Greetings,
This week professor @stream4u has delivered his lecture on Cryptography.
In this lecture he looks to educate us on the whole concept of Cryptography.
After going this his lecture I will now submit my assignment.

Introduction
In the world of centralization privacy is important to users of the traditional system.
Even though we have been introduced to the decentralized system the centralized system is still getting ahead of the decentralized because the traditional system was kind of introduced first and it has gained more popularity than the decentralized system.
For privacy reasons, cryptography was introduced for users who want outmost privacy and to prevent people for intercepting a piece of information they are trying to send out to others
Explain the Blockchain Cryptography and mention few names which are the Blockchain Platforms (Few names of the Blockchain Platforms)?
In simple English terms cryptography means to find a secure way of protecting one's information from people or hackers looking to get access to that piece of information which is meant for another user.
That being said, this is not far from cryptography in blockchain.
What we should know is that a blockchain is decentralized and secure through cryptography.
So in blockchain, cryptography makes sure once the information is stored on the hash block nothing can be changed by a user.
By this means it means that a third party or hacker has not access to the information that is stored.
Blockchain cryptography works by encrypting the piece of information that is supposed to be received by the receiver.
So in order for the information to he access and read it has to he decrypted.
That being said, every participant on the network have their own private keys.
It is this private key that a user uses to encrypt and decrypt a message he sends and receives.
names of blockchain
- Bitcoin blockchain
- Ethereum blockchain
- Binance smart chain.
- EOS blockchain
- Steem blockchain.
Explain the Public Key Cryptography.
I spoke about keys in the previous key question and in this question I I will look to explore the public key.
A public is made of numbers and alphabets .
These alphanumeric functions are combined with hash functions to make transactions by creating public addresses.
The public key is a key that works in pairs.
What I mean by this is that in order to use the public key, the private key too is used.
Let me explain further.
On the blockchain, the public key as the name suggests is known by the users on the blockchain.
It is through this public key that a user is able to encrypt a message he wants to send to a recipient.
After the recipient receives the message that is when he uses the private key to decrypt it.
A uses private key is handed to power to be able to create a public key.
That being said, when the sender wants to send a piece of information to a receiver, the sender and the receiver both will exchange public keys.
When the receiver finally receives the information it is the public key that he uses to confirm that he has actually received information from the sender.
So finally a public key which may be known by many users doesn't guarantee that the information isn't safe because before the user can confirm receiving it he needs the public key to confirm and then before he can read it he needs the private key to read it.
Explain the Private Key CryptoGraphy.
As I explained, the public key combines with the private keys to work because you need the private key to create the public key but the other way is not possible.
A public key cannot be used to create a private key as the private key is very private.
The private key is only known to the owner of the key.
The private keys are what a receiver uses to decrypt the piece of information.
The private key is consisted of a combined numbers and alphabets.
These key uses digital signatures to confirm the transaction.
When a sender sends the information to the user the receiver is able to access the information with the help of this digital signature with the private key.
Explain the Digital Signatures CryptoGraphy and what is Singing Of Transaction/Message?
Digital Signatures cryptography
In simple English terms a signature is a persons unique identification that he or she uses to confirm a deal.
This is not far from a digital signature.
A digital signature combines the use of the public and private keys before a transaction is confirmed by the receiver in the blockchain.
When using a digital signature, since the private key is only particular to only one person the owner cannot deny his signature.
Since it is on a blockchain once the information or transaction is confirmed the information that we see is very reliable.
In the world of decentralization users are looking for a way to make life easier, using the digital signature and the hash value, large amount of transactions can be confirmed.
Signing of transaction or message
Signing of a transaction or message simply means combining the private and public keys with the help of the hash value to verify a transaction or message.
The Signing process starts with generating a hash value, after the hash value is created the sender inputs the value of the hash generated by Signing in digitally.
After the sender sends the data, the verification phase then comes up.
In the verification phase the public key is as I explained is used in verifying.
After the message is verified, the hash value that was generated from the message is then compared with verified transaction or message to make sure its valid.
Explain what is Symmetric and Asymmetric cryptography?
In this question I will look to explain what a symmetric cryptography is and also what the asymmetric cryptography is.
But firstly I will look at what a symmetric cryptography is,
A symmetric cryptography is a type of cryptography that employs the use of a single key.
This key is what is required in the encryption and decryption of a message.
This key is also known as the private key.
The symmetric cryptography happens in two ways.
The information comes as its raw form using the private key to encrypt it.
After the information is received the same key that was used to encrypt it is still required to decrypt it.
You will realize that it does not use the public key which is known by almost every participant to encrypt the message and then use a private key to decrypt it.
This process works differently from the normal method we know.
The symmetric encryption is suitable for use by two participant who want to share a piece of information or are looking to close a transaction.
The two participant involved will simply share the keys with each other and then send and receive the information after which it is decrypted with that same key used in encrypting it.
Generally there are two types of symmetric cryptography.
- Block symmetric cryptography.
- Stream symmetric cryptography.
After explaining the symmetric cryptography to my satisfaction I will now look to explain asymmetric cryptography.
Asymmetric cryptography is a type of cryptography where unlike the symmetric cryptography requires two different keys are needed to send and receive a message or complete a transaction.
These keys are what are known as the public and private keys
The public key as explained earlier is what is used to encrypt the piece of information about to be sent( Known by both participants) and then the private key( which is supposed to be known by only the receiver) is what is used to decrypt the piece of information.
What we should know is that tis type of cryptography is used amongst large groups of participants.
I said earlier that a private key is used in creating the public key that the user needs to encrypt the information, so therefore it is only a private key that was used in creating the public key can be used in decrypting the information.
How Blockchain Wallets CryptoGraphy works and explains the available types of Crypto Wallets.
A Blockchain cryptography puts software in place to help keep the public and the private keys.
As I said earlier a public key that doesn't have relationship with a private key has no business with that private key.
The public key and the private key has function they perform in the blockchain.
The public key is the key the user uses to collect the funds receive.
After the funds are received the private key then comes in to perform it's function as the key that claims the funds.
Let me explain it in simple term.
You see that when your create your steemit account you are given a posting key and a private active key.
A user can use the posting key to collect rewards but the user cannot use the posting key to perform any transactions rather the user needs the private active key to spend his funds.
The public key and the private key works in the same manner.
However in the blockchain, the addresses to the wallets cannot be the same as the wallets do not keep crypto assets in them but the history of transactions performed on the blockchain.
The wallet addresses are created or generated using the public key, and hash algorithm.
And then when it comes to verification time the use of the hash algorithm is still needed with the combination of private key and the hash algorithm.
Types of crypto wallets
The main types of crypto wallets are Hardware wallets, Paper wallet and then Software wallets
There are other types of wallets but these other types are under the 3 main types of wallets.
Hardware wallets
Hardware wallets are wallets that are generally used offline.
In this type, the wallet is handed the ability to be able to retain the keys.
Because they are offline there is no internet connection needed to use this type of wallet.
This type of wallet is very safe as a third party cannot have access to a users keys because it is offline. A perfect example is the ledger wallet.
Paper wallets
Paper wallets are just like a piece of document.
As the name suggests the keys to the wallet is stored on a piece of paper.
Which means when that document gets missing the user looses all his funds.
Software wallets
Software wallets are wallets that keep information about its keys on a software system.
This means that without internet connection the user cannot have access to his wallet.
This ultimately makes software wallets less secure as a third party can access the software and steal your keys.
A perfect example is the web wallets.
What is the Merkle trees and What its importance in blockchain?
A Merkle tree is a representation of data on a tree like structure.
These data is generally known as hashes.
The hash is represented on the tree, whiles each hash is represented on a block hash.
When the data is represented on the block hash it makes validating of blocks on the blockchain by miners very easy.
The Merkle tree is made by representing the top block down to the down block.
It is further represented by adding the hashes of the transaction on a tree like structure.
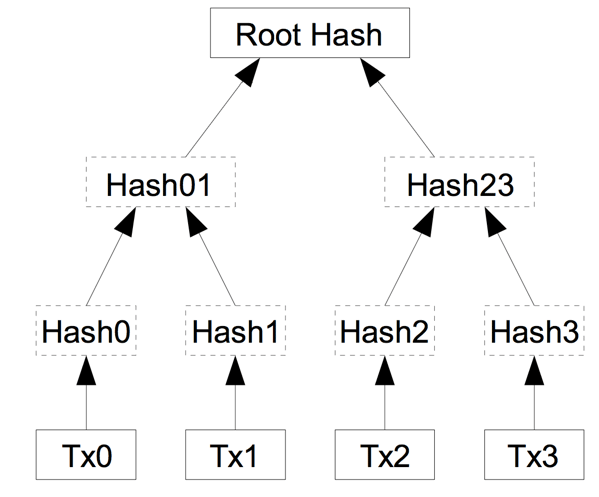
S
In the above Merkle tree the TxO, Tx1, Tx3 these leaves represents leaves with Hash0 to hash 3, these various leaves represent the transactions.
The transactions contain transactions with different details.
However the leaves Hash01 and Hash 23 are the nodes which represent the pairing in different blocks.
Then finally the Root Hash is the node that is responsible for the verification of transactions of all type on the blockchain.
The Merkle tree importance
Merkle tree allows the validation of transactions easy and simple.
The Merkle tree helps reduce the validation time, which means it is scalable.
Practical + Theory, do some practical research, study on Blockchain Demo: Public / Private Keys & Signing and then explain the functionality of Key, Signature, Transaction, Blockchain with proper screenshots of yours practical. (Do study well for this topic)
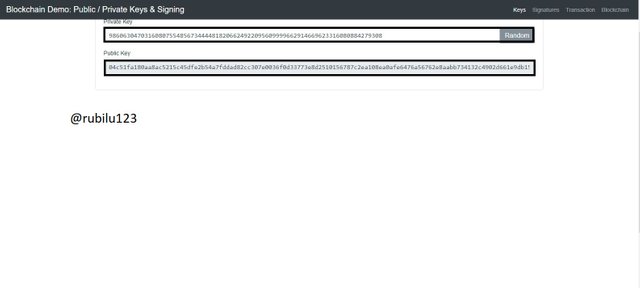
For this question, In the asymmetric aspect of cryptography we have two keys required. Thus, we have the Private Key and the Public Key which are used for decrypting and encrypting for messages. The two keys are related together and I will show the relation in the screenshot below. There is relation in the sense that, when one Private Key is generated, a Public Key is generated. With the help of this link we will explore the Blockchain Demo
From the Screenshot below, we have the Private Key which is related to a Public Key. The Private Key is generated randomly.
Private Key
98606304703160807554856734444818206624922095609999662914669623316080884279308
Public Key
04c51fa180aa8ac5215c45dfe2b54a7fddad82cc307e0036f0d33773e8d2510156787c2ea108ea0afe6476a56762e8aabb734132c4902d661e9db153aac19c477f
Furthermore, I mentioned earlier that, A private Key is related to a Public Key in a sense that for a private Key generated, it generates a New Public Key. I will therefore generate a Private Key which will go in a long run to create a New Public Key.
From the screenshot below, it can be clearly seen that, I generated a new Private Key which created a new Public Key. this goes in a long run to explain the concept that, for any Private Key, there is a Public Key linked to it.
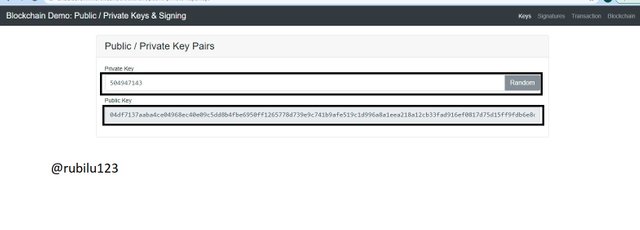
New Private Key
504947143
New Public Key
04df7137aaba4ce04968ec40e09c5dd8b4fbe6950ff1265778d739e9c741b9afe519c1d996a8a1eea218a12cb33fad916ef0817d75d15ff9fdb6e8c2a513ac86d7
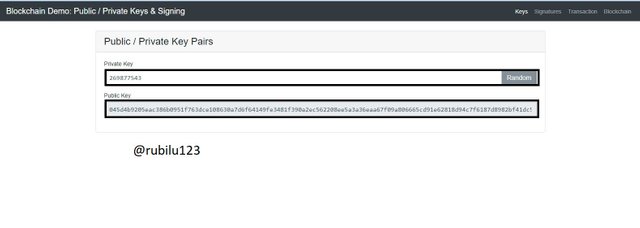
Another exploration is made in the sense that, I created another Private Key to see the effect. This New Private Key generated another Public Key, This clearly shows the fact, for every New Private Key, there is a New Public key and these keys are linked together which helps in the decrypting and encrypting of data.
New Private Key
269877543
New Public Key
045d4b9205eac386b0951f763dce108630a7d6f64149fe3481f390a2ec562208ee5a3a36eaa67f09a806665cd91e62818d94c7f6187d8982bf41dc5d88d39f2786
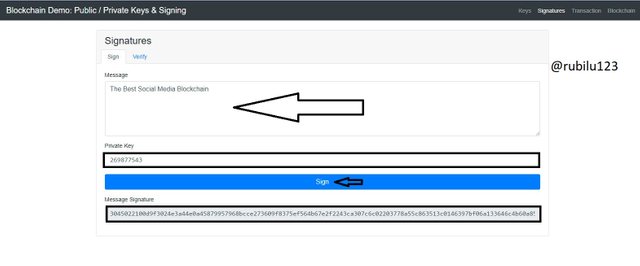
In this aspect of the Blockchain demo, I am going to explore the signing of messages and the verification. The message which I am going to sign is The Best Social Media Blockchain. My Private Key is going to be used in the signing process. I then click on the sign tap for the Message signature.
Message Signature
3045022100d9f3024e3a44e0a45879957968bcce273609f8375ef564b67e2f2243ca307c6c02203778a55c863513c0146397bf06a133646c4b60a85721a46134e0d19fa71f8cf4
Private Key Used
269877543
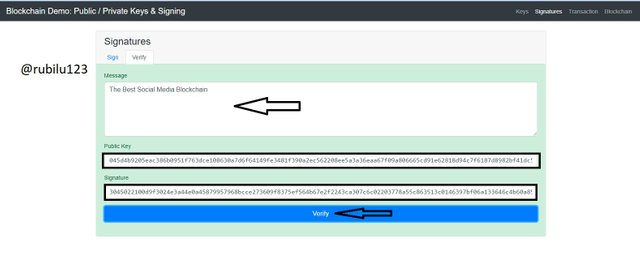
Now, let's make a verification of the message signed. With this section or area the Public Key which is linked with the Private Key is put in and the verification tap is clicked on. When this occurs, the Block becomes validated and which is made visible as a result of the color.
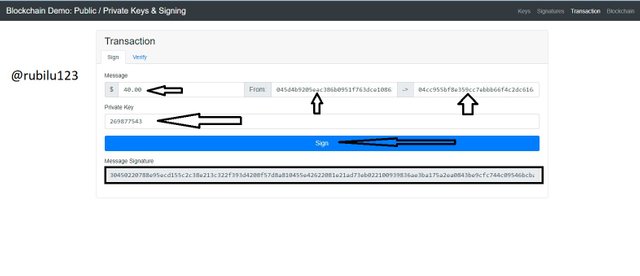
Transactions are made in the Blockchain from one wallet address to another and this is done with the help of the Private Key. I am thereby going to make a transaction of $40 from one wallet address to another.
Wallet Address From
045d4b9205eac386b0951f763dce108630a7d6f64149fe3481f390a2ec562208ee5a3a36eaa67f09a806665cd91e62818d94c7f6187d8982bf41dc5d88d39f2786
Wallet Address To
04cc955bf8e359cc7ebbb66f4c2dc616a93e8ba08e93d27996e20299ba92cba9cbd73c2ff46ed27a3727ba09486ba32b5ac35dd20c0adec020536996ca4d9f3d74
Message Signature
30450220788e95ecd155c2c38e213c322f393d4208f57d8a810455e42622081e21ad73eb022100939836ae3ba175a2ea0843be9cfc744c09546bcbad13adc2bffcb63fe87bcebc
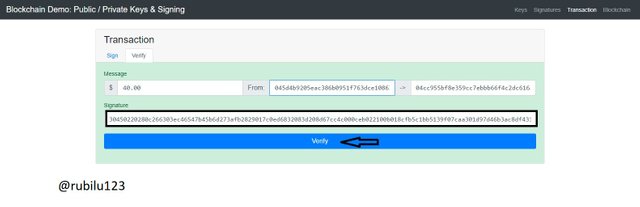
Just as we verified the Signing process, we will do same for the Transactions aspect. This is simply done by entering the signature to confirm the transaction was signed and clicking the verify button or tap. This makes the block validated and can be seen by the color change.
This area of the Blockchain Demo, We are going to take a look at the transactions which are stored with their various Hashes. These transactions are saved in the Blockchain and their Hashes functions.
The Screenshot below displays the valid blocks of Block 2 and Block 3 with details of various transactions of the Hash.
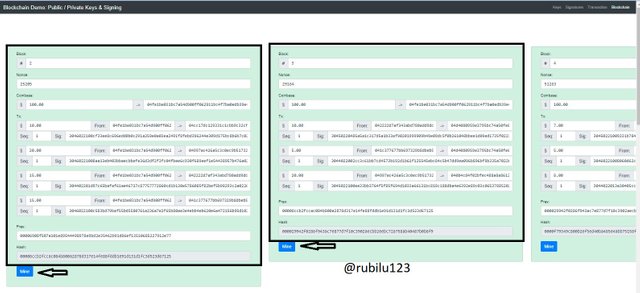
Furthermore, I will be making some changes to some details of Blockchain more specifically the transaction details. I am going to change the amount of transaction in the Block 3. When this is done the Block will invalid and this will seen clearly. The Price was changed from $10.00 to $6.00.
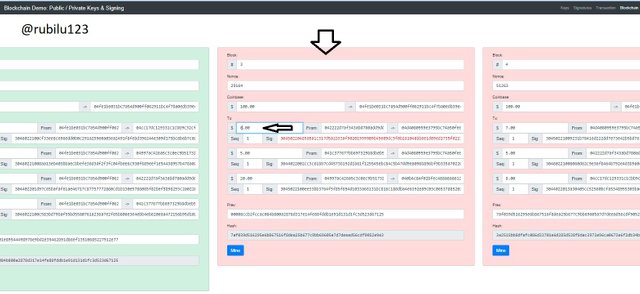
Looking at the above screenshot, the Block is invalid and this can be seen since it is red in color. When the change was made it can be seen that the Block 3 became invalid and the color changed to red. The changed made to Block 3 had an effect on the next Block which is the Block 4. From researched made, it is known that, when a Block is invalid, it has a effect on the next Block. This shows the Hash of a Block if been invalid has an effect on the next Block.
In a attempt to make the Block valid, we have to re-mine the Block. That is we will have to re mine Block 3 and also we have to re-mine Block 4 as well. In addition, for a Block to be valid, it depends on the Nonce. Therefore, when we re-mine the Block, we have the Nonce changing. But the Signature will still be invalid since we used different Private and Public keys.
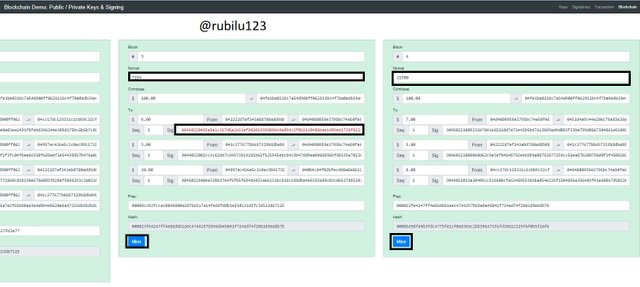
From the screenshot below, the Block has been re-mined and the Nonce has been changed.
Wrong Nonce
Block 3 = 21964
Block 4 = 51263
Correct Nonce
Block 3 = 7154
Block 4 = 21500
Conclusion
t without reading the professor's homework you might think the professor's work is too difficult.
After reading and researching on the topic I now got some understanding.
Cryptography was brought into the system because of blockchain.
That being said using blockchain Cryptography assures a user that the transaction he has entered, the moment confirmed cannot be altered.
I also looked at Crypto wallets in my assignment, they are wallets that help us to keep our keys.
I have realized that the most secure way of keeping one's keys in through the offline method.
The Merkel tree was presented to help simplify the work that is done in the blockchain by miners and participants.
Hence the tree has any of advantages.
Thank you.