Hello,
I hail all colleagues and professors in the Cryptoacademy. Most especially professor @pelon53 who has taught us Root Hash and Merkle Tree.
Question
Explain in detail the hash rate
Revising what Hash is will help us to understand what Hash rate really stands for.
Hash is a fixed distance alphanumeric code that can be used to represent any length of words, data or file. To generate different sorts of hash codes, crypto projects use a number of hashing algorithms, you can think of them as random word generators, with each method being a distinct mechanism for creating random words.
Miners must compete with their machines to predict a number before they may add fresh transactional data to the next blockchain. Miners strive to change a single value called nonce to produce a hash that is less than or equal to the numeric value of the target hash. A fully new hash is constructed every time the nonce is updated. It's similar to a lottery ticket system, with each new hash being its own ticket with its own set of numbers.
Here, the hash rate is very significant
The hashrate is a crucial measure for assessing a blockchain network's strength, and more importantly, its security. The higher the hashrate and the more difficult it will be for malicious agents to disrupt the network, the more machines honest miners concentrate to uncovering the next block.
The hash rate is a measurement of the processing capability of the equipment (computers) that mine digital currencies on the blockchain network
The more miners on the network, the more hashrate is created, which means more "guesswork." The more guesswork there is, the more likely the correct hash will be found soon. Because blockchains are meant to create blocks and distribute new coins at a consistent and predictable rate, the difficulty is set to alter automatically after a certain number of blocks to keep the rate consistent.
Question
Make the following Merkle Tree: Transaction (tree leaves): Steem1; Steem2; Steem3; Steem4; Steem5; Steem6; Steem7; Steem8.
I made it to the Root Hash. And put every hash generated using SHA-256 , show screenshots.
Tell the steps to follow to verify if Steem6 is included in the Markle Tree.
Using: https://passwordsgenerator.net/sha256-hash-generator for hash generation.
Merkle tree leaves hash
Steem1
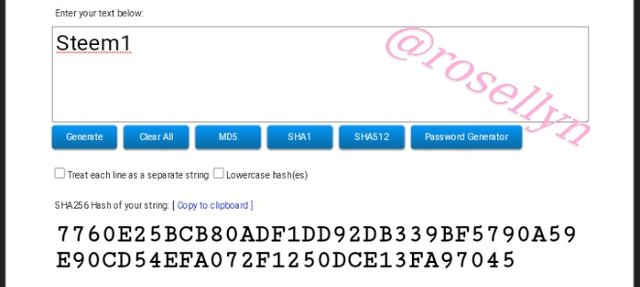
7760E25BCB80ADF1DD92DB339BF5790A59E90CD54EFA072F1250DCE13FA97045
Steem2
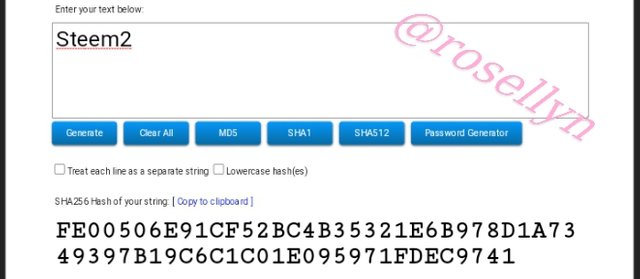
FE00506E91CF52BC4B35321E6B978D1A7349397B19C6C1C01E095971FDEC9741
Steem3
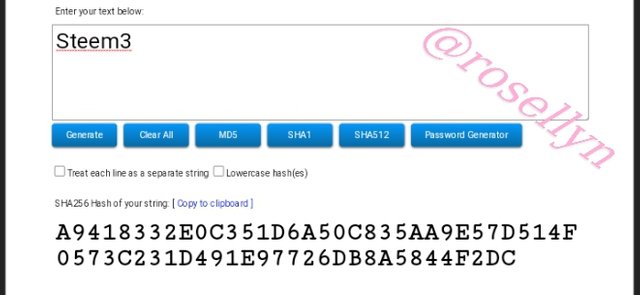
A9418332E0C351D6A50C835AA9E57D514F0573C231D491E97726DB8A5844F2DC
Steem4
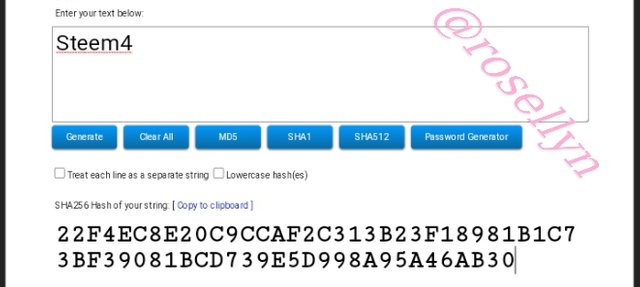
22F4EC8E20C9CCAF2C313B23F18981B1C73BF39081BCD739E5D998A95A46AB30
Steem5
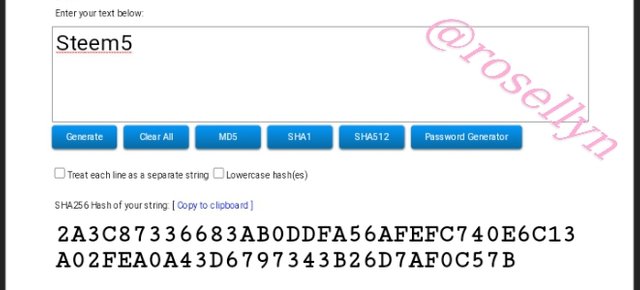
2A3C87336683AB0DDFA56AFEFC740E6C13A02FEA0A43D6797343B26D7AF0C57B
Steem6

A7BAA6DE0C0658E9E3681966E542BACD116529F5AE9A2D9126CDB1C1D5BC1278
Steem7

D441688DDA7F9285E8811728DD9A3955CF74F0A3C7600C1589D0F1D3B48FFAC7
Steem8

F2E38ED4FF662087B6E9BEAFA4158EBC488B995732057BDA019A6A77FFB5F9F5
Merkle tree branches hash
Steem1Steem2
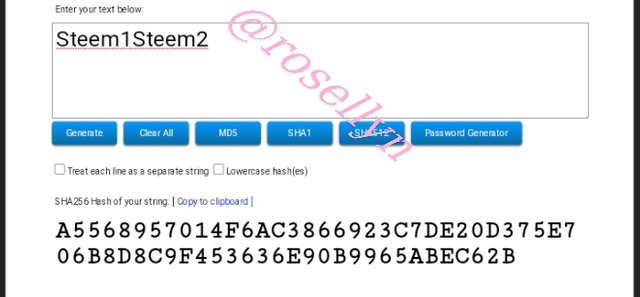
A5568957014F6AC3866923C7DE20D375E706B8D8C9F453636E90B9965ABEC62B
Steem3Steem4
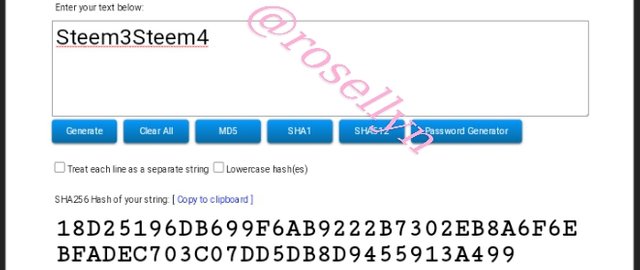
18D25196DB699F6AB9222B7302EB8A6F6EBFADEC703C07DD5DB8D9455913A499
Steem5Steem6
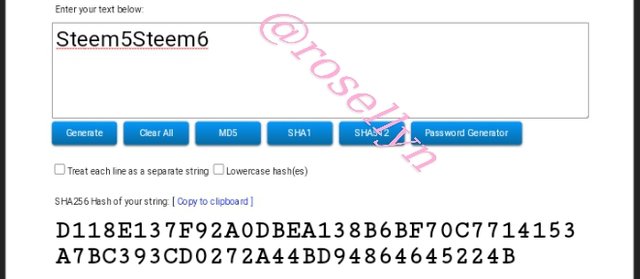
D118E137F92A0DBEA138B6BF70C7714153A7BC393CD0272A44BD94864645224B
Steem7Steem8
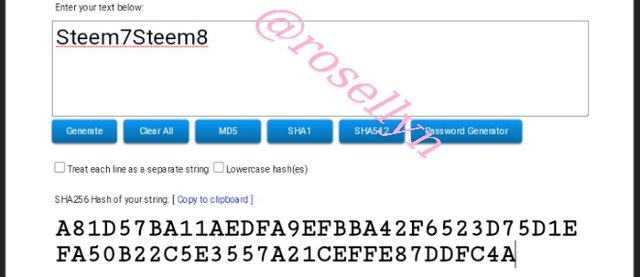
A81D57BA11AEDFA9EFBBA42F6523D75D1EFA50B22C5E3557A21CEFFE87DDFC4A
Merkle tree branches hash
Steem1Steem2Steem3Steem4
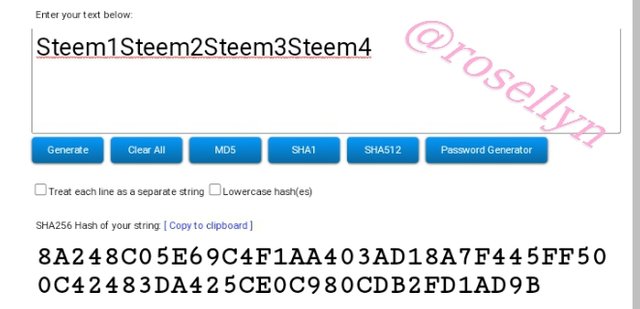
8A248C05E69C4F1AA403AD18A7F445FF500C42483DA425CE0C980CDB2FD1AD9B
Steem5Steem6Steem7Steem8
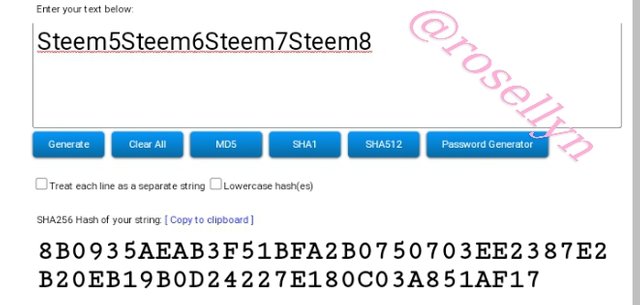
8B0935AEAB3F51BFA2B0750703EE2387E2B20EB19B0D24227E180C03A851AF17
Merkle tree root hash
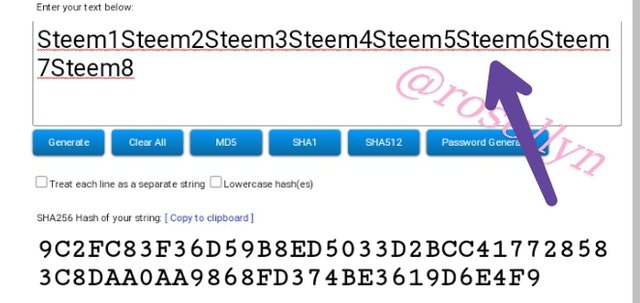
Steem1Steem2Steem3Steem4Steem5Steem6Steem7Steem8
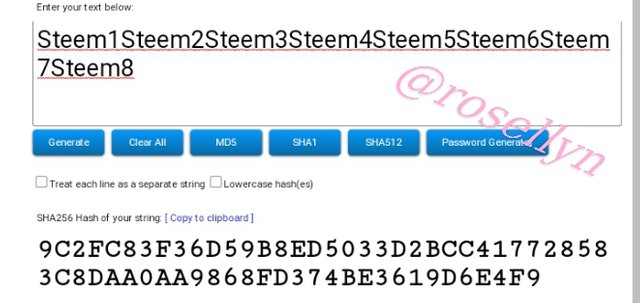
9C2FC83F36D59B8ED5033D2BCC417728583C8DAA0AA9868FD374BE3619D6E4F9
Merkle tree
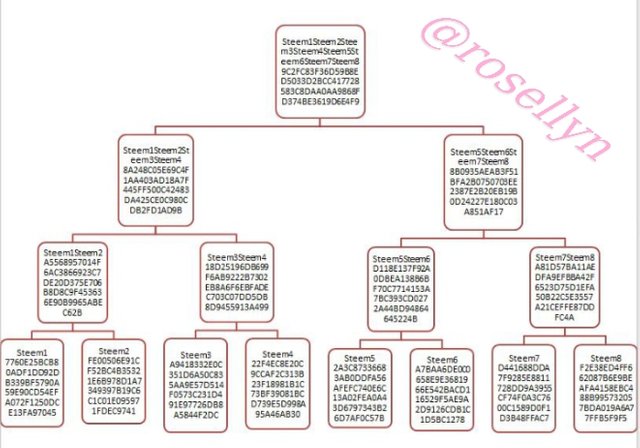
Tell the steps to follow to verify if Steem6 is included in the Markle Tree.
Step 1
As shown in the Merkle Tree, two hash branches led to the root hash.
To verify Steem6 we can begin from where Steeem6 doesn't appear on
Steem1Steem2Steem3Steem4, and then confirm the hash.
Steem1Steem2Steem3Steem4 8A248C05E69C4F1AA403AD18A7F445FF500C42483DA425CE0C980CDB2FD1AD9B
Step 2
Steem5 and Steem6 were together, therefore, we will confirm the hash Steem5
Steem5 2A3C87336683AB0DDFA56AFEFC740E6C13A02FEA0A43D6797343B26D7AF0C57B
Step 3
From the branches, we will confirm the hash for Steem7Steem8.
Steem7Steem8 A81D57BA11AEDFA9EFBBA42F6523D75D1EFA50B22C5E3557A21CEFFE87DDFC4A
Step 4
Now that every other hashes has been confirmed, then we will look into the Root Hash input data, and we will see if our Steem6 is present data
Question
3. Using the SHA-256; you must place each complete hash in the Merkle Tree.
Transaction (tree leaves): SCA1; SCA2; SCA3; SCA4; SCA5; SCA6; SCA7; SCA8. Explain each step, show screenshots.
If the number of leaves on the tree is odd, what should you do? Explain.
Using: https://passwordsgenerator.net/sha256-hash-generator for hash generation
Merkle tree leaves hash
SCA1

13E0A04BB0E669E1C638DBE3A704743F99F162B25245E4D8C064D35BA38FA8C8
SCA2

27849353A9C8CC4E948EB6E5748EDD79CB83513D8C0ADAF3E8C83D3792C9149B
SCA3
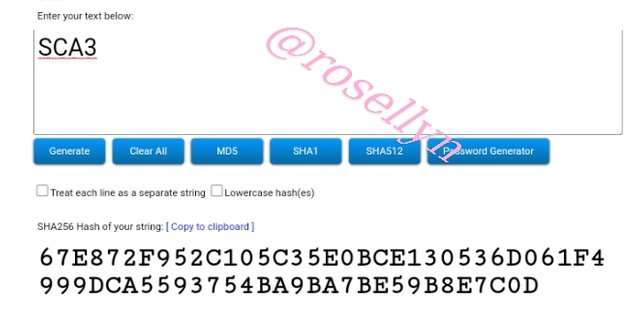
67E872F952C105C35E0BCE130536D061F4999DCA5593754BA9BA7BE59B8E7C0D
SCA4

491928A32BAE70A12FA251412BBFD7C9999F317BA6BF577C283C724225270A43
SCA5

99C078C39CDE7F47799E0E8691460A9F3E83E78D498EA989308FCFCC58907B19
SCA6

7A648D887B124DB14E96E23BA92783E7F26D00957C19B9B8229632C2C1873729
SCA7

7E0BBD6BA4BA9896F9911AF46B06DD2C47535F9C80B29D693FDF6B9319D0D68E
SCA8

562ABCEEB497E1FE7AE275A883FD5EF9D92A05F5C19D82ABAA0DC1571B7DF3AD
Merkle tree branches hash
SCA1SCA2

91B09BBA815748166FB36413342C7E4E7E809F4BAC538C0418841A4476B527EF
SCA3SCA4

B49B48697A3ACBC5E3D2E36B6EE49C44020D88E664C5C1AA7A7CF34058177379
SCA5SCA6

F026924CD1285FF92C2A2DE9B9313027EB67273A82375C939348C887F6B52F77
SCA7SCA8
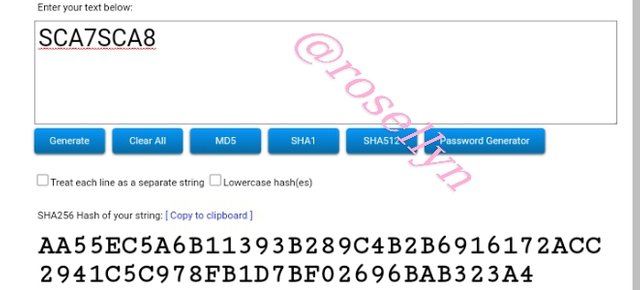
AA55EC5A6B11393B289C4B2B6916172ACC2941C5C978FB1D7BF02696BAB323A4
Merkle tree branches hash
SCA1SCA2SCA3SCA4

F50DC120CBF6C46923037F6D7F41D4153ECC9AB7430DDA662C142DB1FFE483F7
SCA5SCA6SCA7SCA8

A3D8CA8494CC426ABD5E1FC5FA0FEAE4F2B2ECE4C4CECDCA05E19EB66542533F
Merkle tree root hash
SCA1SCA2SCA3SCA4SCA5SCA6SCA7SCA8
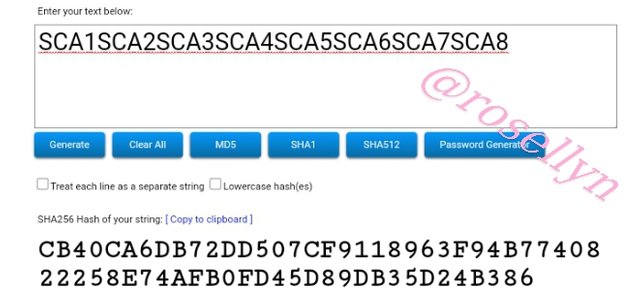
CB40CA6DB72DD507CF9118963F94B7740822258E74AFB0FD45D89DB35D24B386
Merkle tree
If the number of leaves on the tree is odd, what should you do? Explain.
For the Merkle tree to serve it's purpose of creating a solid and efficient root hash, it is necessary that all files in total must be "even" in number
The below image show an example of where the tree leaves turns to be odd in numbers.
In such cases, the last odd file or data will be duplicated to complete the system and make leaves to be even. If the branches generated data turns out to be odd, the last branch file or data will be duplicated to complete the Merkle Tree process.
.jpeg)
Here, the leaves was odd, and the last data was E, so it was duplicated, and another E was generated at the dotted area of the leave.
Also, the branches turns out to be odd to, and the last branch data was duplicated "EE" at the dotted area of the leave branch. And then the data became even for the Merkle Tree to carry out it's function.
Conclusion
Merkle Tree is another advanced function of blockchain security.
In this homework task, I have been able to refresh our memories of what Hash means, and I also explained what Hash rate is, which I believe we can clearly understand that from the explanation.
Also, I have practically demonstrated how Merkle Tree works. It was really a wonderful learning week and lecture from @pelon53.

Gracias por participar en Steemit Crypto Academy Season 3:
Espero seguir leyendo tus publicaciones.
Pregunta 1, hay que investigar más.
Pregunta 2, todos los hash coinicden. Se debió explicar con un gráfico para enteder mejor la verificación de Steem6.
Pregunta 3, Todos los hash coinciden. No quedó muy claro lo de las hojas impares. Involucars las ramas impares también.
Recomendaciones:
Investigar con mayor profundidad.
Explicar con sencillez para que otros puedan entender.
Calificación: 6.5
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit