
Hello everyone, I am very happy today to make a summary of my findings to the week's lecture with professor @pelon53. I would like to use this opportunity to say a very big thank you to the professor for his wonderful lecture this week. I must say that it was a great class. This week is all about Hash Cryptography Etherscan tronscan, I will be making my submissions based on the questions asked by the professor.
Before I dive into the subject matter, I will like to make some points clear, which is, what is Hash.
Hash
Hash has been defined as a cryptography function or algorithm that performs its task by helping users generate alphanumeric code from a given summarized data. This also has the ability to secure and make data safe due to the nature of the converting of data into sensitive 64 alphanumeric characters which have been summarized. Further simplicity to what Hash is.
A secured working environment is created for users since the codes are highly secured.
Hash has 64 character case sensitive which makes them very unique.
Hash makes available a secured environment for its users by securing the data.
A long time frame is required to develop from MD2 to SHA-256.
Some Uses of Hash
- Hash is used in the mining of crypto.
- Hash is used to generate keys for crypto wallets and addresses.
Cryptography
This term simply means the method in which protection of information is employed with the help of using codes. This gives opportunity to only those whom the information is messaged to read. The major aim of this idea is to secure transactions that occur from different platforms.
The three types of cryptography are;
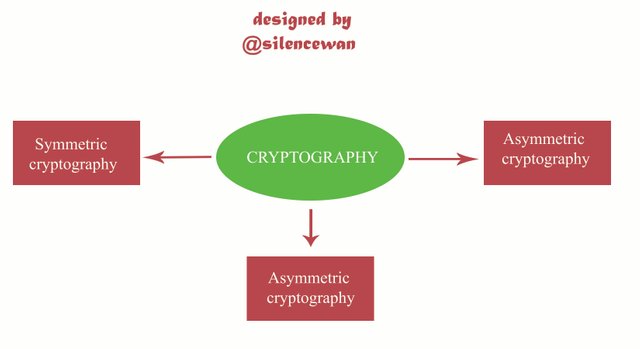
Symmetric cryptography: This type of cryptography deals with only one key function.
Asymmetric cryptography: This type of cryptography deals with two keys. These are; Public key and private key cryptography.
Hybrid cryptography: This is the combination of the use of both symmetric and asymmetric cryptography.
Question One: Explain what does the resistance to collision mean? And what does resistance to preimage mean?
Resistance to Collision
This is said to be a property of a hash function that is said to be computationally infeasible in finding two inputs colliding. his technology was developed by Sir Rabin in 1978
This term, Resistance to collision can further be explained as, a property in which cases where there are difficulties in finding two inputs for the same output then it results in a collision property in a hash function.
This is really necessary due to the importance it shows in securing data from hackers.
Let's consider this example, assuming we have two inputs which are H(S) and then H(T). These two hash functions can show a collision property if the two hashes short in value, thereby not equal to the value of the inputs S and then T.
Resistance to Preimage
This is said to be a property of a hash function in which is very difficult to come, invert it, meaning if there is a given element that falls in the range of a hash function, then it is said to be infeasible computationally in finding an input which will map to that element. Or a technology that secures and suppress preimage attack on hash
There are two mainly types of preimage resistance. These are;
- Preimage resistance
- Second preimage resistance
I will further explain this two to give a better understanding.
- Preimage resistance
This is a property of the hash function which secures data that is difficult in finding information from the hash code.
An example is;
Let's employ N as our input and also M as our output, it means that H(N) and also M will be the same but very difficult to hack and then decode. H(N)=M
*Second Preimage Resistance
The second Preimage Resistance is a property in which it is very difficult in finding two inputs for the same output.
An example is if the two inputs N and then M, where N not equal to M, the property will hold since there will be no out of P
Question Two: Use tronscan and etherscan to verify the hash of the last block and the hash of that transaction. Screenshot is required for checking.
In this question, I will be using tronscan and etherscan to verify the hash of the last block and the hash of that transaction. Screenshot is required for checking.
Etherscan
First of all Search Etherscan on google then click on the website link.
Once it's opened to the site, you will find on the main screen two different options one is latest blocks and the other one is latest transactions.
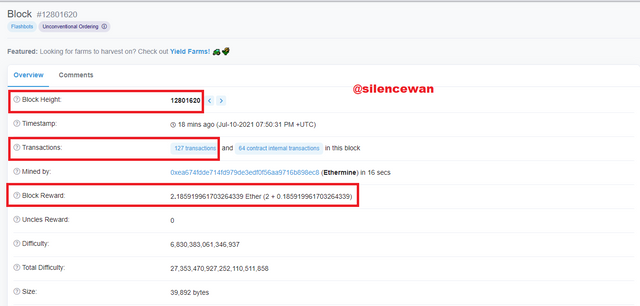
What I do next is to click on one of the blocks to display the features such as block height, hash code, number of transactions, the block reward, and so on.
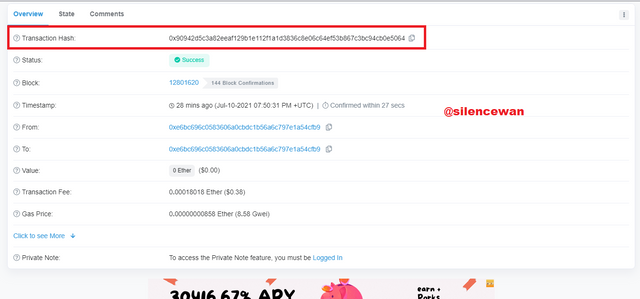
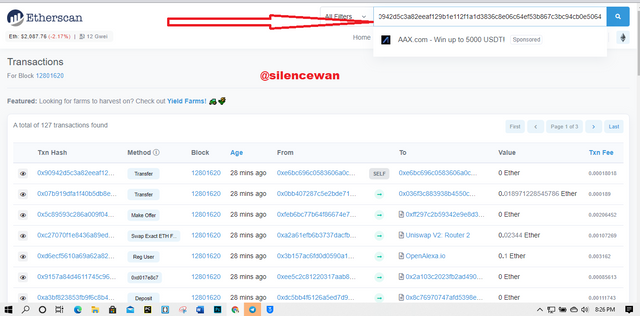
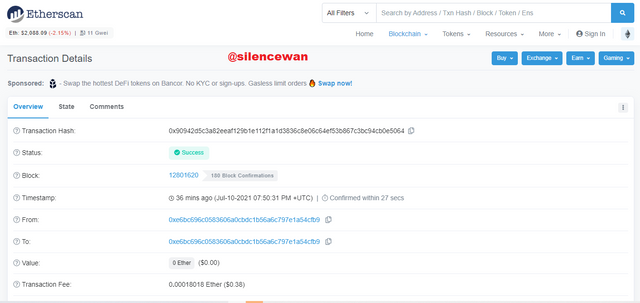
This step here is to copy the Transaction hash and paste it into the search bar to verify the transaction. Check whether we get the same transaction or not.
Once you paste it in, the process will be verified after pasting.
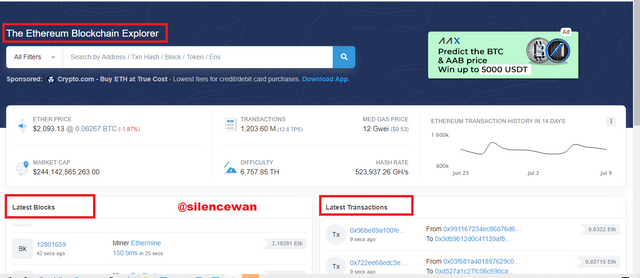
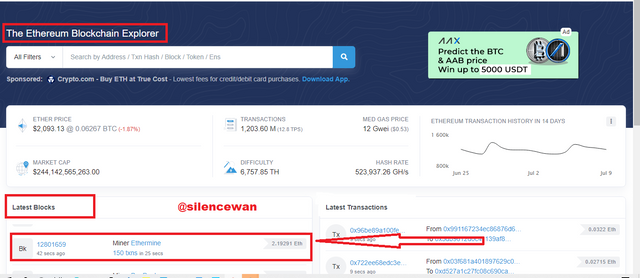
Block Height: 12801620
Block Hash: 0x90942d5c3a82eeaf129b1e112f1a1d3836c8e06c64ef53b867c3bc94cb0e5064
2.185919961703264339 Ether (2 + 0.185919961703264339)
Status: Confirmed
I then clicked on 127 transactions to view the transactions list then selects one transaction and then view the details of it.

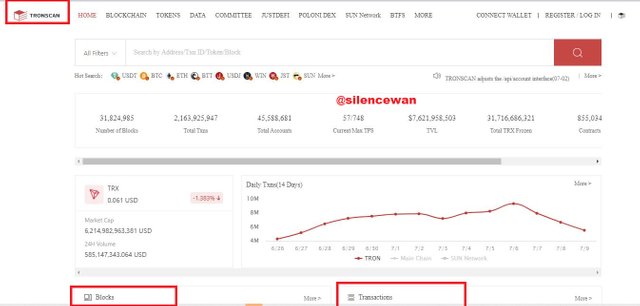
Tronscan
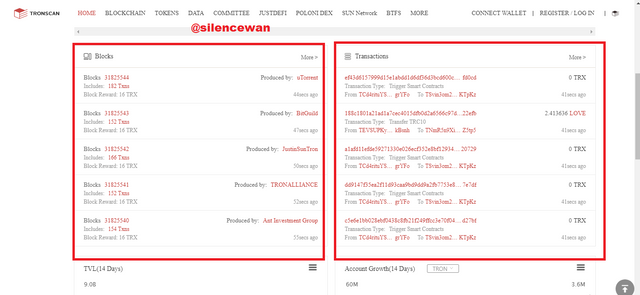
- Search Tronscan on google and then open the link to the website.
2.We can find two different tabs as in the Etherscan, one is blocks and the other is the latest transactions.
Click on the blocks option where you can see the block details like block height, hash, transactions, rewards and so on.
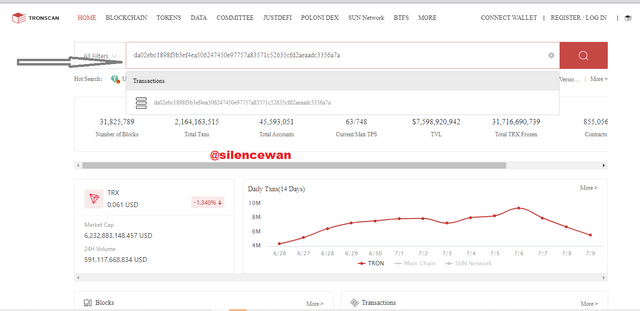
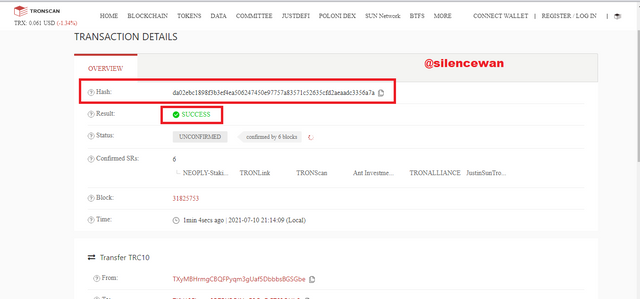
This step here is to copy the Transaction hash and paste it into the search bar to verify the transaction. Check whether we get the same transaction or not.
Once you paste it in, the process will be verified after pasting.
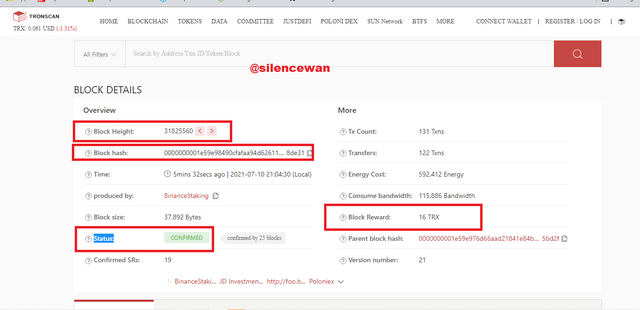
Block Hash: 0000000001e59e98490cfafaa94d626119d4e3a37f4126b5a18f8b55aba8de31
Block Height: 31825560
Block Reward: 16 TRX
Status: Confirmed


Question Three: Generate a HASH using SHA-256, From the word CryptoAcademy and from cryptoacademy. Screenshot required. Do you see any difference between the two words? Explain.
The steps below will serve as a guide on how to generate a Hash code for two given words using SHA-256.
- First I visited the SHA-256 website by searching from google. source
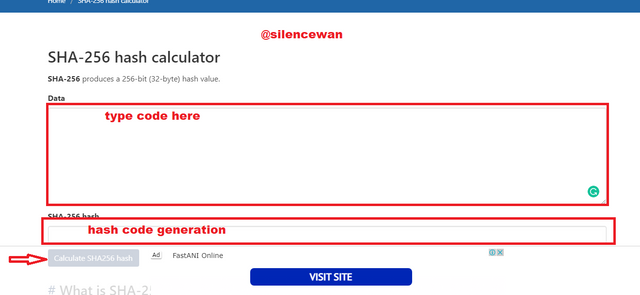
- On the main window, you will type the input for which you want to create a hash. Click on generate button after typing the input.
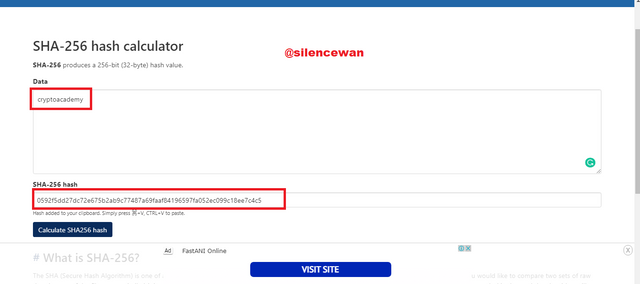
Hash code: 0592f5dd27dc72e675b2ab9c77487a69faaf84196597fa052ec099c18ee7c4c5
- So now I do for our second input which is CryptoAcademy. So its respective hash code is given below
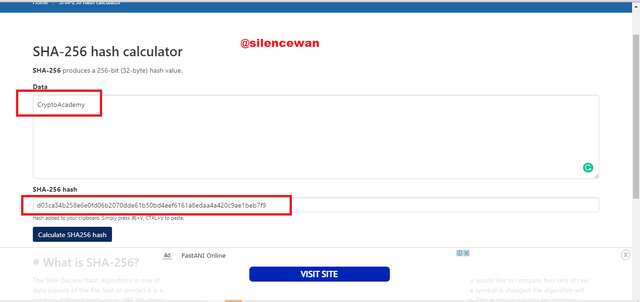
Hash code: d03ca34b258e6e0fd06b2070dde61b50bd4eef6161a8edaa4a420c9ae1beb7f9
So I can now explain the results I have generated. Those in the two codes that have been generated. We know that the computer works in binary form that is the os and 1s. So therefore the computer grants some specific numbers with regards to specific commands. So we know that there is a difference between the letters a and that of A and also c and that of C. We know that, these letters are all case sensitive which makes their generated codes very different. So if both the inputs where the same, then we would have seen the same hash code for them due to its sensitive nature we have seen that,they are both different. It simply signifies how these codes are both treated differently in the machine language also the binary language.

Question Four: Explain in your own words the difference in between Hash and cryptography.
I will make the difference of a Hash and Cryptography in seperate folds. That is differentiating for Hash and then for Cryptography.
Cryptography
In Cryptography, there is no requisitionof a key for encryption but requires a key during decryption.
We know that, the major use of Cryptography is to send data to other user safely and on time with full security and also make available a user friendly environment.
This is said to be a two direction process both encryption and decryption take place.
In cases where there is decryption, then the original input can be retrieved.
Also, It contains large information in an extensive amount.
Example code :-
Input: I am in the person of silencewan
Output encryption
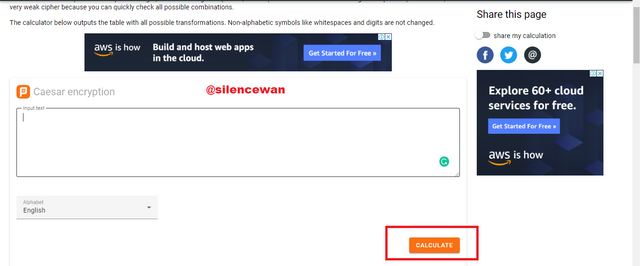
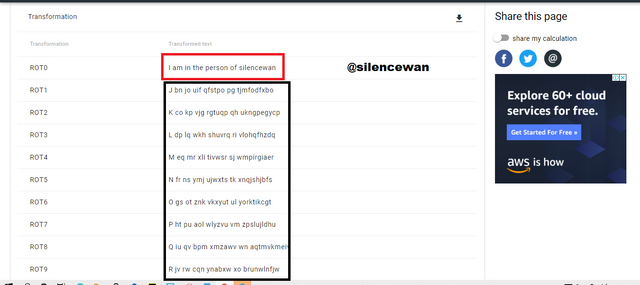
Hash
The process of calculation is easy to operate.
It is secured and it does not also requre any key to open its softwares.
Hash is the process of getting secret code for a given day input in an alphanumeric code format.
The main aim is to verify the input data and to secure it with the code
In getting a secret code in the form of alphanumeric code for a given input data is known as hash.
Also used to securely send passwords and files to other users.
Example code
Input: I am in the person of silencewan
Hash code: 5e8bb4cff65d3ae4b63603c25bda235e4e53ed79943c1af4051b5dc7f483df60
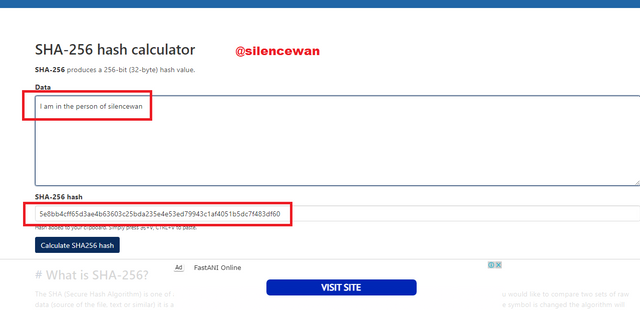

Conclusion
In this task, we hae talked about hash and cryptography. We also spoke about how to use the etherscan and the tronscan to see details of blocks and transaction hashes. What was discussed again is the process of how to generate a hash code using SHA-256 hash code then we finally discussed the differences between hash and cryptography
All parts of the questions asked by the professor has been answered. It was a great class and I really enjoyed the lecture with the professor. it is my greatest hope and prayer to be part of his next lecture that will be coming next two weeks.
Thanks for the time and attention.
Gracias por participar en Steemit Crypto Academy Season 3:
Espero seguir leyendo tus publicaciones.
La transacción del hash no pude observarla, letras muy pequeñas.
En la pregunta 3 se puede ver la resistencia a la colisión.
Recomendaciones:
Cuando los datos solicitados no se pueden ver, favor copiar y pegar en un sitio visible.
Es necesario jsutificar el texto.
Calificación: 8.4
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit