Q. What is a Cryptocurrency? What is Cryptography and how does it make cryptocurrencies secure? Explore the Steem Genesis Block and Sign in as proof of completion.

a) What is a Cryptocurrency?

The word cryptocurrency is derived from "cryptography".
But from my little observation, one can see that the word cryptocurrency can be a compound word made up of each "crypto" and currency. We all know this 2 word as cryptocurrency.
For a better explanation, I am understanding these 2 words, so it makes sense to make a North American nation what a cryptocurrency is.
Based on my very little analysis, the word "crypto" is understood to mean completely hidden, secret, or hidden from information, while the word "currency" may be a very fashionable word derived from the Latin word. Known as "Karre". suggests that "a medium of exchange for products and services.
So at present I think it is safe for me to mention that crypto-currency is purely a secret way of completing transactions or a secret type of exchange medium permanently and services, because my lot on every word. So less analysis suggests.
I am not disputing the fact that the term crypto-currency originated from cryptography, I am merely spreading my own reading of what I believe is cryptocurrency.
Now, what is lot cryptocurrency??
Crypto-currency is defined as a digital currency within which a transaction area unit is valid and records are being maintained by a local blockchain/system victim "cryptography" within the function of central authorities such as central banks.
It is a unique exchange that is being viewed online, permanently acting as a form of payment and repair.
Crypto-currencies are collaborative in nursing, adopting the method of peer-to-peer transactions as it is localized and there is no central authority to manage transaction activities.
A person holding a crypto currency would not like to deal with it, as such a person has premium management unlike a traditional currency which is under the management of a central authority.

b) What is Cryptography and how does it make cryptocurrencies secure?

Cryptography:
A technique or strategy is to convey or transmit a hidden, hidden or cryptic message, idea, or data to a person or several people who understand it and can decode it to inspire an important message or plan.
Without this idea (cryptography) I don't think crypto-currency would be successful, as we look at the square measure we experience these days. Furthermore, cryptography is the main tool for keeping crypto-currency secret and secure;
• Protecting cryptocurrency from intrusion
Any attempt or attempt to allow group action or double payment in a cryptocurrency peer-to-peer, without the involvement of any third party or intermediaries, and the central authority Stay protected from theft and interference with
use the keys to operate
The cryptography used in crypto-currency additionally involves 2 keys, which fully measure "private and public keys".
Public key is the pocketbook address that belongs to anyone whereas non-public secret is like a signature of someone famous only to the owner. The group action may not be valid while it is not a non-public key.
The result is a signature for any group action language similar to the language on the check within the actual industry.
Once the crypto-currency is distributed to an individual's pocketbook, the non-public secret is used in the decrypting operations, resulting in a much smaller chance for someone else to steal your coins. You don't have a non-public key. Proof and signature of the owner.
• Hashing
The use of "hashing" is the conversion of information into text strings that are used to verify the authenticity of the information, thereby keeping cryptocurrencies safe, secure and free from danger, unlike traditional currency.

c) Explore the Steem Genesis Block and Sign in as proof of completion.

Step1- to sign in firstly click on this link that is
https://steemworld.org/
Step2- after that tap on block explorer
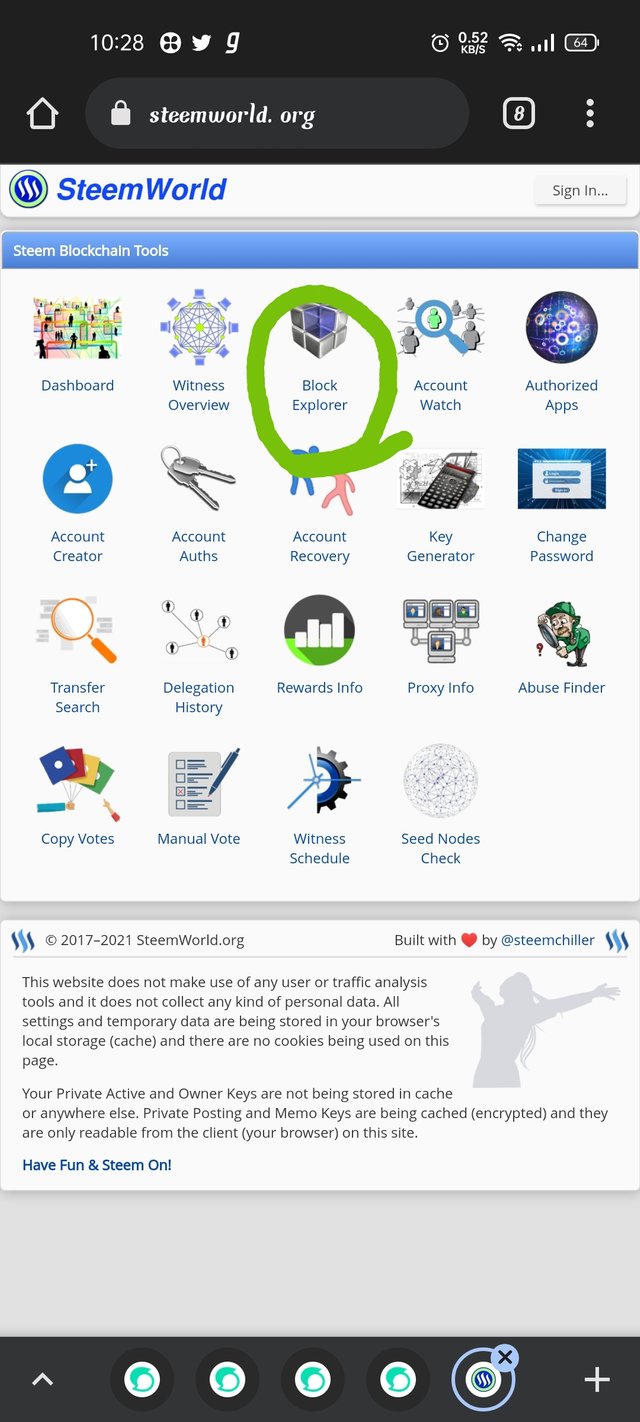
Step3- then new slide is open after that click on ok
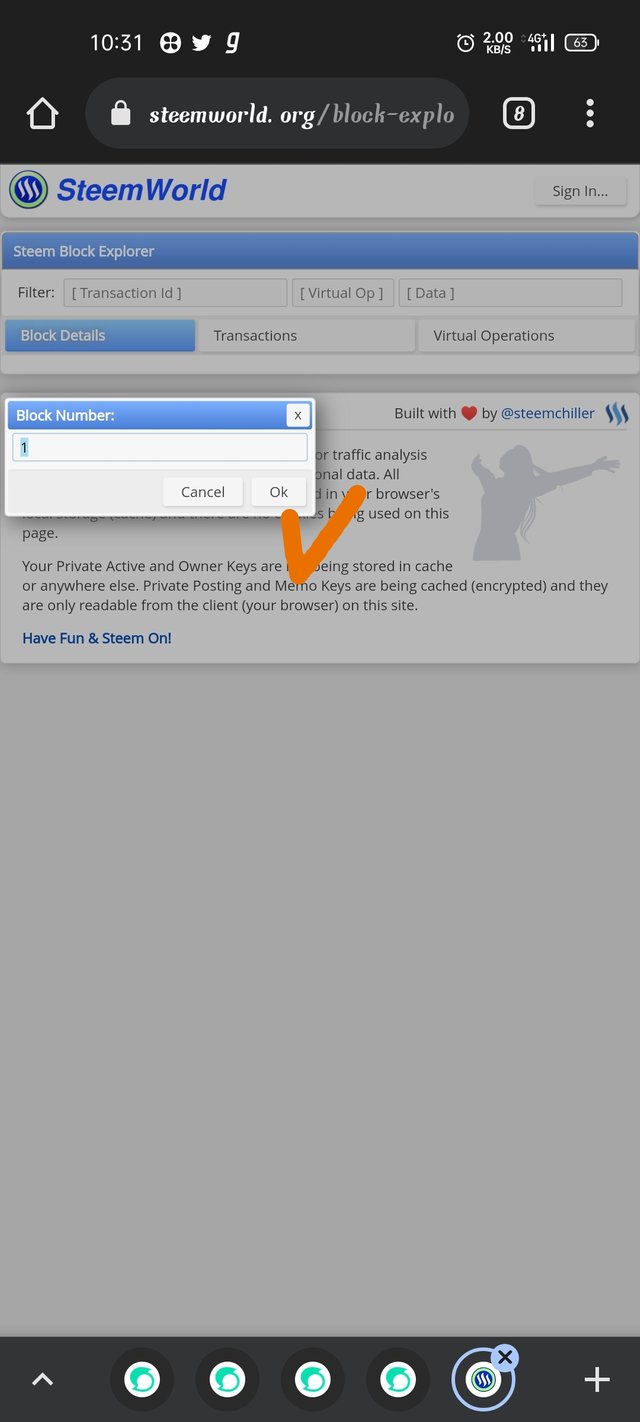
Step4- then new slide is open
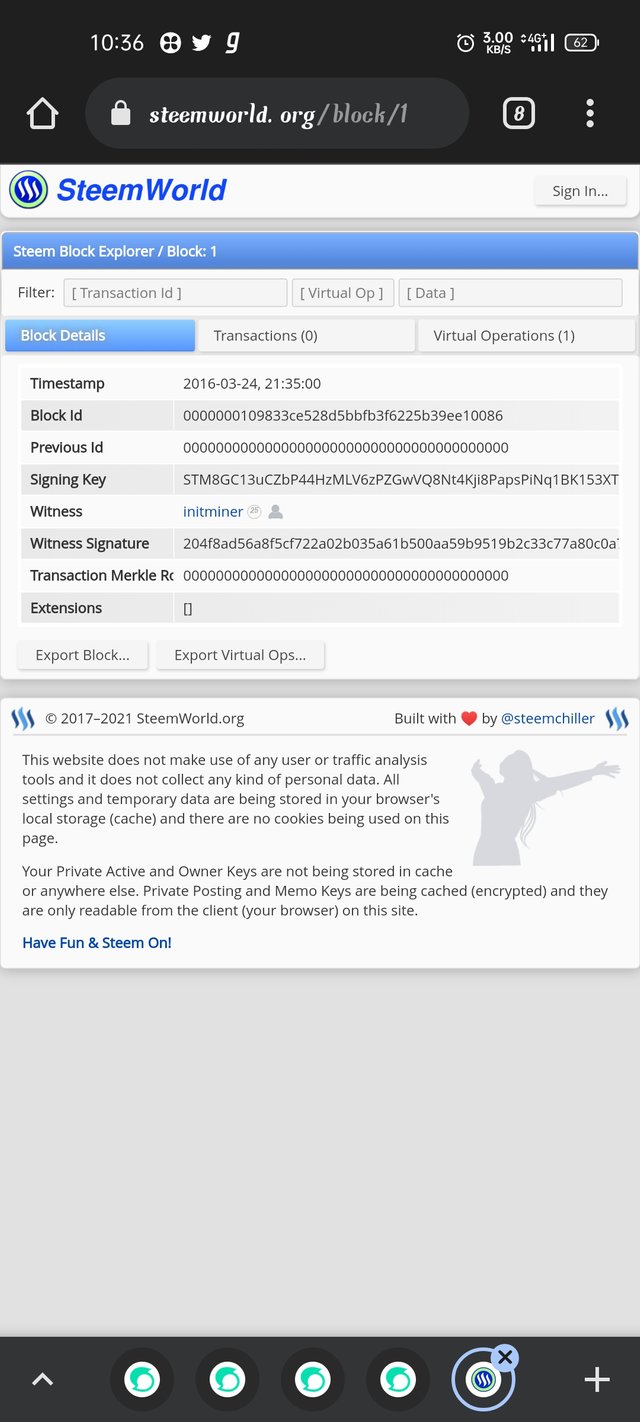
so you see the information above
Timestamp- 2016-03-24, 21:35:00
Block Id - 0000000109833ce528d5bbfb3f6225b39ee10086
Previous id - 0000000000000000000000000000000000000000
Witness- initminer
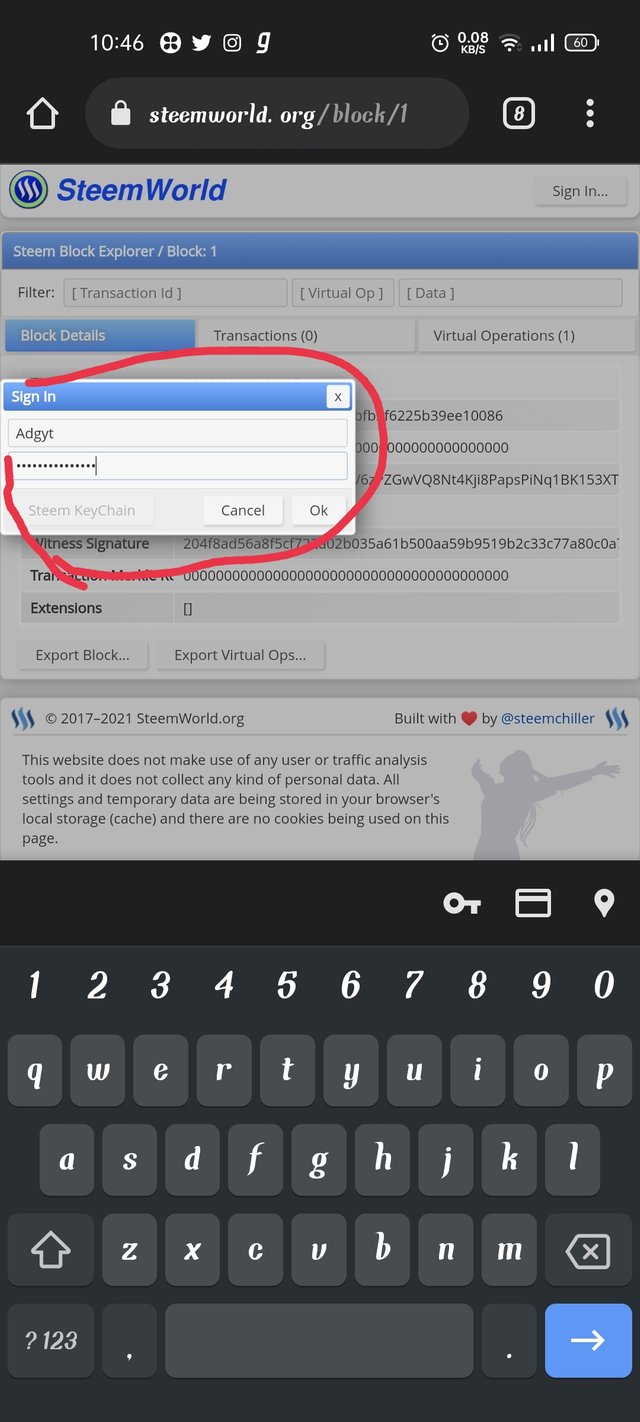
Step5- sign in by clicking on sign in button
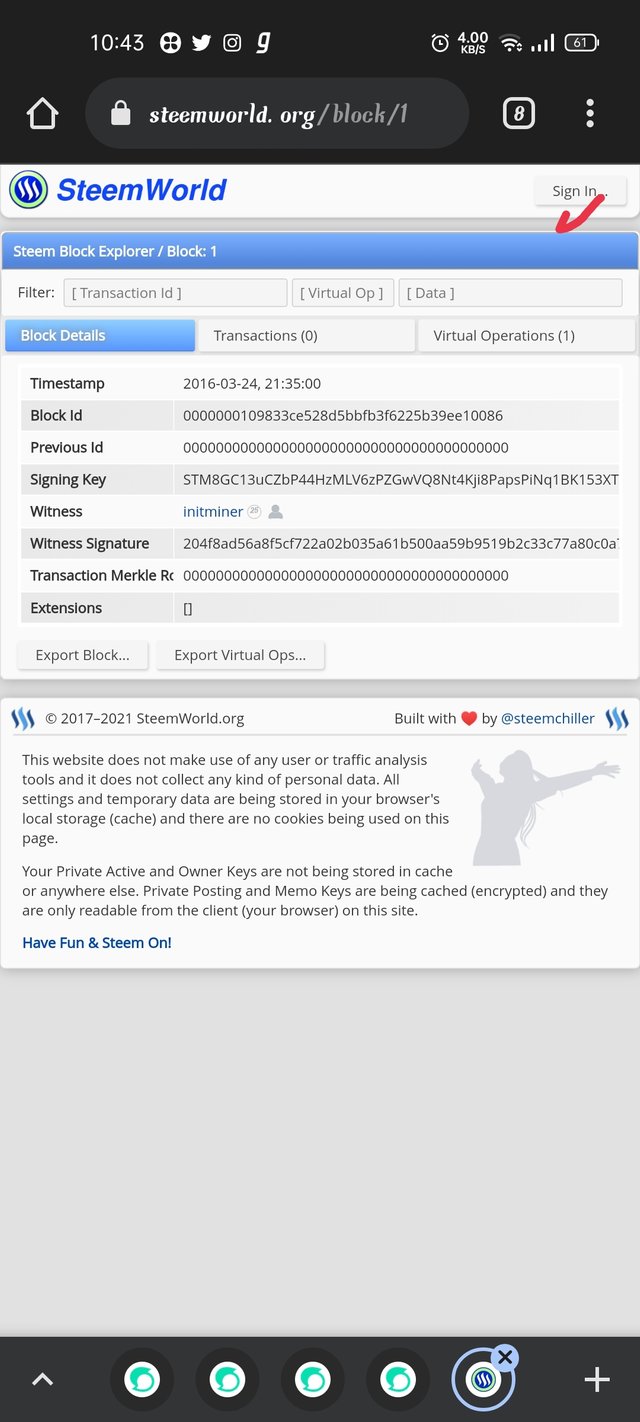
Step6- then write your STEEM Id and password after that you are in ...

Conclusion

The day is the opposite measure when it involves cryptocurrency, anonymity and concealment. And each one of these various cryptological techniques tries to confirm that these goals have been achieved, and to ensure that users and their activities remain hidden to the extent necessary on the network.
.jpeg)
.jpeg)
#club5050 😀
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit