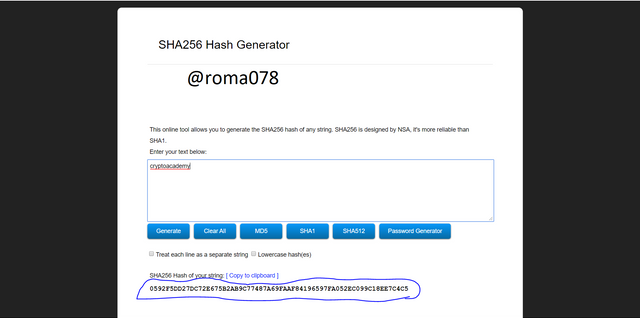
lets also generate hush key for cryptoacademy by visiting the same site
our hush key is 0592F5DD27DC72E675B2AB9C77487A69FAAF84196597FA052EC099C18EE7C4C5
OBSERVATION
We input CryptoAcademy and got generated hash key D03CA34B258E6E0FD06B2070DDE61B50BD4EEF6161A8EDAA4A420C9AE1BEB7F9 and also cryptoacademy and had our hash key 0592F5DD27DC72E675B2AB9C77487A69FAAF84196597FA052EC099C18EE7C4C5. Looking at the two hash kkeys we can see they are both diffrent from each other. This is because the words CryptoAcademy and cryptoacademy are both diffrent. CryptoAcademy has two capital letters and cryptoacademy are all small letters. This experiment is to indicate that it is case sensitive and hence it generates different hash keys
Question 4
Both Cytography and Hashing are related to each other and below here i will make some few difference between them.
| Cryptography | Hashing |
|---|---|
| It hides its meanings behind data | converts data to a fixed value |
| Keys are required | Hashes does not require any keys |
| does not have a set length of code. | has a fixed number of characters |
| its main work is to encypt and decrypt | It converts data to codes |
| It encrpt and decypt data and make sense of it | It is generated by entering data into SHA-256 input box |
| Cytography can store information of a very big data | Hashes have 64 character long |
I really enjoyed the class. i was able to learn some new stuffs from this week lecture. I did my best to work on every aspect of the assignment and im looking forward to participate in your subsequent lectures of yours.
Gracias por participar en Steemit Crypto Academy Season 3:
Espero seguir leyendo tus publicaciones.
Pregunta 1, mejorar cada concepto.
Pregunta 2, no pude observar los hash generados en tronscan.
El experimento de la pregunta 3, es para que observen la resistencia a la colisión.
Recomendaciones:
Explicar de una forma sencilla y clara.
Cuando los datos solicitados no se observen, debes copiar y pegarlo en un sitio visible para ser chequeados.
Calificación: 8.0
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit