I
 source
source

Hello everyone.I am pleased to participate in the crypto academy class by @stream4u it was indeed a opener and I hope I have learnt a lot from it.Permit me to the homework proper.
QUESTION ONE
Blockchain Cryptography
Blockchain is arrangement of blocks (record of transaction) in chains such that each block is attached to an already existing block.While Cryptography is the science of making something secret and secure.Blockchain Cryptography is a process of creating protocols or algorithm that ensures that third-parties are probably prohibited from accessing information.The information is only meant to be accessed by the authorized recipient.
The main reason for Cryptography is to ensure the security of transactions and security of the users as well making it to be free from any central authority or intermediaries.
Blockchain Cryptography ensures that transactions or information is shared on a peer-to-peer basis between the sender and the intended reciever and not to the general public.
To further understand blockchain cryptography,let's consider the radio communication between soldiers on a mission,only the reciever gets information from the caller/sender and so the message is kept and made private within the sender and the reciever.
Working Principle
In Blockchain Cryptography,the sender uses his private key and digital signature together with the recievers public key to encrypt the message such that no other person can decrypt it except the reciever,once the encrypted message is sent out,the reciever uses his private and public key to decrypt the message and then claim the reward.
The encryption makes it impossible for another user except the intended reciever to decrypt the message,this is security at its best.
Inorder to strengthen Cryptography in blockchain, encrypting can also be achieve through hashing and digital signatures.
Hashing involves using a input of any length to generate a unique output of a fixed length.Hashing ensures that there is Immutability and irreversibility
in transactions because the output hash cannot give back the input.Digital Signatures are used to ensure or verify whether a transaction is true or not.
Examples of Blockchain Platform
•Bitcoin Blockchain
•Binance Smart Chain
•Ethereum Blockchain
•Tron Blockchain

QUESTION TWO
Public Key Cryptography
Public keys are shared publicly in the blockchain.It can be shared public without its private pair,the presence of hashing algorithm makes this possible as it is only the node with the corresponding private key(authorized node) can interprete the message sent.
The public key is a combination of alphanumeric data that is used to encryption of plain text to a ciphax text which is now broadcasted on the blockchain.
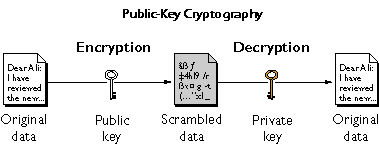
Public key Cryptography involves a pair of keys which is known as a public key and a private key which are associated with an entity that authenticates or validates its Identity electronically.When a public key is published,its corresponding private key is kept secret.The public key is used to encrypt the message such that only the private key that corresponds to it can be used to decrypt the message.
It is important to note that the public key enables encryption and decryption between the sender and the reciever such that no other node can read it.How it happens is that the sender will encrypt the message before sending it out,and the reciever decrypts the message upon receiving it.In this way,no third party can decrypt the message.This message sent from the sender to the reciever cannot be altered or deleted,this makes it to be secured by cryptography.
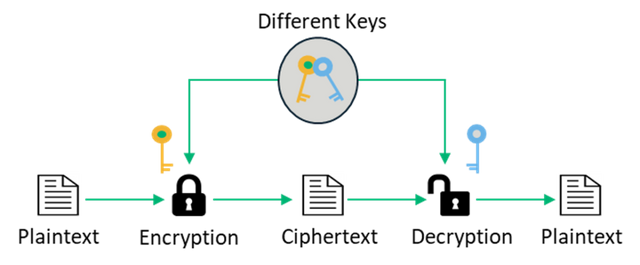
To make this Public Key Cryptography more Simpler,let's look at this image below 👇
From the image above,you can see that the data is first encrypted to a scramble with the private key of the sender and public key of the reciever,once the message gets to the reciever,he now uses his private key which corresponds to the public key used for the encryption to decrypt the message into a plane text.

QUESTION THREE
Private Key Cryptography
Unlike the public key,the private key is kept secret and never made public or broadcasted in the network.
The private key is a long,randomly generate sequence of bits that is almost impossible to guess.It is the only the owner of the private key that has access to it.It is used to decrypt an encrypted message.The decryption by the private key is possible when the public key used for the encryption corresponds with the private key.
The private key works together with another form of cryptography called digital signature-which helps to verify the identity if the sender and also makes sure that the message or transaction sent is tampered with.
Private keys designed in way that they automatically generates,signs and verify transactions with the highest level of cryptography with the private key which is attached to the given wallet.
Salient Points about the Private Key
•The strength of a private key depends on its length and randomness.
•They are not shared to the public.
•They must be kept in a secure place more preferably offline.

QUESTION FOUR
Digital Signatures Cryptography
Just like in the traditional banking system,a user signs his signature on a cheque book or withdrawal slip to sure that he authorized the transaction.
Digital Signature is an authorization technique that uses mathematical algorithm to validate the authenticity and integrity of a message.Digital Signature is achieved by combining the private key and public key to sign and verify a transaction in the blockchain such that only the authorize reciever can access it.
Digital Signatures ensures cryptography by ensuring that the message was not altered right from the moment it was signed.This is achieved through an algorithm called hashing.
To achieve this,a unique hash to generated for the message and it is encrypted with the senders private key.This is highly secure because once any part of the message is altered,the hash will automatically change.
On the part of the reciever,once the recievers gets the message,he generates his own hash of the message and decrypts the senders hash,using the public key of the sender.The reciever will now compare his own hash with that of the senders hash,if they corresponds,it means that the sender is authenticated.
What is Signing of Transaction/Message
Signing of transaction simply means using a digital signature on a transaction with the combination of the private key to ensure that the transaction is correct and authentic in the blockchain and also to authenticate to the reciever.
In the case of exchange wallets,the private key automatically generates and signs the digital signature.

QUESTION FIVE
Symmetric and Assymetric Cryptography

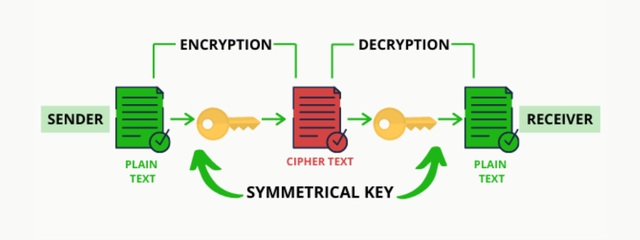
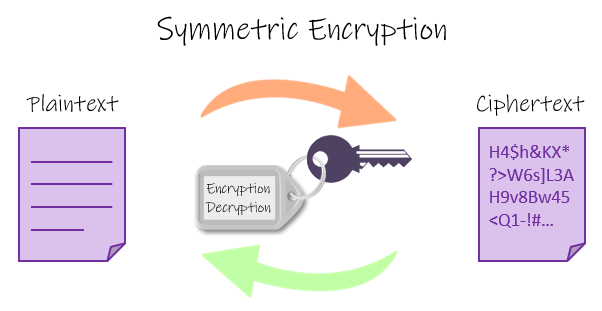
•Symmetric Cryptography:
This is a type of Cryptography where the sender and Recievers share a single key which is kept very private and confidential.This single key is used for both encryption by the sender node and also for decryption by the reciever node.It is important to note that this key is accessible to both the sender and the reciever.
How it happens is that the single key is first used by the sender to encrypt the plain message/text into a cipher text which cannot be read by human and it is broadcasted on the blockchain.
Once the reciever is identified,the reciever uses the same key to decrypt the cipher text into a readable plain text.
This Symmetric Cryptography is much more faster and it can employ any of these encryption technique👇
•Stream Ciphers:Recall that ciphers are encrypted mesages that are not human-readable.Stream Ciphers encrypts the letters of the message one at a time and broadcast it without storing it.
•Block Ciphers:This technique encrypts a group of bits and it is stored in blocks and all broadcasted to the blockchain when the last information is encrypted.
Since Symmetric Cryptography is faster and quicker,it has found application in the following areas:👇
•In Hashing and creation of Random number.
•Payment applications like bank purchases where identity theft needed to be dealt with.
•In bulk encryption-to encrypt a large volume of data.
Examples of Symmetric Cryptography are:
• Rivest Cipher 4,5,6.
•Advanced Encryption Standard(AES) etc.

•Asymmetric Cryptography:
This is a type of Cryptography that where two keys are used.The two separate keys works in synergy with each other.They are the public key and the public.The are used for the two main functions which is encryption and decryption.
The public is is made public and can be shared among connecting nodes in the blockchain and it is used for translating plain text into cipher text(encryption) while the private key is kept secret and itv used to translate the cipher text to a plain text (decryption).
To further understand this,the asymmetric cryptography operates in a way that all the nodes in the network can share the public key which is used to encrypt a message,sign it digitally and then broadcast it openly in the blockchain.Once the reciever gets the message,he now uses the private key to decrypt the message.
When any node wants to broadcast an encrypt a message,he uses the recievers public key to encrypt and so the recievers can use the corresponding private key to decrypt the message.
Asymmetric Cryptography is more secure than the symmetric cryptography because the sender and reciever do not share a single key.Asymmetric Cryptography also helps to
check the authenticity of a transaction using digital signature.
Examples of Asymmetric Cryptography are:
•SSL/TSL Cryptographic Protocol that's provides encrypted connection between websites.
•the Digital Signature Standard (DSS)
•Elliptical Curve Cryptography (ECC) etc

QUESTION SIX
Blockchain Wallet Cryptography
A crypto wallet is a program or software which is used to store private keys and to hold crypto assets.A wallet stores the private key which grants the owner access to his funds.Once the key is lost,it may be impossible to access the crypto assets stored in the wallet.A crypto wallet
can also be said to be combination of private key and public address and a private key.It can also be used to encrypt and sign information.
A crypto wallet could be online or offline depending on the choice of the user.
A crypto wallet has a random generated number called the private key which is used to generate a public key.The private key is used to by the owner to access his wallet and to send/transfer cryptocurrency while the public key is shared to any node on the network to be used to recieve cryptocurrency.The public key is like our bank account number,we can give it to anybody to make payment with it by our private key is like our debit card pin or signature which is more the privacy of the owner.
Cold and Hot Wallet
Like I mentioned in the earlier paragraph.A Crypto wallet could be offline or online.
Cold Wallets are offline wallets that holds the keys to the users crypto assets.This type of wallet has the keys stored offline in harddisk and so it is highly secure because it is not present in the internet.It is almost impossible to hack an offline wallet.
Hot Wallets are online wallets which exist on the internet which holds the keys to the users crypto assets.Hot wallets are not very secure because its presence on the internet makes it subject to hacking.
Types of Wallet
There are basically three types of wallets.They are hardware wallet,software wallet and paper wallet.
•Hardware Wallet:
This are external hardwares that are used to store crypto assets and keys in an offline form.It is connected to the internet and do is more secure.
By appearance it looks like a USB and can be connected to a PC when it needed to to be used.The user id a hardware wallet has full control of his funds and keys as it is not on the internet.Trezor and Ledger Nani S are examples of hardware wallet.
•Software Wallet:
Software wallets are the opposite of hardware wallets.The software wallet stores the users access keys and crypto assets on a software program which is assessed on the internet.Soft wallets could be held on Exchange Platforms (like my wallets on Binance Exchange) or on a Decentralized Exchange Platforms (like trust wallet).It is important to note that software wallets are not very secure especially the ones in Exchange Platforms.
Examples of software wallets are;
Desktop wallets-which are available on Operating Systems,
Mobile wallets-which are used on Android and Smart phones,
Web wallets-which are accessible by internet browsers.
•Paper Wallet
This is a type of wallet this stores crypto assets offline in a paper form.In this method,the values are stored as hardcopy as in physical documents.It cannot be used to send partial funds and once the paper is lost,all the funds are gone.

QUESTION SEVEN
Merkle Tree and Its Importance in the Blockchain
Merkle Tree is named after Ralph Merkle who proposed it in 1987.We all know that a hash is a non reversible process that can be used to verify the authenticity of a transaction in the blockchain.However,a hash cannot be used to generate the original set of transactions.
A Merkle Tree is therefore an arrangement of hashes in the blockchain in such a way that each hash is represented in the root hash(genesis hash).
The beauty of the Merkle tree is that it allows users to verify transactions easily without downloading the whole blockchain.
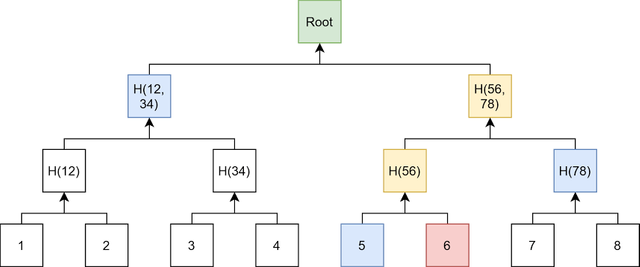
In the Merkle Tree arrangement,the first hash from the bottom are called leaves,the follow hashes are called branches while the top most hash is called the root hash.Let's look at the illustration below.👇
•The Transactions,T are 1,2,3,4,5,6,7,8 and they were hashed using a hash function to get the first set of hashes called leaves
•The first set of hashes H(12),H(34),H(56) and H(78) are the called the leaves.
•The leaves were further hashed to get the get the second set of hashes called the branches which are:H(1234) and H(5678).
•The branches H(1234) and H(5678)were hashed to get the root hash.This root hash contains all the hashes of the transactions in the blockchain.
Importance of Merkel Tree
•It saves time because the miner does not need to go through all the transactions stored on the block before validating a block.
•It reduces memory space because the evidence required are computational straightforward and faster.
•It supplies a means of verifying the integrity and validity of data because any alteration in the hash(say leaves or branches) changes the root hash.
QUESTION EIGHT
Practical+ Theory Using blockchain demo
Keys
There are two sets of keys which are the private key and the public key.The private keys is kept secret while the public key is shared to the nodes in the blockchain.When I Visited blockchain demo...I clicked on Keys.
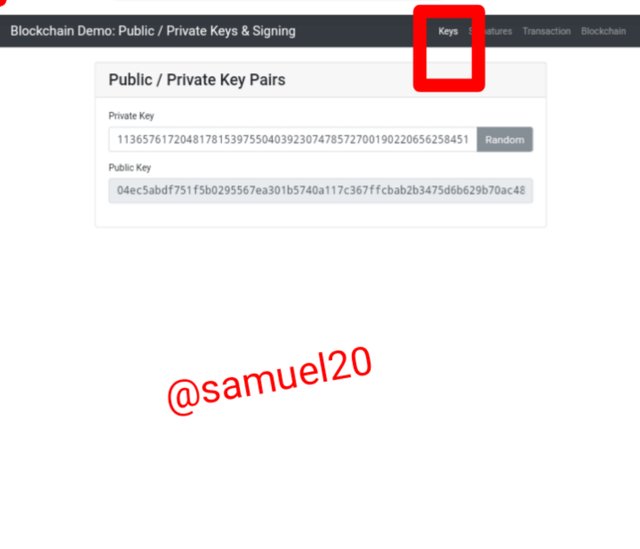
Private key:
113657617204817815397550403923074785727001902206562584513099381314749798024050
Public Key:
04ec5abdf751f5b0295567ea301b5740a117c367ffcbab2b3475d6b629b70ac48b684ca45080d32af4eb560f7ca79befee78e8307397b0755c2a3dc35c6c9c51af
•Inorder to explore the site.I decided to delete private key and I introduced my own private key as:4321 and automatically it generated a new public key with the private key of 4231👇
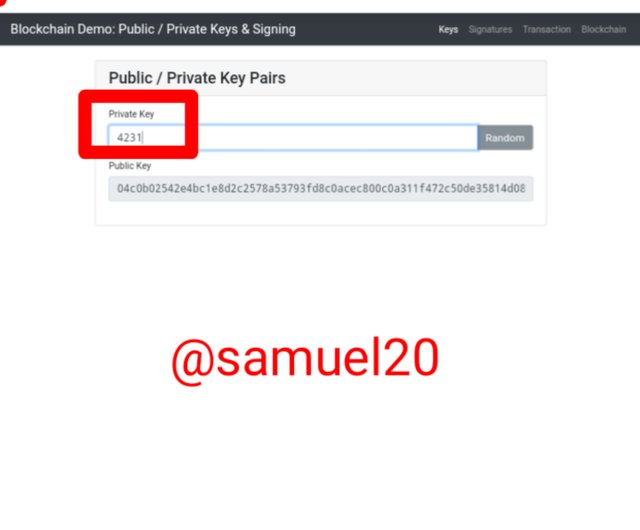
Private key:4231
Public Key:
04c0b02542e4bc1e8d2c2578a53793fd8c0acec800c0a311f472c50de35814d081024bdc710f5917c001ae6bb571c0919776b1a884ebffd67313698bc1b57f8371
This proves to me that all private keys have a unique corresponding private key.This accounts why the recievers public key can be used encrypt a message by the sender.
Signature
Next I moved to the Signatures to explore Signature section.Signatures are used to ensure the authenticity and veracity of a transaction.The Signature has two features which are:
1.Sign
2.Verify
•Sign In Feature:
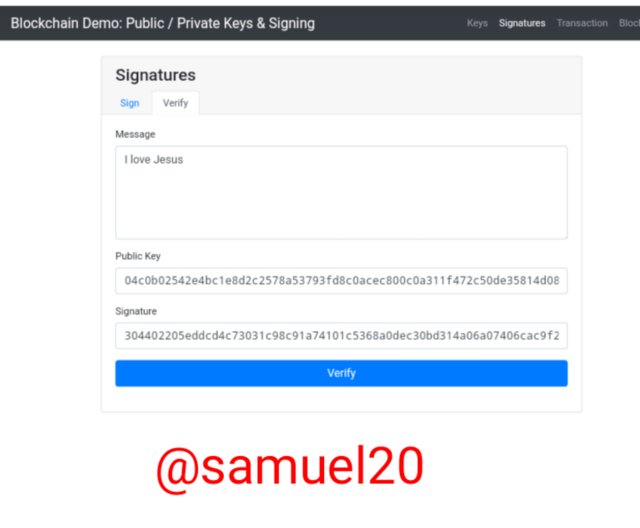
I entered a message which is "I love Jesus" and I want to generate a signature for it.
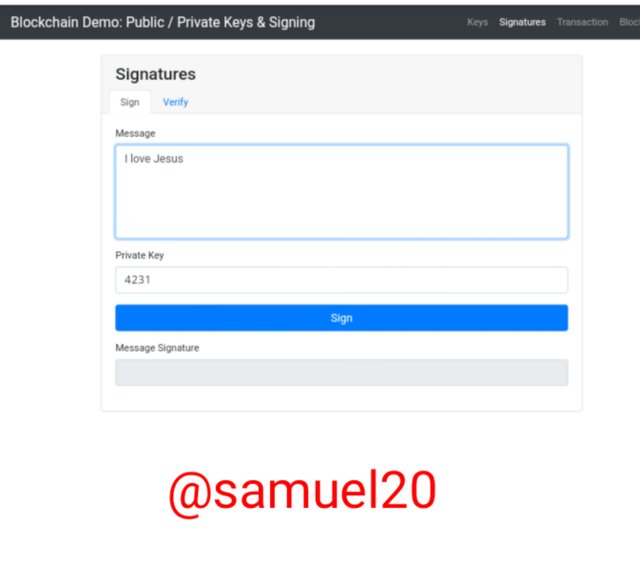
After I clicked on Sign,the system generated a signature for the message "I love Jesus".
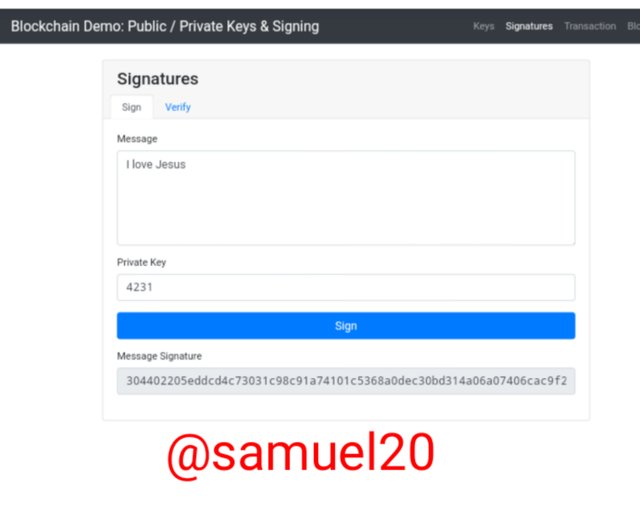
Here is the generated Signature:304402205eddcd4c73031c98c91a74101c5368a0dec30bd314a06a07406cac9f22b37f1702207182d9c692ad6d01be513cde6d45163b9318be19d9f9c9b4b582ef95c2757806
•Verify Feature
Now I can to verify the transaction.The senders Signature and Public key is used to verify the transaction or to ascertain the validity of the transaction.
Transaction
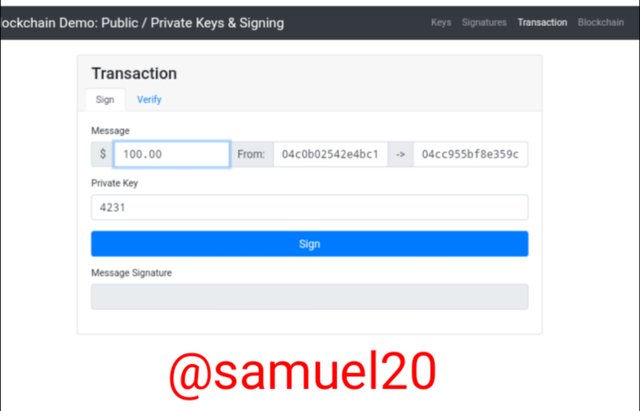
Now I have moved to Transaction section.This section shows how transaction happens on the blockchain.The sender uses the public key of the reciever to encrypt the transaction and then broadcast it to the network.Here i sent $100.
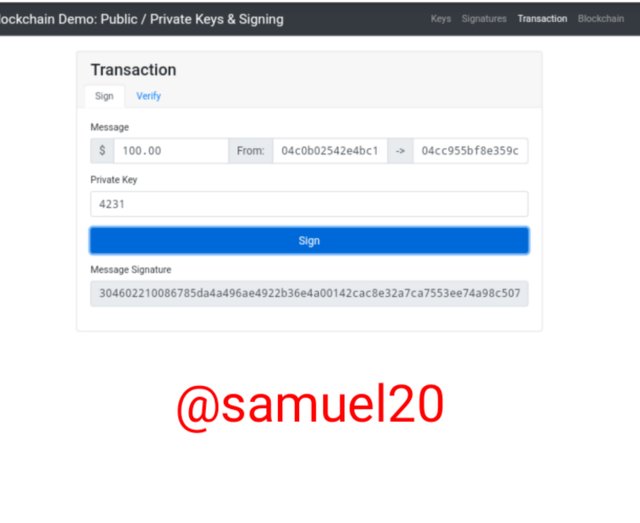
Then the sender have to sign the transaction.And I got a signature for the transaction.
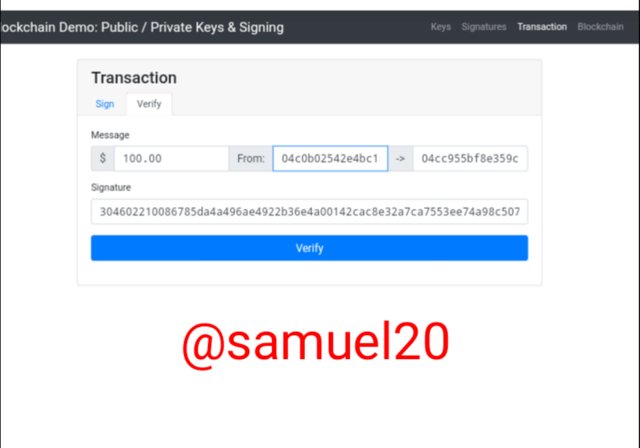
Next is to verify the transaction.Once the senders Signature corresponds to the Recievers Public Address,the the transaction is said to be valid.Otherwise,it is invalid.
Blockchain
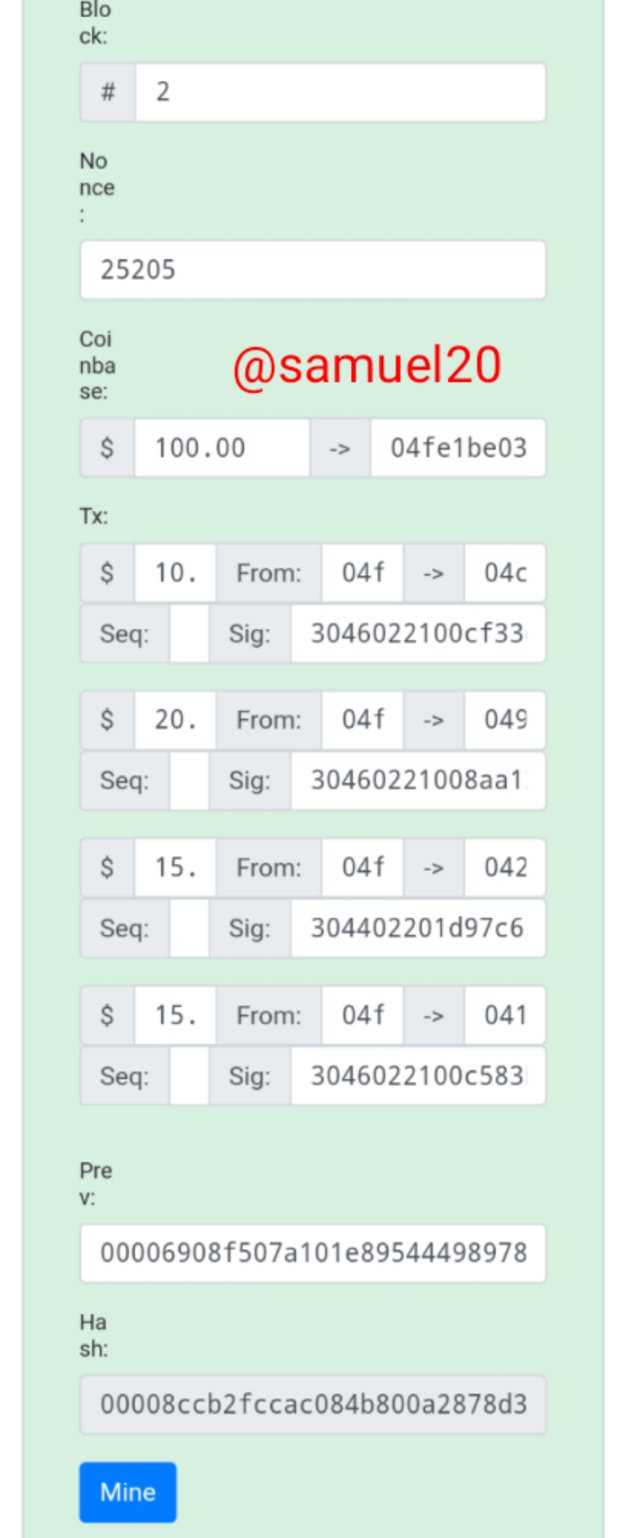
This is the last section.This shows how transactions are recorded on the blockchain.I am using block 2 as a case study.
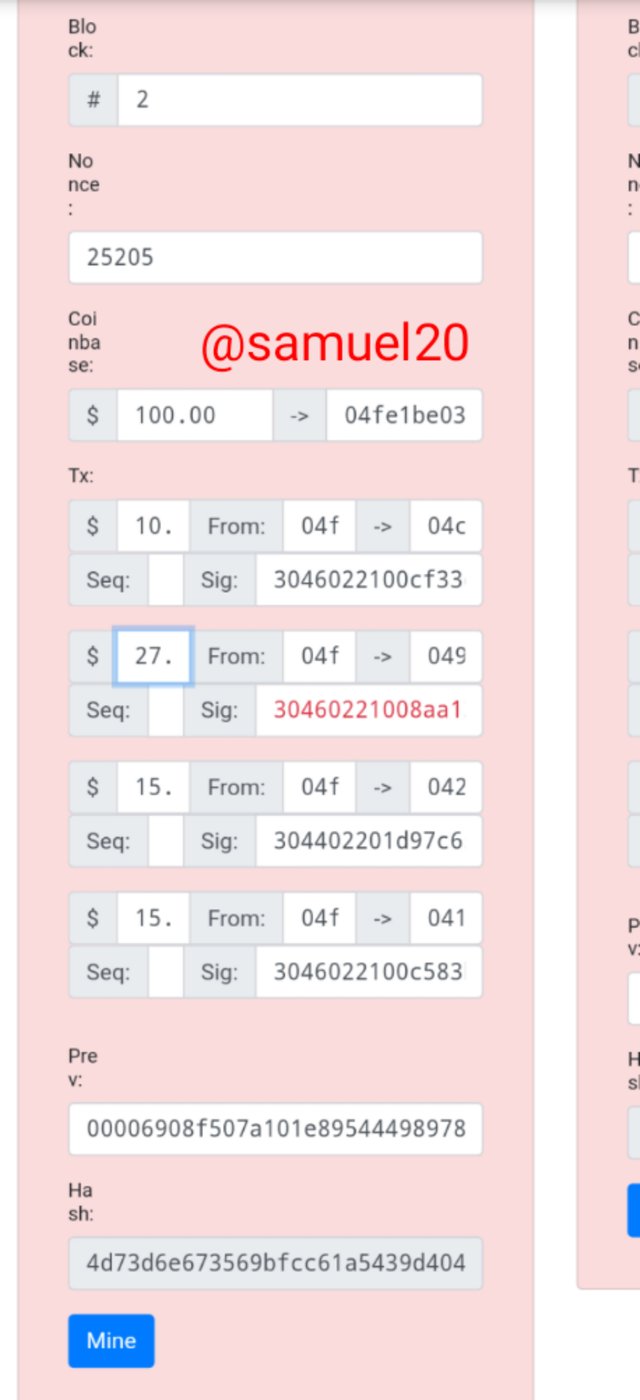
From the list of transactions here,I decided to take a risk by changing one of the transactions from 20 to 27*.
Immediately I changed the value from 20 to 27,the thing showed a red flag which means that I have altered the sequence name so it is no longer invalid.This shows that blockchain technology has a high level of Cryptography.

Conclusion
Blockchain Cryptography is the process by which information is made private and secure such that only the authorized reciever can access the information without the interference of any third-party.This involves the use of private and public keys to encrypt and decrypt the information.The sender encrypts the information with the recievers public key and the senders private key into a format that cannot be read by anyother node except the authorized node,while the reciever decrypts the information then can access it with ease.
Symmetric Cryptography involves the sharing of a single key by both the sender and the reciever while Asymmetric Cryptography ensures that the sender and reciever do not share the same key.
The Merkel Tree is way to save time and storage space by making it possible to validate a block without downloading the entire blockchain.In the Merkle Tree,each hash of the leaves and branches is represented in the root hash.
I thank professor @stream4u for this wonderful class.
.png)
wow very nice my friend
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit