Hello Steemit Crypto Academy Community,
This week, the Professor @pelon53 gave much knowledge about tokens. The professor give us task to explain what Security tokens, utility tokens and Equity tokens are, with example of each. After reading the professor's lecture and doing some research on this topic, i am now going to write my assignment.
.png)
WHAT is the TOKEN?
In general, any depiction of something factual, eventful, significant, or thought may be used as a token. In simple words, if a present or something is offered in response to an initiative, it is a token. It does not have to be money, but it may be anything that resembles money.
.png)
A token in blockchain technology is a coin or asset that can be transfer between two people on blockchain platform. It is a monetary unit issued by a company, approved by the public, and backed by an emerging blockchain. Tokens are a form of cryptocurrency that is created on top of another blockchain.The tokens can be installed on any blockchain project and are fully reliant on it. Tokens should be traded and they have a monetary value.
Different blockchains can be used to create a token. For example USDT is a type of token which does not need to have a its own blockchain to work. This token can be created on a variety of blockchain networks, including Ethereum, Tron, and Eos.
Cryptocurrency tokens are fungible crypto currencies that can be exchanged (traded) within the ecosystem of the issuing blockchain project. In the cryptocurrency world, the term "token" is used as a sign. A token is a list of properties or access rights which is managed by a collection of PCs, a blockchain network, or another decentralized ledger system. The way they serve the end user is the easiest way to explain them. Tokens can be thought of as the food that keeps blockchain ecosystems running.
Difference between Tokens And Cryptocurrencies
| Token | Cryptocurrency |
|---|---|
| Tokens is Digital assets | While Cryptocurrency is digital money |
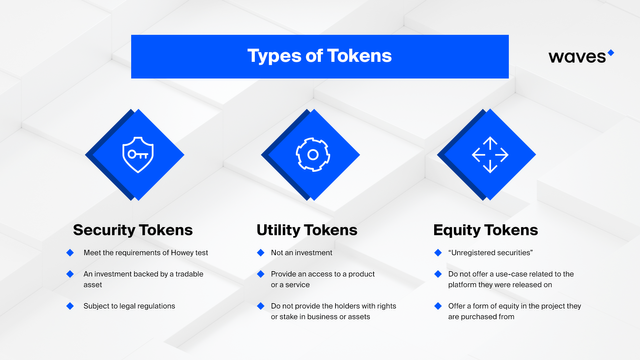
Types of Token:
There are many types of token with unique features but here we will discuss only three: Security Tokens, Utility Tokens and Equity Tokens.
Security Token
A Security token is a portable computer that electronically authenticates a person's identity by preserving personal information. To grant access to a network infrastructure, the owner inserts the authentication token into a device. STS (Security Token Services) creates security tokens that verify a person's identity.
.png)
The Basics of a Security Token
Hardware tokens with chips, USB tokens that connect through USB ports, and wireless Bluetooth tokens or programmable electronic key fobs that unlock computers remotely are all the forms of security tokens.
security tokens are also used for single sign-on providers to automatically log person into third-party websites. If token is disconnect from network it is not connected to the device or network in any way; however, the user manually inserts the token's information into the system. When wired, connected tokens communicate with the network electronically and automatically.
KEY TAKEAWAYS
By saving identifying information, security tokens authenticate identity electronically.
Security Token Services (STS), which authenticates the person's identity, issues them.
It can be used to confirm the owner's identity instead of or in addition to a password.
Security tokens aren't necessarily safe; they can get misplaced, broken, or compromised.
ADVANTAGES OF SECURITY TOKENS
Liquidity: Security tokens allow for fractional ownership, which reduces the amount of capital required to invest dramatically. It may have an impact on how markets function; for example, venture capital funds are typically thought to be very illiquid.
Open market: Issuers and customers can be able to gain access to the global exchange market by using security tokens.
Increased transparency: security tokens are easy to trace and validate since they are issued on a blockchain. Investors are given a clear picture of the issuer's financial status as well as the past of their recent purchases.
Regulation: Many nations are either drafting new legislation or attempting to extend existing legislation to cryptocurrency-related ventures. Since protection tokens reflect an asset's ownership rights, they must adhere to regulations
Cost-effective: Trading the assets of real world comes with a lot of extra challenges which takes a lot of time. Several administrative and consulting fees are included in the expense of security issuance.
Example of a Security Token
To add an extra layer of protection to a critical network device, such as a bank account, you could use a security token. The authentication token is used in conjunction with a password to verify the account owner's identity in this case.
Security tokens often store data that allows the owners' identities to be verified. Cryptographic keys, which are used in blockchain services such as Bitcoin, are stored by others, but the key should be held hidden. Few use time-sensitive passwords that are reset at regular intervals that are synchronized between the token and the network
Weaknesses of Security Tokens
Protection tokens, like any other scheme, aren't perfect. The token cannot be used to unlock a service if it is misplaced or broken, or if it is not in the owner's hands. However, the owner may take measures to deter failure or stealing, such as installing locks or detectors, and the token can be made worthless to a unethical user by using 2-factor authentication, that allows the owner to have both a physical and digital object. Some use biomatric to ensure that only ethical user have access to personal data.
Security tokens may be hacked as well. It also occurs where a business owner unwittingly provides confidential data to an ethical user, who then enters it into the protected network. Man-in-the-middle scam is the term for this kind of deception. An intrusion like this will happen to any network that is linked to the Internet.
Utility Token
A utility token is a digital currency that is used to fund a network by guaranteeing that its customers will be able to purchase any of the network's goods. Utility tokens, unlike security tokens and bonds, do not confer equity rights to a portion of a business.
.png)
Since utility tokens are not mineable and depend on third-party blockchains, they should not be confused with coins (Bitcoin, Monero, Litecoin, and so on). Utility tokens, like chips, are valued solely for their underlying features and properties.
Initial Coin Offerings (ICO) often use utility tokens (ICO). When a utility token ICO is conducted, a special ammount of tokens are issued and sold to the public (mostly in several rounds for different prices). The Token owners are given exclusive rights of using the company's goods, such as being the first to use them or receiving other benefits. This method allows a corporation to raise funds without sacrificing its freedom.
These tokens aren't often found in ICOs. If the team behind a blockchain-based organization wishes to raise funds in some way, these tokens can only be used to fuel the network, serve as the currency, or for other goals.
Example of utility Token:
FunFair Project: This project is a blockchain-focused English business based in London that specializes in online casino gaming. The company's growth is primarily focused on improving casino gaming. The goal is to create a safe, equal, and distributed casino gaming platform with a user-friendly and intuitive Interface.
The FunFair token (FUN) is an Ethereum platform-based ERC-20 basic token. Because of this, it can use smart contracts and is simple to use for Ethereum users. While this tokens are held anonymously, all transactions are recorded on the blockchain. this coin can be monitored using Ethereum blockchain research solutions, which is vital for the platform's transparency.
FUN is useful both in-app and in-game purchases, as well as to promote progress. On June 22, 2017, all of the FunFair tokens were produced. There are 11 billion FUN in all. The FunFair corporation owns a bit more than 2,3 billion of them. FunFair's assets, on the other hand, are locked and will be released after an 18-month period following the token event.
Basic attention Token: This is an ERC-20 utility token that may be useful to use a variety of BAT utilities. BAT is mostly used as a payment method for content producers. The group behind BAT created it in order to build a blockchain network which will allow content producers of all types find out many other ways to earn. In the meantime, users could be rewarded with less invasive advertising on the sites that host this content.
Advantages
They have a license that helps them to create their own games without violating the law
The forum for the funfair has its own currency.
The platform's user-friendly interface enables users to migrate their web projects;
High-speed project service, as well as cash transactions;
Due to cryptographic encryption, there is a high level of reliability. Fees are low, which benefits both participants and game organizers.
Equity Token
It is a type of security token that functions similarly to a traditional stake of the underlying entity, a third-party commodity, or a venture, and derives its value from the company's success or loss. Holders actually own a share of the total business, just as they will for any equity acquisition. They will also be entitled to a portion of the company's profits and a say in its future plans.
.png)
On a blockchain, these tokens are used to monitor company ownership. Simply put, fairness means being equal and neutral. s a result, equity token investors have some level of trustworthiness in their investment in the underlying network. The token represents the percentage of their network possession.
Advantages
Its value has been maintained. Equity tokens can maintain their worth as long as the operation or company continues to function.
It's a tried and true approach. Its similarity to standard share problems, as well as its stringent oversight, make it a safe bet.
Example of Equity Token
refers to a modern way of managing and operating companies that makes use of smart contracts and blockchain technologies to provide them with unrestricted efficiency, immutability, freedom, and security. There are no particular regulations or rules that apply to DAOs.
You can also make these smart contracts as simple or as complicated as you want. They will, though, be open and irreversible until they were launched on the blockchain. All will be able to inspect the operation and the rules that have been programmed into it, so that they cannot be modified in the future.
Conclusion:
Al these token have different feature and usage. Al these are revolutionizing the world in their own way. I got huge knowledge from the proferssor @pelon53 's lecture about token and from my own research on this topic. I didn't know much about it but now i can say i have vast knowledge about token and its three types. Special thanks to @pelon53.
Gracias por participar en Steemit Crypto Academy.
Creo que tienes una confusión con los Security Token y los token de seguridad bancaria.
Faltó un poco de información en los ejemplos.
Las imágenes deben tener la fuente.
Espero ver tus mejoras en las próximas tareas.
Calificación: 4.6
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
https://steemit.com/hive-108451/@tymes2/steemit-crypto-academy-season-2-week2-or-tokens-part-1-by-tymes2
Please prof my work has been skipped
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Saludos, hoy se corrige.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
I'm glad you're working so hard! May Allah grant you more success Inshaallah. I don't know much about crypto but I can see you working hard and doing well.
Stay blessed 🤗
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Great effort very well done
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit