Hello everybody, Hope you all are fine and in good health!
My this post is a Homework Task assigned by professor @pelon53
I hope that I will get some good grades from professor, wish me best of luck!
So let's start my Homework Task...
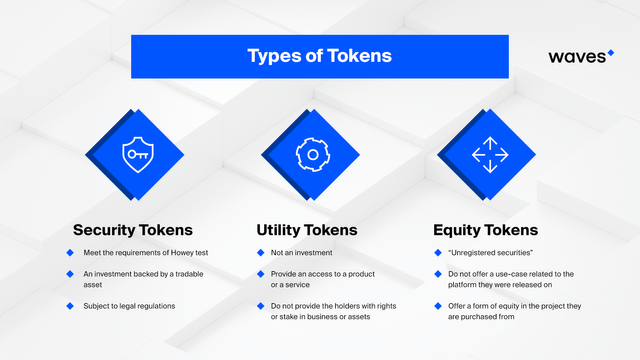
What is a Utility token?
A utility token is described as a digital token of cryptocurrency that is issued in order to finance the cryptocurrency's growth and that can later be used to buy a product or service sold by the cryptocurrency's issuer.
A utility token is a blockchain-based commodity that people purchase to use in the future for something. A business creating an online game, for example, may issue utility tokens to finance the game's growth.
After the game's progress is complete, token owners will use their tokens to make in-game transactions. Gamers gain access to in-game tokens for potential use, while game creators gain access to money to finance their project.
In a variety of areas, utility tokens may be beneficial to buyers. They provide consumers with early access to a new product or service in the future. A software startup usually creates a digital product or service before launching an ICO (Initial Coin Offering). Utility tokens are sold during the initial coin offering (ICO). These tokens may be purchased and used as a mode of payment on the issuing company's website.
Example
A trip in an Uber driver, for example, maybe paid for with an Uber token. Anything else, though, is out of the question. If you were to buy something else with the Uber token, you'd have to first swap it for fiat currency or a crypto-coin like bitcoin.
Role of Utility token
The following are the six roles:
- Giving the token owner a right, such as buying or using a commodity or the ability to vote on a subject.
- Providing value in exchange for resources, such as decentralized storage.
- Charging customers for using digital services or using the blockchain infrastructure.
- Serving to enhance the user interface by rewarding users with tokens for completing those tasks.
- Serving as a form of payment both within and outside the blockchain as an alternative to conventional financial transactions.
- Utility tokens may be used to distribute and exchange those types of earnings.
What is a Security Token?
Security tokens are basically smart contracts for parts of any resource that as of now has esteem, similar to land, a vehicle, or corporate stock. Utilizing security tokens implies financial backers can expect that their ownership stake is protected on the blockchain.
A security token offering/tokenized IPO is may be a sort of public offering during which tokenized digital securities, known as security tokens, are sold in cryptocurrencies.
Security tokens are computerized resources that get their worth from an outside resource that can be exchanged.
Moreover, In other words, A security token (also known as an authorization token) is a tiny piece of hardware that the owner carries around to authorize access to a network service. The gadget may take the shape of a smart card or be inserted in a specific item like a key fob.
Two-factor authentication adds a layer of security to security tokens: the user has a personal identification number (PIN) that authorizes them as the owner of the specific key; the device then shows a number that uniquely identifies the user to the service enabling them to log in. Each user's identification number is updated regularly, usually every five minutes or so.
Example
A Security token, unlike a password, is a physical entity. A key fob, for example, is convenient and easy to hold, making it simple for the customer to safeguard. And if the critical fob falls into the wrong hands, it cannot be used to obtain entry since the PIN (which is only known by the authorized user) is still needed.
The following are examples of security tokens:
Connected token
Tokens that are connected. The token must be physically connected to the device that the user wishes to use. A Yubikey smartcard or fob is a fine example. Users insert the gadget into a scanner, and the device automatically sends authentication data to the computer system.
Disconnected token
Tokens that are not connected. Users are not required to inject something into the system physically, but they may be required to enter a code provided by the token. A disconnected token is a cellphone that has been set up as a 2-factor authentication system.
Contactless token
Tokens that do not need to be touched. Users are not required to link to a computer, nor are they required to enter a separate keyword or access code. Instead, these systems provide a wireless link with the machine, and access is allowed or refused depending on that connection. Bluetooth tokens and keyless entry systems operate in the same way.
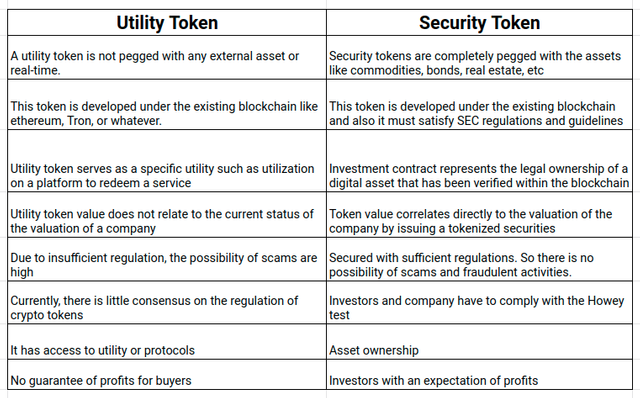
Difference between Security and Utility Token
- Security token Created to be used in investments , whereas Utility token provide product or services.
- Security Token Abide by the Howey test, whereas Utility Token don’t abide by the Howey test.
- Security Token represent ownership of an asset, whereas Utility Token don’t represent ownership of an asset.
- Security Token subjected to abide by GOVT Policies, whereas Utility Token s are not Subjected to abide by GOVT Policies.
For more detailed difference, we can look at the below screenshot
What is an Equity token?
An equity token list of cryptographic data (a block) serves as an equity certificate on the blockchain. Equity tokens have the same contractual records as physical or book-form share certificates, but they are stored on a blockchain rather than a share register.
An equity token is a security token that works like a typical stake of the underlying entity, a third-party commodity, or a venture. It derives its value from the success or loss of the company.
Holders own their assigned percentage of the overall enterprise, much as they do in any equity buy. They will also be entitled to a share of the company's earnings and a vote on the company's future. As units in corporate ownership, equity tokens may be classified.
By law, all of a company's shares of stock have no designation and are referred to as common shares. Earnings and voting rights are split evenly among common shares.
Example
For instance, if a company issues 100 equity tokens, each token entitles the holder to 1% of the company's profits and one vote out of 100. The owners of ten tokens will be entitled to 10% of the profits and ten votes, and so on. Preference shares, non-voting shares, Class A shares, Class B shares, etc. (also known as alphabet shares), and shares with additional voting rights are all different types of shares (sometimes called management shares). The share-class scheme is highly adaptable.
As it comes to Class A and Class B bonds, these designations usually change the voting rights of the company's stock.
I have Re-shared this post as instructed by Professor @stream4u because I have got grades on this post but my post went empty or without curation.
Marks 7.4
Link of my same post which went Empty
https://steemit.com/hive-108451/@saarah/crypto-academy-week-10-homework-post-for-professor-pelon53
Here is an evidence where Professor advised me to Re-share your post if it expires without curation.
Moreover, Here is an evidence of marks on this post by Professor @imagen
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Cc: @pelon53 @imagen
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Gracias @stream4u.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit