Hello,
I hail all colleagues and professors in the Cryptoacademy. Most especially professor @pelon53 who has taught us Hash and Cryptography.
Question
1.) Explain what does the resistance to collision mean? And what does resistance to preimage mean?
A cryptographic hash function:
This is commonly referred to as a Hash and it is a computational technique that converts any random data block into a new, fixed length unique characters totally
Hash generates a set of unique alphanumeric keys with the data or file it receives. The most recent Hash generator used SHA-256, which converts files and data into 64 alphanumeric character.
Basic Hash features which makes it outstanding when it comes to security cases is why this mathematical technique was adopted.
What is collision?
Collision is the occurrence of two data inputs producing the same result, either by accident or through attack.
Resistance to Collision
It is one of the basic function of the Hash. Resistance to Collision means, two different input messages should not hash to the same output.
Hash was made in such a way that it will make it impossible for two diffrent data, or information to bring the same Hash result. This is to protect data and give quarantee to safe usage.
Resistance to Preimage
When it is computationally difficult to determine the input to any cryptographic hash result, this is known as resistance to preimage. With Resistance to Preimage users are guaranteed that input that has already gone through hashing can not be reviewed, or manipulated to give the same Hash
Second preimage resistance
Second preimage resistance is the condition that a HASH has that makes it difficult and impossible for find two matching input that will give same outpu. This function is very similar to the original attribut of Resistance to Collision.
Question
2.) Use tronscan and etherscan to verify the hash of the last block and the hash of that transaction. Screenshot is required for checking.
Tronscan
We go to the address https://tronscan.org
We go down to the section on Blocks and Transactions. Click on the last block
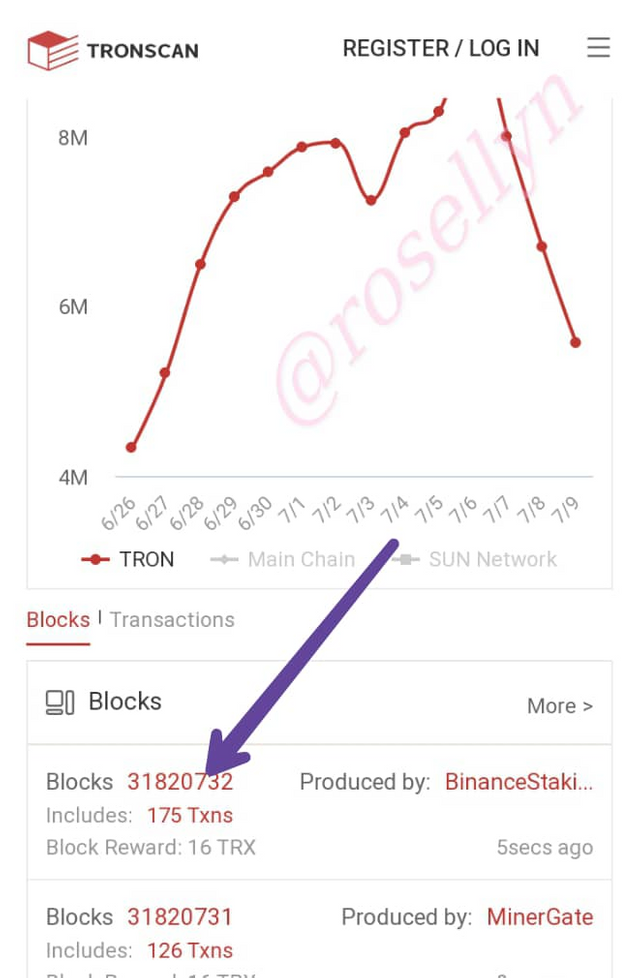
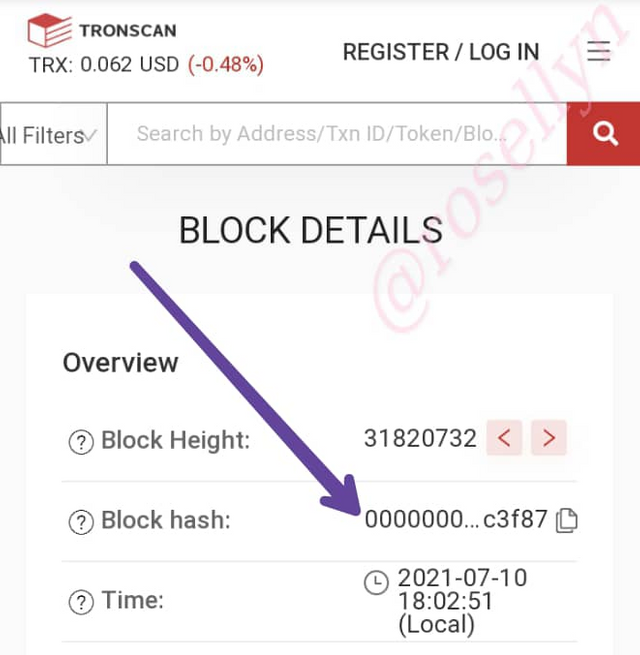
On the next page we have the Block hash: 0000000001e58bbc8f4d2f2134ca67a721b251240043389cc043cbc448fc3f87
Let verify the Last Transaction Hash now
On the same page, go down to where we have transaction
Click on the last Hash
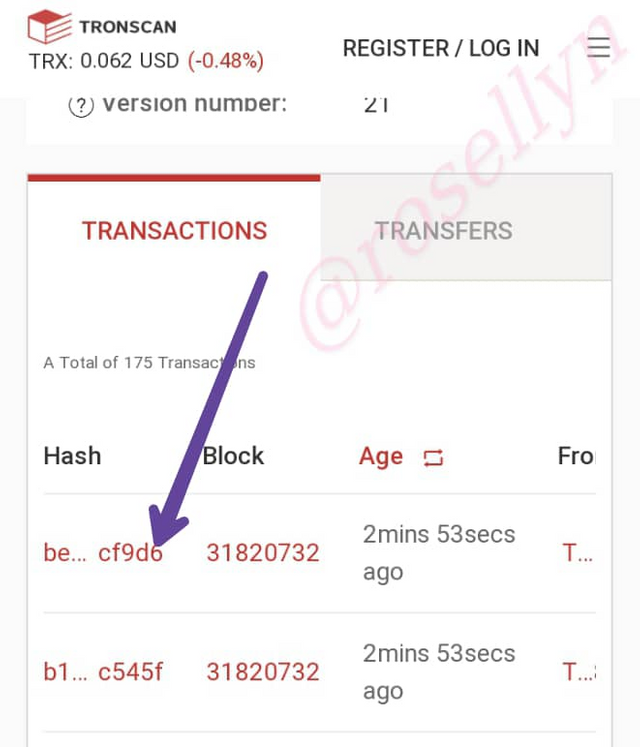
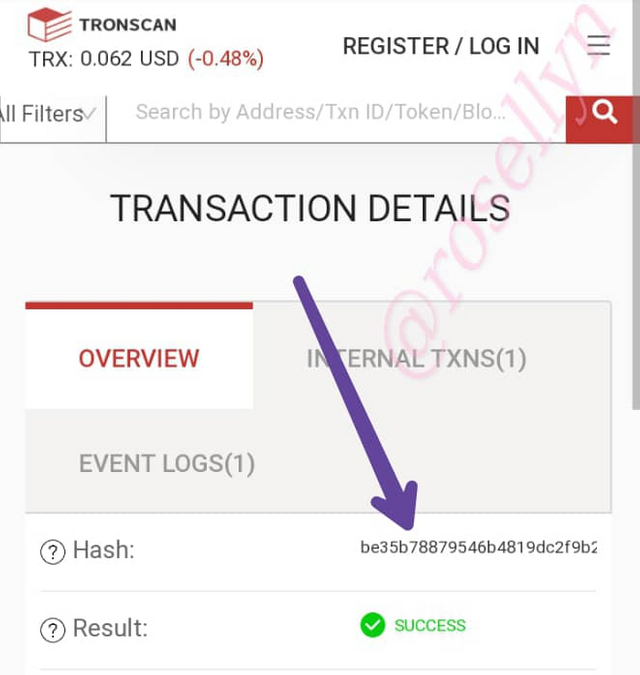
Last Transaction Hash: be35b78879546b4819dc2f9b22104fa5e1665776ff406df247bcf80c8d1cf9d6
ETHERSCAN
We go to the address https://etherscan.io/
We click on the last block number to verify its details.
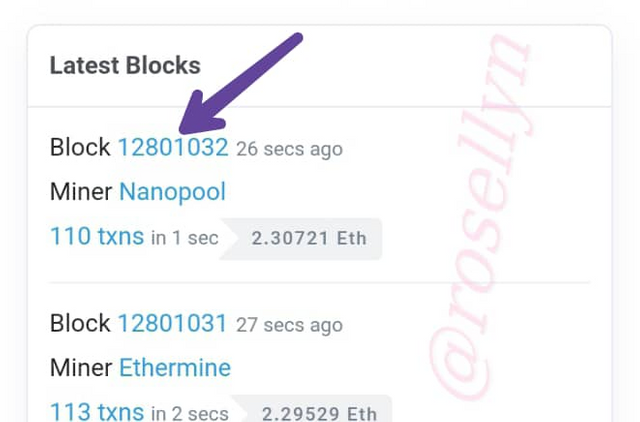
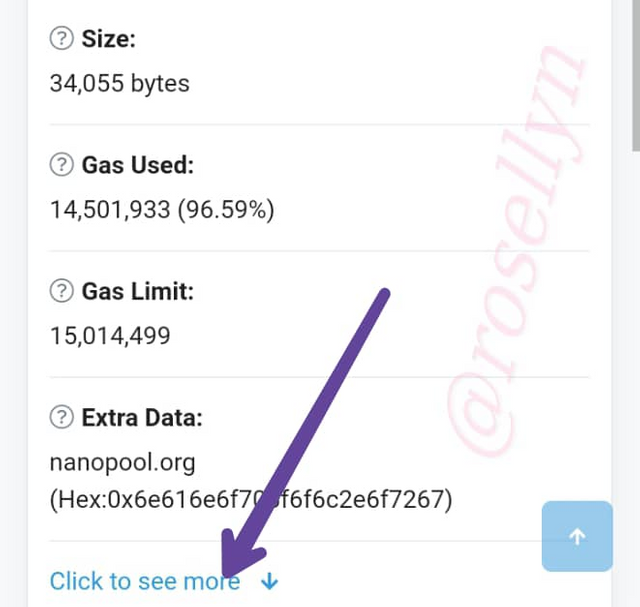
scroll down on the next screen to the bottom, select the arrow that says " click to see more", and the Hash will come up
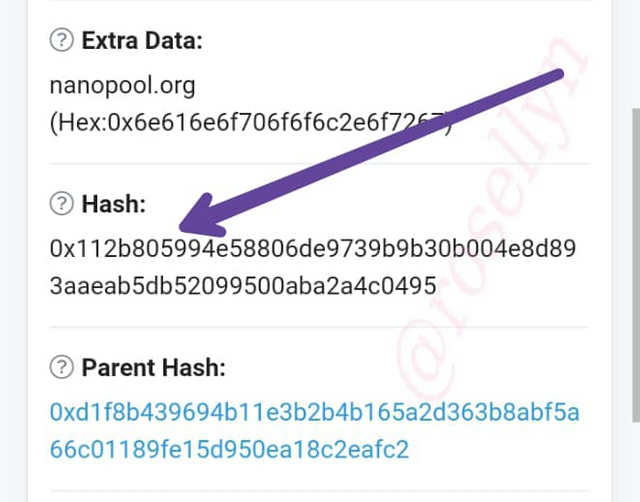
The Block Hash: 0x112b805994e58806de9739b9b30b004e8d893aaeab5db52099500aba2a4c0495
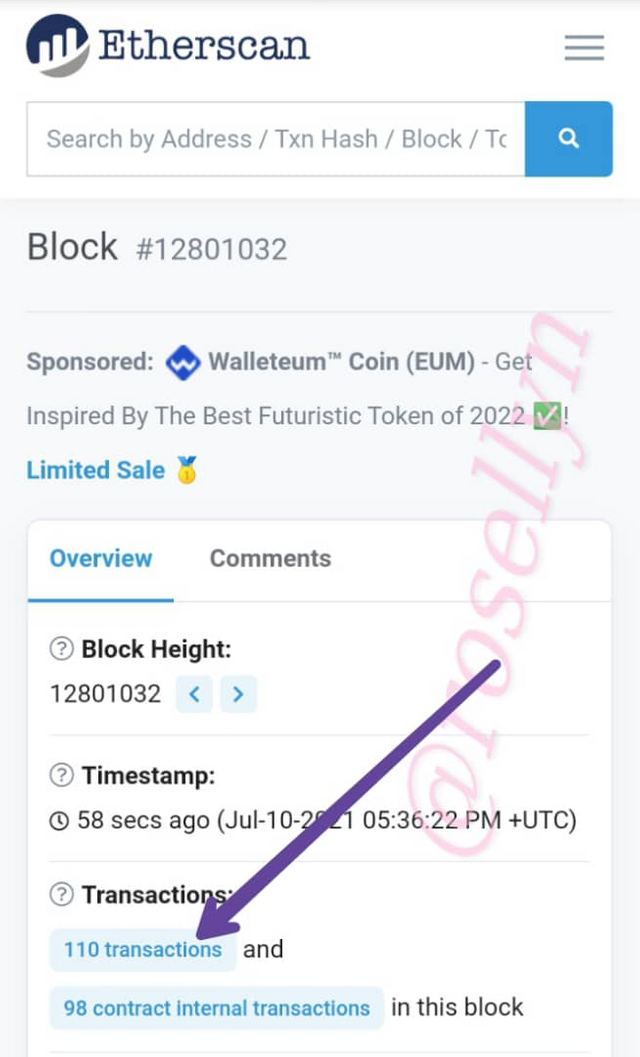
Let look for the Transaction Hash now
Go back to the top of the block page
Click on transaction
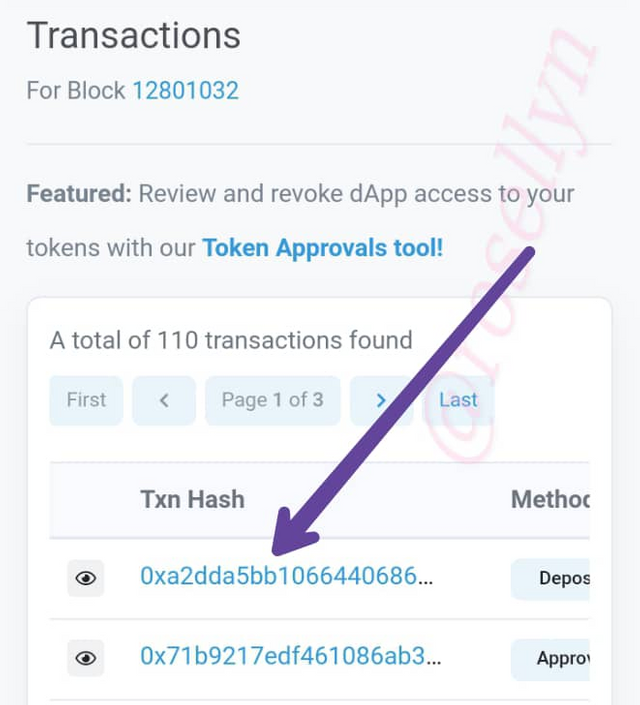
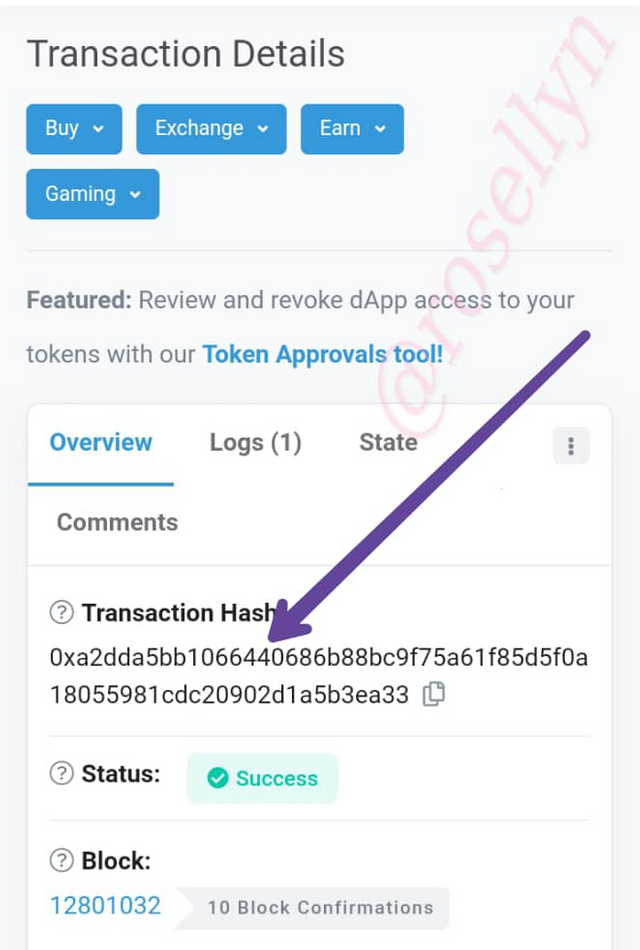
Last Transaction Hash: 0xa2dda5bb1066440686b88bc9f75a61f85d5f0a18055981cdc20902d1a5b3ea33
Question
3.) Generate the hash using SHA-256 , from the word CryptoAcademy and from cryptoacademy. Screenshot required. Do you see any difference between the two words? Explain.
We go to the address https://passwordsgenerator.net/sha256-hash-generator/ to generate the hash
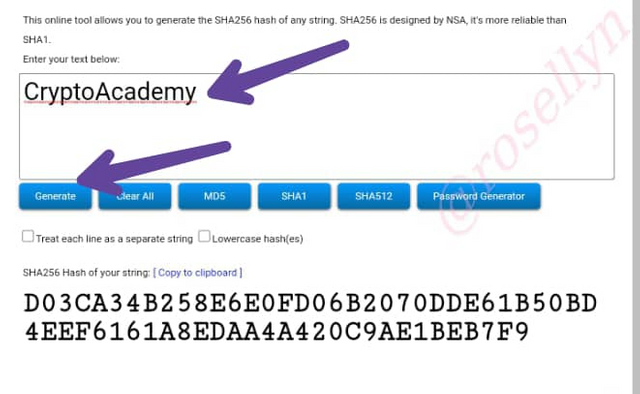
We fill in our first word CryptoAcademy
We generate this Hash: D03CA34B258E6E0FD06B2070DDE61B50BD4EEF6161A8EDAA4A420C9AE1BEB7F9
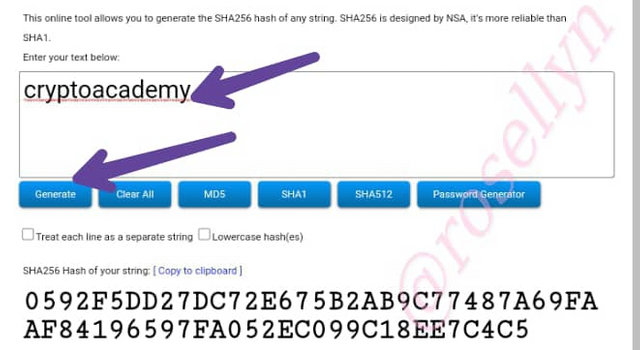
And for our second word cryptoacademy
This is the output: 0592F5DD27DC72E675B2AB9C77487A69FAAF84196597FA052EC099C18EE7C4C5
I can tell that the two terms are different because one has two uppercase letters and the other has only lowercase characters. As a result, no matter how hard we attempt, the results will always be different.
This means that two sets of data that are close to been similar cannot have the same Hash.
In summary, the results are not comparable in any manner.
Question
4.) In your own words explain the difference between hash and cryptography.
| Hash | Cryptography |
|---|---|
| Hash translates information to produce a series of alphanumeric results | Cryptography is an information encryption mechanism while it can be accessible by third parties |
| Hash have a specific limited output that can be generated | Cryptography encrypted code is unlimited |
| No encryption in Hash, therefore no need for access keys | Cryptography uses access keys: Only people with the required access keys can decrypt the encrypted data |
| Hash operation is known to be irreversible | With cryptography, encrypted data can be modified with the required access keys |
Conclusion
Blockchain and cryptocurrencies rely heavily on cryptography and hashing. They do different things, yet they have a lot in common.
The Hash is incredibly significant in the blockchain, and knowing what it is and what it accomplishes will be beneficial to any cryptocurrency enthusiast.
Gracias por participar en Steemit Crypto Academy Season 3:
Espero seguir leyendo tus publicaciones.
Buena investigación. Felicitaciones.
Recomendaciones:
Calificación: 9.8
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit